Tips for using the Microsoft Defender for Endpoint for best results
With the recent addition of Microsoft Defender for Business to the Microsoft 365 Business Premium license, a lot of organizations have suddenly received the endpoint detection and response (EDR) capabilities of Microsoft Defender for Endpoint. I have seen organizations rolling out quickly after they got it for free in their licensing and have forgotten about it afterward.
What is important to know with a product such as Microsoft Defender for Endpoint, is that this is not a product you roll out and forget about it. To get the most out of a tool such as Defender for Endpoint you need to maintain it on a daily basis. In this blog, I will walk through some of the actions you should be doing to keep current with the product.
Setting up notifications
I recommend setting up email notifications right away. Microsoft Defender for Endpoint will generate events each day and it’s important to stay current. Setting up email notifications avoids the need to visit the portal manually to find out if there is anything new, you can set up email notifications for two categories:
Alerts
- When Microsoft Defender for Endpoint identifies a potential security risk on a device, it will generate an email notification alert.
Vulnerabilities
- Every day a new vulnerability is identified. This notification rule will generate an email notification when a new severity affecting your devices is identified.
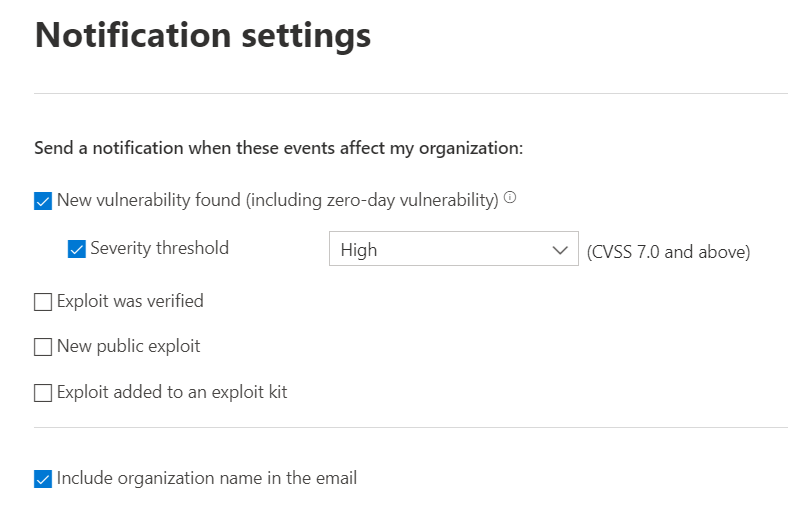
To set up email notifications navigate to the Microsoft 365 Defender portal and select Settings > Endpoints > Email Notifications.
I recommend setting up filters for email notifications based on the severity of the incident. Vulnerability severity is ranked from 0.0 for the lowest risk to 10.0 as the most severe. I suggest configuring notifications for all vulnerabilities which have a severity of 7.0 or higher. By setting up a severity range, you will receive a “manageable” number of notifications. Without a severity filter, you will be bombarded by emails for all new vulnerabilities.
Responding to incidents
If you have received a notification about a new alert affecting your organization, there is no time to waste. Microsoft Defender for Endpoint alerts indicate that there could be an attack currently ongoing in your infrastructure. So time is critical. Within Microsoft Defender for Endpoint, one or more alerts will be summarized into a single incident to keep a high-level view of the events.
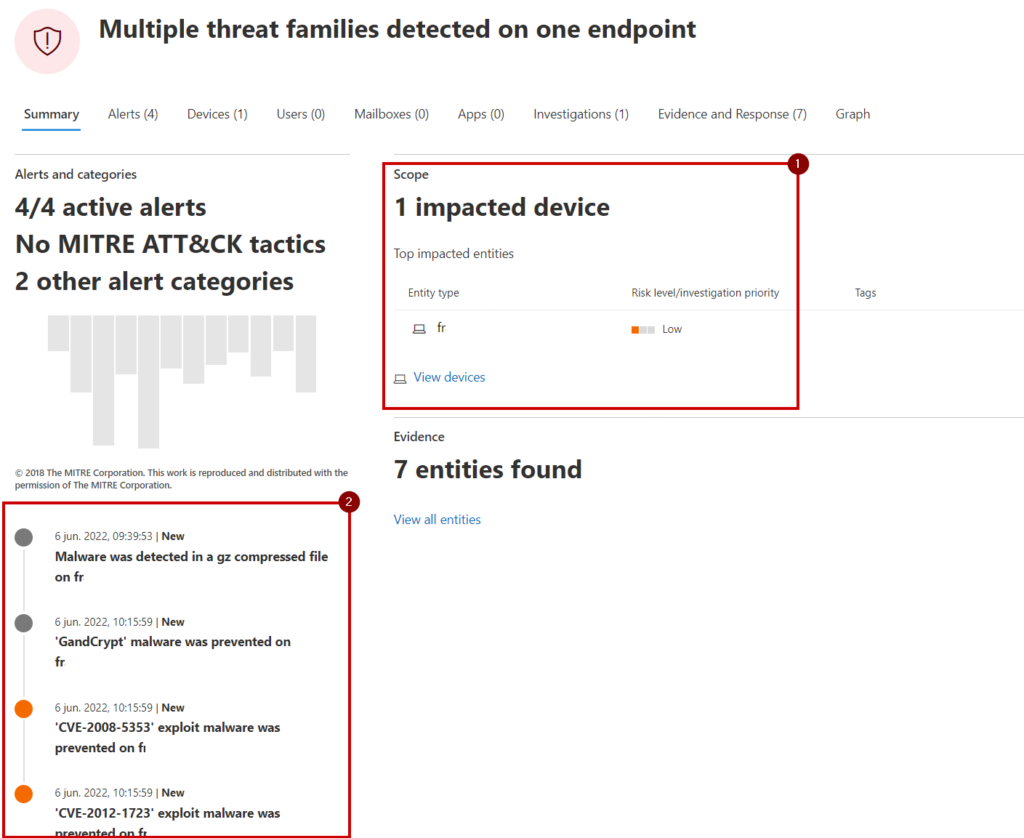
When you receive an incident, the first thing you should do is assess the impact; validate how many devices are in scope and what type of alert it is. This can be easily done by looking into the incident summary page which will provide a clear overview of the impact.
- By looking at the affected devices, you can see how many devices are impacted, but also which devices are involved. Critical machines (such as Domain Controllers or C-level machines) should be prioritized over kiosk devices.
- The incident page shows an overview of all active alerts. An alert contains detailed information about the attack happening in your environment. By looking into the alert title, you are able to see what exactly is going on.
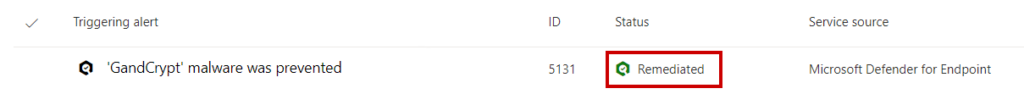
Other hidden gems in Defender for Endpoint are the “automated investigations”, which are available through the Investigations tab of the incident. When an alert is generated, an automated investigation is started. This will retrieve additional information from the endpoint and other cloud services (Security Graph, Threat Intelligence sources, etc.). This checks not only the malicious software in question but also subprocesses that could be affected. Each investigation shows a status and when the status shows Remediated as shown below, you can rest assured that the initial remediation steps have already been handled.
Top 10 Security Events to Monitor in Azure Active Directory and Office 365
Discover how native auditing tools can help — and how to overcome their shortcomings.
Handling exclusions
When dealing with investigations, you will most likely encounter false positives. These kinds of incidents are triggered by legitimate business software which triggers malware detection and blocks the application. In order to avoid business impact, an exclusion needs to be created in order to ensure these things don’t happen again.
The most important part when dealing with exclusion in Microsoft Defender for Endpoint is to know that there are different places to create the exclusion, depending on the source of the incident. There are currently four different ways to add an exclusion. Be aware that adding an exclusion at the wrong place will mean that your business application is still blocked.
| Exclusion Type | Cause | Configuration |
| Antivirus | A program is stopped by the local antivirus on a machine. | Add exclusion through a MEM Antivirus Policy or Group Policy Objects (GPOs) |
| Attack Surface Reduction | A program is impacted by an Attack Surface Reduction Rule. | Add Attack Surface Reduction specific exclusions through Intune or GPO. |
| EDR (Endpoint Detection and Response) Engine | Program is identified as malicious by the cloud service. | Create an allow indicator in Microsoft 365 Defender |
| Automated Investigation | An automated investigation identifies a file as malicious. | Ignore the file or folders through an automation exclusion. |
In addition to the right location for the exclusion, it’s important that the exclusion is added as restrictive as possible. For example, exclude a specific file rather than the whole folder.
Managing devices
If you have been working with Microsoft Defender for Endpoint for a while, you might have noticed devices will remain in your inventory, even when they are inactive.
When a device has been onboarded, it will remain in the inventory depending on your configured data retention (from 30 to 180 days) and there is no way to delete them.
While this might be annoying at first, the reasoning is logical. Data should be retained in order to investigate a device when a security incident is discovered after a couple of weeks/months. If it was possible to completely remove a device, an attacker could log into your security portal, remove all of your devices and cover their own tracks.
But that does leave us in an awkward scenario when trying to deal with inactive devices:
- When you reimage a device, a new entry will be created when you onboard the device again. This single, physical device will now have two different entries in your inventory list.
- If you decommission a device because it’s end-of-life, it will remain in your inventory even though it’s no longer active.
In order to solve this issue, Microsoft does try to help. A device will automatically receive an “inactive” status after seven days of inactivity, which means it can be filtered in your device list.
I recommend working with device tags to help stay in control. You can assign more than one tag to each device. This allows you to create a tag called “Decommissioned” or “Missing” and assign it to a device. This tag can then be used to populate a device group. A device group is used throughout the portal for filtering certain dashboards and views, which will allow you to show the correct, up-to-date information.
Prioritizing vulnerabilities
It’s important to prioritize vulnerabilities correctly so that you can better manage the large number of notifications you’ll receive. Because you will get new vulnerability notifications every day, it’s almost impossible to manage them all. Prioritizing by Impact Score, a tool within MDE will help you identify the vulnerabilities that need immediate attention. When remediation is available for a vulnerability, Microsoft will create a recommendation with an impact score. This score is calculated by a few different parameters, which includes:
- Number of weaknesses this recommendation will solve
- Whether this vulnerability is currently being actively exploited
- The amount of affected devices
- While this is a great step in the right direction, this doesn’t take into account the effort to deploy this recommendation. Take for example a vulnerability that affects a specific version of Chrome compared to the update of a SQL database. Even though Microsoft might recommend you to look into the SQL database first, the Chrome update might be a quicker win which could lead to a more interesting case.
When managing vulnerabilities, it’s important to consider the effort and potential impact of a vulnerability. Look for vulnerabilities that can be remediated quickly and return a higher degree of positive impact rather than big fixes which will require a lot of planning and work.
While your goal should be to remove all vulnerabilities from your environment, you also need to be realistic about the fact that there is not enough time in a day to solve everything. Therefore, it’s important to pick your battles and ensure you’re covering the most vulnerabilities with the least amount of effort.
Final words
I always say to my customers “After deploying Microsoft Defender for Endpoint, the work has just begun.” This isn’t a tool you just set and forget. It requires constant follow-up. It’s important to be aware of the different things to keep an eye on and manage. The product can provide immense value, but it’s up to you to take the data it outputs and use it as input for your improvements.
Top 10 Security Events to Monitor in Azure Active Directory and Office 365
Discover how native auditing tools can help — and how to overcome their shortcomings.





Curious if you will write a best-practises from the field blog. I mean like how many device groups, which advanced features to enable. AIR on which devices, device tags, which policies to activate etc. Thanks and great post!
Do you have any suggestions about these tasks should be coordinated with Sentinel operations?
I am not sure I follow? What do you mean exactly?