Passkeys are a Stronger Authentication Method for MFA
According to Microsoft in early 2024, only 38% of Entra ID accounts use multifactor authentication (MFA). Although this percentage has improved over the years, it remains alarmingly low. Another concern is that many think that SMS-based challenge/response is an adequate authentication method. As Thijs Lecomte points out in a 2023 article, it’s long past time to move away from phone-based authentication methods to something offering better protection against phishing attempts.
Passkeys fall into the category of strong, phishing-proof authentication methods. In early April, Entra ID introduced preview support for passkeys stored in the Microsoft authenticator app for MFA, but only for use with applications that depend on Entra ID. I don’t intend to cover the details of how to configure Entra ID to enable support for passkeys within a tenant. That information is available in Microsoft documentation and in many blog posts published by security professionals: Jan Bakker’s article covers many details of passkey usage, including on Windows and macOS. Further details are in Microsoft 365 message center notification MC718260.
Instead of going over well-trodden ground, I offer some personal observations about using passkeys to sign-into Microsoft 365 applications for daily work.
Introducing Passkeys
Passkeys are part of Microsoft’s strategy to eliminate passwords. The problem is that attackers can easily compromise passwords using tactics like password sprays (essentially, guessing the password for an account) or by intercepting credentials between clients and servers.
Passkeys use public key cryptography to avoid the need to share credentials across the network. The Authenticator app generates a public and a private key for an account. Entra ID stores the public key: the private key remains on the device where the Authenticator app runs (iOS or Android). The APIs necessary for Authenticator to create and manage the keys are in iOS 17 and Android 14 (or later), so the first issue is to make sure that those who will use passkeys have recent devices and the latest version of the Authenticator app (I used version 6.8.7 of the iOS app).
The Authenticator app acts like a FIDO2 hardware key, which is why a change is necessary to the Entra ID settings for the FIDO2 key authentication method (Figure 1) to enable people to use the Authenticator app.
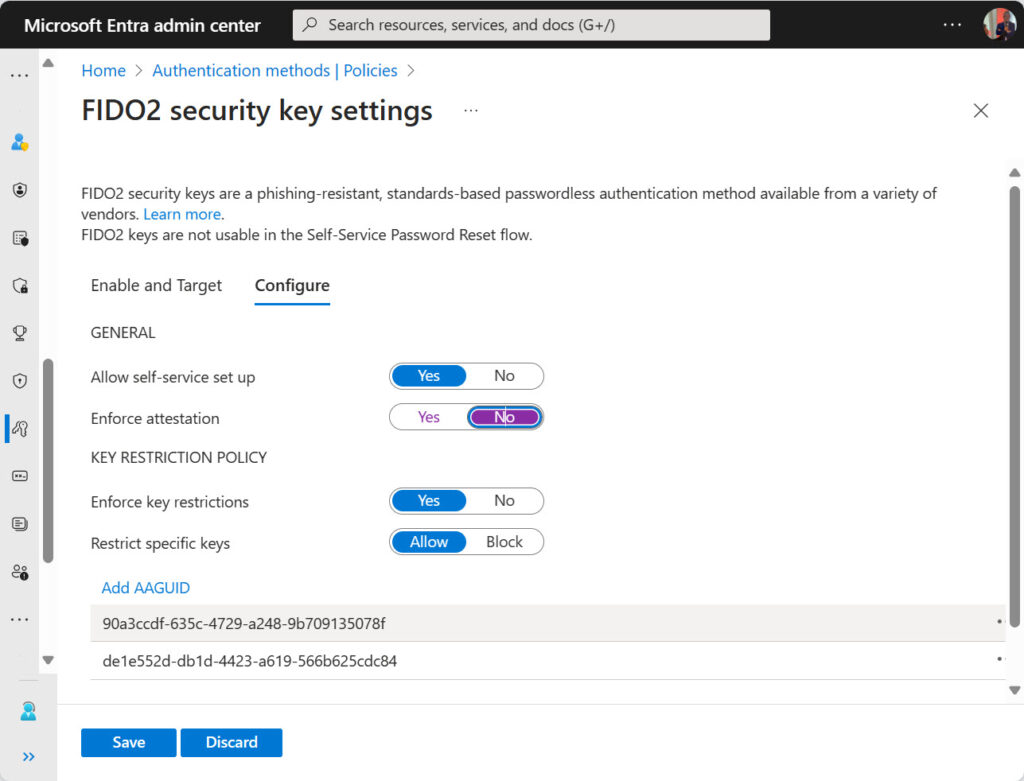
The important pieces of information here are the AAGUIDs that identify the Authenticator app on iOS and Android. An AAGUID is an Authentication Attestation Global Unique Identifier assigned by the FIDO alliance to recognize authenticator devices capable of managing passkeys. This “visual explorer” shows some of the other available devices. The Microsoft Authenticator app does not appear in the list, possibly because its FIDO capability is still in preview.
Like FIDO2 hardware keys, the passkeys managed by the Microsoft Authenticator app are device-bound credentials. In other words, the private keys for the passkeys are on the device. Password manager apps synchronize passkeys to make the passkeys available on any device supported by the password manager app.
Signing in with a Passkey
When a user enabled for multifactor authentication with passkeys signs into their account, the Authenticator app communicates with Entra ID to authenticate using the WebAuthn API (also used to create the public and private keys). Users must approve the use of the passkey through an on-device biometric check (like Windows Hello or a fingerprint sensor) or a local device password/PIN.
When I sign into a Microsoft 365 app, I enter my user principal name. At this point, Entra ID recognizes that I use a passkey. The next prompt I see asks me to select an authenticator. Earlier, we discussed the update for the FIDO2 authentication method to add the identifiers for the Authenticator app on iOS and Android. The options to use these devices appear as a valid choice (Figure 2).
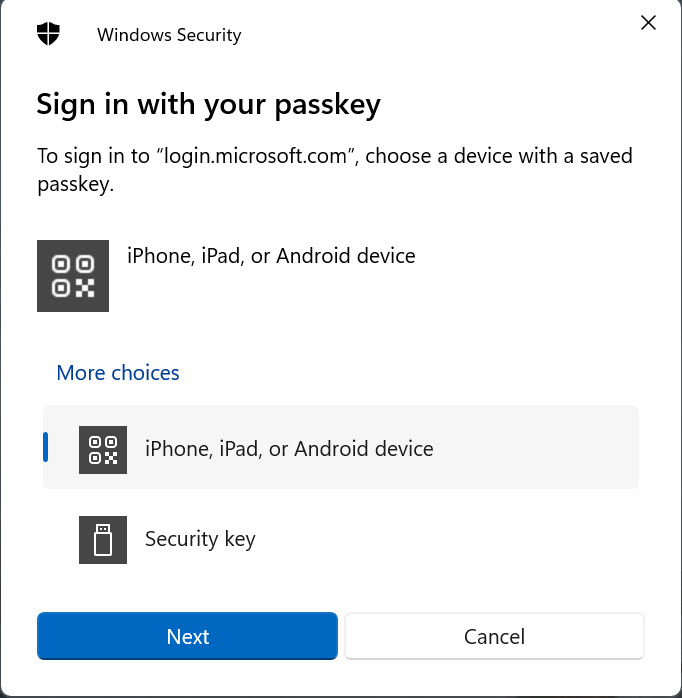
Selecting the iPhone, iPad, or Android option provokes a challenge from Entra ID for the Authenticator app to respond to. The phone must be connected to the workstation via Bluetooth to allow the challenge flow to proceed. Smartphones come with QR reader apps, so the challenge is in the form of a unique QR code (Figure 3).

To respond, use the smartphone’s QR reader app to read the code, which is recognized as a link to a passkey for login.microsoft.com. Authenticator then asks if you wish to use the passkey to authenticate. A positive response completes the sign-in process.
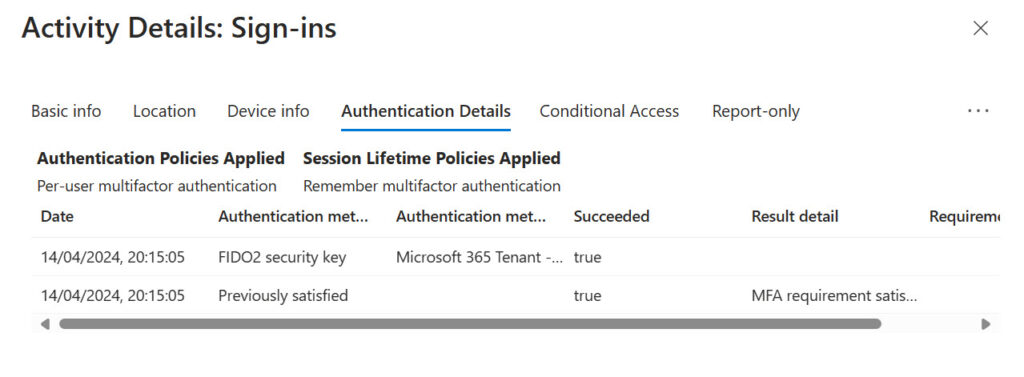
The details of the interaction are captured in the Entra ID sign-in logs as an interrupted sign-in (because of the challenge). Examining the record for the interrupted sign-in, we see that the authentication method used is a FIDO security key (Figure 4). The authentication method detail noted is the name of the passkey created by the user. The name appears in the list of sign-in methods configured for the user in the Security Info section of their My Sign-ins page.
The Critical Role of the Authenticator App
Passkeys underlines the importance Microsoft attributes to the Authenticator app as a core element in driving stronger authentication practices within the Entra ID installed base. I don’t have a problem with this approach, except when the time comes to switch to a new phone. The last time I replaced my iPhone, it took effort to update the Authenticator app to deal with guest accounts in other tenants.
I have no idea how easy it will be to move passkeys to a new phone. Perhaps it will be easy, but given that people replace phones regularly, it would be good if Microsoft dedicated effort to helping users move credentials more easily than it is today.
Making Things Better
Anyone coming from SMS-based MFA challenges will consider passkeys to be much more complicated than having to enter a six-digit response. Even those accustomed to using number matching in the Authenticator app will think that passkeys are more complex. It’s true that the process of using a passkey probably takes a few seconds longer to complete, but the benefit is that the way passkeys work with authenticators makes this method not susceptible to phishing attempts. That’s a good thing.
The downside is that the complexity of the current passkey implementation in Entra ID might turn users off and increase the volume of calls received by help desks. Technical folks will relish the degree of extra protection their account receives through a passkey. The challenge for Microsoft is to make the technology easier to use without losing any of that protection.





For windows devices I understand you can use WHfB as a phishing resistant MFA method for Entra ID, and so if you combine that with using passkeys for mobile device signin, I expect you could avoid the cross-device signin experience that seems to be the part the users might struggle with?
Ideally you could sync your passkey to your desktop, but as MS Authenticator & iCloud are primarily mobile first apps i’m not sure how this would work unless there was a desktop (or web browser) component. I see LastPass has passkey support coming so potentially that would be a way to sign into both platforms using passkey synced to the browser plugin, rather than having to use the cross device flow?
I have no knowledge of how Microsoft plans to develop passkey support further. They have invested a lot in the Authenticator app and for now that seems to be the only game in town…
Also.. using Authenticator could be great but the migration of Authenticator to newer phones is a big pain, even worst if you have a few tenants registered.
Yep. I’ve lived through a couple of migrations to new phones and it hasn’t been a wonderful experience. https://office365itpros.com/2023/01/04/microsoft-authenticator-app-qr/
not able to login with passkey error received from windows security that ” something went wrong” what can i do now
I have no idea. I cannot see your tenant details and I don’t know if you set everything up correctly. Check everything and retry…
So we train users to scan a QR code to login? Hard pass.
Actually that is only when using iPhone. On Android, when setting up the passkey, you can choose to store the QR code. So instead of having to scan the QR code on the monitor, you get a list of options on the phone (MFA, Security Key, Passkey and so on), and you just choose the mobile device your are on from the list.
This part may be a bit misleding: “The phone must be connected to the workstation via Bluetooth to allow the challenge flow to proceed.”
It may be good to know that yhey do not have to be “Bluetooth paired” in a technical sense, the CTAP 2.2 solution uses Bluetooth BLE simply as a proximity check. 🍺
The implication of this is pretty heavy though. It means that passkey logins cannot be done remotely. This may be good or bad, but it will exclude a lot of remote client scenarios (vdi, VMs…) unless the authentication is done locally.
From the Microsoft documentation: https://learn.microsoft.com/en-us/entra/identity/authentication/how-to-sign-in-passkey-authenticator?tabs=iOS
Bluetooth and an internet connection are required for this step and must both be enabled on your mobile and remote device.
Indeed, but no BT pairing is needed beforehand, you just have to be in proximity of the device you are authenticating on. I know you do not state this so there is nothing wrong in the article, I just want to clarify this so people don’t interpret Microsofts docs wrong. 🙂
Good point. I read the BLE used not just for proximity check but it may used for key exchange or transmit small amounts of data. Most of the VDIs support passkeys as long as the SSO configured correctly.