This is the second iteration of a two-part blog series about FIDO2 and passwordless authentication, with the first part covering FIDO2.
Passwordless authentication reduces the risk of phishing and password spray attacks by removing the need to use traditional passwords. Users can authenticate up to 3x faster and helpdesks should receive fewer requests for password resets, saving the organization money.
First announced at the Microsoft Ignite conference in March 2021, passwordless authentication for Azure AD is globally available. You can deploy three different passwordless authentication methods for your Azure AD users:
- Windows Hello for Business (Platform Authenticator, hardware)
- Security key sign-in with FIDO2 security keys (Roaming Authenticator, hardware)
- Phone sign-in with the Microsoft Authenticator app (Roaming Authenticator, software)
Plan Your Passwordless Deployment
At first, it might sound counterintuitive to tell users they will be able to log in to their computers and Microsoft 365 services without a password. Rest assured, the FIDO2 standard withstands the most common threats to authentication methods. To test the waters, you should include the use of USB tokens in proof-of-concept projects to understand if passwordless authentication is achievable. Sometimes, due to regulatory or legal restrictions, companies are unable to use USB hardware, or USB ports must be disabled.
First, you’ll want to get an idea of what your rollout will look like for scaling and planning purposes. Luckily, Microsoft includes the passwordless wizard in the Microsoft 365 admin center to help organizations determine which devices and passwordless authentication methods best fit their infrastructure and needs:
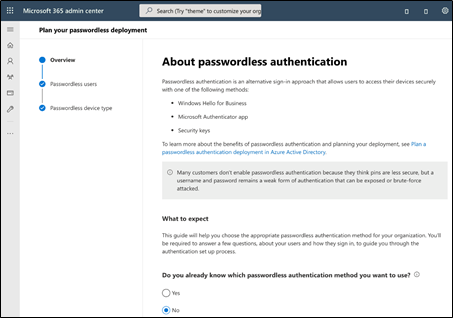
For example, if your users have PCs with biometric hardware, they can use Windows Hello for Business and leverage single sign-on capabilities for their local and cloud-based resources. The wizard covers all kinds of your identities, such as Frontline workers who have their own devices or identities that share the same hardware at work. You can choose the best method that suits your organizational needs, and from there you’ll also receive recommendations on how to successfully launch this feature within your organization.
Aside from testing with a small group of trial users, communication is critical to the adoption and success of any new service. If needed, Microsoft does provide materials that will help draft your communications:
Enable Passwordless Authentication for Azure AD identities
Now that you’ve performed a device audit and determined your project scope with the passwordless wizard, you are ready to begin the process for Azure AD identities. Azure AD can use all certified FIDO2 devices and enable passwordless authentication across all services and applications connected to Azure AD as an Identity Provider (IdP).
Note: FIDO2 is backward compatible with U2F, which means that in general a FIDO2 authenticator can also be used as a pure MFA device. Unfortunately, Microsoft does not offer this option in Azure, which means that you can only use FIDO2 devices for passwordless authentication. Alternatively, the Microsoft Authenticator app can perform both MFA and passwordless authentication.
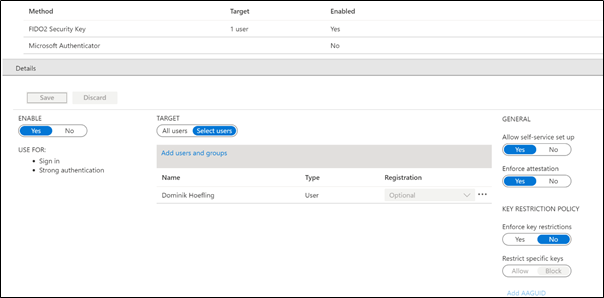
When you deploy passwordless authentication, you should first enable one or more pilot groups. You can either enable FIDO2 for a single user or a group of users, even if the group is synchronized from your on-premises Active Directory. Below is an example of how to enable FIDO2 for a single user:
*First, an administrator must enable the passwordless authentication option. This can be done for individual users, a group of users, or for all users:
- Sign in to the Azure AD admin center.
- Browse to Azure Active Directory > Security > Authentication methods > Authentication method policy.
- Under the method FIDO2 Security Key, choose the following options:
Enable – Yes or No
Target – All users or Select users - Save the configuration.
Once your users are enabled, they can set up their FIDO2 device by accessing the URL https://myprofile.microsoft.com. Registering the FIDO2 device is simple, and the process is similar to configuring MFA. If the FIDO2 device has additional biometric security, such as the fingerprint (which is stored exclusively on the device) this is also configured during setup. If the device does not have a biometric feature, a human presence is checked and verified with a simple gesture on the FIDO2 device.
Note: at the time of writing, there is no way for admins to pre-provision FIDO2 security keys for users.
Here’s how to set up a FIDO2 device:
- Browse to https://myprofile.microsoft.com.
- Click Security Info.
- If the user already has at least one Azure AD MFA method registered, they can immediately register a FIDO2 security key.
- If they don’t have at least one Azure AD MFA method registered, they must add one.
- Add a FIDO2 Security key by clicking Add method and choosing Security key.
- Choose USB device or NFC device.
- Have your key ready and choose Next.
- A box appears to ask the user to create/enter a PIN for your security key, then perform the required gesture for the key, either biometric or touch.
- The user is returned to the combined registration experience and asked to provide a meaningful name for the key so the user can identify which one if they have multiple. Click Next.
- Click Done to complete the process.
Monitoring and Auditing
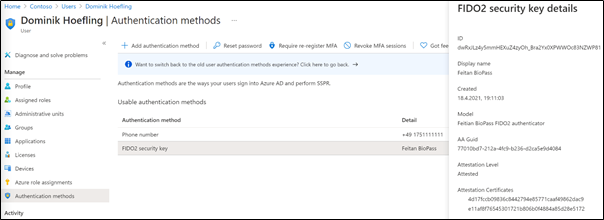
Now that your users have successfully completed the process, an administrator can check and verify all registered authentication methods of your users in the Azure AD admin center:
Azure AD includes reports that provide robust technical and business insights; you can and should monitor your pilot users to see if they had any issues during registration or authentication, and also determine if the login is working properly. The preview version of the authentication methods activity report offers you a modern diagram where you can get insights into all relevant reports. For example, Figure 4 shows the authentication method used in my tenant:
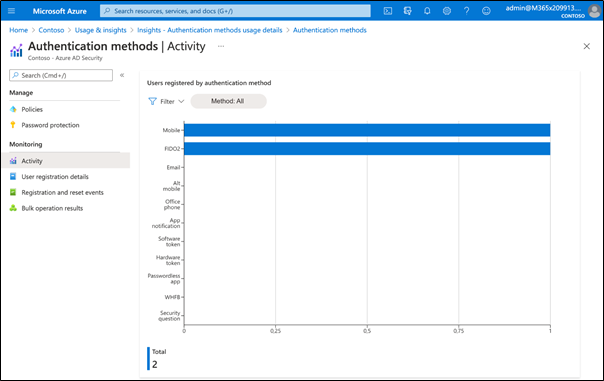
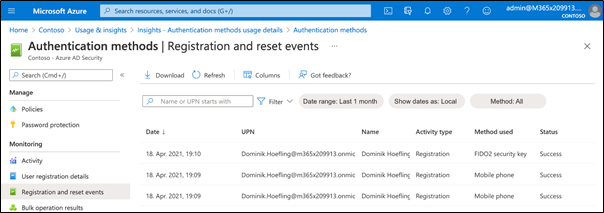
Registration and reset events will help you audit the registration process, and see if the registration of a FIDO2 security key was successful or not:
Manage methods using PowerShell
The Microsoft Graph PowerShell SDK includes cmdlets that allow administrators to manage authentication methods for users. Currently, you can get and delete FIDO2 authentication methods for users:
Install-module Microsoft.Graph.Identity.Signins
Connect-MgGraph -Scopes UserAuthenticationMethod.ReadWrite.All
Select-MgProfile -Name beta
Get-MgUserAuthenticationFido2Method -UserId Dominik.Hoefling@m365x209913.onmicrosoft.com | fl
AaGuid : 77010bd7-212a-4fc9-b236-d2ca5e9d4084
AttestationCertificates : {4d17fccb09836c8442794e85771caaf49862dac9, e11af8f76545301721b806b0f4884a85d28e5172}
AttestationLevel : attested
CreatedDateTime : 4/18/2021 5:11:03 PM
CreationDateTime : 4/18/2021 5:11:03 PM
DisplayName : Feitan BioPass
Id : dwRxJLz4y5mmHEXuZ4zyOh_Bra2Yx0XPWWOc83NZWP81
Model : Feitian BioPass FIDO2 authenticator
AdditionalProperties : {}
Additionally, you can also use Microsoft Graph to manage users’ authentication methods.
Handling Lost or Stolen FIDO2 Authenticators
Lost or stolen FIDO2 devices are in principle protected against unauthorized use. Depending on the device, the protection is either with a 6-digit PIN (which is mandatory for Azure AD), or with a biometric feature. Incidentally, this setting can be defined individually for each Relying Party and can therefore be handled differently by different providers. The device should be reported as lost or stolen as soon as possible so that the administrator can delete the device from Azure AD.
The W3C recommends registering a backup authenticator for each service or application, which does incur additional costs and requires re-registration with the service. If there are many services in use, re-registration can be time-consuming. However, an extension to the WebAuthn API describes a new prototype approach to account recovery. Essentially, the approach is to apply a key agreement scheme that allows a main and backup authenticator to agree on a common EC (elliptic curve) key pair. Only the backup authenticator can derive the private keys, and no additional registration with the backup authenticator needs to be performed. The backup authenticator should always be kept in a secure location.
Preview: Temporary Access Pass
One of the most frequently asked questions on this subject is, “how can organizations be truly passwordless and onboard new users without knowing a password?” The figure below shows Temporary Access Pass settings, which allow users to register a passwordless authentication method and recover access to their account without a password by first authenticating with a time-limited passcode. Instead of giving a temporary password to your users (to be changed after their first login), the passcode serves as a temporary password:

Once a user has a valid passcode, they can use it to sign in and register a FIDO2 device from the My Security Info page or register for passwordless authentication directly from the Authenticator app on their mobile phone.
Summary
The use of passwords for authentication to services has been a common and established method of protecting access to resources for decades. Users tend to use simple, easy-to-remember passwords, often taking words from other people’s environments or resorting to dictionaries. The use of Password Strength Meters and various mathematical measures have little impact on password security since the most common cause of password theft is phishing attacks and attacks on inadequately protected ISP systems.
The FIDO2 standard of the FIDO Alliance and the W3C is attractive for many reasons, the most important being it dramatically increases the security of AD authentication to services, while making it as convenient as possible for users. The automated key management by the Authenticator eliminates the need for time-consuming administration which can become costly for organizations. Additionally, research has shown that the FIDO2 standard withstands the most common threats to authentication methods, making it a worthy successor to the password. That being said, traditional authentication methods – first and foremost the password – will most likely remain in place for a long time.




Thanks for your greate blog. Is there any option to remove Passwords from Azure AD cloud only users?
It would be awesome if we could force users in a tenant to use Passwordless as part of a Conditional Access Policy
Hi,
is there any way that I can let users have FIDO keys as their only method of MFA? It doesn’t appear so. They always need to set another method such as SMS or call. I am getting a lot of resistance to using mobile numbers or indeed mobile phones at all.
From my findings, you will need to use a token that supports TOTP.
With conditional access a fido2 key is enough.
I do it this way: https://scloud.work/en/passwordless-security-key-microsoft-365/
Exactly, if I want to avoid the vector of password and authenticator and only rely on the FIDO key, which does not seem to be possible, then why bother with the security key (from a security perspective)? Is it only the Microsoft consumer accounts which supports true passwordless setup?