Enterprise SSO is a feature offered by Apple for users using Apple devices (macOS, iPadOS, and iOS) to allow applications (mostly web-based applications) to perform single sign-on (SSO) using corporate identity. This helps users to reduce the need to prompt for authentication when using different applications.
What is Enterprise SSO Plug-in for Apple Devices
Enterprise SSO Plug-in for Apple Devices is a small piece of software that comes with the Intune Company Portal for macOS and Microsoft Authentication for iPadOS and iOS. This plug-in will tap into the OS subsystems when authentication is requested by supported applications. The way it works is that the Enterprise SSO plug-in will help perform the login when the login page or authentication, using a supported authentication protocol, (OAuth, SAML, ConnectID) is requested by an application.
One of the key things to note is that for Enterprise SSO Plug-in to work, it requires applications to support it. For example, it only works with built-in applications that use Apple’s WebView for authentication or when accessing applications with the Safari web browser. Meaning you are not able to use the Enterprise SSO Plug-in with Google Chrome at the time of writing, although it does support Microsoft Edge.
Of course, Microsoft provides some special treatment to apps that use Microsoft Authentication Library (MSAL) as part of their application. All Microsoft-provided apps are using MSAL, so Enterprise SSO Plug-In will work without special configurations for all of their apps.
Enabling Enterprise SSO Plug-in
I would like to highlight one key requirement to use Enterprise SSO Plug-in: your device must be enrolled in Intune and have the needed client software installed (i.e. Microsoft Authenticator for Android/iOS/iPadOS and Company Portal for macOS). It’s a requirement enforced by Apple for security purposes, meaning BYOD devices using MAM will not be able to use this plug-in. You can also refer to Microsoft’s Documentation for other detailed requirements like OS version support.
To use the Enterprise SSO Plug-in, you need to first enroll the devices to Intune MDM and then configure a configuration profile using the device feature template (Figure 1), and then scroll down to enable the SSO with Azure AD by selecting AzureAD as the SSO app extension type. Figure 2 shows an example profile for macOS.
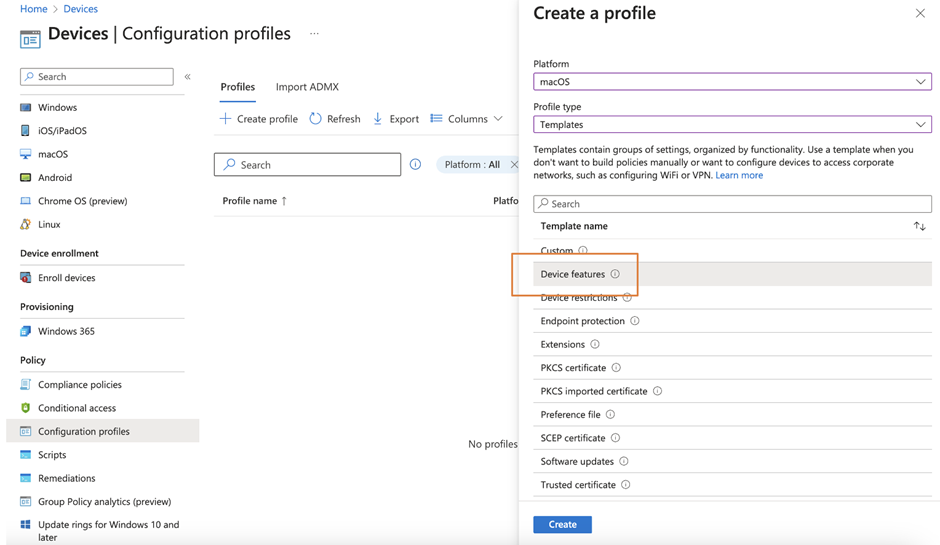
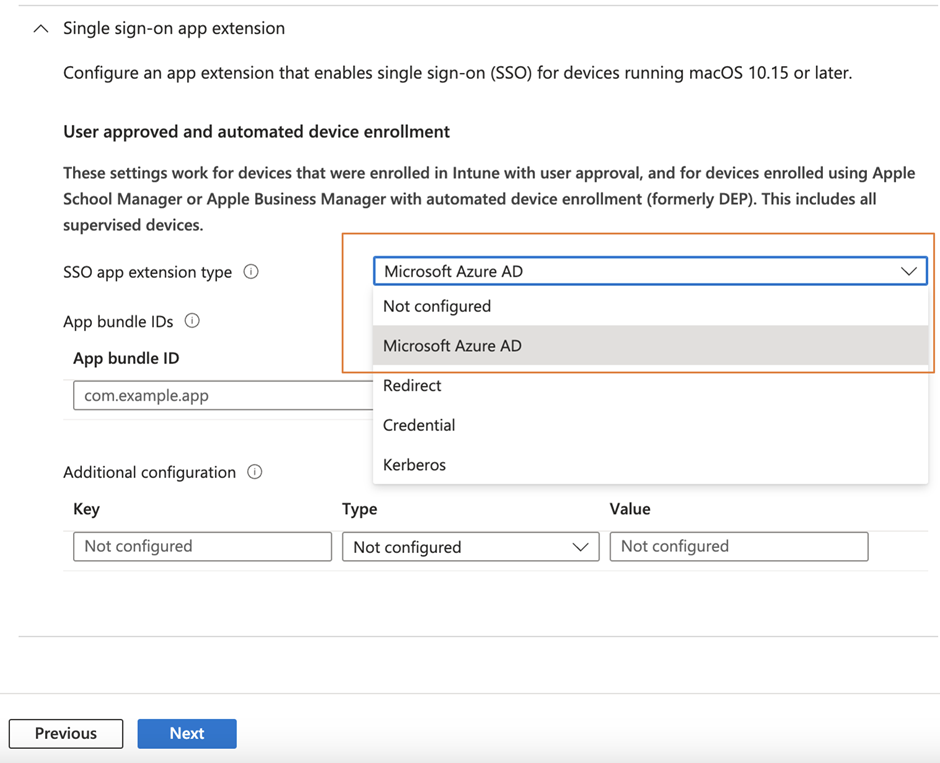
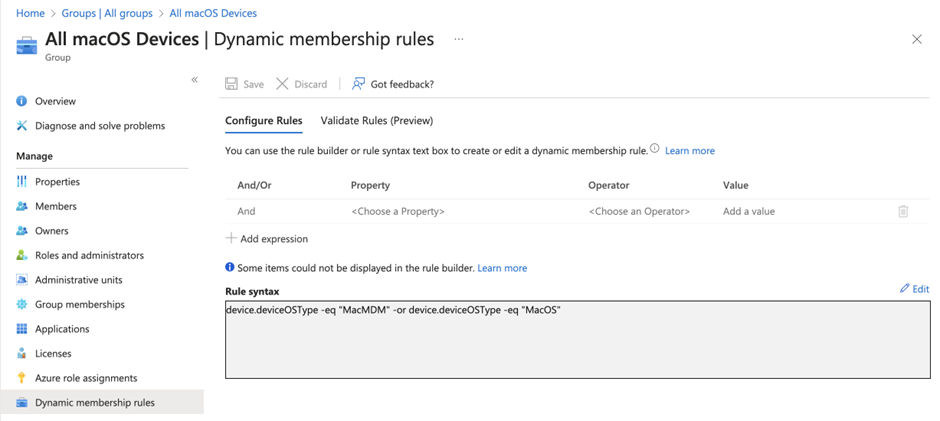
Since this configuration is a machine-based configuration, you will have to assign the configuration to machines instead of users. For pilot deployment, you can add devices to the group or even this configuration profile one by one. But for production deployment, I always prefer to assign to a group instead of individual users/devices. To save time, you can create a dynamic group that automatically includes all MDM-managed Mac devices upon completed enrollment. You will need to define a dynamic group with queries, as shown in Figure 3.
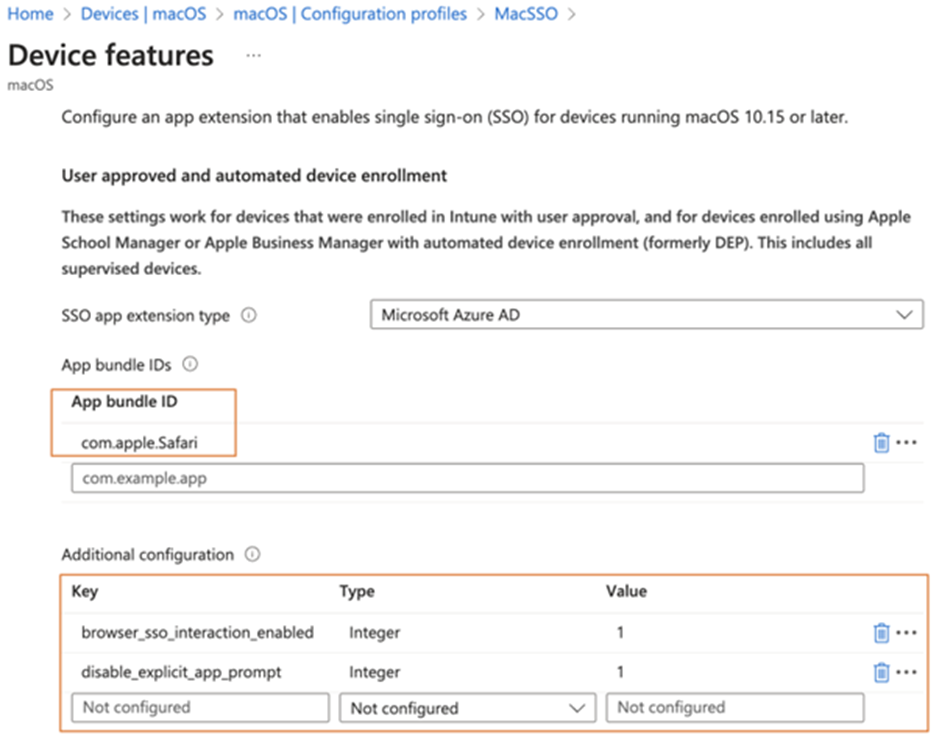
As you can see there are additional configurations that you can include in the configuration profile to control the behavior of the Enterprise SSO plug-in. You can refer to Microsoft’s Documentation for details of the advanced configuration options you can include within your configuration profile. Also note that if you want to enable support for apps not using MSAL (except apps built-in with macOS), you also need to specify the app ID, as shown in Figure 4.
That’s all we need to enable the Enterprise SSO plug-in. Users will then see the prompt to ask them to sign-in to the Enterprise SSO plug-in, in addition to the traditional login prompt. Don’t worry, this prompt only shows once as that’s the point of using SSO. Also, note that you need to repeat these steps for iPadOS and iOS.
End User Behaviour in macOS
Once the configuration file is deployed to the device, users will be prompted to log in to the Enterprise SSO plug-in, as shown in Figure 5.
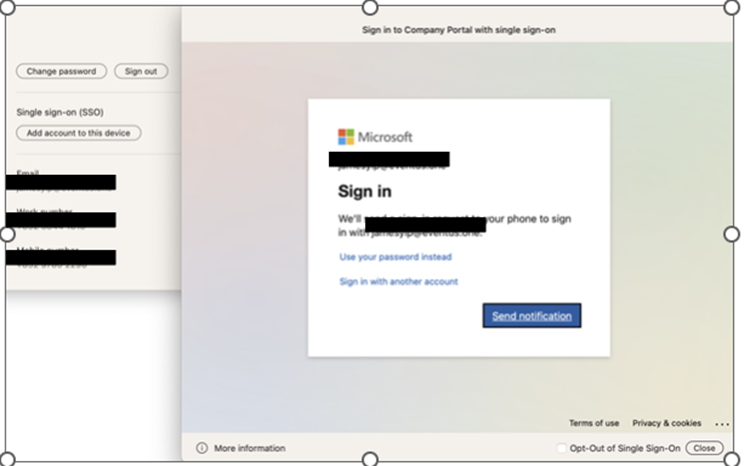
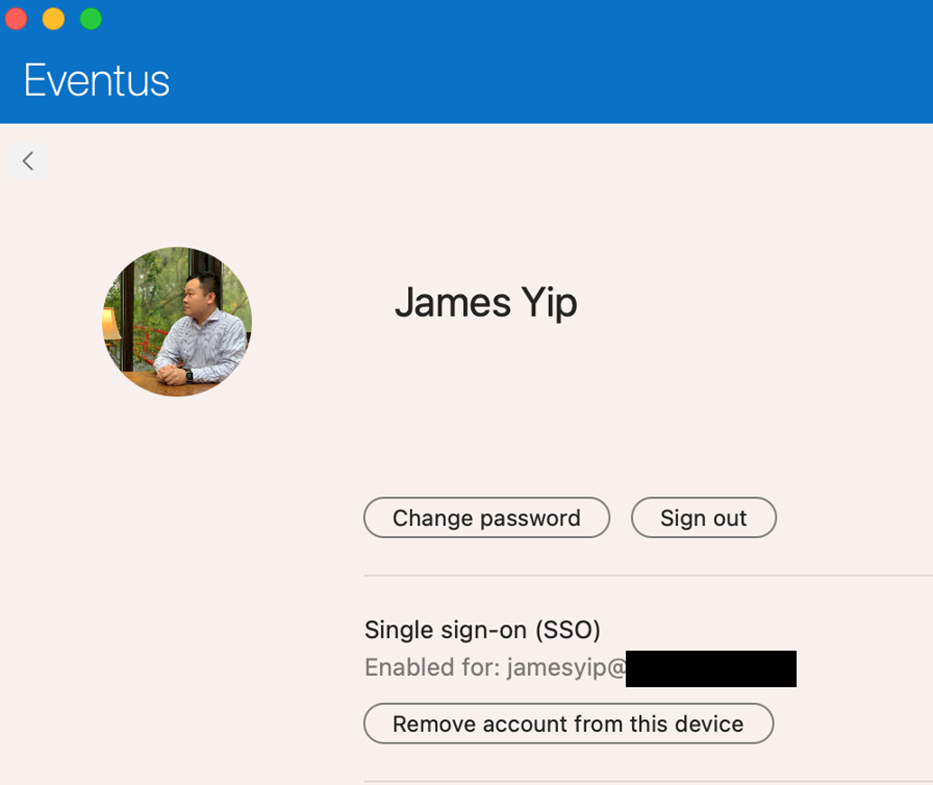
Upon successful authentication, you can check the status by opening the Company Portal app and clicking the profile icon (your login icon at the top right) as shown in Figure 6. You can also remove the Enterprise SSO support for that account by clicking Remove account from this device.
Now all apps that support Enterprise SSO will not prompt for login. For example, if you open Outlook and add the same account you’ve signed in with, no login prompt will display, and you can just complete the configurations without logging in. Just remember you also need another configuration profile created for iPad and iOS to use this feature.
Microsoft also published an animation showing how it works in macOS’s Safari browser, which you can check out here.
On Demand Migration
Migrate all your workloads and Active Directory with one comprehensive Microsoft 365 tenant-to-tenant migration solution.
Other MDM System Support
You may wonder if the Enterprise SSO plug-in is an Intune-specific feature, but it’s actually not. You can deploy the app that includes the Enterprise SSO plug-in with other MDM systems like JAMF. You just need to follow the guide provided by the respective vendor or the guide from Microsoft. The steps would follow the manual deployment approach like deploying a configuration profile with the PLIST setting file like this for advanced properties:
<?xml version="1.0" encoding="UTF-8"?> <plist version="1.0"> <dict> <key>AppPrefixAllowList</key> <string>com.microsoft.,com.apple.,com.jamf.,com.jamfsoftware.</string> <key>browser_sso_interaction_enabled</key> <integer>1</integer> </dict> </plist>
Enterprise SSO Plug-in Troubleshooting
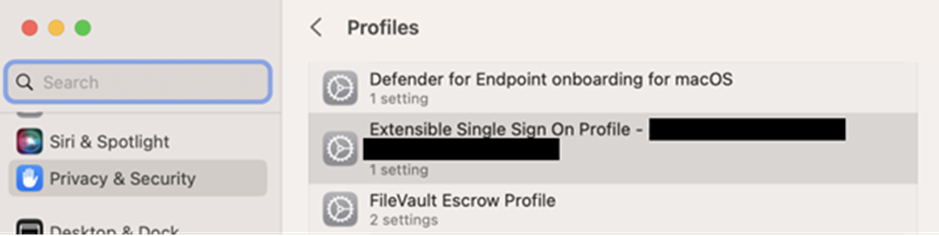
In case there are issues (like SSO not working for some domains), you can take a simple step to check if the Enterprise SSO Plug-in configuration is deployed and the settings inside are correct. For macOS, you can open the macOS Settings app and open the deployed profiles screen by opening System Settings > Privacy and Security > Profiles. Identify the profile named Extensible Single Sign On Profile – xxx, where xxx= guid of the profile (Figure 7).
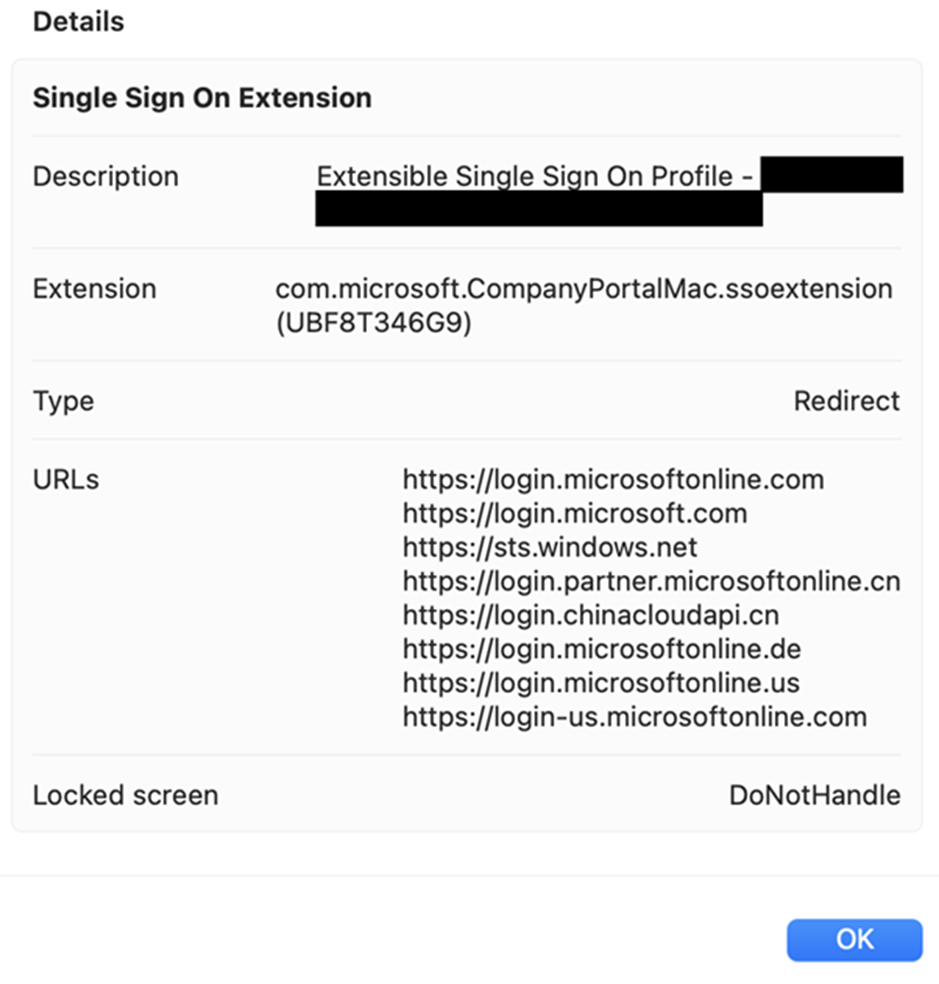
Open the profile setting by clicking the profile name, and you should see all the configurations deployed to this device (figure 8). You can then confirm if the settings are deployed correctly to the users’ endpoint.
When deploying the Enterprise SSO plug-in, I have experienced some common issues (such as missing URL, latest settings not deployed to endpoint, etc.). However, I have come across some interesting issues. In one instance, we inspected the MDM configuration and found that they were fine, but the settings were not deployed to the endpoint because the push certifications had expired a while ago.
Summary
I do recommend all our clients to deploy this in their macOS deployment, so users won’t be getting prompted to sign-in to supported applications. This helps increase the user’s satisfaction as it is easier to use when dealing with different applications.




