Showcase of the Value of MITRE ATT&CK Within a Typical Microsoft Environment
MITRE is a well-known organization within the cybersecurity community. It is a non-profit based in the United States and fully funded by US government organizations. MITRE is best known for its framework. These frameworks are used by cyber security professionals to ensure there is a common language. They help to close the gaps and keep everyone in the same direction.
MITRE has two frameworks where it gets its fame: MITRE ATT&CK and MITRE D3FEND.
ATT&CK and D3FEND
MITRE ATT&CK is the oldest and most well-known framework. It provides an overview of all potential types of attacks an attacker can do, spread across the kill chain. A kill chain is a collection of all the steps an attacker executes. All attacks start with ‘reconnaissance’, where they will research and identify entry points. Successful attacks end with ‘impact’, this can mean (among other things) the deployment of ransomware or the exfiltration of data.
ATT&CK can be used in a couple of different ways:
- As a SOC (Security Operations Center) team, we can use ATT&CK to check how many detections we have made and if we cover every type of malware.
- During reports of incidents or pen tests, MITRE ATT&CK is used to identify what kind of techniques were used.
MITRE D3FEND tailors, as the name suggests, more to the defensive side. It stands for ‘Detection, Denial, and Disruption Framework Empowering Network Defense’. The framework provides a uniform way to discuss countermeasures against cyberattacks. Examples include hardening of your applications, detection of malicious activity using log collection, and taking actions against compromised entities such as disabling an account or isolating a device.
Organizations can use D3FEND to map how well-thought-out their defenses are and where they might encounter potential gaps. A mapping exists to identify how we can defend against certain techniques within the ATTACK framework. This can be used to correlate the two frameworks.
MITRE ATT&CK is the most well-known framework, and it’s also embedded within Defender XDR and Sentinel. While D3FEND has it’s use cases, the ATT&CK framework is the most useful. That is why we will now deep-dive into the specifics of it.
Tactics, Techniques, and Sub-Techniques
As we discussed earlier, MITRE ATT&CK allows us to map the behavior of an attacker against a predefined list. Each phase in an attack is labeled as a tactic. Examples of tactics are reconnaissance, lateral movement, persistence, and impact.
Within each tactic, there are several ways to execute this behavior. Each tactic has multiple techniques. To obtain persistence, an attacker can either use an existing user account (this correlates to the ‘Account Manipulation’ techniques) or create a new one (Create account technique). A technique can have sub-techniques. For example: the ‘create account’ technique has three sub-techniques:
- Local account
- Domain account
- Cloud account
By offering three levels of detail with tactics and (sub-)techniques, mapping can be very detailed. This is extremely useful as attackers keep coming up with new attack vectors.
The MITRE ATT&CK framework is updated regularly, a new version is released twice a year. The latest version is ATT&CK v16 which was released on October 31st, 2024.
Using ATT&CK in Defender and Sentinel
ATT&CK is used through Defender XDR and Sentinel. First of all, Defender maps every alert against an ATT&CK tactic and technique (and even sub-technique).
The same applies to Microsoft Sentinel, when we are creating new analytic rules, we can map the correct ATT&CK reference as seen in Figure 1 below. While this is not a mandatory step, it is highly advised to add the correct reference. We will cover the ‘why’ later in the next section.
For beginners in cybersecurity, choosing the correct tactic and techniques can be quite a chore and unclear at times. In that case, I would recommend taking a look at some of the analytic rule templates. All of them have a predefined MITRE ATT&CK reference added by Microsoft, which can provide you with some examples.
Adding the correct reference is something that takes practice. By combing through different rules and all of the tactics and techniques, you familiarize yourself with the choices. It is also important to note that there is no limit on how many tactics and techniques you can add. Most rules will have multiple assigned to a single rule.
MITRE ATT&CK Dashboard
Within the Microsoft Sentinel and Defender XDR portal, you can find the MITRE ATT&CK blade (figure 2). It provides a visual interpretation of all of the techniques covered by your current Sentinel analytic and hunting rules.
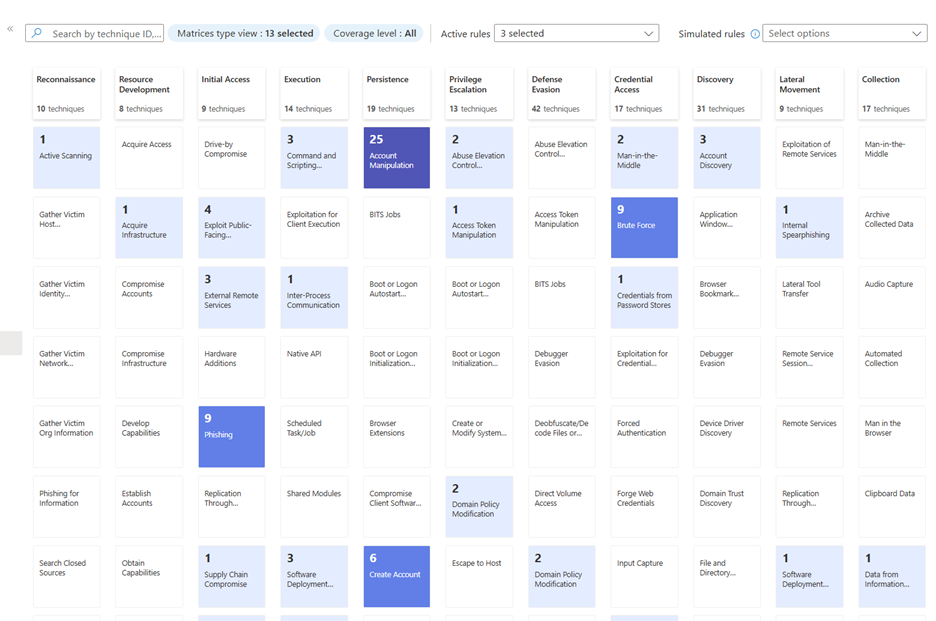
This overview can provide us with insights into the current coverage and potential detection gaps. In the figure above, we can see there are a lot of rules within the persistence tactic, but not for collection and reconnaissance. By using this information, we can choose our next SIEM investments based on factual data. For example, we can create additional detection rules that focus on detecting attackers in the reconnaissance stage or look to ingest additional data sources that we can use.
Limitations Within the Default Features
While the current MITRE ATT&CK implementation with Sentinel provides you with some good insights, it misses some important points:
- Microsoft is using an outdated version of the MITRE ATT&CK framework. The latest version is 16, while Microsoft is still running on 13. This means that it won’t hold the latest techniques and sub-techniques.
- There is no option to add weight to a detection rule. Some detection rules will provide better protection compared to others. This can be the case when a rule has a really niche detection. The framework does allow us to add weight, but Sentinel hasn’t given us this option.
- There are no insights into the current coverage of Defender XDR in terms of detections, it will only show detections that are present in Sentinel. The figure above shows a production environment that has bad coverage at first sight. But when looking further, all Defender products have been deployed, which increases the coverage significantly. Microsoft doesn’t provide us with these insights.
The limitations mentioned above won’t be an issue for everyone, these are more issues when you are diving deeper into your coverage. It is important to note that the Sentinel dashboard doesn’t hold the entire truth, and it should be interpreted correctly.
Going Beyond the Default Features
If you want to overcome the limitations of the default features, you will need to look into creating a custom solution. This can be done based on the official MITRE ATT&CK navigator which provides you with an interactive way to build a dashboard. Additionally, there are official researchers out there who have mapped what techniques are covered by Defender XDR.
The MITRE ATT&CK framework is an important tool to have in your tool belt and you need to be aware of how it can be interpreted. Microsoft goes a long way to add as much context to their products as possible but if you want an advanced integration, a custom tool is required.




