WarGames and Security
Any child of the 80s will immediately recognize the quote “Shall we play a game?” from the groundbreaking 1983 film WarGames. (If you missed it, let me quickly recap: a bright teenage hacker hacks into a system that turns out to be a mostly-sentient nuclear war planning engine, and World War III nearly starts as a result.) WarGames gave us the terms “wardialing” and “wardriving,” and it’s credited with highlighting some fundamental computer security issues in a way, and at a time, that made a big popular impression. It’s a fun movie and you might enjoy it if you haven’t already seen it… but enough movie criticism; instead, I want to talk about playing games, but at work, to improve your security.
Thought Experiments and Dungeons
Albert Einstein coined the term “thought experiment” (Gedankenexperiment in German) for his habit of performing conceptual experiments to formulate and test theories. There’s a great deal of power in this technique since you can think through theories and problems without requiring physical laboratories or equipment. This basic technique turns out to have many other applications. Militaries around the world use similar techniques to think and plan through both strategic and tactical problems, adding data (where it exists) about the correlation of opposing forces and other factors. At the end of the day, though, a thought experiment is just that: thinking about a problem.
You can do these thought experiments in groups, of course. The popular Dungeons and Dragons game is, at its core, a big thought experiment. The dungeon master sets some initial conditions, and the members of the party try to think their way out of the problems they encounter. There are no actual swords, monsters, or traps involved. Government agencies all around the world do this with large-scale exercises to test things like continuity of government or disaster response. These exercises are generically referred to as “tabletop exercises,” because they can literally be performed in many cases with nothing more sophisticated than a table, some paper, and the involved players. More than just a set of questions, a good tabletop exercise will be an entire script that develops a scenario in enough detail for the participants to get a realistic look at whether their responses would solve the desired problem(s).
Naturally, the techniques of tabletop exercises are immensely powerful when applied to cybersecurity problems. The problems, and solutions, are limited only by your imagination. In fact, the US Cybersecurity and Infrastructure Security Agency has a whole guide on how to plan and execute cybersecurity tabletop exercises—more on that shortly. First, let’s dig into a simple example.
Moving From Simple to Complex
Imagine that you walk into work one morning and learn that no one is able to log in to your domain-joined Windows machines. That scenario (which many of us have probably experienced in real life) makes a great start for a tabletop exercise. As the exercise planner, you can take things in several different directions. The problem might be due to an obvious or easily detected security compromise, or it could be something more subtle. It could be simple (some of your DCs caught ransomware but others are unaffected) or fiendishly complex (like the 2017 Maersk outage).
You can level up this simple example by thinking like a dungeon master, or maybe a chess master: “If player X does this then I’ll make the scenario do that.” A few examples to stimulate your imagination:
- If the player representing the admin tries to restore from backups, X% of the backups will randomly fail to restore properly. (To make this more fun you could actually roll dice for this one!)
- If the player representing the CISO isn’t involved enough, they get a simulated call from the New York Times asking for comment on a rumor that your organization has been attacked.
- Depending on the organization, if the team doesn’t make reasonable progress within a set period of time, the problem gets worse (maybe the ransomware spreads to end-user devices too?)
- If the team’s progress is a little too good, and they’re making all the right moves, maybe one of the roles suddenly develops a medical emergency and becomes unavailable.
The point of these scenarios is not to put the players in an unwinnable situation. Instead, it’s to force them to think and plan in advance. What would your real CISO do with a press inquiry from the NYT? Would they know who to reach out to for crisis communications help or would they blurt things out? What would your real admins do if the break-glass M365 account turned out to be inaccessible or locked out? And so on.
Finding the Right Level of Complexity
The larger and more complex your organization, the more options you have in designing realistic scenarios to test and shape your responses. A few sample prompts will show what I mean:
- Your CIO gets an email from Troy Hunt of HaveIBeenPwned asking whether she’s aware that your organization’s data is being sold on the dark web.
- One of your system admins at your manufacturing company is arrested in an unfriendly foreign country and their laptop is confiscated by a potentially hostile intelligence agency.
- One of your university’s executives says something inflammatory. Now the Internet is mad and they’re spamming your support forums, the web applications you use for admissions, and your help desk.
- Microsoft calls you to notify you that they’ve seen evidence of a nation-state attacker rooting around in your Office 365 tenant.
- A vendor whose products you use sends a security advisory about a critical 10/10 RCE vulnerability that they say must be immediately patched… and it’s Christmas Eve.
These are all things that could very plausibly happen (or have happened!) and that you might need a response for. Obviously, not every one of these cases will pertain to every organization, but this isn’t meant to be a catalog—just something to kickstart your creativity.
Table-Topping the CISA Way
I mentioned the CISA guide to tabletop exercises earlier. It has a lot of practical suggestions on how to organize, plan, and carry out tabletop exercises, and you’ll probably find its guidance useful. However, the CISA document talks about how to do the exercise… not the exercise itself. For help with that, you might want to look at the CISA cybersecurity scenarios here. The screenshot below is taken from their ransomware tabletop exercise guide:
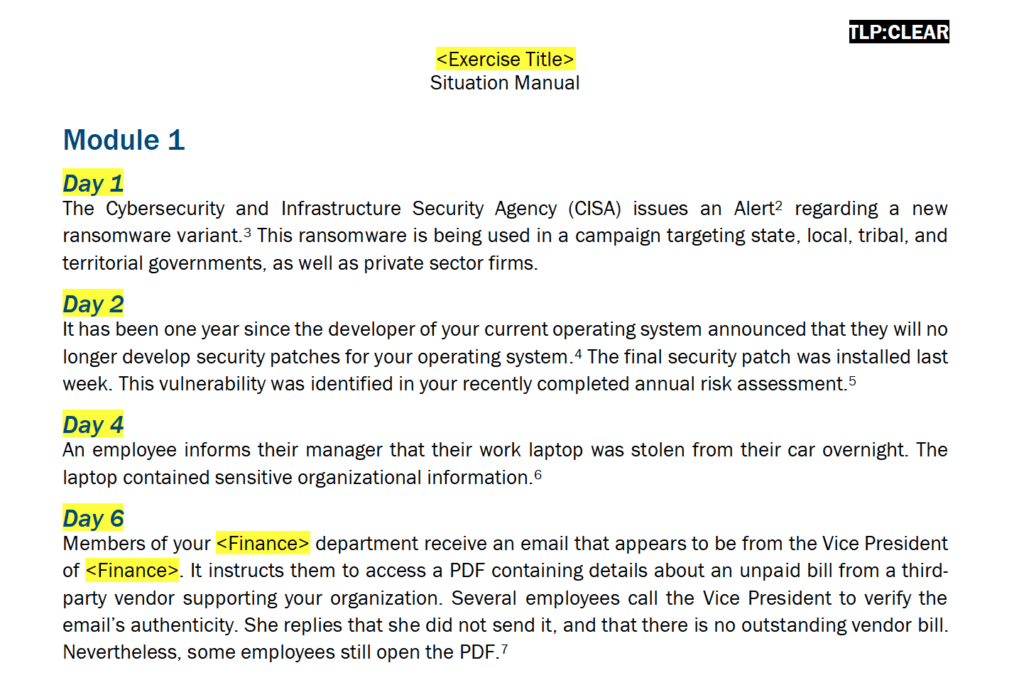
For each of the days, you can easily construct a set of questions or actions that are specific to your organization. The CISA scenarios are a great way for you to ease into the process of conducting tabletop exercises around common scenarios (such as ransomware attacks); as you gain more experience with conducting these exercises, you can apply increasing levels of detail and customization to match the specific risks (and responses) you most want to investigate.
Free and Yet Valuable
One of the best parts of tabletop exercises is that they don’t cost you anything but time. There’s no software or equipment to buy; you don’t have to subscribe to anything; you don’t need a fancy venue. Get a conference room, some legal pads and pencils, and a big pot of coffee, and you have the basic materials to get some profoundly useful insight into your security response capabilities. All you need to do is apply some imagination.




