When an Exchange Online mailbox has the ActiveSync protocol disabled, you may find that the Outlook app for iOS and Android mobile devices is still able to connect to the mailbox to send and receive emails.
PS C:\> Set-CasMailbox dave.bedrat -ActiveSyncEnabled $false
The reason for this is the architecture of the Outlook app and the infrastructure it connects to. From TechNet:
Outlook for iOS and Android uses a stateless protocol translator component that is built and run in Azure. This component routes data and translates commands, but it doesn’t cache user data. The app is coded with the Outlook device API, a proprietary API that syncs commands and data to and from the app. Exchange Online data is accessed via the publicly available REST APIs. The protocol translator enables communication between Outlook and Exchange Online.
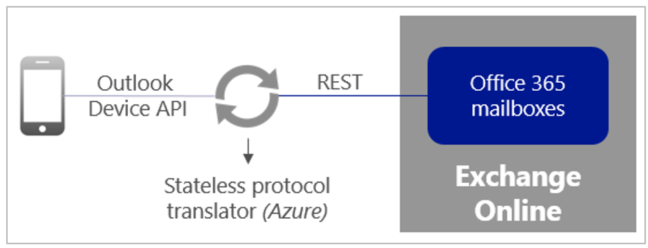
Even when ActiveSync is disabled the REST API is still accessible by Outlook. To block access to the REST API we need to use a different method. There are a few approaches that we can use:
- A device access rule to block Outlook for iOS and Android. This is an organization-wide block and requires you to manually approve Outlook app usage on a per-user basis for anyone who still needs to use it, so it may not be a practical approach if you’re just trying to block one user from having any mobile email access.
- A client access rule to block REST API access. Client access rules can be targeted at specific users but managing the target list over time could be cumbersome. This approach also blocks all REST API access for the targeted users, not just the Outlook app.
- Block the Outlook app using an EWS block list. This is the approach I’ll demonstrate here.
As I’ve previously written here, EWS policies can be used to block or allow specific applications on a per-user or per-organization basis. If you want to block Outlook app usage for the entire organization then you would use an organization-level EWS block list. Since this example scenario is for a user who has had the ActiveSync protocol disabled I will stick to the per-user option. As a side note, if your Office 365 tenant has any “K” (kiosk) licenses then the organization-level EWS controls will not work, and you’ll need to use per-user EWS controls.
First, let’s take a look at the mobile device association that shows Outlook connecting to the REST API.
PS C:\> Get-MobileDevice -Mailbox "Dave Bedrat" | Where {$_.FriendlyName -like "Outlook*"} | Select DeviceModel,DeviceUserAgent,DeviceAccessState,ClientType
DeviceModel : Outlook for iOS and Android
DeviceUserAgent : Outlook-iOS/2.0
DeviceAccessState : Allowed
ClientType : REST
Next, let’s look at the EWS configuration for the mailbox.
PS C:\> Get-CASMailbox "Dave Bedrat" | Select *EWS* EwsEnabled : True EwsAllowOutlook : EwsAllowMacOutlook : EwsAllowEntourage : EwsApplicationAccessPolicy : EwsAllowList : EwsBlockList :
To block EWS access for the Outlook app we need to block the user agent. The iOS version of Outlook currently has a user agent of “Outlook-iOS/2.0” (shown above), and the Android version uses “Outlook-Android/2.0”. Earlier versions had a user agent of “Outlook-iOS-Android/1.0” for both platforms, so we can expect the user agent to change in future as the version number increments. As such, it’s best to use a wildcard in the EWS block list. The example below will block the original user agent, the current user agents for both platforms, and any future user agent strings that follow the same pattern.
PS C:\> Set-CASMailbox "Dave Bedrat" -EwsBlockList @{Add="Outlook-iOS/*","Outlook-Android/*"}
Another look at the EWS configuration for the mailbox shows the two user agents have been added to the block list, and the EwsApplicationAccessPolicy option is now set to EnforceBlockList.
PS C:\> Get-CASMailbox "Dave Bedrat" | Select *EWS*
EwsEnabled : True
EwsAllowOutlook :
EwsAllowMacOutlook :
EwsAllowEntourage :
EwsApplicationAccessPolicy : EnforceBlockList
EwsAllowList :
EwsBlockList : {Outlook-Android/*, Outlook-iOS/*}
This change doesn’t take effect immediately. In my demo environment it took about 30 minutes before the Outlook app on my iPad stopped retrieving new emails. The access token life is 1 hour by default though, so you should expect it to take at least that long.
To reverse the block, remove the two user agents from the block list, and if there’s no more block list entries you can also null the EwsApplicationAccessPolicy.
PS C:\> Set-CASMailbox "Dave Bedrat" -EwsBlockList @{Remove="Outlook-iOS/*","Outlook-Android/*"}
PS C:\> Set-CASMailbox "Dave Bedrat" -EwsApplicationAccessPolicy $null
As one last point to keep in mind, the DeviceAccessState for the mobile device association won’t change from Allowed to Blocked when you use an EWS block list.

Just FYI, this no longer applies to the Outlook for iOS/Android apps. See the purple note about 3/4 down the page.
https://docs.microsoft.com/en-us/exchange/clients-and-mobile-in-exchange-online/client-access-rules/client-access-rules
Hello Paul,
thx 4 your great & helpful article.
Unfortunately EWS application support is not included in Office 365 F3 license. 🙁
https://docs.microsoft.com/de-de/office365/servicedescriptions/exchange-online-service-description/exchange-online-service-description
How can the Outlook app blocking be done with F3 licenses?
Did you ever figure out how to do this with an E3 license?
I have set the this policy to only allow these agents to connect using the EnforceAllowList, but Apple Mail can still connect. Am i missing something?
Set-OrganizationConfig -EwsApplicationAccessPolicy EnforceAllowList -EwsEnabled $true -EwsAllowList @{add=’WorxMail/*’, “Microsoft Office/*”, “Microsoft+Office/*”, “UCCAPI/*”, “OC/*”, “Mozilla/*”, “*Teams/*”}
I’m 2016 trying to block specific connections with the STEM of /EWS in the attempt to block clients that present a specific user string.
Set-CASMailbox –identity USER–EWSApplicationAccessPolicy:EnforceBlockList –EWSBlockList:”AppleExchangeWebServices/*”,”MacOutlook/14*”,”MacOutlook/15*”,”MacOutlook/16*”,”Mac+OS+X/*”,”Airmail*” –EWSAllowOutlook:$True –EWSAllowMacOutlook:$true –EWSAllowEntourage:$false –EWSEnabled:$true
Dredging the IIS logs and testing mac for outlook 16 I see sc_status of 200 and I can still login.
Is there something I’m missing. You stated that there is a possible delay of 1 hour. Does IIS need to be restarted?
Our goal is to set this at the CASMBX role and not ORG for flexibility reasons. Does that make a difference?
It appears that EWSAllowMacOutlook must be set false to block MAC for outlook clients. The EWSBlock list does not honor agent strings. I could be wrong, but in testing that is my experience.
Is there a way to run report to find all users that are using Outlook-iOS/*”,”Outlook-Android/* on their phone?
I’ve got a few Exchange Online P1 users that should use esclusively Outlook for Desktop.
I do not have Intune nor conditional access available.
I want the configuration to be very simple to maintain for coworkers so I do not want to use PowerShell.
I’ve disabled ALL email apps (protocols ) but MAPI from Microsoft 365 Admin Center on a test mailbox.
I’ve also disabled OWA for Devices in Exchange Admin Center.
I know that disabling EWS on a mailbox removes some functionality in Outlook for Desktop and I accept it.
PS C:\> Get-CASMailbox “Test” | Select *EWS*
EwsEnabled : False
The issue is that even now I can add account and read mail for the mailbox “Test” via Outlook for Android.
Any ideas, anyone ?
OutlookMobileEnabled, which is not exposed in Admin Center, really does something ?
Thank you.
I prefer to use set-casmailbox user@domain.com -OutlookMobileEnabled $False (after about 30 minutes, they will get a block message).
You are simply the best. thank you for your help.
Hi,
When I execute
Set-CASMailbox xxx -EwsBlockList @{Add=”Outlook-iOS/*”,”Outlook-Android/*”}
Return
EwsEnabled : True
EwsAllowOutlook :
EwsAllowMacOutlook :
EwsAllowEntourage :
EwsApplicationAccessPolicy : EnforceBlockList
EwsAllowList :
EwsBlockList : {Outlook-Android/*, Outlook-iOS/*}
But, App keeps working.
Same here. I’ve cleared, re-added these settings. I’ve removed / re-added Outlook for Android – still works depsite the above settings.
I want to restrict ios and OL app onmobile devices for specific users –
When I started with
When I execute
Get-MobileDevice -Mailbox “Swapnil” | Where {$_.FriendlyName -like “Outlook*”} | Select DeviceModel,DeviceUserAgent,DeviceAccessState,ClientType
I don’t get any results
Hello Champ,
-I want to restrict ios and OL app onmobile devices for specific users –
When I started with
Get-MobileDevice -Mailbox “Dave Bedrat” | Where {$_.FriendlyName -like “Outlook*”} | Select DeviceModel,DeviceUserAgent,DeviceAccessState,ClientType
I don’t get results
2) ClientType is showed as : EAS , Instead of REST
PS C:\windows\system32> Get-MobileDevice -Mailbox v-9sjosh
DeviceUserAgent : Apple-iPhone9C2/1601.366
DeviceModel : iPhone9C2
ClientVersion : 16.1
ClientType : EAS
This is an on premise 2013 Exchange.
Thanks in advance for any valuable suggestions.
Hi,
I want to create a ActiveSync device access rule based on the accepted smtp domains as we have multiple accepted domains. One of the accepted domain should have block rule by default and the other accepted domains should allow any devices to connect the ActiveSync.
Paul,
Thanks again for the help. I have opened a case with Microsoft because I have a situation where I have two iPhones, each with the latest Outlook for iOS, that are able to access my account in O365 but do not show up when I run a get-mobiledevice. Not sure if you have ever seen anything like that but that is the current situation I am in. My other two mail clients I am testing (native and nine) work fine. I’ll post back once MS has figured something out.
Kirk,
Did MS ever find out why a couple of your users could see your mailbox? I am running into this issues as well now.
Hi Paul,
First off thank you for not only this information but for your entire site. I refer to it often.
Above you mention the following: “Outlook respects some ActiveSync policy settings (e.g. device access rules, mobile device mailbox policies). But once it’s connected to a mailbox it uses the REST APIs for it’s comms, not EAS.”
Are you aware of any documentation that states exactly what it respects? Also…do you know if it should still show up under get-mobiledevice or get-casmailbox (does it still generate an activesyncdeviceID even though it uses REST for data access)?
TechNet has some doco like this https://technet.microsoft.com/en-us/library/mt465748(v=exchg.150).aspx
Get-MobileDevice will return those devices. There’s also a -RestApi switch if you only want to see those devices and not regular EAS devices.
We have been using this method for a few months now and it works well. However we have discovered a user connecting to her O365 mailbox even with {Outlook-Android/*, Outlook-iOS/*} defined in the EWSBlockList, EwsApplicationAccessPolicy set to “EnforceBlockList” and with EAS disabled. The O365 audit logs show “Client Info String: Client=Microsoft.Exchange.WebServices; Email/1.9.9 (iPhone; iOS 11.3)”. I can’t figure out what “Email/1.9.9” is. I suppose it could be some other mail app. Would it be bad to set “EwsEnabled” to “False” on mailboxes to prevent any connections over EWS?
Hello All,
I just want to block my team members (few selective users) from able to access SKYPE ON MOBILE. In short, these selective users should not be able to login/access Skype from their mobile device like iPhone or Android.
Please tell me all possible steps and tips.
Note: they should have access to install Outlook app in mobile. Just and only want to block Skype on mobile.
We are currently on Office 365, cloud.
Please reply at the earliest.
Thanks,
You can use Azure AD conditional access to block mobile apps from accessing Office 365 services.
In our environment, the user agent doesn’t necessarily follow one string format. Would it be possible to simply use “*” in the EWSBlockList to block ALL apps being used for email on mobile devices?
I’m fairly certain it does since it seems wildcards are accepted, but just want to make sure I’m thinking of this correctly.
Thank you for your excellent post!
Not sure if that’s the best way to achieve that. Instead of using the block list you can switch it to use an allow list, and only allow specific strings.
But, as always, test your theory and see if it suits your needs.
Hey Paul,
Thanks for this informative post. I do have a question for you though. Can this approach also be applied to the mobile OneDrive App while retaining the ability to do it per user? or a different approach would be required?
I don’t understand your question. OneDrive doesn’t connect to ActiveSync or EWS. You can control OneDrive app connections through the OneDrive admin portal, by using Intune app policies, or by using Azure AD conditional access rules.
I am confused with how Outlook for iOS and Android is still blocked if the default organization setting is set to block and then can be allowed using a device access rule, since these settings are ActiveSync settings.
I wonder if there are tenant settings or Organization Config settings that tell the app which protocol to use? In my current trial tenant it seems Outlook mobile uses ActiveSync and not EWS or REST. Modern Authentication is enabled and MFA is enabled on all users, as a confirmation that Modern Auth. is being used.
Any thoughts on this? In my case , disabling ActiveSync globally as a means to only allow the Outlook app to work was a seemingly decent approach. But if Outlook app won’t use EWS/REST then it will be blocked too.
Outlook respects some ActiveSync policy settings (e.g. device access rules, mobile device mailbox policies). But once it’s connected to a mailbox it uses the REST APIs for it’s comms, not EAS.
Hi Paul,
Is the following Outlook iOS app info accurate?
Exchange Version: Protocol Port
Exchange On-Premises 2016 CU6-8: EAS 443
Exchange Online: REST/EWS 443
Thanks,
MM
Hi Paul,
So, do “Mobile device mailbox policies in Exchange Online” apply for EWS access? We are using the Outlook app instead of the native ActiveSync client to access corporate email, but we need to enforce PIN and encryption on Mobile devices (BYOD) , we have a Default policy configured but it doesn’t work. There is another specify configuration for device policies for EWS?
Thanks!
Same exact question as Jean above.
Mobile device mailbox policies do not apply to EWS.
To enforce policies in this scenario you would need to look at an MDM solution such as Intune.
Hi Paul,
With ActiveSync DefaultAccessLevel set to Quarantine, i’m notified everytime someone tries to configure his email account on a mobile device using activesync, and i have the choice to block or allow that device.
But with EWS i don’t have that possibility. For Example, this morning i have configured my email account on Spark Mail App on iphone. I was able to access my emails and i received no notifications (as admin) that someone was accessing his emails with a mobile device. So is there a way to quarantine by default all devices using EWS ?
Thanks.
I just wanto to add also that the Spark email app is not event listed in the device list when using the command Get-MobileDevice.
EWS is not ActiveSync, so the ActiveSync controls and things like quarantine do not apply to EWS, nor will an EWS connected device show up in the output of Get-MobileDevice which is an ActiveSync-related cmdlet.
Barry,
You can allow only Outlook app for accessing through EWS doing this:
https://technet.microsoft.com/en-us/library/mt465747(v=exchg.150).aspx
Regards,
hi there
thanks for the info excellent post , do you happen to know what you need to enter for stopping the windows mail app?
hi
just found it, its microsoft.windowscommunicationsapps
Thanks for the valuable information Paul but I have few things to clear:
1st: why OL app is forcing to use MS Authenticator app
2nd: not able to setup account on updated version which was released a week ago.
3rd: how can I verify If rest API is blocked or allowed ?
4th: what role does EAS play for this app
Thanks in advance.
For #1, if you’re using Exchange Online then it’s possible there is an Intune or conditional access policy being applied to your access.
#2 – no idea, but could be related to #1
#3 – REST API is accessed via EWS. In the article above I demonstrate EWS block lists, and also mention client access rules that can be used to restrict EWS access in Exchange Online (search for TechNet article on that topic)
#4 – EAS is not used by the Outlook app to connect to Exchange Online mailboxes. It is used for on-premises mailboxes though.
For federated accounts what are your thoughts on a fourth option, namely applying ADFS claims rules to block access to the legacy protocols?
If it works for you and you prefer doing it that way then I see no problem with it.
Hi Paul,
Will this outlook for Android app issue is included for On-premises Exchange 2013 as well.
Could you please clarify.
Thanks in Advance
Regards,
Aravind