Practical 365 in Europe
At the end of March, Practical 365 traveled with the TEC European roadshow, traveling between three cities in Europe over a week, listening to experts talking primarily about security-focused topics aimed at improving your Microsoft 365, Azure AD, and Active Directory.

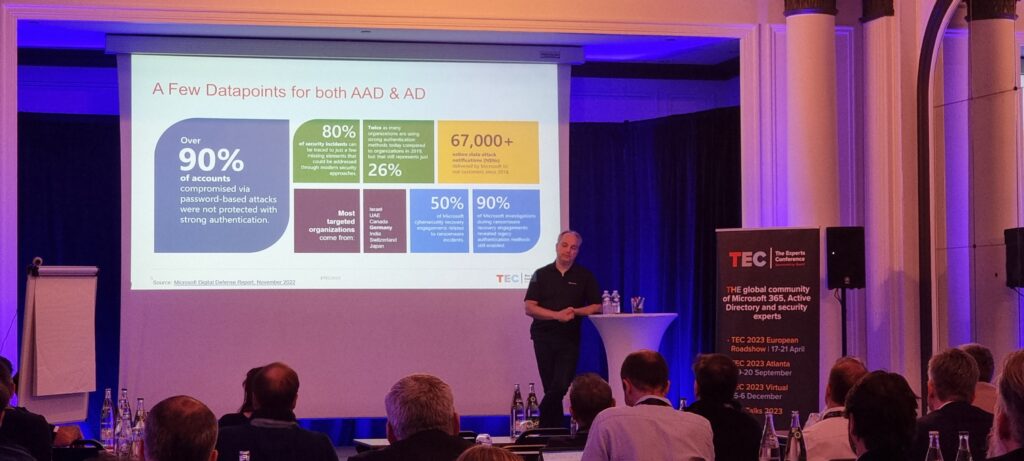
As you might expect, Practical 365 was out in force, with Tony Redmond and myself presenting a number of sessions. However, some of the most useful content came from MVP speakers from dedicated cybersecurity companies and experts at Microsoft providing some hard-to-find statistics.
There was so much useful content on each day that we would be doing the speakers a disservice by attempting to summarise everything, but there are several key points that you really need to know about and are summarised below.
Don’t let your Cloud Environment Become Compromised
André Lutermann of Microsoft gave real-world data about how long it takes from when an Active Directory (and it’s often AD) is initially compromised to when all your cloud environments are compromised too. On average, it takes just 15 minutes for your cloud to be compromised for customers without basic security measures. Microsoft expects, without mitigation, that the average will be just 5 minutes soon for those Orgs.
André also shared data on how long it takes to recover from an attack. The average recovery time is 2 weeks, and the businesses affected are often out of action for 6 weeks. It goes almost without saying that this is longer than the RTO (Recovery Time Objective) for most organizations.
Microsoft is also seeing an increase in state-based attacks – such as the recent Mercury attack Paul reported on a few weeks ago; these don’t just target big businesses or large government departments, they will take many other organizations in their wake too.
Several speakers pointed out that, large or small, you will be targeted by attackers if they come across a vulnerability. Tools are readily available in a criminal marketplace that makes it easy for anyone to conduct large-scale attacks across many organizations using automated deployment of tools. If someone malicious wanted access to your organization, it costs an average price of $2800 but can be as low as just… $5.

Beware of MFA Breaches
Techniques to by-pass Multi-Factor Authentication in Azure AD were demonstrated by Paula Januszkiewicz and Mike Jankowski-Lorek, and the method is straightforward. A fake login page is created that looks like a Microsoft 365/Azure AD sign-in page with a similar domain.
The login process on the fake site attempts a real login to Azure AD via a simulated web browser session and then proxies the multi-factor messages to the user, then when they respond to the challenge via a code, app, SMS, or similar, the process stops.
The user lands at an actual Azure AD login page and usually will think it’s a strange blip and log in again successfully. The attacker has everything they need to log in, though – the successful MFA challenge resulted in a URL being provided to the app underpinning the fake login page, and the attacker simply copies and pastes that into a web browser, fully logged into Microsoft 365.
Use of Microsoft 365 E5 tooling configured fully can prevent this – both to prevent the user from receiving a phishing message, to scan links as they attempt access, and to prevent the “impossible travel” aspect too, as can proper use of Conditional Access policies and Azure AD configuration.
Active Directory is the Target
Finally – the resounding message was: The primary target is your Active Directory. Protect it; manage it; monitor it; implement the basics for security to help prevent the worst from happening and assume a breach.

As you might expect, Tony Redmond’s session was jam-packed with practical advice you can take away and should plan to implement, such as removing SMS and phone calls for MFA challenge response, using new features in Azure AD such as number matching and key Conditional Access policy features you need to utilize. A similar TEC talk version of Tony Redmond’s session is available on demand.
TEC 2023 in Atlanta
The full conference – TEC 2023 Atlanta – will be back later in the year and should be on your list of conferences to consider. Speaking at TEC Europe and attending the many great sessions underpins why conferences like TEC – that leave the marketing fluff to one side and focus on real, practical advice from experts – provide so much value.




