As of June 30, 2024, Microsoft stopped supporting the group writeback feature in Microsoft Entra Connect. It still works, but it is no longer supported and it may just stop working without any notice.
Group writeback is also available in Microsoft Entra Cloud Sync, so if you are using this feature it’s time to start looking at Entra Cloud Sync.
Entra Cloud Sync
Microsoft Entra Cloud Sync is a Microsoft cloud service used to synchronize objects from an on-premises Active Directory to Microsoft Entra ID and vice versa. As such, it is the successor of Microsoft Entra Connect.
Compared to Entra Connect, Entra Cloud Sync does not apply any logic to on-premises objects. All processing like the selection of objects or transformation of objects takes place in the Microsoft cloud. The database, the sync engine, and the Synchronization Rules editor apply in the cloud. The only piece of software that runs on-premises is a lightweight agent that communicates with Entra Cloud Sync. In addition, managing Entra Cloud Sync is done in the Microsoft Entra ID Portal.
Installing and Configuring Entra Cloud Sync
Installing the Cloud Sync agent is similar to installing the Entra Connect software. The difference is in configuration, which happens in the portal.
To install the Cloud Sync agent the following prerequisites apply:
- The account installing the software must be a Domain Administrator or Enterprise Administrator. During the installation, a group managed service account (gMSA) is created to run the agent.
- To configure Cloud Sync, the minimum requirement is to use a Hybrid Identity Administrator to connect to Entra ID.
- The server where the agent is installed must run Windows 2016 or higher.
- And…. For Entra Cloud Sync the account that installs the software needs an Entra ID P1 license.
You can download the Cloud Sync agent software from the Entra ID portal (Select Microsoft Entra Connect à Cloud Sync à Monitor à Agents). After downloading the software, you can start it by double-clicking on the file AADConnectProvisioningAgentSetup.exe.
After the welcome screen, you are presented with an Extension Selection screen where you can choose between HR-driven provisioning (selected by default, Figure 1) and On-premises application provisioning. For more information regarding this option, check the What is Provisioning page on Microsoft Learn.
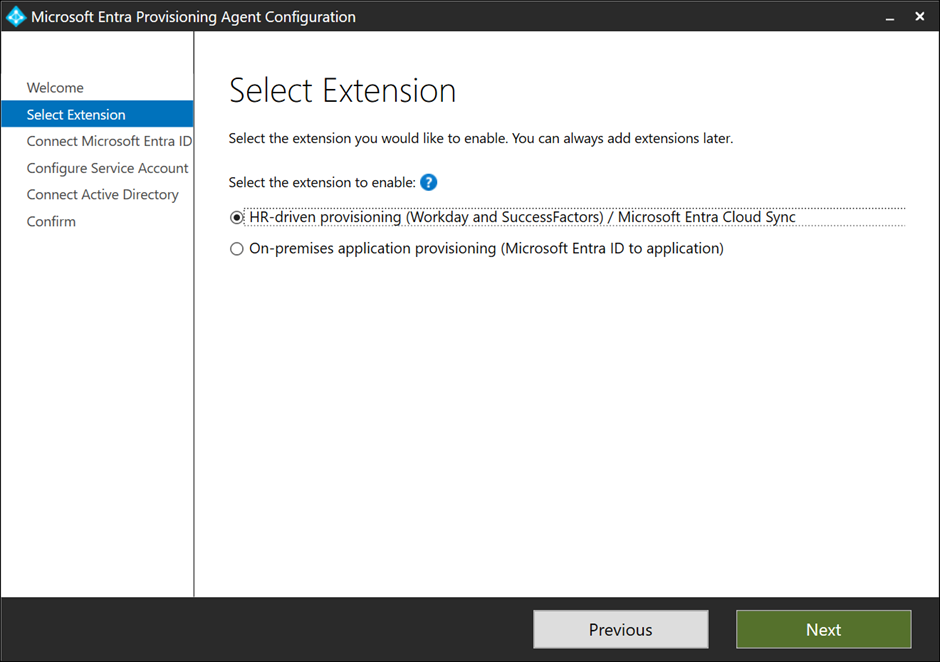
Click Next to continue, and when prompted to authenticate, log on to Entra ID using a Global Administrator or a Hybrid Identity Administrator. Follow the wizard’s directions and enter details for your local on-premises administrator account. You can decide to create a new gMSA (group Managed Service Account) or use an existing gMSA (when you install additional Cloud Sync agents on other servers). A gMSA is a managed service account, but compared to a local managed service account it can be used on multiple servers.
The remainder of the setup wizard is simple. Connect to Active Directory, review the settings, and the agent software is installed.
Configuring Entra Cloud Sync
To continue with the configuration of Cloud Sync, login to Entra ID and select Hybrid Management à Entra Connect à Cloud Sync. Select New Configuration and click AD to Microsoft Entra ID Sync to start the configuration wizard.
The domain name is already listed (assuming the on-premises domain is also registered in the Microsoft Online environment). Note that you can only select PHS (password hash sync). ADFS and PTA (pass-through authentication) are not available.
Creating a cloud sync configuration consists of three steps:
- Add scoping filters (required).
- Attribute mapping (optional).
- Test the synchronization (recommended).
Scope Provisioning to Specific Users and Groups
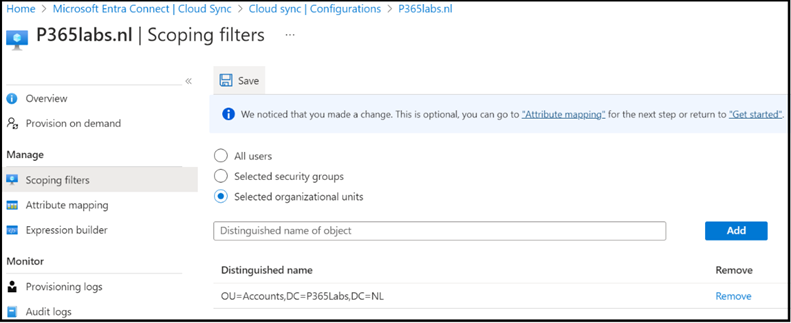
Scoping is a required feature and is similar to scoping in Entra Connect. With scoping you define what users and groups will synchronize to Entra ID. To create a new scope, click Scoping filters, and in the right pane select Selected organizational units. Enter the distinguished name of the OU (like OU=Account, DC=Contoso, DC=Com) and click Add the add it to the configuration (Figure 2).
Attribute Mapping
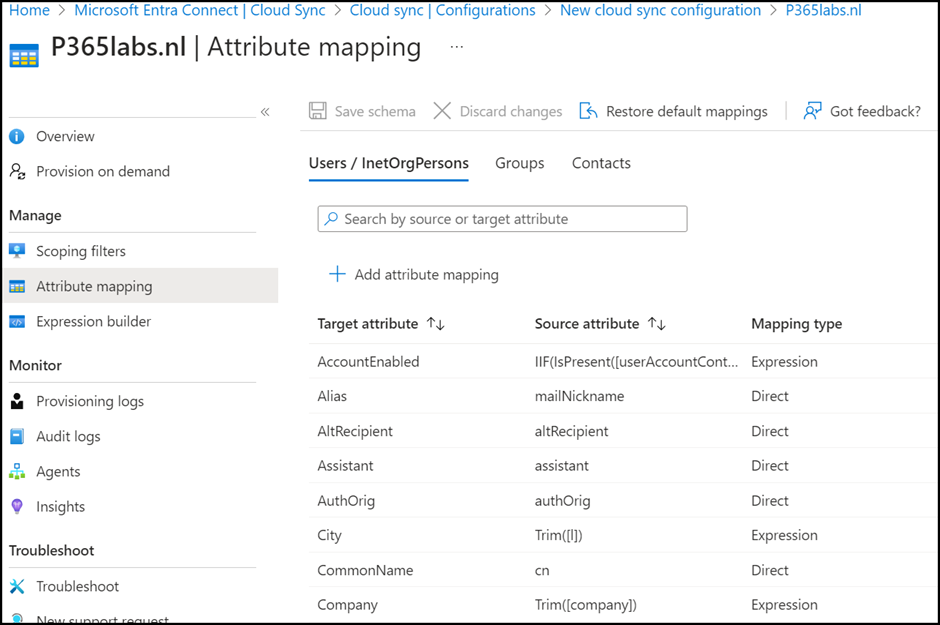
Attribute mapping is similar to attribute mapping in Entra Connect. This is where Active Directory attributes are mapped to attributes in Entra ID. Unless you have specific requirements to do this, there is no need to change anything here, so I normally accept the default settings as shown in Figure 3.
Test on Demand
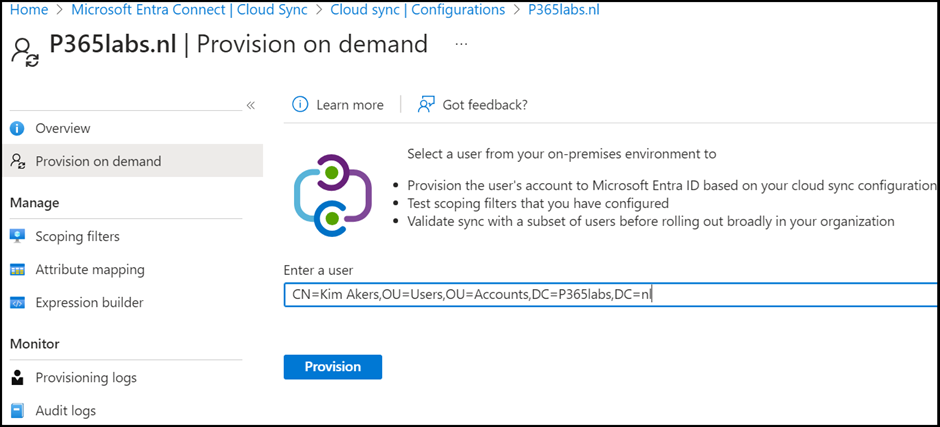
Test on demand is a nice feature where you can test the new sync configuration using just one (test) user account before you enable the new configuration. Select provisioning and enter the Distinguished Name of the user, like CN=Kim Akers, OU=Account, DC=Contoso, DC=COM) as shown in Figure 4.
When everything is ok (you’ll see three green checkboxes in the configuration screen), the configuration can be enabled. Select Overview, click Review and Enable, and click Enable Configuration. When finished, the configuration should show a healthy status.
When you check the Microsoft Online Portal (or Entra admin center) you’ll see the on-premises account appear online.
Group Writeback to Active Directory
To configure group writeback in Entra Cloud Sync you must create a new synchronization configuration. To do this, login to the Entra admin center and select Hybrid Management > Entra Connect > Cloud Sync. Select New Configuration and select Microsoft Entra ID to AD sync.
Just like with synchronizing users from Active Directory to Entra ID, the group writeback configuration consists of:
- Scoping filters (required).
- Attribute mapping (optional).
When creating a scoping filter, all security groups or a selection of security groups can be selected. When selecting the latter, a selection of security groups that are synchronized can be made in the ‘edit objects’ section.
The default location to store the groups synchronized back to Active Directory is the CN=Users administrative unit. To change this, select ‘Edit attribute mapping’ and enter the distinguished name of the container where the objects must be stored as shown in Figure 5.
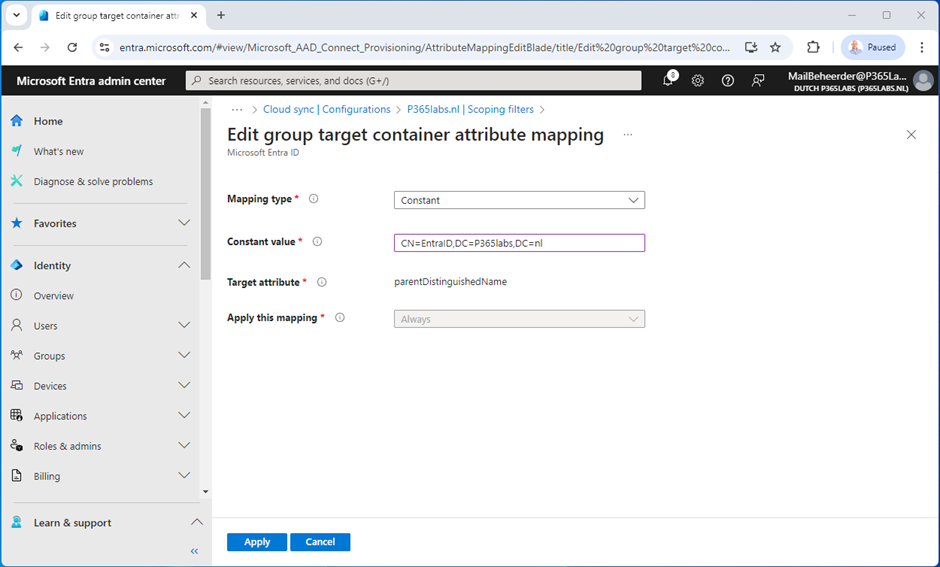
Click Apply and Save to store the new configuration. The remaining attributes in the attribute mapping section can be left at their default values.
You can use the provision on demand option to use only one security group in Entra ID to test the new configuration. If the test is ok, go to overview, select review, and click enable to start the new synchronization configuration.
After a couple of minutes, you will see the security groups appear in Active Directory.
Limitations
Unfortunately, some limitations exist for Cloud Sync group writeback:
- Only cloud-created security groups are synchronized from Entra ID back to Active Directory. These can be assigned or dynamic, both are supported.
- These cloud-created security groups can only contain members that are synchronized from your Active Directory to Entra ID.
- Nested groups are not synchronized. If you need to synchronize nested groups, you must add the individual group members to the configuration.
- Editing synchronized groups in Active Directory is not supported, and edits are not synchronized back to Entra ID.
The old Microsoft Entra Connect was not perfect when it came to functionality and features, but it was better than Cloud Sync.
Summary
As of June 30, 2024, Microsoft stopped supporting the group writeback feature in Microsoft Entra Connect. It still works, but it is no longer supported and it may just stop working without any notice.
Microsoft Entra Cloud Sync is the successor of Entra Connect, and it also supports group writeback functionality. Unfortunately, Cloud Sync is still limited to security group writeback (no distribution group and no Microsoft 365 Group writeback), and even security group writeback is limited. The good news is that Microsoft is developing new features so in time things will become better. The bad news is that when you have group writeback running extensively on Microsoft Entra Connect you may run into issues, and the only thing you can do is wait.





Jaap, there is a lot of misunderstanding about group writeback and of support on the internet, including on this page.
According to Microsoft via your link:
“The public preview of Group Writeback v2 in Microsoft Entra Connect Sync will no longer be available after June 30, 2024.” “For customers who provision Microsoft 365 groups to Active Directory, you can keep using Group Writeback v1 for this capability.”
This article explicitly states that Group Writeback v1 will continue to work, is still supported by Entra Connect and no end of support date has been announced. You may want to update your article to include this detail, and perhaps expand upon the article and explain the differences between Group Writeback v1 and Group Writeback v2.
Luis the difference between V1 and V2, according to what I could found and understood is Writeback V1 syncs Microsoft 365 groups ONLY.
Hi Jaap – thanks for sharing this article. Really insightful and I had a question about managing the on-prem AD groups through Entra ID as part of Provisioning process using Joiner workflows. Can we add default AD groups which are available on-prem through entra ID and note that the groups are not available on entra.is it even possible or we have some limitations?
Hi Jaap – thanks for sharing this article. Really insightful and I had a question about managing the on-prem AD groups through Entra ID as part of Provisioning process using Joiner workflows.
Can we add default AD groups which are available on-prem through entra ID and note that the groups are not available on entra.
is it even possible or we have some limitations?
thanks in advance.
Thanks for clarifying the initial wording, Jaap! I had similar concerns to Brian B.
No no, it’s not the Entra Connect that’s no longer supported, it’s the group writeback feature in Entra Connect that’s no longer supported. Have a look at the Entra Cloudsync article where it states this feature is no longer supported: https://learn.microsoft.com/en-us/entra/identity/hybrid/group-writeback-cloud-sync
Sorry for the confusion.
Do you have something stating officially that the non-cloud Microsoft Entra Connect is no longer supported? Their documentation so far does not state that it is no longer supported, just older versions have end of support dates. https://learn.microsoft.com/en-us/entra/identity/hybrid/connect/reference-connect-version-history . The latest version of this is 2.3.20.0 and has a TBD end of support date, with the prior version ending in July 2025.