There is More to It
Keeping Defender for Endpoint agents up to date is more complex than people initially think. It’s not about just deploying one update; a Windows agent has multiple updates.
Across operating systems, there are two main types of updates that are applicable.
Security Intelligence – Signature
- Antivirus Detections: This is the most frequent update and contains updates for the malware database of the antivirus product.
- Engine Updates: These are included within the signature update packages and update the antimalware scanning updates.
Product Updates – Platform
- New Functionality: These updates bring new functionality to the Defender antivirus product, such as new protection mechanisms or features.
- EDR Sensor (SENSE): The endpoint detection and response (EDR) component of Defender for Endpoint itself requires updates as well. This is done using a recurring update that checks the sensor version.
The Importance of Defender Updates
These updates are of paramount importance in keeping your environment secure. New signature updates are published as quickly as every four hours; they ensure the latest threats are detected by the antivirus. The sooner you deploy these updates; the sooner a new type of malware is blocked.
The other updates are responsible for providing you with a working and healthy antivirus and EDR agent. Not all versions of those components remain supported, typically only the three latest versions remain in active support. Keeping your agents updated not only keeps you secure, but also ensures a device is in a supported and functional condition.
Windows Updates
For Windows, there is a lot of ground to cover. Windows is still the biggest focus for Microsoft and that can be known by looking at the number of updates and functionality.
For signature updates, you can choose the update frequency and update source. In terms of frequency, I recommend updating every four hours as these updates are typically released every four hours. For the update source, use an internet-based source such as Microsoft Updates, compared to using file shares, WSUS or MEMCM. The reason for that is that the release cycle of signature updates is so frequent (too frequent for these systems to manage). A typical MEMCM deployment only synchronizes its updates every 24 hours. This does not align with an update frequency of 4 hours, as it would cause too much delay. Signature updates are small, iterative updates that are only a few MBs in size, meaning there is limited impact on the internet bandwidth. I only suggest using on-premises sources if you can ensure updates are synchronized frequently and you have a large on-premises deployment (100+ servers).
While there have not been a lot of issues with signatures updates, there have been some impactful incidents. One example is when a faulty update removed desktop shortcuts in 2023. This had caused quite a big impact as it affected end-users and showed the need for using gradual roll-out. Gradual roll-out ensures updates are rolled out in waves, allowing an organization to test them on a test group before deploying them across the environment. This delay between waves will be minimal (3 hours by average), so if there is a faulty update you need to be quick to disable new updates from being deployed.
Platform updates are pushed using the regular Windows Update process. Which means: Intune, MEMCM, WSUS or others. This deployment mechanism happens automatically without much interaction. If you are using Microsoft Intune, no additional configuration is required except the regular Windows Update configuration. For MEMCM and WSUS, double check that the ‘Microsoft Defender for Endpoint’ product is enabled in the software update configuration. Not enabling it there will mean no Defender platform updates are pushed.
macOS
macOS shares most of the configuration options that Windows systems have but lacks the native gradual roll-out process and update location preferences.
Using configuration profiles, there are options to enable and disable signature updates and configure an interval. While not ideal, the interval can be used to create make-shift gradual roll-out plans. Ensuring one ring receives the update quicker, as it scans more regularly.
Platform updates are deployed the same as updates for M365 Apps, OneDrive or Edge using Microsoft AutoUpdate. This is a separate application that is responsible for the update process. It can be configured independently to configure update preferences, such as the interval.
Linux
Defender updates for Linux systems are the hardest among all operating systems. This is because there isn’t a real native program to manage this.
Signature updates allow little to no configuration. You can only enable or disable automatic signature updates, but there is no way to configure the source, frequency or gradual roll-out like in Windows.
Performing the platform updates requires the configuration of a cron job (scheduled task). While Microsoft offers some examples, this is often not known to customers and Linux is where I see the most misconfigurations.
The update process of Linux lacks customization. This functionality shows that there is room for improvement in this category.
Android & iOS
Android & iOS updates are pretty straight forward. The Defender for Endpoint receives regular application updates and should be patched accordingly. Typically, there is no specific strategy that should be followed here. Use the same mechanisms that you use for other applications, these are typically pushed using an MDM tool such as Intune.
Tracking Updates
To follow up on all of the different updates, Defender Vulnerability Management can be used. While there is some information available in the GUI, the most interesting information available is advanced hunting. Microsoft provides us with three separate queries to validate the update process.
In Figure 1 below, you can find an example of the results of the query. This is an actual response I got while using it in a customer’s environment. There are a couple of things of note:
- You are able to see the version of the update (in this case signature updates). It is advised to cross reference this to the update website to learn more about the update and its release date.
- The last column contains all devices that have an unknown status. Unfortunately, this happens quite often. It is possible the device hasn’t been online for an extended period of time.
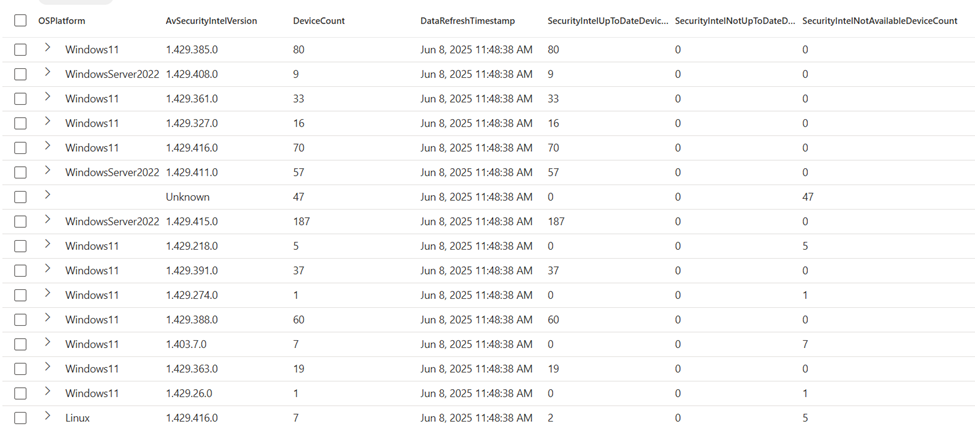
It is recommended to review this progress regularly. This process can be automated by running this query on a schedule and emailing the results. While this blog from MVP Jeffrey Appel focuses on Sentinel data, the same logic could be used to deploy these queries.
The Process is Important.
Updating Defender is quite complex as the process differs between each operating system and not all updates are alike. The first step you need to take is fully understanding the process on the operating systems you support. Afterwards, double check the configuration and ensure you follow up continuously. When running audits at customers, I often notice a small percentage of devices isn’t being updated sufficiently.





From a practical standpoint, I would have appreciated getting more substantive information about updating like how to set up a task in task scheduler to have the workstation update signatures every 4 hours or specifically how to configure the same thing in Group Policy (if that’s at all possible).