Figuring Out How to Control App Access in a Microsoft 365 Tenant
I recently received an email from a reader of the Automating Microsoft 365 with PowerShell eBook about an interesting article they’d read titled Simple role based authorization with Microsoft Entra ID in ASP.NET Core using App Roles. The question flowing from the article is what’s the best way to control access to Entra ID apps to prevent unauthorized users from running those apps. Given the increasing number of apps found in most Microsoft 365 tenants, it’s a fair and obvious question to ask.
App Assignments
By default, any account can run the apps defined in Entra ID within a tenant. If you don’t want people to access apps, you must restrict access. To control user access to an app, the usual approach is to require assignment to access an app. Quite literally, an assignment grants a user account access to an app. Assignments are supported for both tenant apps and enterprise apps.
Assignments can be granted on an individual account or group basis with the proviso that group-based assignments require Entra ID P1 or P2 licenses. When a user account receives either a user or group-based assignment, the app shows up on their My apps dashboard (Figure 1).
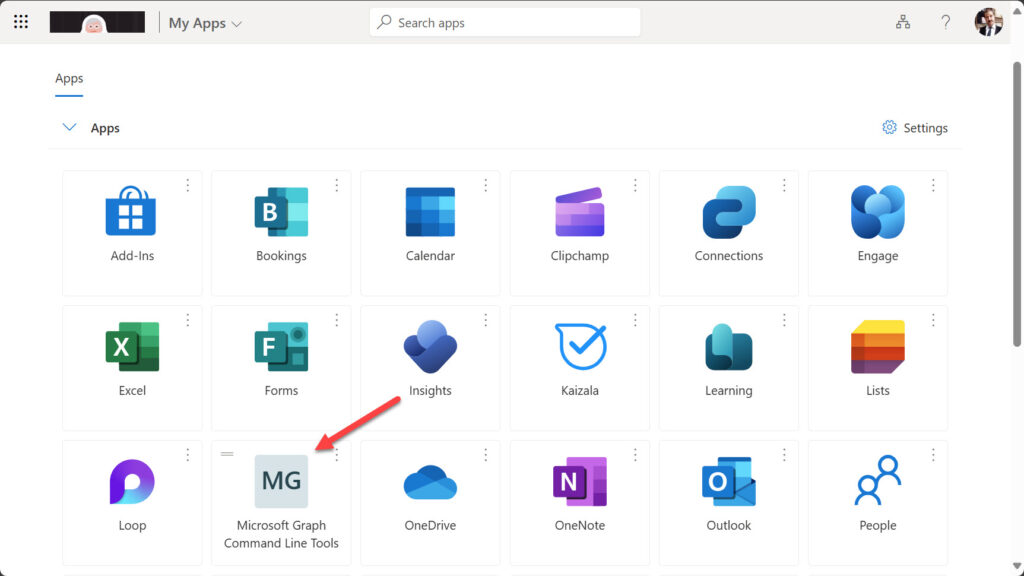
Clicking an app in the app dashboard invokes its homepage URL. In the case of the Microsoft Graph Command Line Tools app, that URL is the Get Started page for the Microsoft Graph PowerShell SDK.
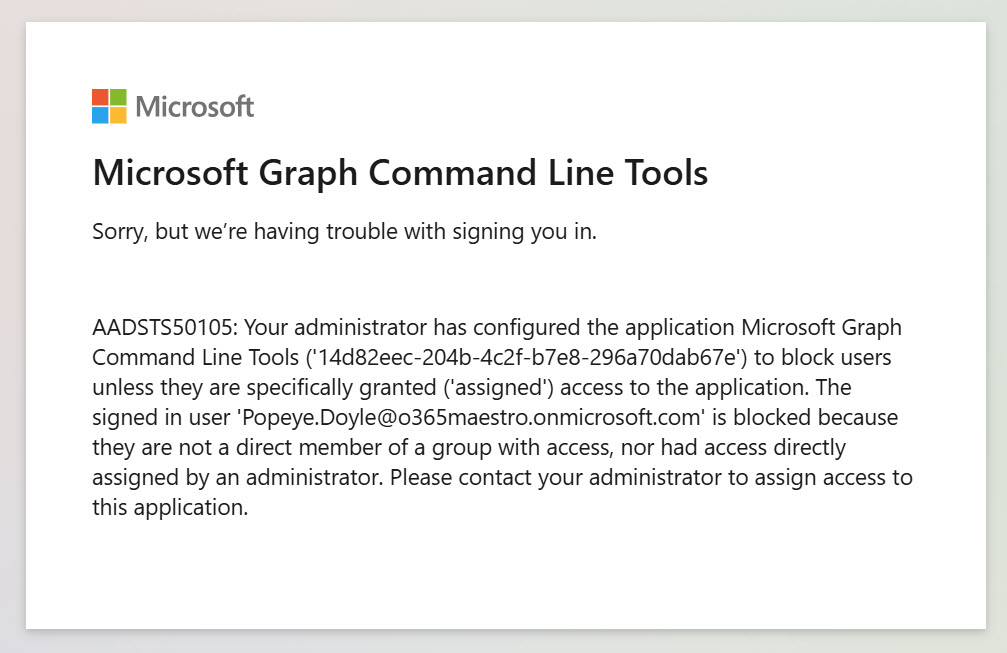
Assignments work well to stop unauthorized users from having interactive access to apps. For instance, you can create assignments to restrict interactive sessions with the Microsoft Graph PowerShell SDK. Failure to be on the list of assignments means that anyone attempting to run the Connect-MgGraph cmdlet gets an AADSTS50105 error (Figure 2).
Third-Party Apps Have Different Needs
User and group assignments are not so good when third-party apps use the Microsoft Identity Platform for authentication and must then need to distinguish between different levels of access that can be granted to users. For instance, one user might have administrator access when working with an app while others enjoy only read-only access.
This is where Entra ID RBAC custom app roles, a relatively new facility, come in. Custom app roles are specific to an app. It’s up to the app to define how many roles it needs. Once created, app roles can be granted to user accounts or to the service principals for other apps. In fact, a custom app role can be configured to be available for both users and service principles. In all cases, when Entra ID issues an access token after successful authentication, the roles are included in the claims in the token to allow third-party platforms to decide what level of access to grant for an app. Custom app roles can only be created and assigned for apps registered in the tenant. They can’t be created for enterprise apps.
Custom app roles have full Graph API coverage through the appRoleAssignments and the appRole resources and their associated methods.
Don’t Mix App Assignments and Custom App Roles
The simple rule is that you should not mix app assignments and custom app roles for a single app. If you create a custom app role for an app, you’ll no longer be able to make app assignments. Existing assignments will continue to work, but new assignments are impossible through either the Entra admin center or Graph API. The reason is that app assignments depend on a hidden default role called ‘Default Access’ with an identifier of 00000000-0000-0000-0000-000000000000. When custom app roles are used with an app, any role assigned to a user or group must be defined for the app. The Default Access role is not defined, so it can no longer be assigned.
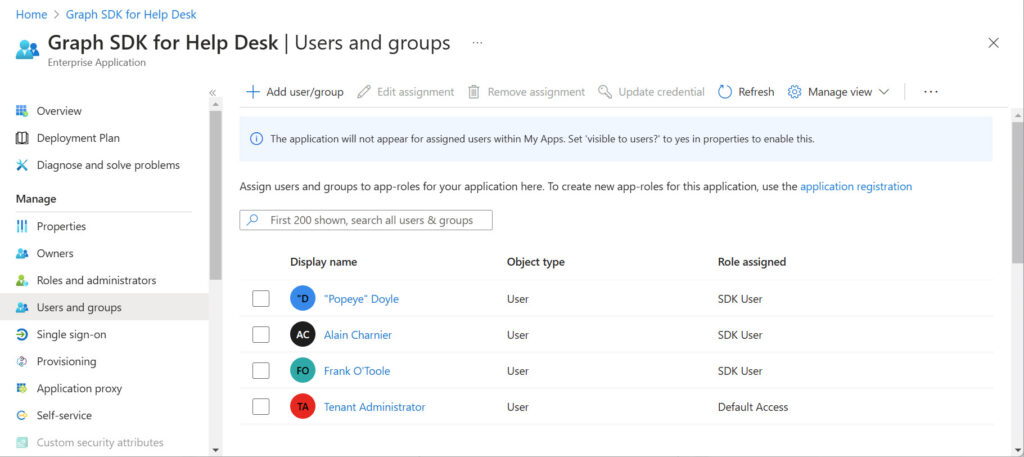
Take Figure 3 for an example. All apps have a default assignment for the account used to create the app. Here, the assignment is for the tenant administrator account. The other three assignments are custom app role assignments.
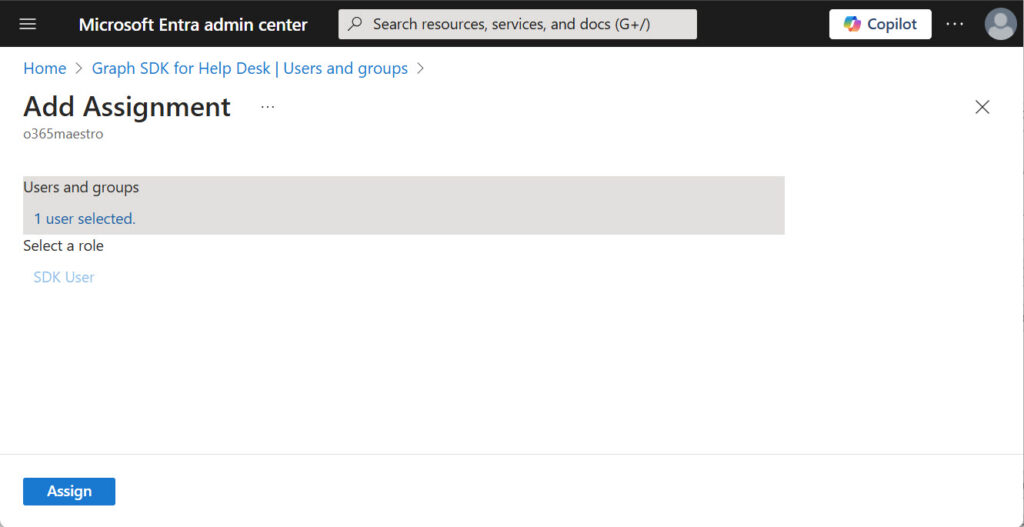
Any attempt to make a user or group assignment through the Entra admin center fails. The GUI only supports the assignment of custom app roles (Figure 4).
Unless you’re very proficient with app roles, I recommend that you use the Entra admin center to manage custom app roles. However, sometimes we can gain extra insight by looking behind the scenes. To see the assignments for an app, we can use an interactive Microsoft Graph PowerShell SDK session with the AppRoleAssignment.ReadWrite.All and Directory.Read.All scopes. Here’s what is revealed for app assignments after fetching the service principal for the app and using its identifier to find the set of role assignments for the app.
$GraphApp = Get-MgServicePrincipal -filter "displayname eq 'Graph SDK for Help Desk'" $GraphApp | Format-Table DisplayName, Id, AppId DisplayName Id AppId ----------- -- ----- Graph SDK for Help Desk 9ab45c18-7e3f-45bc-9f73-d034fb30cdf0 14d82eec-204b-4c2f-b7e8-296a70dab67e $Assignees = Get-MgServicePrincipalAppRoleAssignedTo -ServicePrincipalId $GraphApp.Id $Assignees | Format-Table CreatedDateTime, PrincipalDisplayName, AppRoleId, Id CreatedDateTime PrincipalDisplayName AppRoleId --------------- -------------------- --------- 05/01/2025 21:52:34 Alain Charnier 8c6f5dd0-86a9-4cb5-9e41-17619c6490fe 05/01/2025 21:52:34 Frank O'Toole 8c6f5dd0-86a9-4cb5-9e41-17619c6490fe 05/01/2025 19:27:02 "Popeye" Doyle 8c6f5dd0-86a9-4cb5-9e41-17619c6490fe 05/01/2025 19:25:21 Tenant Administrator 00000000-0000-0000-0000-000000000000
In the set of role assignments, we once again have the default access role for the tenant administrator account and the custom app role assignments for the other three accounts. The identifier used for a custom app role is assigned during the creation of the role. This example shows how to create two app roles for an app. Both roles are enabled so they can be used immediately.
Reverting Apps to User and Group Assignments
To revert an app to use user and group assignments, delete any custom app roles. At that point, you can add assignments through the Entra admin center or with PowerShell. Remember that all assignments are made using the app’s service principal because the service principal is the object that holds the app permissions:
$SP = Get-MgServicePrincipal -Filter "DisplayName eq 'PlannerReport'" $DefaultRoleId = ‘00000000-0000-0000-0000-000000000000’ $User = Get-MgUser -UserId Popeye.Doyle@office365itpros.com New-MgUserAppRoleAssignment -UserId $User.Id -AppRoleId $DefaultRoleId -PrincipalId $User.Id -ResourceId $SP.Id
The lesson here is to only use custom app roles when you’re in complete charge of an app’s development and can dictate what the app code will do. User and group assignments simply cover access to an app, not what happens when someone runs an app.
Entitlement Management
If your tenant has Entra ID P2 or Entra ID Governance licenses, you can use Entitlement Management access packages to control access to apps. Access packages are a more flexible way to manage assignments for apps than direct user or group assignments and include features like time-limited assignments and access reviews. Entitlement Management can grant access to resources based on values in Entra ID account properties like a department. Access packages do more than manage app assignments; they also include resources like SharePoint sites and Teams.
If you work in a large tenant, Entitlement Management is definitely something to consider. And even if you don’t work in a large tenant, read Vasil’s series about Entitlement Management to help figure out if this capability can do a job for your organization.
Control Access to Entra ID Apps
Outside full-blown entitlement management, direct user or group assignments are a binary control for user access to Entra ID apps while custom app roles are for apps to know what access a user has when they run an app. From the perspective of tenant administrators, you’ll find that direct assignments are more useful because they work out of the box without needing any bespoke code. Developers will take the opposite view because custom app roles give them the flexibility to segregate app functionality depending on the role a user has. Both approaches are valuable, provided they’re used correctly.




