Packaging Some of the Many Policies Beloved by Teams
Group policy assignment functionality is available in the Microsoft Teams admin center and the Teams PowerShell module. Group policy assignment is a solution for a problem faced by many organizations, particularly large enterprises, who find it difficult to achieve consistent assignment of Teams policies to user accounts.
Read More: Seven Years Too Late, Microsoft Realizes the Reality of Group Sprawl.
The Many Policies of Teams
Teams loves policies. The Teams PowerShell module included 47 cmdlets with names matching a pattern of Get-Cs*Policy. Although many of these policies are a little obscure and might never be accessed or changed in a tenant, they do exist. When an administrator edits a user account through the Teams admin center, they can tweak sixteen different policies to affect how the user interacts with Teams (Figure 1).
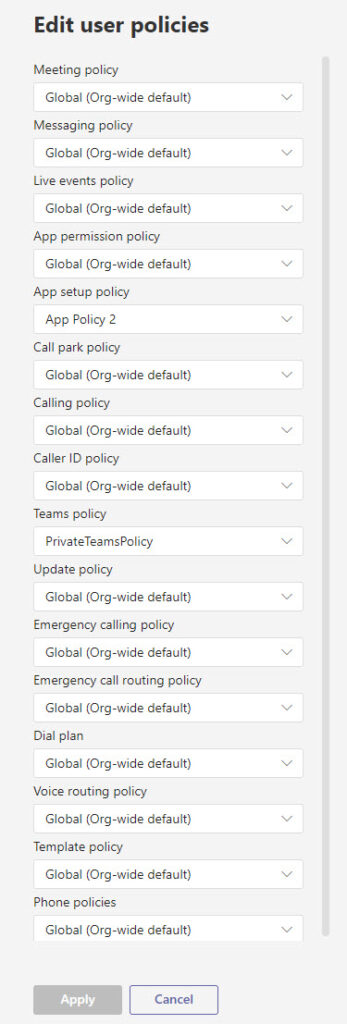
Many of the policies used to manage Teams today originate in the calling and meeting heritage of Lync and Skype for Business Online, which use a similar policy-based management framework. There’s a lot to like about policy-based management. Applying a policy to an account to control functionality is more consistent than tweaking individual account settings. Changes are easily made by updating a policy instead of updating multiple accounts, and so on. But when so many policies exist, it can be hard to understand which policy controls what setting.
Policy Assignment to Many Users
Group-based policy assignment means that a set of users receive a package of Teams policies. The scope for the set of users comes from a distribution group, security group, or Microsoft 365 group. The package is composed of several Teams policies. Assigning the policy package to the group means that Teams assigns the policies in the package to the members of the group. Assignments only occur for accounts which are direct members of the group. Accounts in nested groups don’t receive assignments.
As the group changes, Teams assigns the package to new members and removes the package from those who leave (as we’ll see later, this didn’t happen in my tests). It’s a helpful solution to the problem in situations where you want to be sure that specific users see certain apps or are allowed to switch into the Teams public preview mode to see new features.
Bulk policy assignment is another solution. In this case, the administrator identifies a set of users (perhaps in a CSV file) and a background job assigns a policy to the target accounts. It’s the equivalent of a manual assignment of a single policy to an account repeated for each user.
Licensing
Users don’t need any additional licenses to receive assignments through the set of predefined policy packages included in Teams. However, as announced in MC244607 on March 16, once you create custom policy packages, users who receive those packages need Teams advanced communications licenses (Microsoft 365 roadmap item 70776). Quite why Microsoft demands this expensive license for what many would consider to be a fundamental management capability is not clear.
Administrators can’t amend the predefined policy packages to add or remove policies. However, they can edit the details of the individual policies in the packages. For instance, the Frontline Manager policy package includes meeting, messaging, live events, app setup, and calling policies. You could edit the package to amend the details of the include policies (but not the policies themselves) to customize them to meet organizational requirements. Whether this creates an additional licensing burden is another matter.
Let’s leave the topic of licensing aside and examine how to create a custom policy package.
Creating a Custom Policy Package
Creating a new policy package is straightforward (here’s Microsoft’s documentation). As shown in Figure 2, it’s a matter of choosing the policies you want to assign to users. In this case, I’ve opted for four of the ten policy types supported for this form of assignment. The other policy types are Calling, Caller ID, Call Park, Live Events, Voice Routing, and Update.
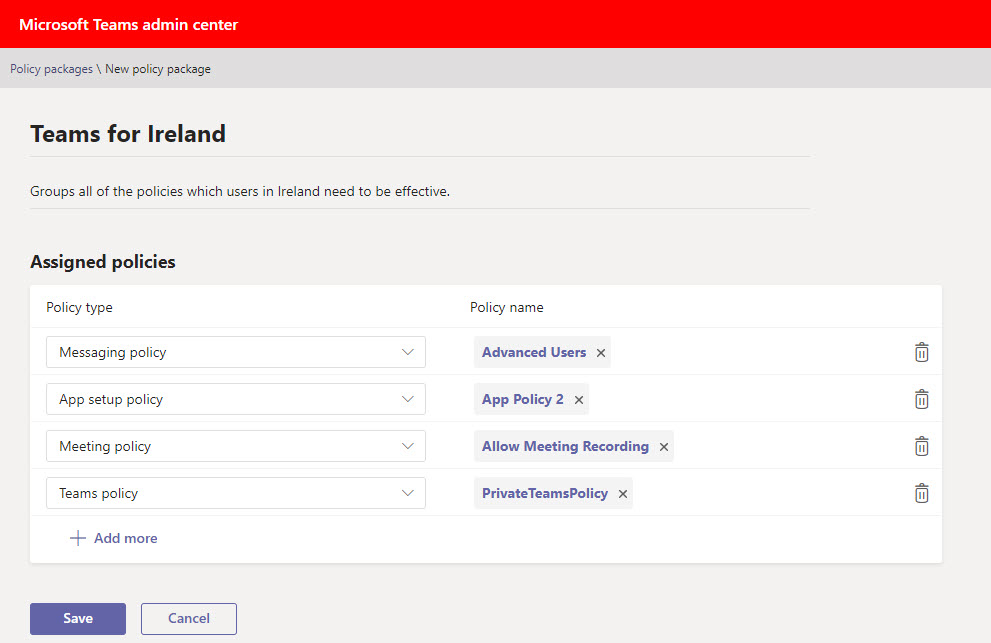
The next step is to assign the new custom policy package to one or more target groups. I used distribution lists for this purpose, but you can also use a Microsoft 365 group or security group. Note that policy assignments only work for direct members of the distribution list; members of nested distribution lists don’t receive assignments.
A policy package can be assigned to multiple groups, but a group can only be assigned one policy package. However, you can’t assign a policy package to multiple groups at one time. Instead, each assignment must be processed individually by selecting the target group. This action allows Teams to calculate the priority (or ranking) order for the assignment (Figure 2) based on what’s already in place.
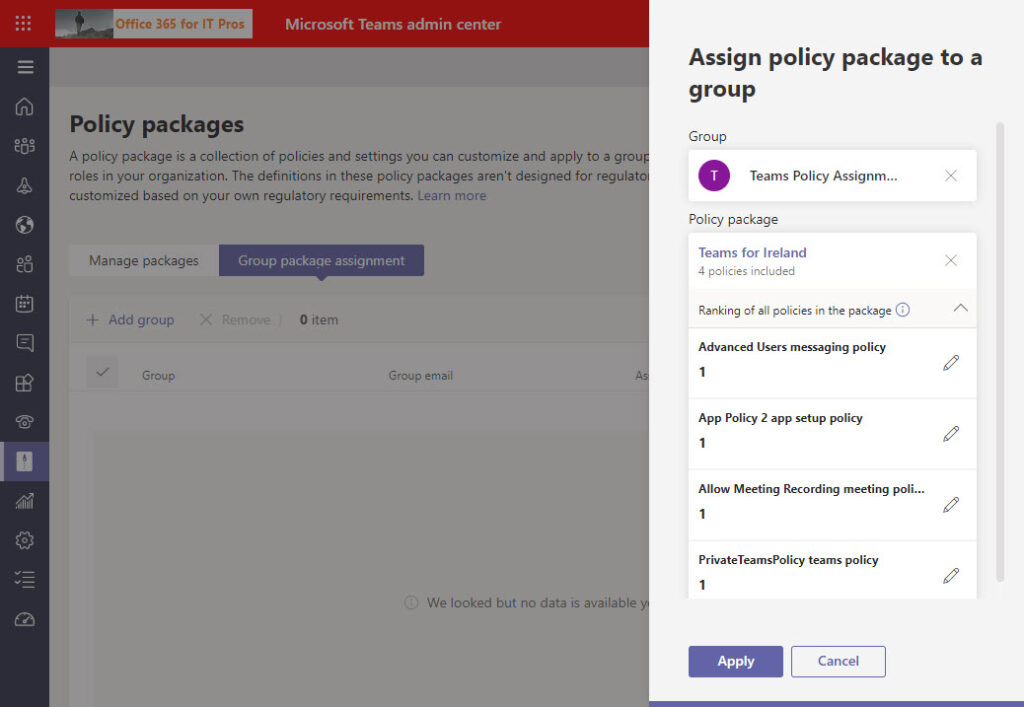
The priority order is important because it’s used by Teams to know which policy to apply when several policy assignments exist for an account. The existence of the priority order allows assignment of several policy packages to an account with a known outcome. The rules of precedence are:
- Manual assignments always win. In other words, if an administrator assigns a policy to an account, that assignment takes precedence over any group assignment.
- If a manual assignment doesn’t exist, the group assignment with the highest priority takes precedence.
- If no manual or group assignments exist, Teams applies the default (global) policy.
Teams adjusts the priority given to assignments as people join or leave groups or when packages are assigned to or removed from groups. This is done automatically by the background process responsible for tracking policy assignments due to group membership.
After a policy package is assigned to a group, a background process applies the policies covered by the package to the accounts in the target group. Team policy assignments are notoriously slow to become effective. There’s no indication in the Teams admin center about the progress of the background job, so the only way to track assignments is to examine user accounts through the admin center (Figure 3) or PowerShell.
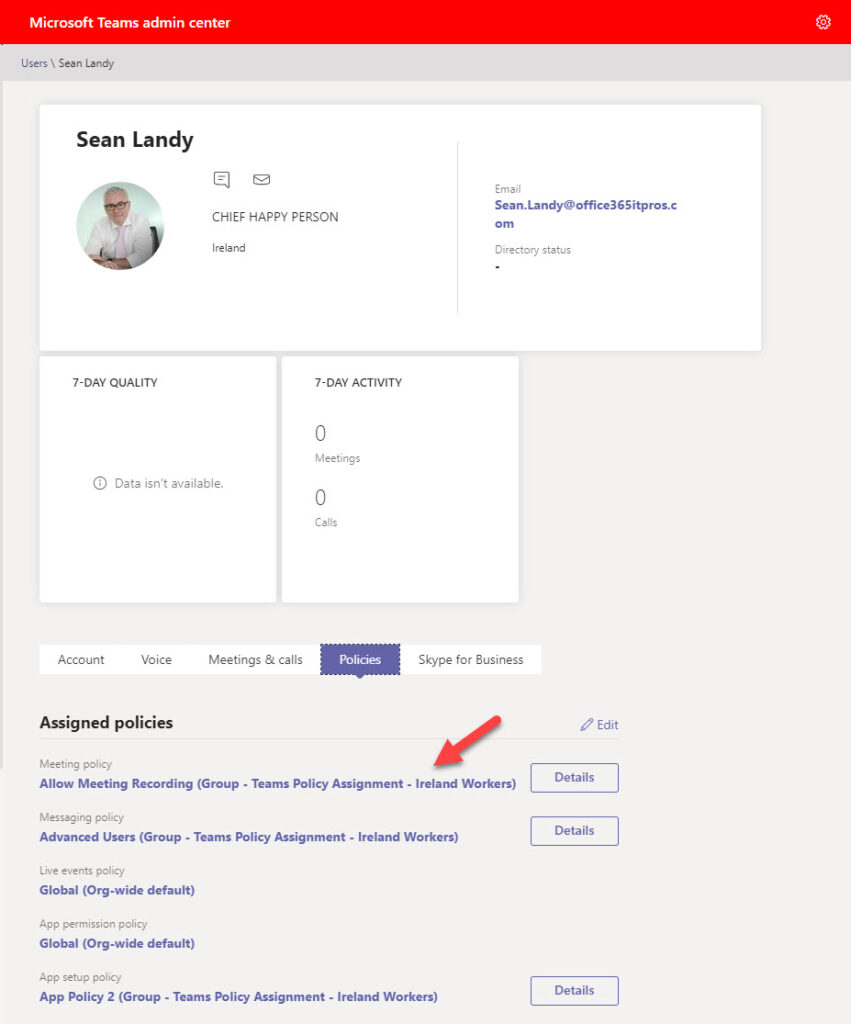
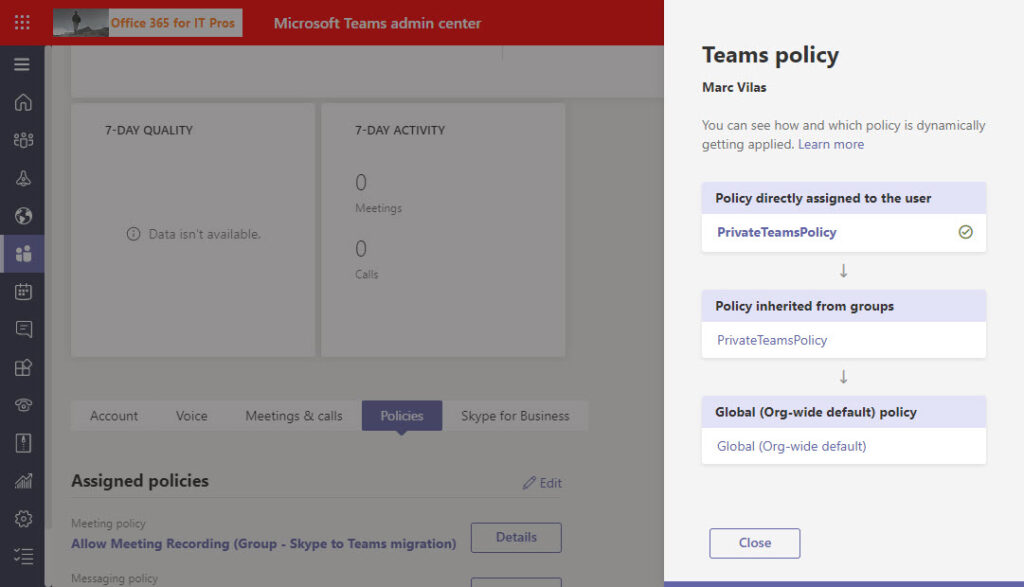
Clicking details for a policy shows how Teams applies the policy based on the rules of precedence (Figure 4). In this case, the user has a direct assignment and inherits an assignment from a group. The direct assignment has precedence.
Individual Package Assignment
If a user account doesn’t come within the scope of a group policy assignment, you can edit their account to assign a policy package manually. Each of the policies included in the package is assigned to the account as if an administrator had assigned the policies directly.
The Odd State of Updates
Over time, the policies assigned to accounts also change. Microsoft’s documentation says, “As members are added to or removed from a group, their inherited policy assignments are updated accordingly.” My understanding of this text is that Teams updates group policy assignments to reflect changes to the underlying groups, a belief emphasized when Microsoft goes on to explain that the background process which handles updates “might take some time” to do the job. The memo might not have reached the background process because my observations based on multiple tests show that:
- Accounts receive group policy assignments when a policy package is first associated with a group.
- Accounts added to the distribution list do not receive the group assignment.
- Accounts removed from the distribution list did not have the policy assignment removed.
- Target groups removed from a policy package leave the policy assignments in place for the members of the removed group.
Either the documentation is incorrect, or the functionality doesn’t work as expected. At least, not in the week or so of my testing. It’s an odd situation for a premium feature to be in. I contacted Microsoft and discovered that a problem exists in processing changes made to distribution list membership. Everything works as expected for Microsoft 365 groups and security groups. I just happened to choose the group type which didn’t work so well. Microsoft expects to fix the problem soon.
For now, if you remove non-direct policy assignments made through groups, be prepared to do some manual cleanup to make sure that accounts have correct policy assignments.
Check Assignments with PowerShell
You can check the policy assignments to user accounts with PowerShell by running the Get-CsUserPolicyAssignment cmdlet. This cmdlet exposes some other detail of the policies applying to an account. For example:
Get-CsUserPolicyAssignment -Identity Sean.Landy@office365itpros.com | select -ExpandProperty PolicySource AssignmentType PolicyType PolicyName Reference -------------- ---------- ---------- --------- Direct MobilityPolicy MobilityEnableOutsideVoice Direct MeetingPolicy BposSAllModality Direct LocationProfile IE Group TeamsMessagingPolicy Advanced Users 35fc0413-e2a7-4b40-83ec-348f252b34b5 Group TeamsMeetingPolicy Allow Meeting Recording 35fc0413-e2a7-4b40-83ec-348f252b34b5 Group TeamsAppSetupPolicy App Policy 2 35fc0413-e2a7-4b40-83ec-348f252b34b5 Group TeamsVerticalPackagePolicy Teams for Ireland 35fc0413-e2a7-4b40-83ec-348f252b34b5 Group TeamsChannelsPolicy PrivateTeamsPolicy 35fc0413-e2a7-4b40-83ec-348f252b34b5
The three direct assignments shown at the top of the listing are automatic. For example, the location profile (IE = Ireland) comes from the user account location, which then determines things like the available dial plans. The meeting policy shows as BposSAllModality, a throwback to the past (BPOS = Business Online Productivity Services, the predecessor to Office 365). This was the name of the default Skype for Business Online meeting policy that’s found its way into Teams.
We can also see five group policy assignments. These are the four assignments (messaging, meeting, teams, and app setup) assignments from the package plus the package itself (TeamsVerticalPackagePolicy). The reference is the GUID for the group to which the package is assigned. We can check the group by feeding the GUID to the Get-Group or Get-AzureADGroup cmdlets. Here’s an example:
(Get-Group -Identity 35fc0413-e2a7-4b40-83ec-348f252b34b5).DisplayName Teams Policy Assignment - Ireland Workers
Many Ways to Assign Teams Policies
Between the Teams admin center, PowerShell, and bulk policy assignments, many ways exist to assign Teams policies to user accounts. Group policy assignment is a good approach to applying multiple policies to many accounts at the same time.
However, charging extra to use custom policy packages is an odd decision for Microsoft to make, especially as easy workarounds exist in both the admin center and PowerShell. It’s also regressive in that it’s surely better for Microsoft to help customers manage Teams policy assignments effectively. After all, Microsoft has created an array of policies which administrators need to master to work with Teams. Why should customers pay Microsoft for software to make that task easier?




