Some time ago I surveyed Practical 365 readers and learned that only around 40% of you have multi-factor authentication enabled for your administrative accounts. What was also interesting was that 20% of respondents have MFA enabled for both user and admin logins.
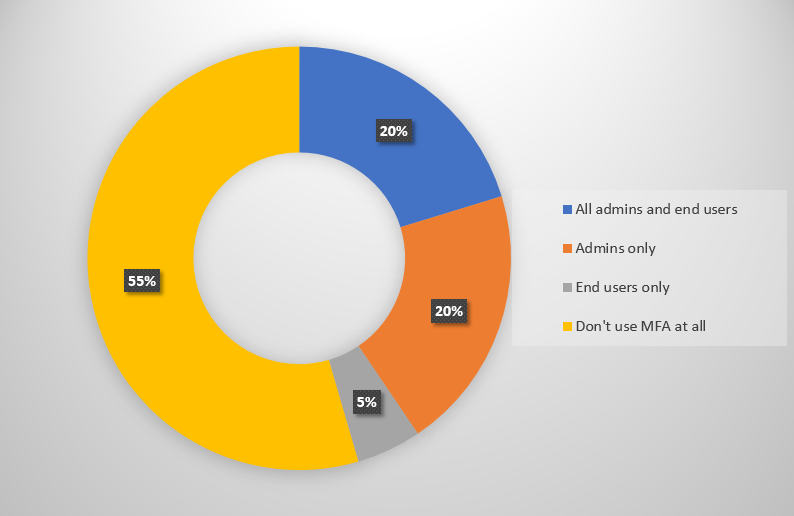
The number one reason that people give me for not enabling MFA is that is annoys their end users. Admins also used to complain about a lack of MFA support in the various PowerShell modules they use, but that is largely a solved problem now. The organizations that have rolled out MFA to their users also tend to be the ones that have reduced the annoyance factor for their users by allowing MFA bypass under some circumstances. Bypassing MFA for trusted network locations is common, as is bypassing MFA for trusted devices.
Those MFA bypasses would also typically apply to administrative logins, which is not ideal when those are the accounts that need protecting the most. A solution to overcome that problem is to create a conditional access policy in Azure AD that requires MFA for admin accounts. However, if you wanted to target a conditional access policy at all members of the Global Administrators group (as an example), you would need to create an additional security group in Azure AD that contained the same user accounts that are in the Global Administrators group. This duplication of effort obviously makes ongoing administration more difficult and error prone.
Now Microsoft has added new functionality to Azure Active Directory conditional access policies to allow targeting of policies to directory roles. This is currently in preview at the time I’m writing this blog post, and may change before it becomes generally available.
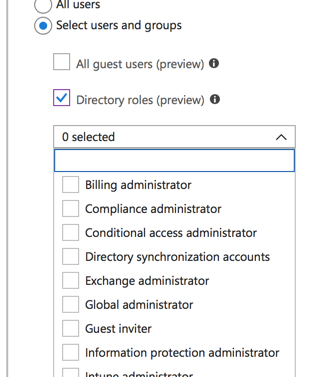
Let’s say you have an organization for which all users and admins are required to login with multi-factor authentication, unless they are logging in from a location or device that is able to bypass MFA. Prior to this change, you would need to target another conditional access rule at your admins to enforce MFA, which requires you to maintain a duplicate group of Global Administrator role members, as I mentioned earlier.
With the new functionality, you can create a conditional access policy targeted at the Global Administrators directory role, and require multi-factor authentication for login to whichever cloud apps or admin portals you wish to secure. You can select multiple directory roles in the same policy. In this example I’m only requiring MFA for Global Administrator logins, but you could choose to secure several other privileged roles as well.
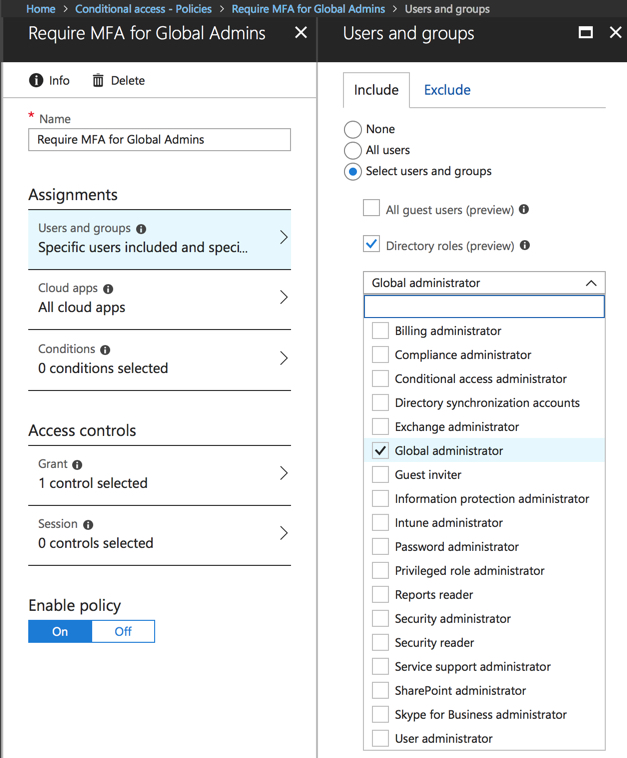
In the access controls for the policy, you can enforce the MFA requirement, and if you want to secure admin access even further you could require login from compliant devices and/or hybrid Azure AD joined computers. This could prevent administrators from logging in from untrusted devices (e.g. personal devices that aren’t enrolled in your MDM, or public internet computers). That is appealing to some customers, but others would want to be a little more relaxed about it. You can make your own decisions there.

This change to conditional access adds another nice layer of security to your admin access. If you combine it with Privileged Identity Management, where your admin users also need to authenticate with MFA when activating a privileged role, you can put up a lot of barriers between attackers and your admin accounts.
Photo by Derek Story on Unsplash



We also notice that “We don’t enable MFA but for any random user it forces ” browser asks More info required and next page only shows “Mobile app” drop down with no other choice?
What could cause this?
Simple user with Business Essentials
Disabled MFA many times but no luck..
Have you noticed that when enforcing MFA this way, it is not reflected within the O365 console? Users don’t seem to have the option to create App Passwords when MFA is enforced this way as well.
>Have you noticed that when enforcing MFA this way,it is not reflected within the O365 console?
When you enable MFA in office 356 it is effectively simple on / off switch for MFA on the account.
When you use conditional access it is not specific to the user, it can check all sorts of conditions to decide if MFA is required or not, eg is the user an administrator or in a certain group, what network or what type of device did they log on to, what application are they using, or where are they located etc.
Pingback: Multi-factor Authentication by Default for Administrators in Azure AD and Office 365 – SimpleITPro