Azure Active Directory conditional access has a new feature, currently in preview, allowing customers to block legacy applications and protocols such as POP, IMAP, or anything that doesn’t support modern authentication.
Here’s an example of how this is useful for Office 365 customers. In this case the user Dave Bedrat is prompted for multi-factor authentication while accessing his Exchange Online mailbox using Outlook on the web. This prompt is caused by a conditional access rule in Azure AD that requires multi-factor authentication if the user is connecting from a non-domain computer.
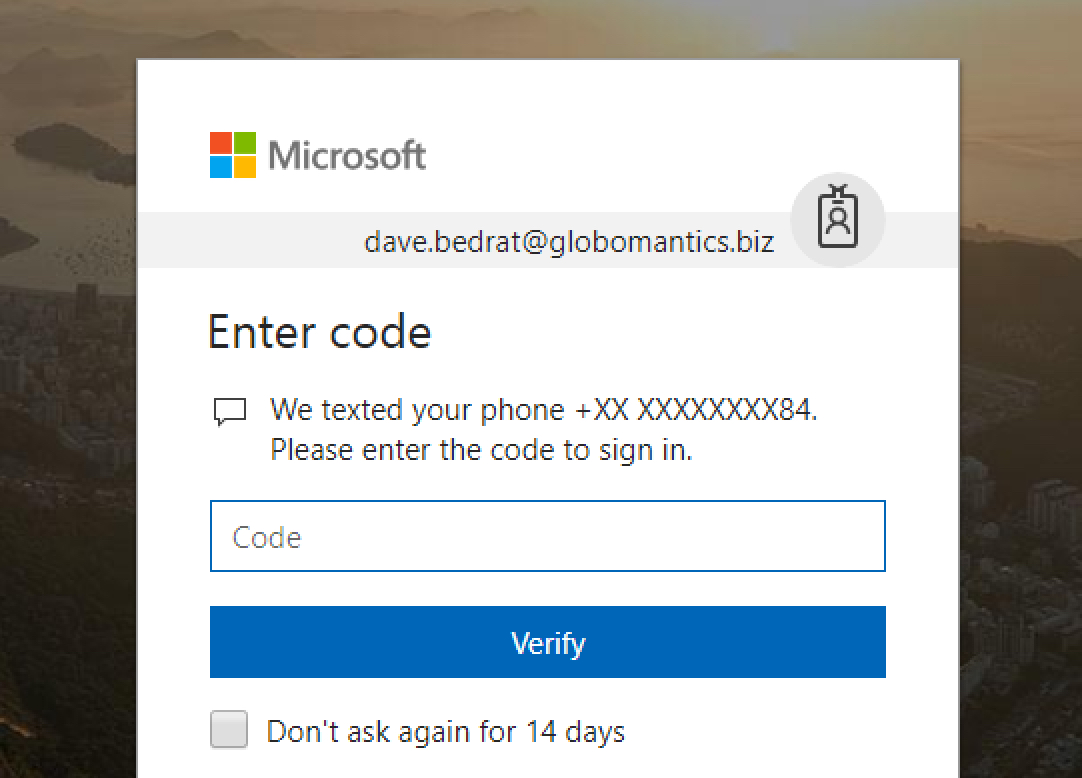
However, using the Thunderbird email client to connect to the mailbox over IMAP, which uses basic authentication, is successful.
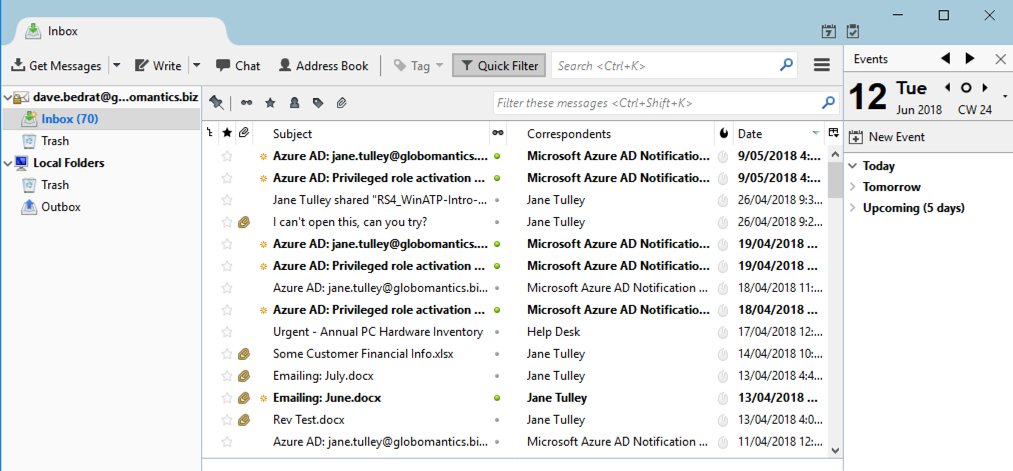
If IMAP were the only problem you could simply disable the IMAP protocol on all your Exchange Online mailboxes, and use a mailbox plan to disable it for any new mailboxes. But that doesn’t solve the issue for other basic authentication scenarios. That’s where the new Azure AD conditional access capability to block legacy apps comes in handy.
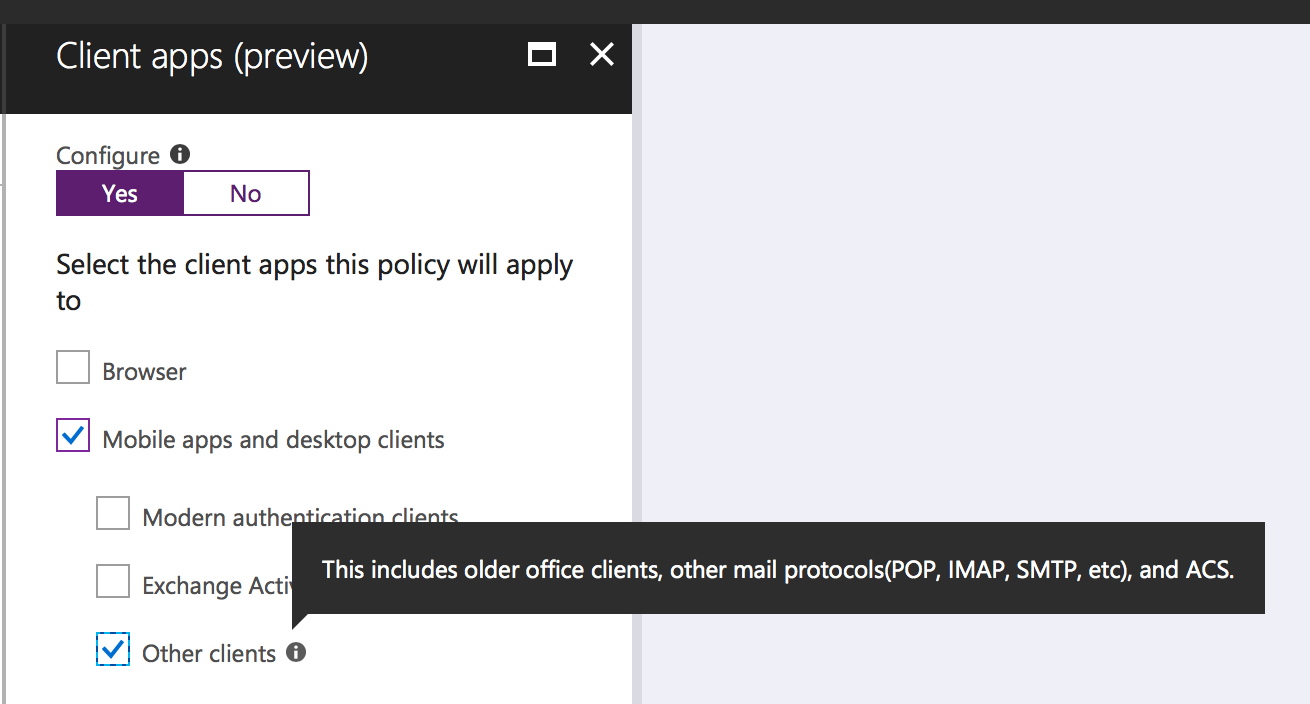
Create a conditional access policy for the users and cloud apps you want to control. In the Client Apps section of the policy you can select Other clients (see screenshot above), which includes legacy and basic authentication apps that use protocols such as POP and IMAP.
You can use a conditional access rule to block legacy apps, but it’s not possible to use any of the other controls such as requiring multi-factor authentication or requiring compliant devices. Those controls all rely on modern authentication. So a practical implementation of this new capability would be to configure a separate Azure AD conditional access rule to block all legacy apps. If necessary you can set exceptions on the users or the network locations that are still allowed to use legacy protocols.
Microsoft has documented this feature here, including an FAQ. Note that it can take up to 24 hours for a new conditional access policy to begin blocking legacy clients. Within the first few hours of implementing the policy I could still connect with the Thunderbird email client. When it tried again 24 hours later, the IMAP connections were being denied.
Photo by Tina Rataj-Berard on Unsplash

This is outdated. IMAP and POP now support XOAUTH (which allows “modern authentication” OAUTH2 and are the standard W3C protocols for email and therefore should be supported until a new universal email protocol is standardised.
I have this setup and it does not work. Was able to block web login but not IMAP or POP. Worked with MS tech support and still no joy in Mudville.
Pingback: Blocking Basic Authentication to Exchange Online - by Steve Goodman
When i configured outlook on a local network this policy is not applying. Any suggestion on this?