Managing the allocation of Office 365 licenses has been a pain point for many customers. For smaller tenants with simple requirements, the allocation of licensing can either be handled manually on an as-needed basis using the Office 365 admin portal, or built in to a provisioning script or system. For larger tenants, automation is essential, as manual methods are far too time-consuming for any environment with a high rate of change (e.g. dealing with new and departed users, or licensing sub-features and extra applications). In fact, quite a few Office 365 customers have remarked to me recently that managing licenses is one of their biggest challenges, and they’ve invested quite a lot of time into scripting solutions based on Active Directory group membership.
Well the good news, or perhaps bad news considering the investment of time they’ve already made, is that Microsoft has now released Azure AD group-based license management for Office 365. The feature is currently in Preview.
Getting Started with Azure AD Group-Based License Management
Microsoft has made group-based license management available through the Azure portal. Choose Azure Active Directory from the list of services in the portal, and then select Licenses.
The groups that you can assign licenses to can be created in Azure AD, or synchronized from on-premises Active Directory. The license assignments can be static (i.e. to the members of a group) or dynamic (e.g. based on user attributes such as ExtensionAttribute1). For this demonstration I’m using groups synchronized from on-premises Active Directory with static membership.
The groups I have created will allow me to demonstrate basic license assignment, as well as a more granular approach, and how license assignment is cumulative for users who are members of multiple groups. I’ve created groups named:
- Licensing_Office365_E3_Base
- Licensing_Office365_E3_Teams
- Licensing_Office365_EMS_E3
My goals are:
- To assign Office 365 E3 licenses with what my organization considers “base” functionality, which is all E3 features except for Yammer, Sway, StaffHub, and Teams
- To assign Teams access only to specific users in the organization, due to Teams currently being in Preview
- To assign EMS (Enterprise Mobility + Security) E3 licenses to specific users only
My tenant currently has licenses assigned to users, so I will need to transition users from direct license assignment to groups-based licensing without disrupting their existing services (e.g. Exchange Online mailboxes).
Assigning Licenses to Groups
After navigating to the Licenses section of Azure Active Directory in the Azure portal, you can view the list of products that your organization currently has licenses for.
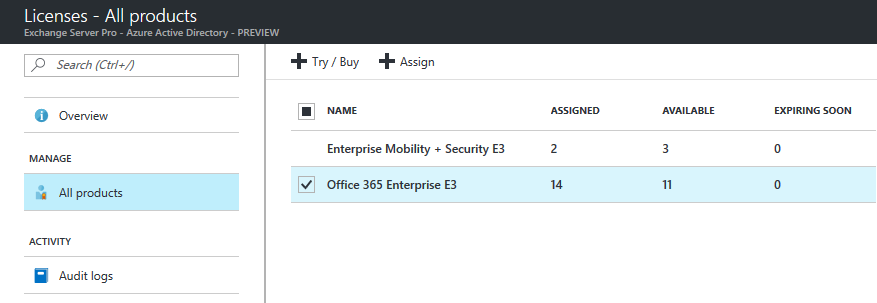
Select a product license and click on the Assign button. From the Users and Groups selection, choose the group that you want to assign licenses to, and then click on Select. You can select multiple groups at this stage, for example if you were using department-based groups to assign product licenses to users. I am using product-based groups instead. Either approach will work, it really just depends on how your organization views license management.

In the Assignment options you can select the sub-features for the license that you’ve chosen to assign to the group. I’ve turned off StaffHub, Teams, Sway, and Yammer for this demonstration.
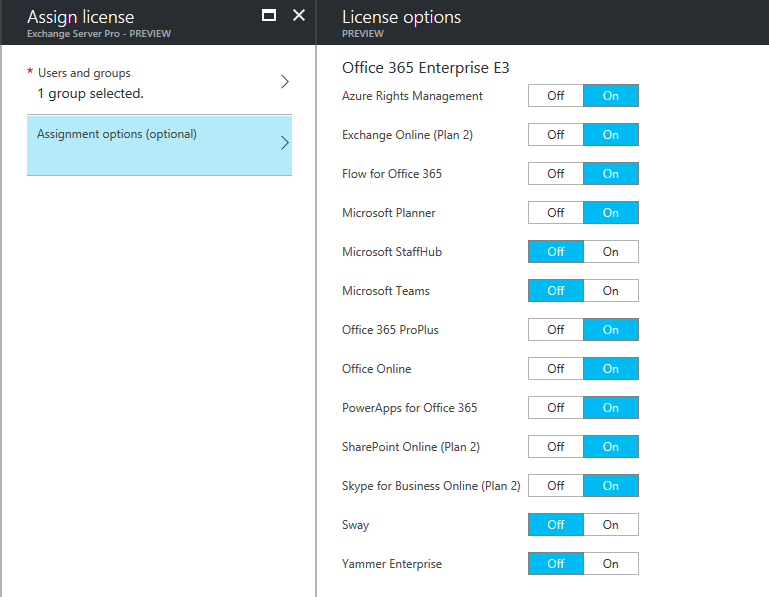
Click OK when you’re happy with your selections, and then click Assign to create the license assignment. If there’s any errors at this stage you’ll receive a notification in your Azure portal. On my first run through this feature I was getting a notification that “Licenses could not be assigned or removed due to an error”, which I was unable to work out a solution for.
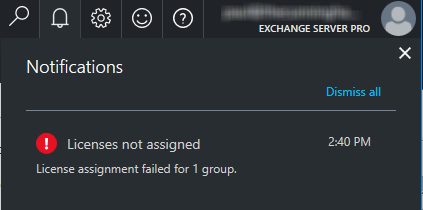
It appears that the problem was that I was using a Microsoft Account associated with my Azure subscription, and even though the account has access to the Office 365 tenant’s Azure AD (and is a Global Admin) it is not able to be used for administering groups-based license management. Logging on to the Azure portal with the Office 365 tenant admin account allowed me to continue without errors. A strange issue that might impact partner or delegated permissions scenarios, but nonetheless I was able to proceed with the correct account.
After completing the steps above I went back through the same steps to create a license assignment for Teams only, and another for EMS E3. For Teams, I created a license assignment that only enables Teams, which will allow me to fully demonstrate the cumulative nature of groups-based license management.
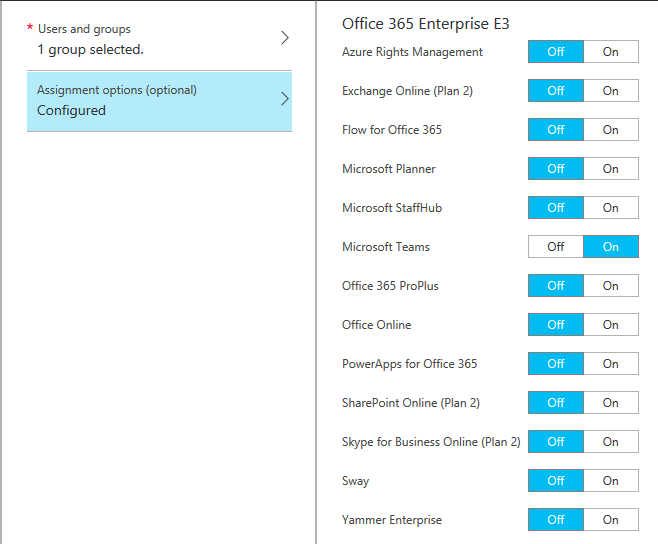
Transitioning from Direct to Groups-Based License Management
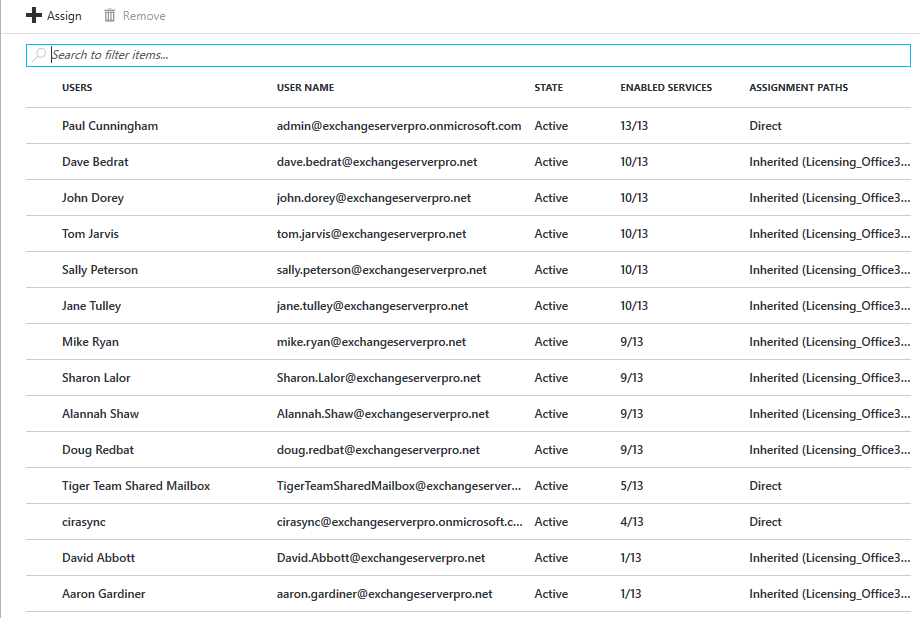
A few minutes after setting up my group license assignments the Azure portal showed my users’ license status as below. Notice how most of the users have both direct and inherited assignment paths. The names of the groups that licenses are being inherited from, such as Licensing_Office365_E3_Base, are also displayed. Notice also that most users have the fully 13/13 services included in an E3 license showing as enabled.
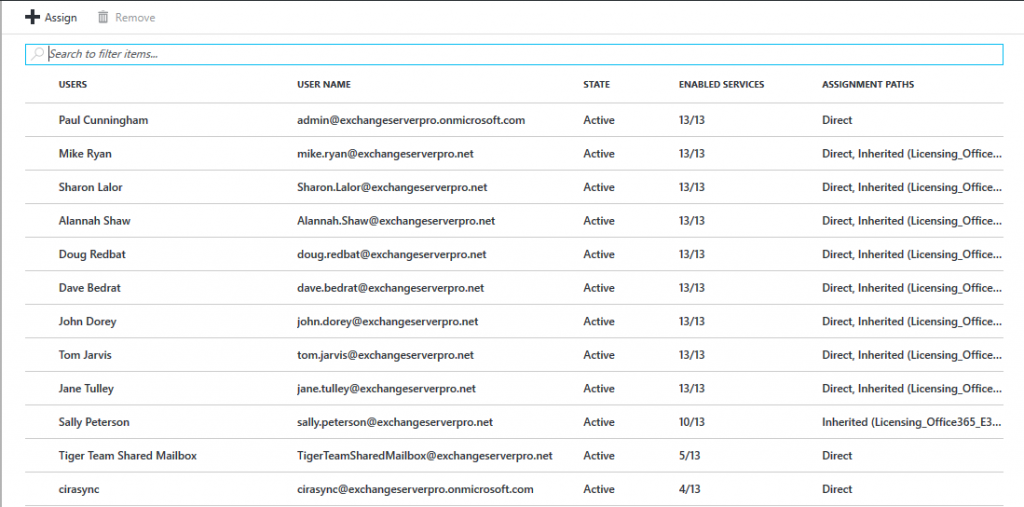
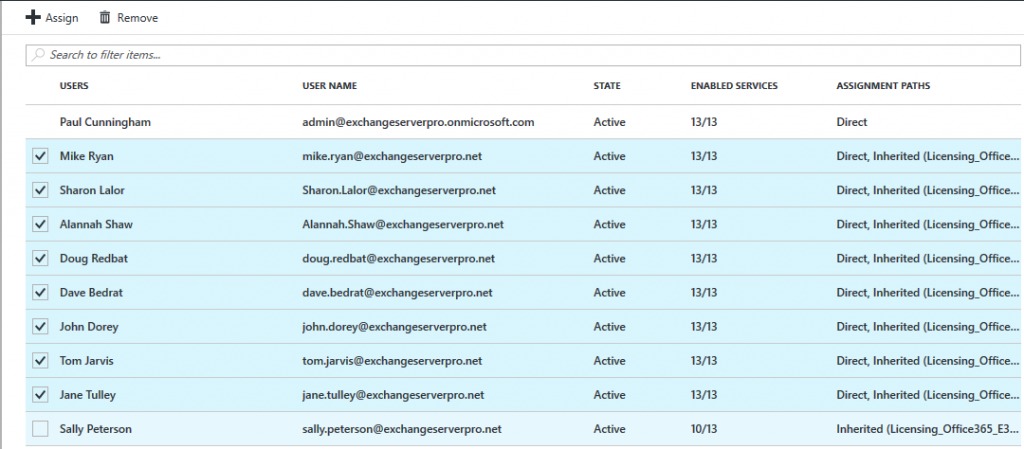
To transition from direct to groups-based licensing, all we need to do is remove the direct license assignment. This is as simple as selecting one or multiple users who are assigned a specific type of license, and then clicking the Remove button. In the example below, the list of E3 license holders is shown, and I’m removing the direct assignment from the users who also have an inherited assignment via a Group.
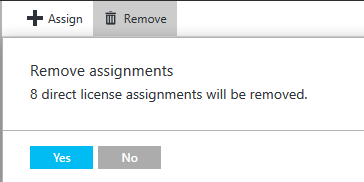
After clicking Remove you’ll get one final prompt before the change is made.
This transition is best performed in stages so that you can be confident that you’re not disrupting your users’ access to services. If you’re transitioning a full E3 direct license to a full E3 group-based assignment, then the risk is fairly small. However in cases where you’re adjusting the number of services that the user has access to, you should be more cautious.
Cumulative License Assignments
As I mentioned already, I am using multiple groups to assign licenses. Most of the users in my organization will have a subset of the E3 license features, and a select few will also get access to Teams. After removing the direct license assignments, the groups-base licensing is in full effect. You can see below that:
- Users who are only members of the Licensing_O365_E3_Base group get 9/13 services, for example Alannah Shaw
- Users who are members of both Licensing_O365_E3_Base and Licensing_O365_E3_Teams get 10/13 services, for example Dave Bedrat
- Users who are only members of the Licensing_O365_E3_Teams group get 1/13 services, for example David Abbott
This is the level of control that customers have been asking for, so it’s great to see Microsoft delivering on it.
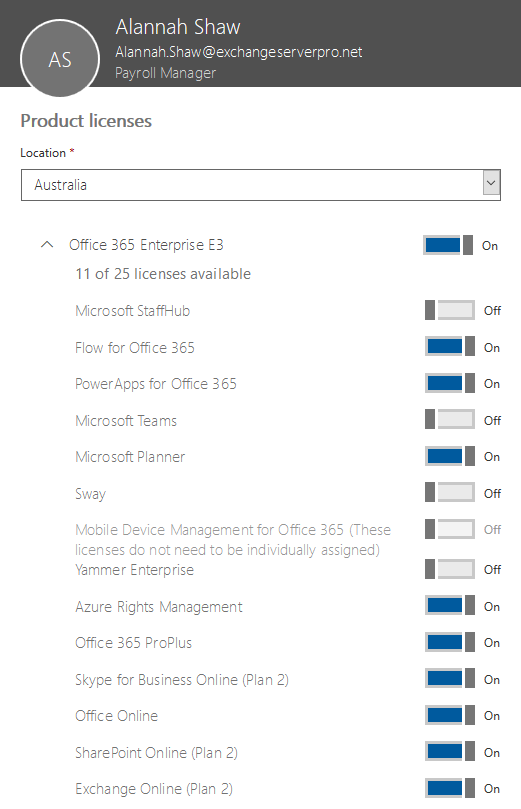
The license assignments are also visible in the Office 365 admin portal, and reflect the same sub-feature license assignment that you can see in Azure. For example, Alannah Shaw has access to most E3 features except for Teams, Sway, StaffHub, and Yammer.
FAQs, Limitations and Caveats
Group-based license management is currently in Preview, and as I’m writing this article the following limitations and caveats apply:
- The features, behaviors, or availability of group-based license management may change between now and when it becomes generally available.
- If a user is assigned a license directly as well as via group membership, they only consume a single license.
- An Azure subscription (trial or paid) is currently required to use group-based license management.
- Although new and modified license assignments take effect within minutes (e.g. enabling Sway in an existing license assignment), there are situations where a license will not assign automatically, for example if you have more members of a group than available licenses, or when license assignments conflict. Notifications in the portal will advise you of how to remediate the issues, and there’s a Reprocess button available as well to reapply assignments after fixing issues.
- Membership changes to groups synchronized from on-premises Active Directory will not take effect until after the next sync cycle.
- Users can have a mix of direct and group-based licenses assigned, for example an E3 license that is group-based, and an EMS license that is directly assigned. Group-based license assignments can only be managed via the Azure portal, and will cause an error if you attempt to modify them via the Office 365 admin portal (at least for now).
- When new sub-features (or sub-SKU features) are released, Microsoft may enable them automatically by default, requiring you to revisit your group-based license assignments to disable new features from time to time. This should encourage you to keep your group-based license assignments as simple as possible.
- Nested groups are not currently supported.
- Removing a user from a license group will result in services being set to a “suspended” stage instead of disabled. Microsoft is using this approach to avoid data loss issues due to accidental removal of group members. You can expect in future that suspended services will eventually age out to a disabled state and data will eventually purge as it does today for de-licensed users.





Pingback: Microsoft Graph PowerShell SDK: User and Group Operations
quote:
Removing a user from a license group will result in services being set to a “suspended” stage instead of disabled. Microsoft is using this approach to avoid data loss issues due to accidental removal of group members. You can expect in future that suspended services will eventually age out to a disabled state and data will eventually purge as it does today for de-licensed users.
This isn’t correct any more. We have AD groups in our tenant and multiple license tiers. This week we found that removing a user from A1 and putting them into A3 can result in an unrecoverable empty mailbox. A support ticket to MS confirms the data is unrecoverable as we “removed the old license, saved and then applied the new” as far as the audit logs show.
HI
We run a hybrid environment do we create the groups in ONPrem AD and then let them synch up and then in azure assign the license to that group. Or do we creatw the group on azure assign the license? If so what do we do for the ONPREM AD group how does the correlation work?
Also we already have 300+ users each assigned a license directly would we have to remove those licenses or can we leave them as they are?
We have a security group we add users to that syncs for licensing, which is already too large to parse in a normal time frame via powershell. We are going to expand our licensing to 25,000, do you just cram them into one security group? What is the best practice for this?
I’ve read the powershell sample page before and it’s only about getting groups with licenses and remove direct licenses assigned to user.
Do you know any any way to assign lienses to a group with the options to disable some service plans?
For direct license assigning, it can be done with PS like below, but can’t find how to do it when using group based licensing.
Set-MsolUserLicense -UserPrincipalName $uUPN -AddLicenses $SKUID -LicenseOptions $options
Hello,
This is good. Thanks. Once it is all configured as you need (I have mine configured for 39k users… my question, is there any way to powershell / export the configuration to CSV or some other fashion? I’d like to capture and monitor any changes that may happen from other admins, good or bad, and at the very least have something to rely on if it all fell apart for some reason.
Hi,
are nested groups possible today?
Hello,
I am currently using group-based licensing (from on-prem sync to the cloud) to “turn-on” specific plans within an E3 license. This part works great! But, when I remove someone from the Group I noticed that the plan is not being disabled/turned-off after the next sync? Is there something additional that I need to do in order to have the plan turn-off after removing the user from the group?
You could login to AzureAD, navigate to the group and hit the reprocess button manually if you needed it done quickly
For those who came across this post, reference the following Microsoft Docs links:
https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/licensing-groups-migrate-users
https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/licensing-groups-change-licenses
(etc.)
This is a great feature… that is tied to an extremely overpriced Office365 Add-on. License management should be included for the crazy amount of money that E3 licenses add up to.
We’re moving to group based licensing. When I think I have all the groups done I want to pull the list of users and see their assignment paths to make sure there are no direct only users left. I cant find a way to export the list of users including assignment path. We have 80k accounts so trying to scroll through the gui is not an option.
Do you know a way to do this?
I was also hoping that you could select the group and click remove license and it would only remove the direct one like it says it will however it appears to remove the group instead.
This is indeed a very good process. However I would like to know what might happen in below situation
1. We create a group. the Members of this group will get licenses only for Sharepoint Online, Azure MFA and Office pro plus. We assign licenses to the group accordingly
2. Once we assign licenses, we no longer need this group .
3. Hence, we delete the group.
Will the members of the group lose all licenses ?
They would lose their licenses. The group is associated with the licenses, and the licenses are applied to the members. If you delete the group, you could run into problems. (I am looking at it from a synced group perspective).
If you have a group that was deleted, and if you have licenses associated with it, it will have trouble deleting in AzureAD. The best way to delete a group associated with licenses is to remove the license association with the group in AzureAD, then let a sync go through, then you can delete the group on prem. The next sync would then delete the group in AzureAD
Q1: What does a license in a “suspended” state entail. Does this take up an actual license in the portal? Will O365 automatically do something with this license?
Q2: If a user has both direct licenses and group assigned licenses.. will there be any issues with mailboxes be de-provisioned… Just need to ask as I need to make sure this will not impact business.
Better yet for Q2: Do I need to remove the direct licenses? And just make it so that all new users added from here on out are provisioned automatically?
Hi,
I want to ask if the group based license management can also be done in powershell?
I’m trying to find some scripts that could for example disable certain services within the inherited licenses, so far I am only able to find management on directly assigned licenses.
Thank you.
Is there a way to get an email alert when there is an issue with assigning licenses using this method? We have this setup for our organization (25k+ users) and there are issues occasionally where helpdesk will upgrade a user but fail to take them out of the orginal licensing group. So this causes an issue that we can only see by logging into the Azure portal and going to the section “groups with licensing assignment errors”. Is there any way to get alerted on this via email alert?
There’s PowerShell samples here:
https://docs.microsoft.com/en-us/azure/active-directory/active-directory-licensing-ps-examples
So it would just be a matter of taking that output and creating email messages via PowerShell to alert you to any results that you want to be alerted to.
Hey there Paul, thank you very much for posting this. Following along with your instructions I am trying to locate the Tenant Admin account.
“Logging on to the Azure portal with the Office 365 tenant admin account allowed me to continue without errors. A strange issue that might impact partner or delegated permissions scenarios, but nonetheless I was able to proceed with the correct account.”
I am not able to locate the tenant admin account, I have Global Admin role added to my separate admin account but I am unable to change the options here.
Would we need to use the billing administrator account for this, or do we use the actual account used to configure the tenancy.
By tenant admin I mean a global admin account in the tenant.
Sigh, created a group with my 1500 users took, almost 30 minutes before the Direct/Inherited started showing up on their objects.
Now is there a way to powershell remove any direct licensed objects without having to go through all 20 panels of the gui? I keep clicking a bunch of them, only to click the wrong spot and have all my selections disappear.
OK, I found when I run a
get-msoluser -userprincipalname (person) | select -expand licenses
…
GroupsAssigningLicense : {7abf4c7a-8dbd-4d80-b693-50379774fbeb,
a1a05b81-a72d-4b49-a277-e8a6f3607417}
…
I can find that the ‘groupsassigninglicenses’ field has 2 groups populated, some random number (i.e. a direct assigned group), plus the group, ObjectID, that I created.
PS PS:\> get-msolgroup -all | ?{$_.displayname -like “AssignO365License*”}
ObjectId DisplayName GroupType Description
——– ———– ——— ———–
a1a05b81-a72d-4b49-a277-e8a6f3607417 AssignO365… Security
By using a script to blanket remove licenses, it only removes the direct group object ID.
Hello,
Is there a difference in Office Groups created in Azure AD and in the O365 Portal? Office Groups that I created in Azure AD can get a license, but I do not see Office Groups created on the O365 portal by licensing
Sounds like Groups (big) vs groups (little G) is the issue.
A Group is an Office 365 collaborative feature. It creates a shared mailbox, SharePoint site, OneNote, Teams, Planner, etc. It can’t be used to assign security permissions.
A group is a security group similar to what we have in on-prem AD, and can be used to assign security permissions.
Only groups (little G) can be used for Azure AD group-based licensing, not Groups.
Paul, thank you for your reply.
When I’m in Azure AD and I create a group there I have the ability to enable Office features. When I do this, I have a Group. This G(g)roup has the same functionalities as a Group made in the O365 portal. However, I can now also use the G(g)roup, made in Azure AD, for the license piece.
When I compare in PowerShell a group created in Azure AD and in the O365 Portal, I do not see any differences except the alias.
How can I see the difference between a G(g)roup made in Azure AD and a Group made in the O365 Portal.
A group made in Azure will be only a security group. If you look in the O365 Admin portal under Groups, you’ll see a list of everything in the tenant. These will show if they are “Office 365” (Big G) Groups, or “Security” (Little g) groups.
Hello,
In our environment we assign licenses using groups
I would like to log the changes done to Licensing groups
Is there any possibility to do it
Thanks
Yes, look into auditing of Active Directory group membership changes.
Would be interested in your thoughts or insights on this issue – I work for a Higher Education institution and we utilize AAD Connect to sync our on-prem AD with Office 365. Our licensing is limited, and we have put together some procedures to utilize dynamic groups in Azure AD to take care of those. We recently obtained the license for Exchange Online for Alumni – this gives former students (inactive for 1 year) lifetime access to their email but not the Office 365 suite. We use an Extension Attribute to denote which license currently registered students receive as well as those that are in between current and alumni status. Those dynamic groups are working great and assigning licenses beautifully.
The process to change students to Alumni is to move them to a non-syncing OU – this puts them into the Recycle Bin in Office 365 on the next sync. We run a PowerShell script to restore those mailboxes to an In-Cloud only state. After that is complete, we change the CustomAttribute for the dynamic grouping via PowerShell for Exchange Online using the Set-Mailbox command. Although it successfully changes the value in the cloud, the dynamic group the students had before being deleted are still attached to their in-cloud only accounts and the dynamic grouping does not work. Therefore, the group licensing is incorrect – I have tried changing it by hand online as well, but no luck.
I have been unable to find any documentation online regarding whether or not this should work, but I have tested it every which way I know how, and it almost seems that only synced users modify appropriately even though the other users exist in Azure AD. Is there some sort of disconnect between Exchange Online and Azure AD? It is odd to me that all of the attributes reside with the mailbox and not with AD – completely backwards mindset than what I am used to on-prem.
My only thought on resolving the issue (if there is truly no way around it) would be to change the Extension Attribute on-prem, allow a sync to happen which would apply the group licensing as expected. After that is done, complete the process as previously mentioned so, when the student is reactivated from the recycle bin, the correct license group is already attached (since when I restored them before they kept the previous group).
You mention both extension attributes and custom attributes, which are two separate things (Get-Mailbox will list both). Which one are you using for the dynamic group?
AzAD and ExoDS are two separate directories but they are supposed to be in sync. But if you’re changing the wrong attribute that might explain the issue.
Another thing to consider is that maintaining the on-prem AD object for alumni might make things easier and more consistent for you to manage. This process you’re using of soft deleting and then recovering accounts seems awkward and risky to me.
Great article!! What happens to users who are on litigation hold? So when the user leaves the org and litigation hold is applied, will it still remove the license based on group membership or that will be a manual task for the administrator?
If you remove the license after applying lit hold the mailbox should still be preserved as an inactive mailbox. You should test that scenario though, if you’re depending on it.
https://technet.microsoft.com/en-us/library/dn144876(v=exchg.150).aspx
I’ve started using this where customers have multiple profile groups of users who have various different licensing requirements or have thousands of users world wide.
Its great as when you create the on prem user and remote mbx you no longer need to then log into the portal to assign the license or script it like i had in the past.
1 question tho… a customer of mine had a paid Azure AD Subscription for 200 users, however this feature was then available to all 13,000 users in Azure AD. I looked through the above link but cannot see what the caveat is here. is there one? ie if I have a paid Azure AD Sub for even 1 user is this feature available for all users in the tenant?
Thanks
Yeah for some features a single license is all it takes to light up a feature. But that isn’t the same thing as being license compliant, so your customer still needs to make sure they have the right number of licenses for the users they are using a feature with.
When this feature will go available?
How often does Azure Ad process the license assignment?
How do you edit or remove the group based assignment?
How did you get to where it displays the users and their licenses?
I did not see where I could choose an extensionattribute only groups. Is that a licensing feature? Did you use Azure AD Premium? I only have Azure AD Basic perhaps it is less functional?
Processing is nearly instantaneous.
Editing, removing, and all other navigation for this feature is found in the Licenses section of Azure Active Directory in the Azure portal.
There’s an example of using extension attributes here:
https://docs.microsoft.com/en-us/azure/active-directory/active-directory-licensing-group-advanced#use-group-based-licensing-with-dynamic-groups
I don’t have Azure AD Premium in the tenant I used for this demo.
I’m not seeing anything close to instantaneous, whether I let AD sync the group membership or attempt to force the situation by triggering the reprocessing manual in Azure.
I’m having this issue also. I need a way to “reprocess” through powershell so it can be automated.
Hi Paul,
Great Article. Just one question that you might know the answer to.
Lets say Exchange on-prem is setup in a hybrid environment with Exchange Online. In this case it is best practise to create all mailboxes on-prem first and then migrate to Exchange Online. Otherwise if the mailbox is created directly in Exchange Online, the on-prem exchange doesn’t know anything about the mailbox.
Picture the scenario where Group Based Licensing is setup. In this case members of the group get assigned an Exchange Online license.
The user account gets created on-prem and added to the appropriate security group that assigns a license. Prior to their mailbox being created on-prem, Azure AD Sync runs, and syncs the user to Azure AD. A license then gets assigned through the automatic group membership. Since there is no on-prem mailbox for the user (yet anyway), Office 365 automatically provisions a Exchange Online mailbox. the IT team finish the new user setup by creating a mailbox on-prem, and attempt to migrate. But now you end up in the situation whereby there is both a mailbox on-prem and in Exchange Online.
In an ideal world, the setup procedure on-prem would be scripted so that it creates a AD user and mailbox at the same time. But lets say it’s not. Do you see a way around the above scenario?
Regards,
Peter
There’s no real magic here. Either change your provisioning workflow to assign them to a licensing group after the mailbox is created, or change your provisioning workflow to account for the mailbox being created in EXO instead of on-prem.
There’s nothing that says mailboxes should be created on-prem then moved to EXO as a best practice. Create them wherever you want them to live. The only caveat is shared mailboxes, which don’t need a license anyway so that’s not applicable to your situation.
Does Azure AD also provision other attributes (like msExchRecipientType or other Exchange specific attributes)? Because if mailbox is created directly in Office 365 without setting up msExchRecipientType, these won’t be visible in on premises EAC and we’d end up with another script still running (though smaller).
You can assign the group membership by verifying few attributes that indicates that the mailbox is created onprem
For example you can look for the homeMDB attribute Get-ADUser -filter {((homeMDB -notlike “$null”) -and (enabled -eq “true”))
Paul,
Great article. We have a few test environments here that we would like to time box the use of licenses in. For example, allow the user to have access to a license for 180 days and then reclaim it, or reclaim a license that has not been used in 180 days. Have you come across a way to do this with Azure Ad Group Based Licensing?
Groups-based licensing assigns and removes licenses based on group membership. If you can orchestrate the adding/removing of group members based on those 180 day blocks of time, then groups-based licensing will handle the licensing back end stuff for you. But right now it doesn’t have timer-based licensing as a native capability.
Hi Guy
Do we need azure ad license to assign this policy (Office 365 License Control with Azure AD Group-Based License ) ?
Thanks
See my answer to the comment above yours.
Hi
How is this licensed? Do i need to pay for this functionality?
regards
peter
Check the end of Microsoft’s post here:
https://blogs.technet.microsoft.com/enterprisemobility/2017/02/22/announcing-the-public-preview-of-azure-ad-group-based-license-management-for-office-365-and-more/comment-page-1/
When I’m at the group selection window I can’t find any of my On-premises AD Groups. We have an hybrid configuration and only have Dirsync. Is it possible that this feature only works with Azure native groups?
It works fine with groups synchronized from on-prem AD, in fact that’s what I demonstrated in my post.
Hi,
We want to set up F5 Load balancer for the office 365 SMTP traffic. Please let us know if there is any solution to implement this
You should ask F5, I’m sure they’ll have documentation to guide customers on that any many other scenarios.