I’ve had a Mac since the launch of the original Macintosh in 1984, 40+ years ago. While I know and use Windows server and desktop systems, I’m also comfortable with macOS and iOS; in fact, most of my daily work is done on macOS. Microsoft has invested a lot of time and effort into making macOS, iOS, iPadOS, and even visionOS devices manageable with Intune and Entra ID. The latest example of this investment is the Enterprise SSO plug-in for macOS. This plug-in is meant to enable Windows-style single sign-on (SSO) for macOS devices and applications. In this article, I’ll walk through the process I used to set up SSO on my six-year-old Mac mini, running macOS 14.4.1 (the latest version as of this writing), with this plugin. This article assumes that you have some basic Intune knowledge, as it depends on using Intune features.
A Few macOS Basics
Every macOS device has a local account created when the device is set up. The vast majority of users only have this local account, because when the device is first configured that local account will be given local administrator privileges. Credentials for local accounts are stored in a keychain, which on modern Macs (those made since 2020 or so) is protected by a piece of security hardware known as the Secure Enclave. You can think of the Enclave as analogous to (although more powerful in many ways than) the TPM chip in most modern Windows machines. On devices that have facial or fingerprint biometric readers, biometric signatures are securely stored in the Enclave so they can’t be extracted. Applications can use OS-level services to securely store data in the Enclave too, or to ask it to perform cryptographic operations.
It’s easy to set up multiple user accounts, which work very much as local accounts on Windows do, but there’s no native concept of signing in the way we’re used to on Windows. Instead, most macOS users sign in to the local account; when they use applications or websites that require login to Entra ID, they type in their Entra ID credentials. Compared to the easy and seamless sign-in process you can get from a domain-joined Windows device, this process is a little clunky. The point behind the Enterprise SSO plug-in is to fix this clunkiness and give the end user a number of desirable features:
- The user can join a macOS device to an Entra ID tenant. This fundamental capability is what enables all of the other features listed below.
- The user can sign into the device using only an Entra ID credential. Microsoft and Apple refer to this feature as “platform SSO” but they have slightly different descriptions. To Microsoft “platform SSO” means “you can sign in with Entra ID.” To Apple, “platform SSO” means that you can sign in with any of several solutions, some of which have capabilities Microsoft doesn’t yet support. Either way, with platform SSO, the actual sign-in is performed using a cryptographic key which is bound to the device and stored in the Secure Enclave.
- The user can sign into the device using an external smartcard or FIDO2 token (Microsoft specifically mentions Yubikey tokens). In this mode, the external token holds the cryptographic key used for sign-in to Entra, and the Microsoft plug-in handles SSO for application sign-in.
- The user can synchronize their local account password with their Entra ID password. In this mode, reminiscent of early Windows networking, the local machine password’s hash is replaced by the plugin with the hash from Entra ID; the actual password itself isn’t copied.
This is a pretty extensive feature set for something labeled merely as a “plug-in.” In order to deliver these features, Microsoft had to wait for Apple to release its own OS-level mechanism for supporting enterprise SSO. That mechanism actually supports SSO for Entra ID through this plug-in and SSO for on-premises Active Directory through a separate Kerberos plugin (which is probably a topic for another day). The Entra ID plugin requires you to install the Entra Company Portal app, as you would for any Intune-managed device, which (through a mechanism I describe below) will install the plug-in. There’s also a separate plug-in required if you want Entra ID SSO to work in Google Chrome, but I won’t cover that here.
Step 0: The Prerequisites
If you’re just playing with SSO, you might be tempted to skip this section, and in fact you probably can. However, when you’re piloting or deploying macOS SSO there are some prerequisites you need to be aware of, as detailed here. Basically, your macOS devices must be running macOS 13.0 or later (to use Platform SSO, anyway; macOS 10.15 or later will work for application-only SSO); the devices need to be able to reach a specific set of Microsoft and Apple URLs, and those URLs need to be excluded from any TLS inspection systems on your network.
If you haven’t already enrolled at least one macOS device in Intune or one of Apple’s bulk enrollment tools, there is a separate set of prerequisites you’ll need to meet, including installing an MDM push certificate. For my tests, it was sufficient to create a device enrollment policy for my devices (which are all BYOD by definition). Verify that device enrollment works properly before proceeding or you will have a difficult and painful time ahead.
Step 1: Create an Intune Management Profile
The Company Portal app downloads and enforces Intune device management profiles. In some places Microsoft calls these “device profiles”, and in others they use the term “management profiles.” Either way, the device management profile is a blob of settings metadata that the client device downloads and parses to know what policy settings are supposed to be applied.
- Log in to the Intune portal (https://intune.microsoft.com)
- In the left navigation rail, choose Devices, then choose Configuration.
- Click Create > New Policy. Choose macOS from the Platform dropdown, then choose Settings catalog as the profile type, then choose Create. (Note that you may be tempted to choose the template that exists for SSO—don’t, because that template doesn’t yet contain the settings required to make Platform SSO work.)
- Give the profile a name and description when prompted.
- In Configuration settings, choose Add settings, then choose Authentication > Extensible Single Sign On (SSO).
- At this point, you’ll need to select several settings from the catalog and give them specific values. Because I expect Microsoft to update these settings as they evolve the plug-in, rather than repeat them here I’ll refer you to step 7 in the Microsoft documentation. Figure 1 shows the settings in place in the profile.
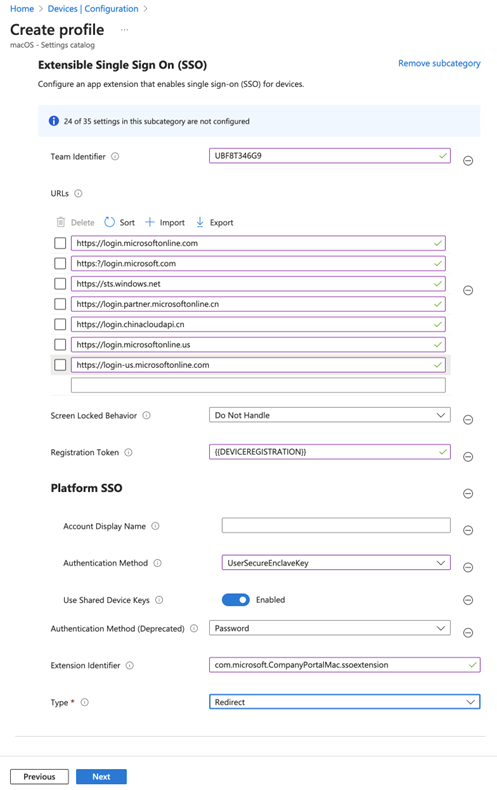
7. Optionally, you can assign scope tags to the profile. When you’re done, click Next.
8. You must assign the profile to users—you cannot currently assign SSO functionality to a device. In the Assignments tab, choose the users and groups to whom you want to assign the policy, then click Next.
9. Click Create to actually create the policy.
Once the profile has been created, you can start installing it on the target devices.
Step 2: Deploy the Company Portal app
However, macOS devices won’t just download Intune profiles on their own. For that, you need an app—specifically, the Company Portal app. Microsoft’s documentation covers multiple methods for installing the app. Sadly, you can’t use Intune to install the app unless the target device is already enrolled in Intune! To bootstrap an installation, you can either have users download the app themselves or package it for distribution using a macOS shell script. (Intune can distribute and run shell scripts too, but only on enrolled machines.) Installing the app is simple: go to Microsoft’s download site, download the app, and, when prompted, grant admin privileges to the installer. The installer emplaces a universal binary that runs on x86 or Apple Silicon devices, and installation doesn’t require a reboot. After installing the app, open it from the Applications folder and sign in using the Entra ID account for the device’s user. You’ll be prompted to allow the Company Portal app to use the device’s keychain with a dialog like the one in Figure 2. Be sure to click “Always Allow” unless you want to be reprompted for access at odd and unpredictable times.
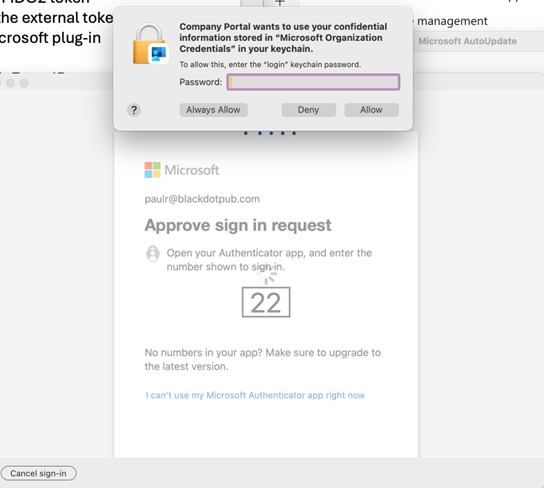
Once you launch the Company Portal app, you’ll see a fairly uninteresting wizard-like interface (Figure 3). You have to click the Begin button to start the enrollment process; after some preflight checks, you’ll see another wizard page with a button labeled Download profile. It’s important to understand that Intune won’t take any action on the device until you click this button.
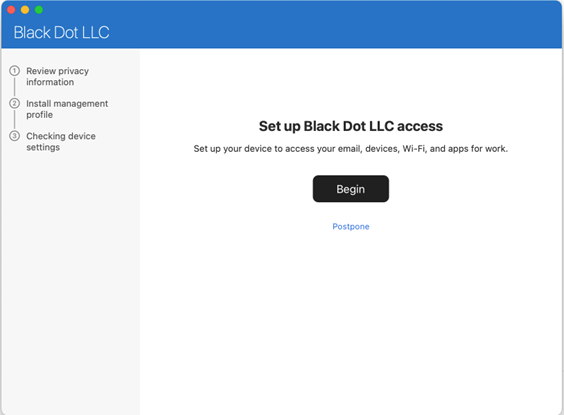
Once you click “Begin” you’ll see another wizard page with a Download profile button. Click it, and the device management profile should automatically be downloaded and installed. However, the profile won’t be active until you open it and approve its installation by entering a local admin account’s credentials. Once the profile has been downloaded and installed correctly, you’ll see something similar to Figure 4 when you look at the Profiles list in macOS.
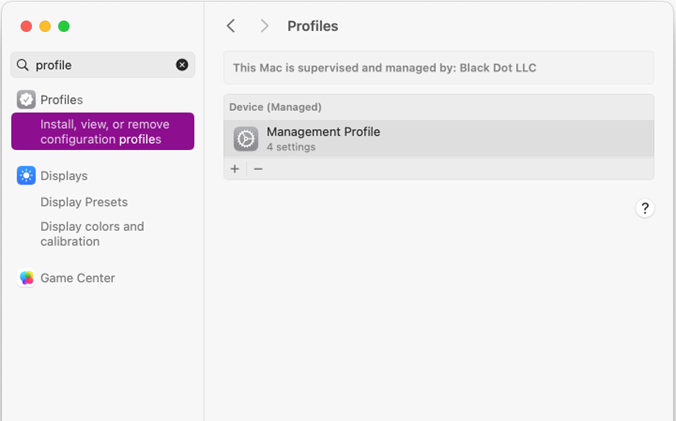
At this point, you’ll need to wait for the Company Portal app to download and apply the policy settings. This may take anywhere from a few minutes to a few hours.
Step 3: Registering for SSO
Once the Company Portal app has downloaded the configuration profile you created, you’ll see a macOS notification labeled “Registration required” in the system Notification Center. Unless and until you see this, you can’t proceed with SSO enablement. When you click on that notification, you’ll be prompted to sign in with your Entra ID account; when you do you’ll see a dialog notifying you that the device is being registered.
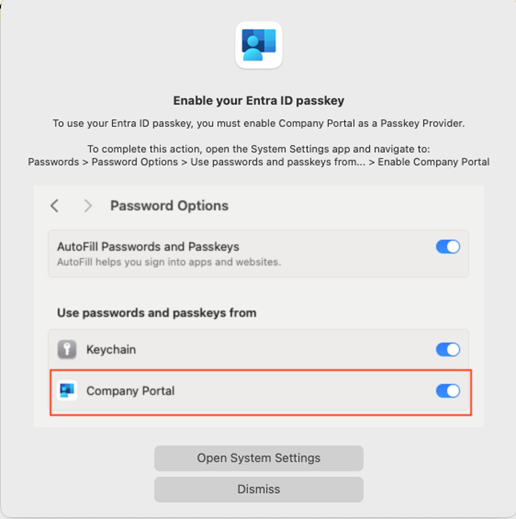
After registration completes, Intune will download and apply device configuration profiles, including the one you created to apply SSO. As part of that process, if your policy allows the use of passkeys, you’ll see an additional dialog telling you to enable the Company Portal app as a passkey source. To do this:
- Open the macOS System Settings app
- Go to Passwords > Password Options
- Make sure the toggle next to “Company Portal” is set to the on position, as shown in
Figure 5.
As part of the registration process, you may be asked to change your local machine password; if this happens, you’ll see the standard macOS password change dialog.
Step 4: Testing
By default, when the Platform SSO payload is installed, you get SSO capability available for Safari, plus any applications that use the Microsoft ADAL library. A simple way to test this is to open Safari and go to microsoft365.com. If you’ve correctly configured everything, you’ll be able to sign in without having to enter your credentials. Once you’re confident that that works, you should then proceed to test the Office applications, although this can be tricky since you may have lingering tokens from previous logins. You may need to forcibly sign out of the individual Office apps before leveraging SSO.
As I mentioned earlier, if you’re using Google Chrome, you can use Platform SSO on websites there too, but you’ll need to download and install the Chrome Platform SSO extension.
The Future of Enterprise SSO
Right now, the Enterprise SSO feature works pretty well. It of course has dependencies on MDM, which means you’ll need to manage your macOS devices using Intune or Jamf in order to effectively deploy it. This isn’t necessarily an obstacle, since Enterprise SSO is primarily useful in the kinds of enterprises that are likely to have deployed mobile device management already. Because the feature’s currently in public preview, you should expect it to change and evolve somewhat; Microsoft hasn’t yet set any public GA dates so you have some time to test it in your environment and decide how it fits into your macOS users’ workflow and your overall Entra ID deployment strategy.




