You may encounter a condition in which Azure Active Directory synchronization stops working, for example in an environment that is using directory synchronization for Office 365.
The Operations view of the Synchronization Service Manager (miisclient.exe) will display a status of “stopped-extension-dll-exception” for operations on the Windows Azure Active Directory Connector.
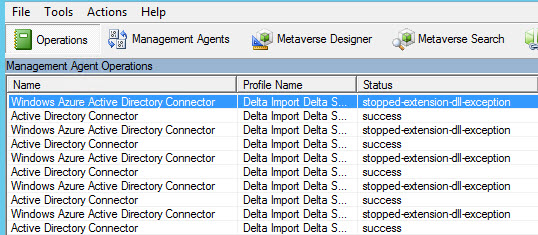
The Application event log of the directory synchronization server may log the following entries:
Log Name: Application Source: Directory Synchronization Date: 26/02/2015 10:34:00 AM Event ID: 0 Description: Update your password and try again. GetAuthState() failed with -2147186688 state. HResult:0. Contact Technical Support. (0x80048831) Log Name: Application Source: Directory Synchronization Date: 26/02/2015 10:34:00 AM Event ID: 109 Description: Failure while importing entries from Windows Azure Active Directory. Exception: Microsoft.Online.Coexistence.ProvisionException: Update your password and try again. ---> Microsoft.Online.Coexistence.Security.WindowsLiveException: GetAuthState() failed with -2147186688 state. HResult:0.
A likely cause of this issue is an expired password for the account used to connect to Azure Active Directory. To determine which user account is used look in the Management Agents view of the Synchronization Service Manager (miisclient.exe), open the Properties of the Windows Azure Active Directory Connector and select the Connectivity settings.
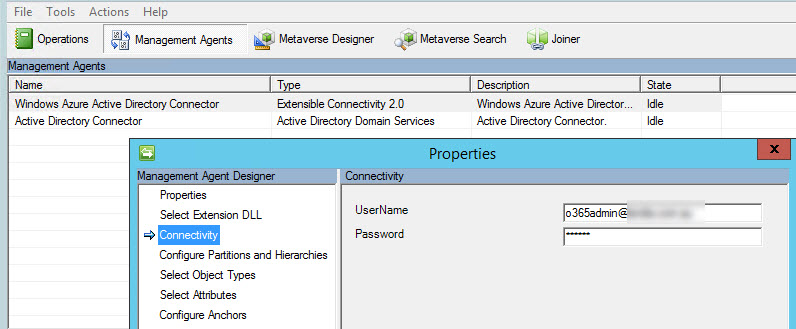
If you know the expired password you can login to the Office 365 portal with that username and password, and follow the prompts to update the expired password. Then return to the Synchronization Service Manager and update the configuration with the new password.
If you would like to set a non-expiring password for the account you can configure this using the Azure Active Directory PowerShell Module.
Install the Azure AD PowerShell module if you have not already installed it. Open a PowerShell console and connect to Azure AD, entering your admin credentials when prompted.
PS C:\> Connect-MsolService
Configure the account to have a non-expiring password. When you do this for an account with an expired password the existing password will begin working again as well.
PS C:\> Set-MsolUser -UserPrincipalName o365admin@office365bootcamp.net -PasswordNeverExpires $true
The next directory synchronization operations should complete successfully.



Thank you BOB! you are a lifesaver, give this man a silver star!
Dear Bob, THANK YOU, the TLS enable worked for me.
THANK YOU!
Thank’s a lot! Fixed my Problem.
TLS 1.2 requirement for version 2.3.20 was my issue.
Amusing how this article is solving a problem it wasn’t written for. Heh
Thanks! I also got this issue, solved by enabling TLS 1.2 (not what was mentionned in this article)
Probably because TLS 1.2 is now required pretty well everywhere in Microsoft 365…
Thank you so much , you fixed my issue
I just had this exact error when I upgraded AzureAdConnect from 2.3.8 to 2.3.20 (July 2024). I tried everything but my solution was: “TLS 1.2 enforcement for Microsoft Entra Connect”.
Link: https://learn.microsoft.com/en-us/entra/identity/hybrid/connect/reference-connect-tls-enforcement#powershell-script-to-check-tls-12
1. Run the PowerShell script to check the current TLS 1.2 settings.
2. Run the PowerShell script to enforce TLS 1.2.
3. Reboot
Afterwards, the “Stopped-Extension-DLL-Exception” error during exports disappeared and AAD sync was successful.
Hope this helps someone.
Awesome, had the same issue after upgrading to 2.3.20.
Thanks!
Bob, you were a lifesaver. I just upgraded today and ran into this exact scenario and nothing worked except for your suggestion. Thank you!
Thank You.
enabling TLS1.2 also fixed the no-start-ma issue
Yeah this wasthe problem after upgrading to 2.3.20.0
I was thinking it was DNS, or account passwords so i reset them and repaired the connector…as i had no issues before the update…
thank you BOB!
Thank you!!! My sync broke after I updated my Entra ID Connect Sync and it took me a week to find your post. This fixed my issue, Thanks!!!
This resolved it for me after upgrading to the latest version. Thanks for the Info
Thanks a million! TLS 1.2 was my issue
Hi Bob,
Thanks for sharing the link it helps me resolve the issue.
Thank you SO VERY MUCH – blood pressure returning – cannot thank you enough for this article!
Setting an admin user as the Azure AD Connector account is a really bad practice, this idea is completely outdated and is more than 6 years old! Pratical365 should be more careful in updating their articles as this information is completely ancient and misleading.
You should let AADConnect manage its connector accounts which will create a special service account in AD/Azure AD.
AADConnect includes a cmdlet to reset the Azure AD Connector account and password (for many years now) – Add-ADSyncAADServiceAccount
Also, on the latest release (1.6), AADConnect also includes a cmdlet to reset the On-premises AD DS Connector account and password – Add-ADSyncADDSConnectorAccount
You’re correct that this is an old article. And old articles don’t get updated very often. In fact, if you look across most blogs, you’ll find very few instances where articles are systematically updated on an ongoing basis. There’s too much work to do to keep on going back to review text periodically to detect when changes occur and authors are not paid for this effort. Which is why you should treat any article that’s more than a few months old with caution and always test the assertions made to ensure that they report what you see with the latest software.
This is the first post that comes up on a web search for Stopped-Extension-DLL-Exception, so here’s another reason for this error: your firewall is blocking autologon.microsoftazuread-sso.com
See if you can get to that link from your Azure AD Connect server.
In my case, turns out it was because the Sync Service user account had Multi-Factor authentication turned on.
Looks like it got turned on when the rest of the user accounts had multi-factor enabled in bulk.
Disabling Multi-Factor Authentication for the Sync user account (found under the Properties > Connectivity) worked for me
This was it for me!
I just configured Conditional Access with required MFA and selected ‘All users’.
This was the problem as you stated.
Thanks!
Thanks, it only took me 2 days to find this post. I followed your instructions, worked first time. Great job!!!
Hi Paul,
After changing password also I am getting stopped-extension-dll-exception error. do i need to wait after resetting password?
Any other steps is required?
Changing which password?
Changing password of cloud Admin which was configured under Synchronization Service Manager. Also I made sure check box is not checked to change password in next login.
I can’t see your environment or what you’ve done. You have to explain exactly what you’re doing, every step, for me to understand your scenario. Changing it where/how?
Problem solved! This is the first website I come to when searching for anything O365 or Exchange.. thanks for the time you put into this website.
First hit on Google Search and it worked. Thanks for the help
I have spent hours trying to fix this after the password expired and changed. Thanks for this article!
Thanks for posting this. Was pulling my hair out over this as none of the other solutions worked.
Ah great work, thanks so much! fixed my problem!