The Need to Understand Group Use
Managing a Microsoft cloud environment can be a challenging and complex responsibility for administrators. Making sure that the tenant operates smoothly requires a good understanding of configurations and applications across Microsoft 365. Entra groups are used extensively across Microsoft 365 services, making it important to know what each group is used for. While administrators in small tenants might be able to remember the purpose and assignments of each group, those in larger tenants must deal with multiple administrators and teams within the organization working with groups, which makes it more challenging to ensure the effective use of groups.
Risks of Mismanaged Groups
The unconsidered use or assignment of groups in a Microsoft 365 tenant can lead to unexpected consequences. Without a clear understanding of each group’s purpose, administrators risk unintended impacts on users or groups of users. This can result in operational disruptions and potential security impacts for the users and the organization, especially when groups are used with services like Conditional Access or Intune policies.
The exact impact of adding or removing users from a group depends on tenant policies and configuration. Here are a few examples of unexpected impacts that could result from such changes:
- A user is added to a test group
- A user is excluded from having a compliant Intune device
- A user can access a restricted Service Principal
- A user is allowed to use a USB storage device
- A user has access to sensitive data in a SharePoint site
- A user is excluded from MFA
Documentation of each group’s purpose and clear communication within and between teams are essential. Without these practices, the risk of unintended consequences increases, making it more challenging to manage and secure a Microsoft 365 environment effectively.
Where is this Entra Group Used?
To address these challenges, I developed the Microsoft Cloud Group Analyzer (Figure 1). This tool provides detailed insights into Entra group usage by reporting the policies, services, and configurations associated with a specified group identifier. Additionally, the tool can perform a full scan of all Entra group assignments, giving administrators additional insights and documentation to help manage their environments.

A Real-World Example
In my role as a consultant, I have encountered multiple issues resulting from group misuse, but I’ll detail one specific case.
At an organization with around 5,000 employees, we experienced several incidents over a two-month period. Unauthorized users were added to pilot tests, developers were excluded from MFA, and users were accidentally given access to SharePoint sites containing sensitive files.
These incidents were caused because not all administrators of the IT team were aware of the purpose of each group or its usage across other Microsoft 365 services. So, the admins added users to groups and assigned groups to policies without knowing the full context of a group’s purpose. These incidents were escalated to the business side of the organization, causing concerns about the IT department’s organization and effectiveness.
To prevent similar incidents, we implemented the Group Analyzer, which I had already developed by then. This tool provided the IT team with documentation of group usage, allowing admins to verify a group’s assignments before making any changes. This gave the administrators more confidence in their tasks and lowered the risk of unwanted impact. Unlike manual documentation, which is time-consuming and becomes quickly outdated, the Group Analyzer offers real-time, accurate information. With this documentation, the IT department reduced the amount of similar conflicts, thereby restoring confidence in the IT department’s capabilities.
Using the Group Analyzer
The Group Analyzer was initially developed in Node.js to support its launch as a closed-source Software as a Service (SaaS). Node.js was chosen because it is a suitable framework and language for back-end and front-end development. However, my commitment to open-source software and contributing to the Microsoft 365 community led to the decision to open-source the tool. While Node.js might be a less common language for administrators compared to PowerShell, there are future considerations for a PowerShell version.
To run the Group Analyzer tool, Node.js, and an Entra App Registration are required to connect to the tenant, as detailed in the setup guide. After completing these steps, follow the instructions below to download and install the tool.
From the Windows, Mac, or Linux terminal, clone the GitHub repository:
git clone https://github.com/jasperbaes/Microsoft-Cloud-Group-Analyzer.git
Navigate to the cloned directory and install the necessary packages:
cd ./Microsoft-Cloud-Group-Analyzer npm install
Before running the script, specify the details of the Entra App Registration in the .env file (setup guide).
CLIENTSECRET=<app secret> TENANTID=<your tenant ID> CLIENTID=<app registration ID>
The script can be executed on three targets:
- On a group: the report details the assignments for this Entra group.
- On a user: the report details the assignments for the Entra groups the specified user is a member of.
- On all groups: the report details the assignments of all Entra groups.
Examples:
node index.js <group ID> node index.js <user ID> node index.js all
The Group Analyzer supports the following group types: security groups, Microsoft 365 groups, mail-enabled security groups, and distribution groups. Dynamic distribution groups are not supported.
The results of the script are displayed in the terminal (Figure 2), and a webpage with visual results (Figure 1) is automatically opened in the browser. To save the report as a PDF file, the shortcut CTR + P (Windows) or ⌘ + P (Mac) can be used in most browsers.
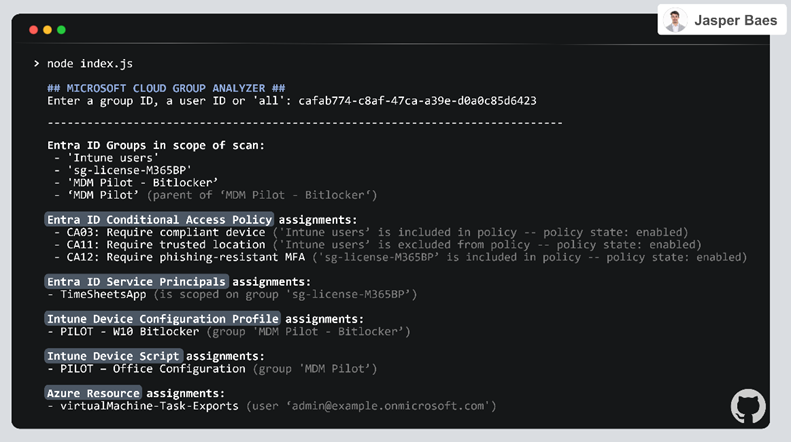
The output can be saved to JSON or CSV formats by adding the following parameters:
node index.js --export-json node index.js --export-csv
When running scans, several parameters can be adjusted to customize the process. These include options to disable the web report output, skip a specified number of groups, limit the number of groups within the scan’s scope, and generate debug logs. Parameters can be combined. Below are examples of how to use these parameters:
node index.js <group ID> --cli-only node index.js <group ID> --skip 10 node index.js <group ID> --limit 5 node index.js <group ID> --debug
The Group Analyzer can be used in several ways: ad hoc when a need exists to check where a specific Entra group is used, or the Group Analyzer tool can be run periodically for all Entra groups. Weekly or monthly reports allow for quickly tracking group assignments and are useful for IAM documentation, periodic reviews, or incident response purposes.
The Group Analyzer features local caching for each Microsoft Graph API call and processes tasks in batches of 10.
Processing 1,000 groups with the Group Analyzer takes an average of 2 minutes. For a tenant with 10,000 groups, the total processing time is approximately 20 minutes. The Group Analyzer scans 19 separate configurations for Microsoft 365 tenants. Therefore, for 1,000 groups, the tool runs 19,000 small scripts within the Group Analyzer tool, each making at least one Microsoft Graph API call.
Overview is Key
The Microsoft Cloud Group Analyzer offers administrators a clear detailed view of group assignments. This tool can help maintain control over complex Microsoft 365 environments and reduce the risk associated with adding or removing users from a group.




This should be a great way to see dependencies on groups, to know if it is safe to delete or otherwise modify them. Great work thank you for your contribution!
I got it up and running in less than 10 minutes and this is amazing data, thanks again!