Why Apply an Intune App Protection Policy
Mobile devices play an important role in all Microsoft 365 deployments nowadays. Almost every Microsoft 365 implementation or migration project I have been involved in over the last few years has to consider the best way to manage mobile devices. Some years back, organizations usually opted to use a Mobile Device Management (MDM) solution to control mobile devices. MDM works but can be overly complicated for administrators and end-users since it was not designed to manage apps but instead manage devices. I have seen clients learn some hard lessons from the complexity of MDM, usually when someone accidentally wipes a C-level executive’s phone and all their family photos are gone.
Nowadays, many organizations prefer to use Intune Mobile Application Management (MAM) to control supported mobile apps (i.e., Microsoft’s mobile apps). Managing applications rather than devices helps to reduce the chances of the kind of accident mentioned earlier. The uptake of BYOD has also been a driving factor for the adoption of MAM.
This article will give an overview of Intune app protection policy within MAM with specific policies I found particularly useful for protecting corporate data.
Recap on How Intune MAM works
Intune MAM creates a container to store corporate data shared across all Intune MAM-supported apps. The container is protected and invisible to users via the Files app, for example. Note that each device can only have one Intune MAM container, meaning that someone cannot have two Microsoft 365 accounts on their device if both tenants require Intune MAM. Android Enterprise with Work Profile is an exception as it supports two user profiles running side by side. Therefore, you can have two MAM containers running at the same time.
To apply Intune MAM to apps, you need a Conditional Access policy with the “require app protection policy” setting enabled (Figure 1). This triggers the mobile app to enrol into Intune MAM.
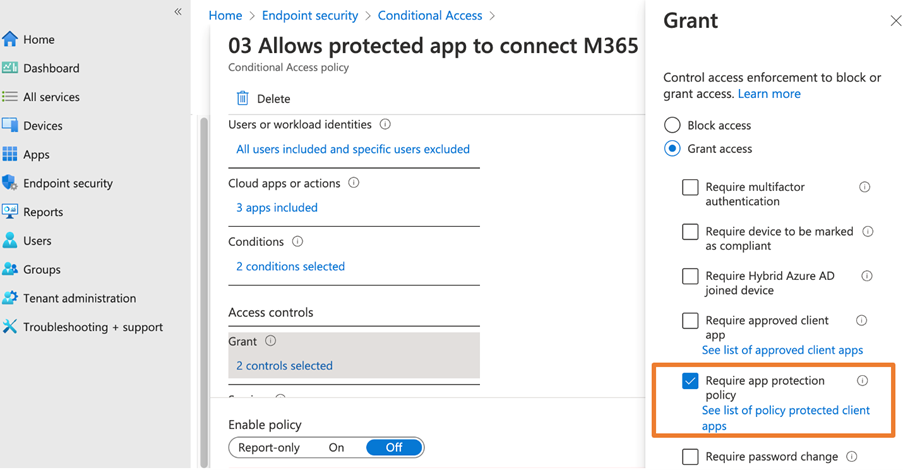
While a policy update is immediate for new users, in my experience, sometimes users whose mobile devices are already registered to Microsoft 365 may have to wait up to 8 hours after updating the CA policy to require Intune MAM before their mobile device respects the policy change.
In addition, for Intune MAM to work, you must install a broker app on the device like one of the following:
- iOS – Microsoft Authenticator
- Android – Microsoft Authenticator or Microsoft Company portal
See Microsoft’s documentation for a more detailed explanation of how Intune MAM works.
Top 10 Security Events to Monitor in Azure Active Directory and Office 365
Discover how native auditing tools can help — and how to overcome their shortcomings.
Useful Intune App Protection Policies to Protect Corporate Data in Outlook
The key objective of using Intune MAM is to control access to corporate data on the device. To accomplish the goal, you need to create at least two application policies. Why two? The application protection policy is configured per device type and hence you would have at least one for iOS and one for Android.
I will highlight key settings in the policy to help you prevent users from sharing corporate data from Outlook. The configured policy applies to all the supported apps or those you assign within the device policy.
Control App Send/Receive Data
You can configure a policy to control if mobile apps can receive data or send it (Figure 2). These settings control the ability of applications to share data (e.g., share Outlook attachments to WhatsApp) or receive data from other apps (e.g., share files from Google Drive to Outlook). The settings are usually configured to allow sharing data across all Managed Apps (apps with Intune MAM support), so users can still share data across apps (i.e., share a file from OneDrive to Outlook and send it out as an attachment).
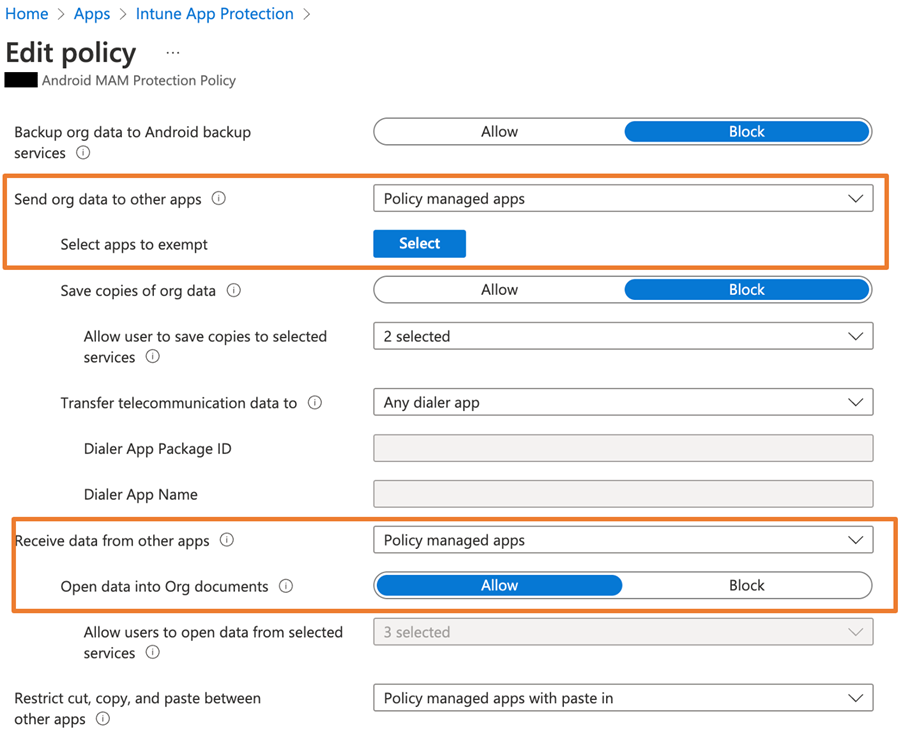
An exception exists for sharing data. In a recent project, we added an exception to allow users to share Outlook attachments to the Salesforce app. This was necessary because Salesforce is not yet an Intune MAM-managed app. The exception allowed Outlook to work with Salesforce.
In Figures 3 and 4, you can see the difference between the sharing experience from Outlook Mobile. Figure 3 is before the policy applies and uses the native OS sharing experience. Figure 4 shows the effects of applying the policy; the user sees a custom sharing experience that only allows managed apps.
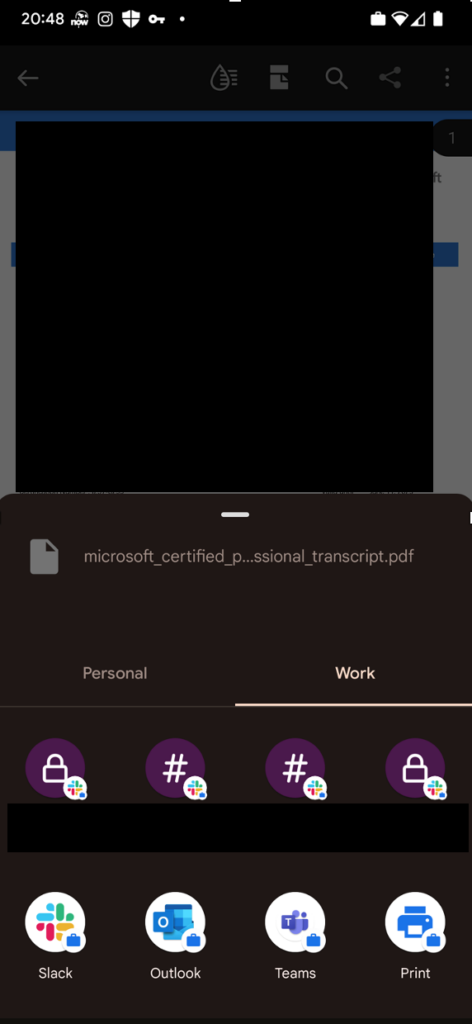
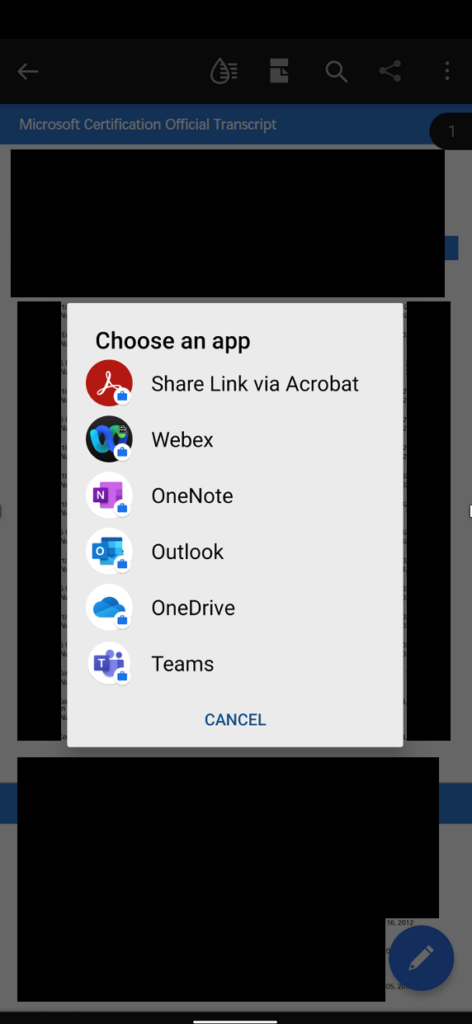
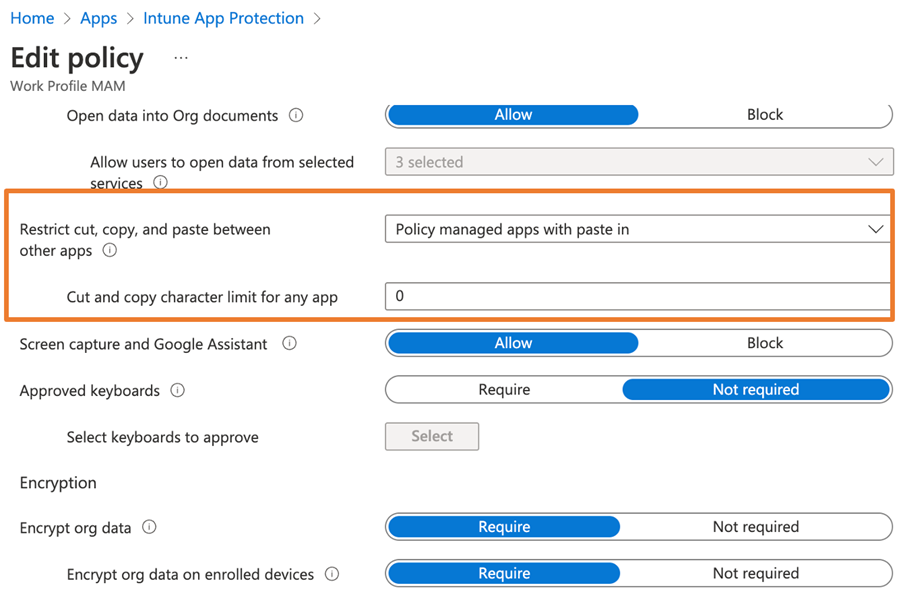
Control Copy and Paste from Outlook
You can also control the copy and paste features between mobile apps to prevent users from sharing data in other applications (i.e., WhatsApp). Most of my clients choose the setting as shown in Figure 5 to allow copy and paste between managed apps but also allow data copied from third-party apps to paste into managed apps like Outlook.
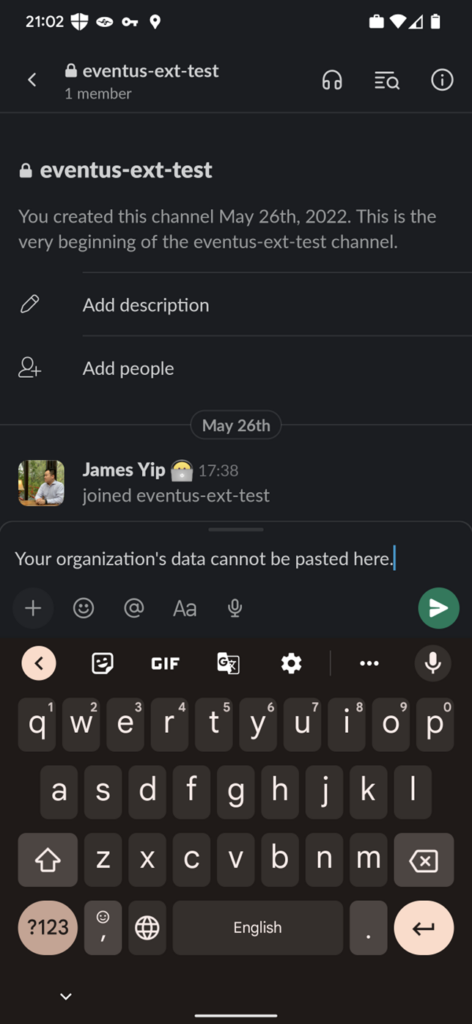
Once the policy applies, I am not able to paste data into Slack which I copied from Outlook mobile (Figure 6)
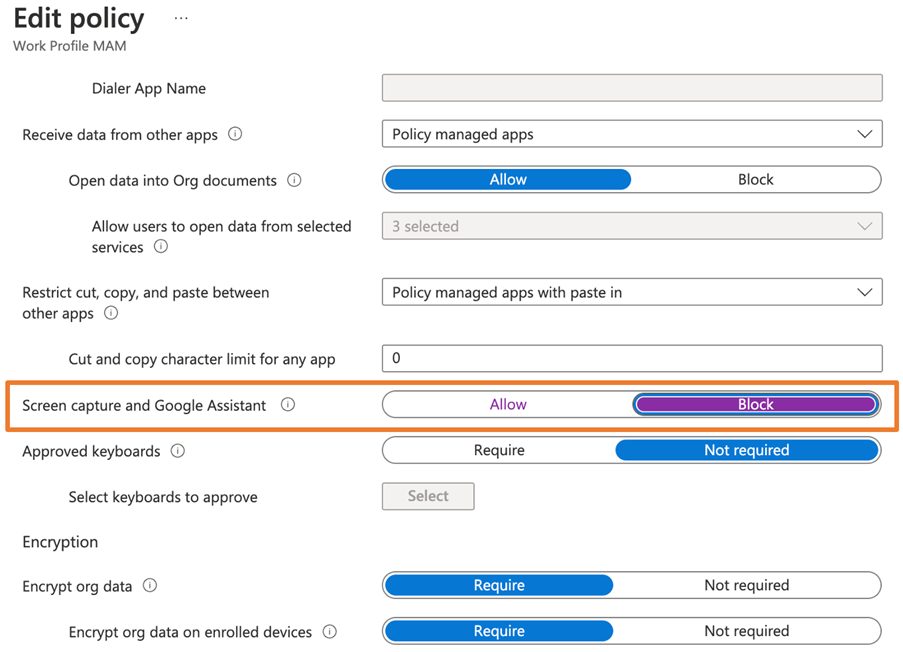
Android Only: Prevent Taking Screenshots in Outlook
Due to the need for the O/S to support an API, this policy only exists in Android. With this policy, you can prevent users from taking screenshots of the apps (see Figure 7). Note the key point: only the selected apps will be prevented from doing print screen. Other apps can still take a screenshot. This way, users can do a print screen of other apps, like WhatsApp, but cannot take a print screen of Outlook mobile.
iOS does support blocking print screen, but it requires MDM support, and it blocks this functionality across the entire device. This often generates complaints from end-users as many want to use screenshots for communications. We only deploy this capability when the iOS devices serve a specialized function, like confidential devices for government officials.
Microsoft Teams supports screen sharing. We often use this capability during support sessions to allow engineers to see the screen of the mobile device. However, if you enable screenshot blocking features, you cannot see the screen of managed apps like Outlook Mobile.
Bonus Track: Using Application Configuration Policy to Control Outlook Settings
Intune MAM is a great tool for protecting corporate data. There are a number of settings to tweak to get the right effect. However, Intune MAM also comes with a great tool called Application Configuration Policy which allows you to deploy configurations to supported apps and control the app behavior.
Every time I deploy Intune MAM, I ask my team to deploy at least one Application Configuration Policy to control the Outlook default signature setting. With the Application Configuration Policy, I can override the user settings and disable the default signature as seen in Figure 8.
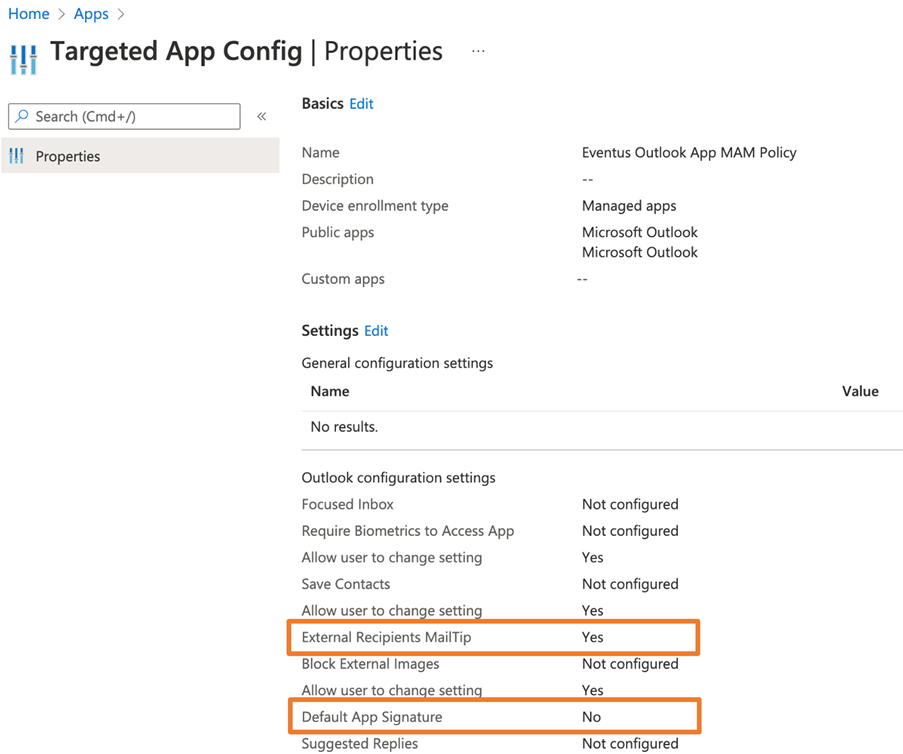
Another setting I often turn on is Enable External Recipients MailTip, a setting that cannot be enabled in Outlook mobile by users. This is a very handy feature that shows if the recipient is external to your tenant (see Figure 9).
Intune App Protection Policy within MAM is a Good Companion to Microsoft 365 Administrators
Intune MAM gives more control over corporate data and the behavior of mobile apps. I always encourage tenants to deploy MAM instead of MDM to gain greater flexibility and reduce the risk of accidental data wipes. If your tenant uses Intune MDM today, consider moving to Intune MAM to reduce the administrative overhead.
Top 10 Security Events to Monitor in Azure Active Directory and Office 365
Discover how native auditing tools can help — and how to overcome their shortcomings.



Android and iOS MAM protection policies appear to be enforced on devices without the need for a Conditional Access Policy. Therefore, I wonder whether creating a Conditional Access Policy is necessary and if there are any advantages to doing so.
Hello,
We want to block users to sign into iOS Mobile device for which they have not been assigned.
I mean User can only login with their Work/School account for their assigned iOS mobile and not in other User’s Phone.
For Example . What will happen if the the Device is complaint and assigned to UserA , But UserB also in same Company and try to login to UserA’s Device ? Is this Possible to block using Intune or any other Policy ?
Thank you.
Any suggestions on how to get a Windows device to use an application protection policy for other apps besides EDGE that is getting blocked by conditional access policy when requiring CAP?
Android requires Intune Company Portal app as broker app…..Authenticator not supported as broker app on Android.
Would you recommend App Protection Policies for laptops as well?
I have a problem “this action is not autorized by your organization” whan i thy to share a file since gallery to outlook
Hi James,
One thing I notice with App PP is when on Android BYOD adding a corp account, all of the photos are getting synced, even though the settings on Android “Camera Backup” show saying “Other accounts are not eligible”.
Example:
I have a personal OneDrive on Android > I will add a Corp account to the OneDrive app > It will ask me to enable backup, I will skip that > I will take a photo on BYOD device > The photo will get sent/synced to my corp OneDrive 🙁 … We can repro those steps on 10 test devices… Pixel 7 PRO and Samsung Galaxy 22 ultra…
Great article, thanks for the excellent write-up. Trying to decide between MDM and MAM right now actually.
Very nice article. Did you know how to audit the corporate data used in Whatsapp when we deploy app as managed app. We need to allow some users to copy past corporate data to whatsapp for some customers, but we want to have a way to audit which info is being sent over whatsapp managed app. Is there a way to do this ? Thank you
Nice article, thanks!