In my recent post about Windows Defender ATP I discussed how we should assume that a breach can and will occur. Even secure Windows 10 computers can be compromised by a determined attacker using advanced tools, although in may cases it is basic attacks such as social engineering that lead to breaches.
When Windows Defender ATP detects suspicious activity on one of your endpoints, it applies a “machine risk” rating, such as “Medium” in the example below.
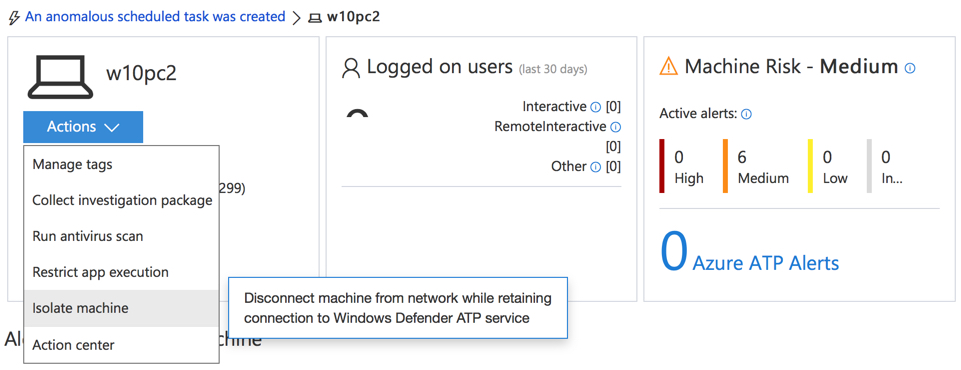
When Windows Defender ATP detects a threat, it has the capability to automatically respond and attempt to remediate the threat. But in some cases, automatic remediation will take some time, or it will be unsuccessful and require manual investigation that takes longer. During that investigation, it makes sense to blocking access to corporate apps and data from the compromised endpoint.
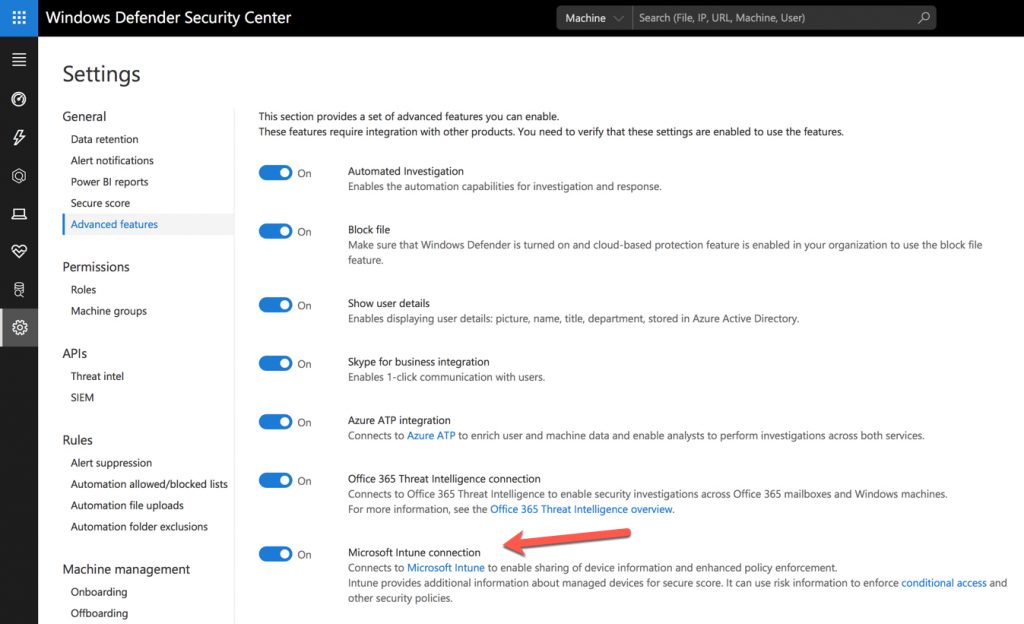
You can achieve that by enabling Windows Defender ATP integration with Intune. The Intune connection is enabled in the Windows Security Center.
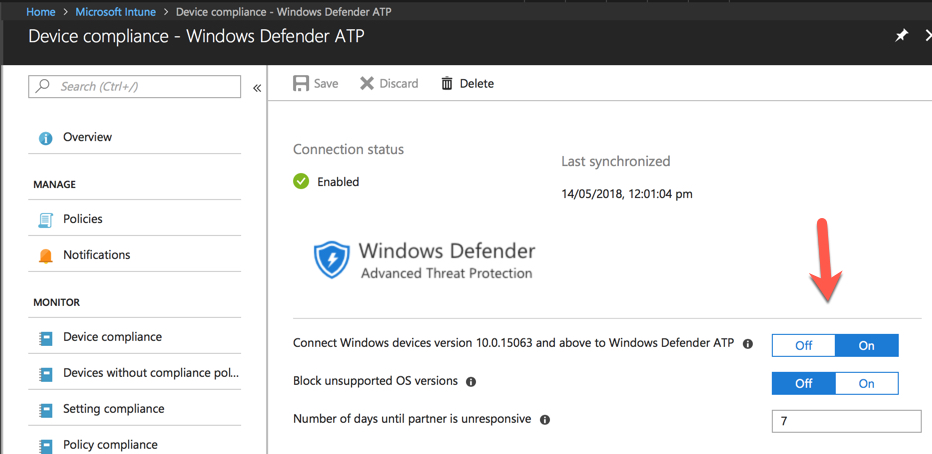
Within the Intune blade of the Azure Portal, you can then enable the connection of supported Windows devices to Windows Defender ATP, allowing their device threat level to be evaluated as part of the Intune compliance policies.
The device threat level is an option when configuring compliance policies in Intune. You can decide which threat level is still considered compliant for your organization. For example, some organizations might be happy to allow access from devices with a Low threat level, but not from Medium or above. Other organizations will require all devices to be at a Secured level, and block any other threat level.
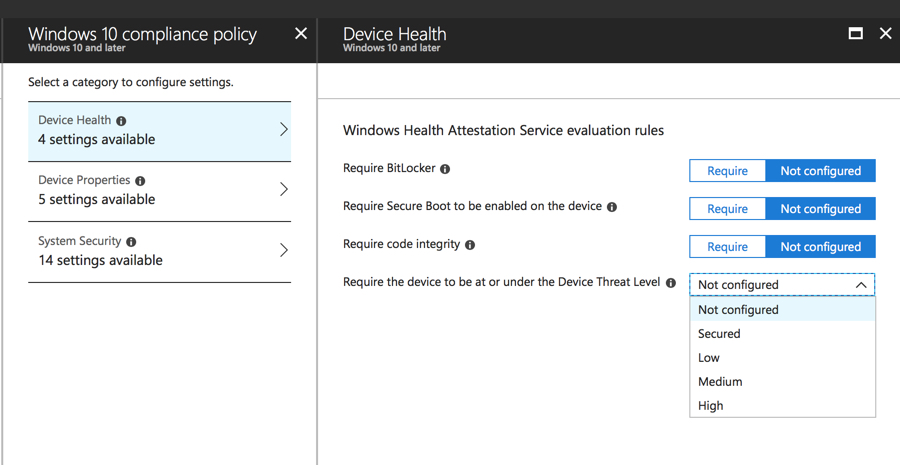
After you’ve made the device threat level a factor in device compliance, any conditional access policies that require device compliance will block the user from access Office 365 services from a device that has been compromised according to Windows Defender ATP. After the compromised device has been remediated, either automatically or manually, and the threat level decreases again, conditional access will begin allowing the device to access Office 365 services again.



Hi Paul,
Do you know the possible reasons that could disable the connection between Intune with Windows Defender ATP automatically?
Thanks in advance,
Tim