As you get ready to decommission legacy Exchange servers after the transition to Exchange Server 2007 or 2010 you might be concerned about any remaining devices or hosts that are using the server for SMTP traffic.
It has been my experience that no matter how well managed or documented an environment is, there is always some application or device that nobody thinks of that is relaying email through the Exchange server. Whether its a custom app that some developer is running on his workstation, or a printer that does scan-to-email, something is bound to break when you remove the Exchange server.
Fortunately you can just about eliminate this risk with a little log monitoring on the Exchange 2003 server. This is best performed after you have migrated all data and known services away from the server, to minimise the amount of potential traffic you pick up in the monitoring.
The first step is to enable logging of SMTP traffic on the server. Open Exchange System Manager and navigate to the SMTP Virtual Server.
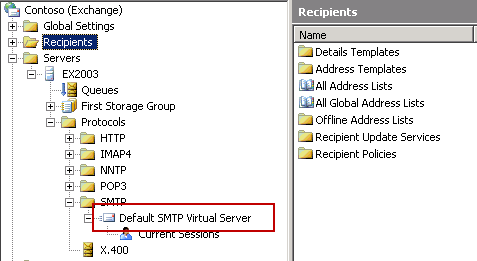
Open the properties of the SMTP Virtual Server. Tick the box to enable logging.
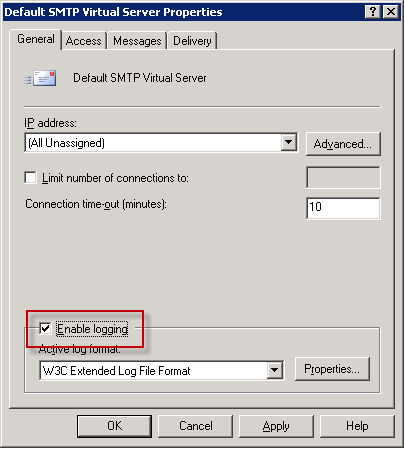
Leave the log format as “W3C Extended” and click the Properties button. Take note of the log file directory, and I also always enable local time for log naming and rollover
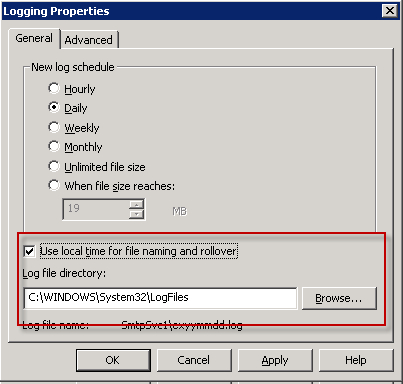
Click on the Advanced tab and enable at a minimum the Client IP Address. I also include the Date and Time, and depending on your environment there may be other extended properties that you should enable.
Click OK, OK, etc to apply the new configuration. You can now wait for as long as you deem necessary to capture any remaining SMTP traffic that is traversing the server. I aim for 48 hours but in some environments a longer period would be appropriate.
Once the logging has been enabled and allowed to run for a while you’ll have one or more log files in the log file directory.
If you look in a log file you’ll see a list of IP addresses that have connected to the server for SMTP. A typical SMTP session will generate more than one line of logging, so this means potentially hundreds or thousands of lines of logging, maybe over multiple log files, that need to be consolidated down into a list of unique IP addresses.
This consolidation is made easy thanks to Logparser. Download and install Logparser, and then launch it from the Start Menu.
A very simple query to extract the unique IP addresses from the SMTP log files looks like this:
C:Program FilesLog Parser 2.2>LogParser -i:IISW3C "SELECT DISTINCT c-ip FROM 'C:WINDOWSsystem32LogFilesSMTPSVC1*.*'" ------------ 192.168.0.2 192.168.0.101 192.168.0.110 Statistics: ----------- Elements processed: 8181 Elements output: 3 Execution time: 0.09 seconds
You have now got a nice short list of IP addresses that are using the server for SMTP communications and can go and investigate the applications or device configs that are causing it, before you shut down the legacy servers for good.



Hi Paul,
Firstly love your blogs always really useful. Secondly I need some advice. Just completed an 03 to 2010 migration. IThe 03 boxes are in a clustered pair. In the smtp logs they seem to be sending from c-ip (there cluster address) to s-ip their cluster address but s-computername is the dns name of the cluster server which is not active. These are all QUIT commands but large amounts of data in the sc-bytes fields ? Is this normal the queues look empty?
cheers
You may need to enable more of the logging fields (to, from, etc etc) to get a better idea of what the connections are for. Maybe PF replication, hard to say without seeing a sample.
Hi Paul,
I’ve changed the ip/server names. Take a look every ten seconds and up 128bytes.
Cheers
date time c-ip cs-username s-sitename s-computername s-ip s-port cs-method sc-bytes cs-bytes cs-version cs-host cs(Referer)
20/05/2013 20:28:19 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 86987 4 SMTP – –
20/05/2013 20:28:29 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 87115 4 SMTP – –
20/05/2013 20:28:39 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 87243 4 SMTP – –
20/05/2013 20:28:49 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 87371 4 SMTP – –
20/05/2013 20:28:59 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 87499 4 SMTP – –
20/05/2013 20:29:09 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 87627 4 SMTP – –
20/05/2013 20:29:19 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 87755 4 SMTP – –
20/05/2013 20:29:19 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 87883 4 SMTP – –
20/05/2013 20:29:29 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 88011 4 SMTP – –
20/05/2013 20:29:39 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 88139 4 SMTP – –
20/05/2013 20:29:49 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 88267 4 SMTP – –
20/05/2013 20:29:59 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 88395 4 SMTP – –
20/05/2013 20:30:09 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 88523 4 SMTP – –
20/05/2013 20:30:19 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 88651 4 SMTP – –
20/05/2013 20:30:19 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 88779 4 SMTP – –
20/05/2013 20:30:29 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 88907 4 SMTP – –
20/05/2013 20:30:39 1.1.1.1 – site1 mail1 1.1.1.1 0 QUIT 89035 4 SMTP – –
Looking for a way with exchange 2010 with multiple receive connectors to identify with hosts are relay mail to an external domain. I would like to capture the email address and the ip address. Is there any shell scripts i can run against the logs to procure this data for me? What method would you recommend?
Hi Charles, turn on protocol logging and you should find what you need in the logs it generates. PowerShell could extract it or Log Parser.