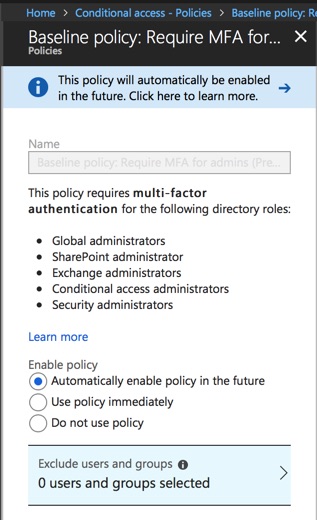
Microsoft is rolling out a new baseline security policy for Azure Active Directory and Office 365 that requires multi-factor authentication for privileged accounts. The policy is in public preview right now, meaning it is visible in tenants but not yet enabled.
The baseline security policy will require multi-factor authentication for accounts that are members of one of the following privileged roles:
- Global administrator
- SharePoint administrator
- Exchange administrator
- Conditional access administrator
- Security administrator
You can view the policy in the Azure AD portal by navigating to the Conditional access section.
Although the baseline security policy is implemented as a conditional access policy there is no customization available except for excluding users and groups. Conditional access rules that you can fully customize require Azure AD Premium licenses, whereas the baseline security policy is available to all customers. You can use the exclusion option to exclude at least one global administrator account from all conditional access policies. Microsoft recommends doing so to ensure that you still have a way to log in if you inadvertently lock yourself out of all admin portals. Think of it as a “break glass in case of emergency” account. The account should have a strong password that is stored in a secure location, and is not regularly used for day to day administration tasks.
The new baseline security policy has been reported elsewhere as “mandatory” or as Microsoft “forcing” multi-factor authentication on customers’ administrative accounts. This is not true of course. You can opt-out of the policy before it goes live by choosing Do not use policy, and you can set exclusions as I just mentioned a moment ago. Aside from the emergency access account you should aim to minimize the exclusions that you add to the policy. Microsoft recommends if possible switching to Managed Service Identity (MSI) or service principals with certificates.
The nature of the policy also ensures that accounts that are temporarily elevated to a privileged role (either manually or via privileged identity management) have MFA enforced on them, reducing the risk of compromise during the period of time they hold privileged access. This is similar to another recent addition to conditional access allowing policies to be targeted at directory roles. That capability extends to a wider range of directory roles than the five that are targeted by the baseline security policy.

Overall this is a good move for Microsoft to make, strongly pushing customers towards securing privileged accounts. When I surveyed readers last year, 55% of respondents were not using MFA at all (even for admin accounts). That’s despite MFA for admin accounts being one of the recommend first steps for new Office 365 tenants, being flagged by Office 365 Secure Score, and being one of the general account security recommendations from Microsoft.
What do you think? Will you be enabling the new baseline security policy in your tenant?



Comments for this blog post are now closed; please contact team@practical365.com for any additional questions and comments, thank you.
We have implemented conditional access policy and it is not working for exchange admin and it works only for global admin
Pingback: What Happens When MFA Fails? - Office 365 for IT Pros
The problem we have is we are an MSP and have about 20 people on our service desk. We manage multiple customers office 365 portals. We also have several engineers out and about that need to sometimes access office 365 portals for our customers. Having MFA for all global admin accounts for those customers is just not practical. Is just having one global admin account with a very complex password secure enough?
Have you become a Microsoft Cloud Partner and then use the Partner portal to connect to each tenant?
This is a really good idea, but what would happen to the Global Admin account that is used for Azure AD Connect as you cannot use MFA for this account?
We have a few SharePoint admin service accounts .. What is the recommended option for MFA on service accounts ? Do we implement MFA on service accounts ?
Can we reset MFA via script or Graph API instead doing it via GUI.
Is MFA Reset the best practice , most of the times we have to perform MFA reset when users are not able to connect to Mobile Outlook app or just in case if we are not able to authenticate of phone number change scenario.
We are using Azure Cloud MFA enforced via Conditional Access
What if the company uses federated identity + on-premises MFA server, so how does this affect SharePoint / Exchange / Conditional access administrators if MFA server is not configured for those Admins? Thank you for your answer in advance.
I’m not really sure what you’re asking me. If you’ve implemented MFA already you can opt out/turn off the new baseline policy before it goes live. It’s a decision for you to make.
Do all the Office 365 PowerShell modules now support MFA?
How do you handle an account that is used as a service account that has global Admin?
Yes.
If you have a service account you can either reduce its permissions to the bare minimum, or exempt it from MFA, or use Microsoft’s recommendations that I linked to in the article.
I consider MFA strongly required for Global Administrators on Office 365 Tenant. This Microsoft movement is really important for security perspective.
As a Consultant, I strongly recommend all my clients set up MFA as default for Global Admins and also other administrative role. But also, I recommend that for the users which usually are more vulnerable because they don’t have mostly security concepts in their minds.