People (by which I mean “mostly me and Steve Goodman”) never get tired of mocking the way Microsoft names and brands its products. This mockery is deserved in many cases, but one area where we’ve seen improvement is in the establishment of some umbrella brands. Azure is probably the most obvious example of an umbrella brand, but we also have Entra for identity management, Viva for employee engagement, and so on. These umbrella brands collect multiple product and service offerings, each of which may have its own name, into a family. That brings us to this week’s Practical Protection topic: the Defender umbrella brand. This is maybe the largest of the umbrellas besides Azure; there are Defender product lines for individuals, the Windows OS, the cloud, Windows and Linux servers, IoT environments, and more. Of course, Microsoft 365 is covered under this umbrella too. Microsoft 365 Defender itself is made up of 5 products: Defender for Endpoint, Defender Vulnerability Management, Defender for Office 365, Defender for Identity, and Defender for Cloud Apps (MDCA). (There is as yet no truth to the rumor that Microsoft will introduce a new capstone product called Defender for Defensive Defense.)
With all these different products, you might assume that Microsoft wants you to buy licenses for them… and you would be correct. However, you already have some Defender functionality for Microsoft 365 available to you as part of the licenses you’ve already bought, so let’s dig into how you can tell what you have and then how you can use it.
Public Service Announcement: a Brief Commercial for Defender on Windows
The native Windows Security suite includes Defender for Antivirus, which is a terrific anti-malware product. It costs you nothing. With none of the installation, configuration, or subscription shenanigans of its competitors, Defender for Antivirus is very well-supported, easy to use, and reliable. For larger installations, you can manage it through Group Policy. You can save yourself worlds of trouble if you enable it on all the Windows machines you have in your family, including for your less-technical relatives who will inevitably be the ones to ask you to help fix their slow, virus-infested machines.
The Old-Timer: Exchange Online Protection
For now, I’ll skip the other Microsoft 365 Defender products and focus on Defender for Office 365. As the name suggests, this piece of the Defender family is intended specifically to improve security for Office 365 deployments; as such it doesn’t include protection for servers, endpoints, other cloud apps, or identity management. Back in 2020, Microsoft renamed the existing Office 365 Advanced Threat Protection (ATP) suite to Defender for Office 365. However, they left alone the contemporary Exchange Online Protection (EOP) toolset, which is included with every Exchange Online tenant. (You can also buy EOP separately if you want to use it with an on-premises Exchange environment.)
The New Hotness: Defender for Office 365
Besides EOP, Defender itself is split into two licenses: plan 1 (P1) and plan 2 (P2). The products are essentially layered:
- Everyone who has Exchange Online has EOP, which includes basic anti-malware, inbound and outbound anti-spam, and antiphishing features
- People who buy Defender for Office 365 P1 have all of EOP’s functionality plus the additional stuff included in P1, including more policies to control Safe Attachments and Safe Links behavior, plus some support for SharePoint, OneDrive, and Teams protection
- Buying Defender for Office 365 P2 gets you everything in EOP and P1, plus threat intelligence tools and attack simulation training.
Microsoft has a helpful graphic in their documentation that sums up the alignment of these three offerings (figure 1). Given how they line up, Microsoft takes the very reasonable position that you should start by configuring EOP before you spend any time on the Defender toolset, as EOP protection is still around when you deploy P1 or P2.
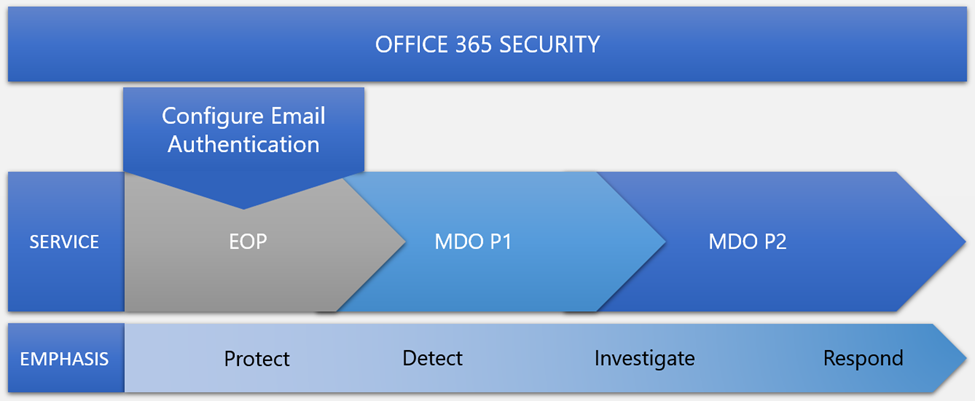
The licensing for these plans, alas, is not so easily deciphered. Microsoft has a large table showing exactly which other Microsoft 365 and Office 365 plans include P2. In general, though, you have to buy an SKU that ends in “5” to get Defender P2 included (including M365 E5 Security or Compliance, O365 E5, or EM+S E5). Because P2 includes all the P1 functionality, if you only want P1 capabilities you’re probably best off buying it as a standalone license.
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.
Standard, Strict, Custom, and Default
Manual configuration is the enemy of good security in many cases. This is true for these services too. You can always go in and define custom anti-phishing, anti-malware, and Safe Links/Safe Attachments policies, then apply them to target users. The fastest and safest way to deploy EOP, Defender P1, or Defender P2 is to use the preset policy categories. These actually come in three tiers:
- The default policy controls what controls are applied to users who don’t have a more specific policy assigned. The default policy is always there, but it’s always overridden by any more specific policy. You can edit some of the settings in the default policies (depending on the policy), but these policies are really intended as the lowest common denominator for protection so Microsoft won’t let you just disable all their settings. EOP has a default set of policies, but you don’t get default Defender P1/P2 policies unless you license those products.
- The Standard policies are intended for everyday use for most users. Microsoft says these policies provide “balanced” settings that (hopefully) don’t irritate users out of proportion to their security improvements, and Standard applies Safe Links and Safe Attachments settings.
- The Strict policies ratchet up security for high-value accounts. For example, you might want your CEO, CFO, and other executives to get additional impersonation protection, in which case you’d add them (or a group containing their accounts) to a target of the policy.
You can manually configure custom policies and assign them to users too.
Order of precedence is important here—the Strict policy always overrides all others that are assigned, then comes Standard, then comes custom policies. If you have settings in a custom policy that conflict with Standard or Strict policy settings, those settings will overwrite the custom settings. It’s perhaps more important to know that you can’t change the underlying settings of the Standard or Strict policies. This makes sense when you think about the intent of these policies—to let you quickly assign strong security settings—but it may make it more difficult for you to tailor the settings you apply to key users.
Going Beyond Preset Policies
Microsoft publishes a tool called ORCA (the Office 365 ATP Recommended Configuration Analyzer) that will produce a report showing how your applied EOP and/or Defender policies line up with Microsoft’s recommendations. However, the Defender portal also has a configuration analyzer that will show you three useful things: how your settings compare to the standard policy recommendations, how they compare to the strict recommendations, and how they have changed over time. To get there, open the Defender portal and choose Policies & rules > Threat policies > Configuration analyzer and you’ll see something like the below (figure 2).
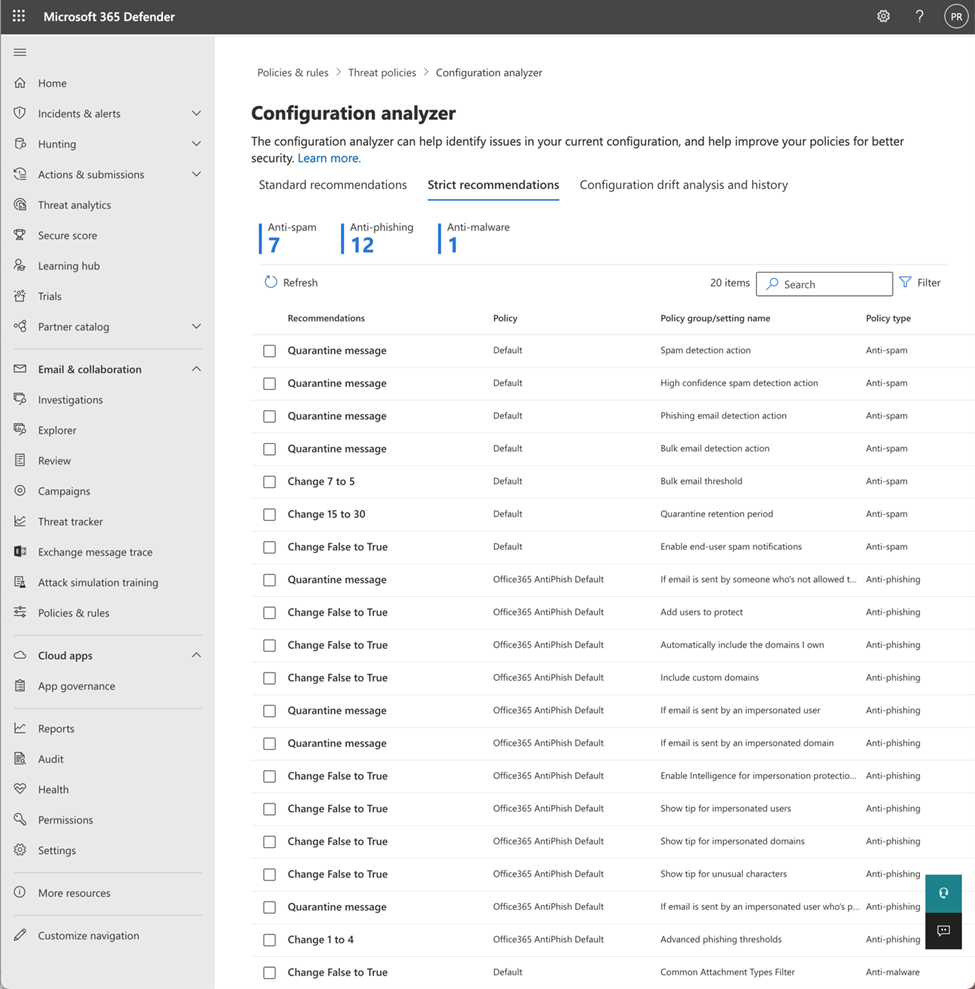
Microsoft’s guidance is that you should start by assigning Strict or Standard preset policies to your users, then run the configuration analyzer, and only then—once you have a good understanding of what level of protection is already applied—should you consider customizing policies.
Defender for Office 365 in context
It’s clear that Microsoft is investing a great deal of effort across their security portfolio. Many organizations will probably look at the specific features of Defender for Office 365 and decide that they don’t have enough independent value to justify their cost—but when you consider Defender P2 as part of the 5-series SKUs, the value proposition may improve when there’s a lower standalone cost. A thorough understanding of what Defender for Office 365 can do is important as you consider how best to protect your tenant.





Thanks, Andi! That link miiiiight not be too useful. Looks like I need to have our editorial staff fix that right quick.
Hi Paul,
thank you for this article. And yes, mockery around names is totallly justified – does anyone remember groove? The kind-of-onedrive then music player then kind-of-onedrive again? Well…
Oh and I think you might have misplaced a link to the “large table from microsoft”: file:///Users/paul/Downloads/Modern%20Work%20Plan%20Comparison%20-%20Enterprise.pdf
Apparently there is no user paul on my machine? 😂
Regards