The Expanded Scope for Microsoft 365 DLP
When it was first available, Microsoft 365 Data Loss Prevention (DLP) policies could only process Microsoft 365 data. Over the last few years, Microsoft expanded the scope for DLP to support these additional environments:
- Microsoft 365 workloads (OneDrive, Exchange, Teams, and SharePoint)
- Microsoft 365 Apps for Enterprise (not the LTSC version)
- Windows 10/11 and macOS endpoints (requires Onboarding of Defender for Endpoint)
- Third-party Cloud Apps (requires installing Chrome and Firefox extensions for these browsers)
- On-premises file share and SharePoint (requires the installation of the Purview Information Protector Scanner )
In this article, we focus on implementation details around applying DLP to endpoint devices.
The Microsoft 365 Kill Chain and Attack Path Management
An effective cybersecurity strategy requires a clear and comprehensive understanding of how attacks unfold. Read this whitepaper to get the expert insight you need to defend your organization!
Microsoft 365 Endpoint DLP
Like other DLP policies, Endpoint DLP monitors and blocks activities the engine identifies as potential evidence for data leakage. The basic configuration principles are the same. We need to define a policy in the Microsoft 365 Purview compliance portal. The policy includes three elements:
- Conditions – this usually involves using Sensitive Information Type (SIT) to tell DLP what kind of information the policy should look for. Microsoft 365 DLP includes hundreds of standard SITs like credit card numbers and passport numbers, and you can define custom types.
- Actions – defines what to do when a DLP policy violation occurs. Figure 1 shows the list of actions supported by endpoint DLP.
- Notification – Defines if the policy informs users (and how) if it detects a policy violation.
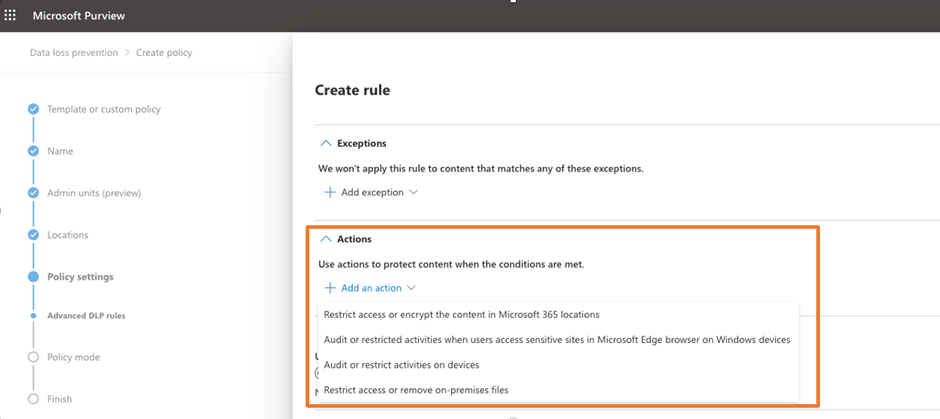
I always use separate policies per environment (like one for endpoint and one for SharePoint), even though you can define a DLP policy to support multiple data stores. This is because policy actions might change depending on the type of data source. It may be confusing if you attempt to process email and endpoint DLP in the same policy, as the actions may not apply to all data sources.
Let’s return to the endpoint DLP policy. You can refer to Microsoft’s documentation on what activities you can monitor and apply restrictions to. There are also differences between Windows and macOS in terms of supported activities.
For example, if you want to restrict users from copying files with sensitive information to USB drives when defining the policy, select Audit or Restrict activities on devices and select Block all supported activities. This is shown in Figure 2.
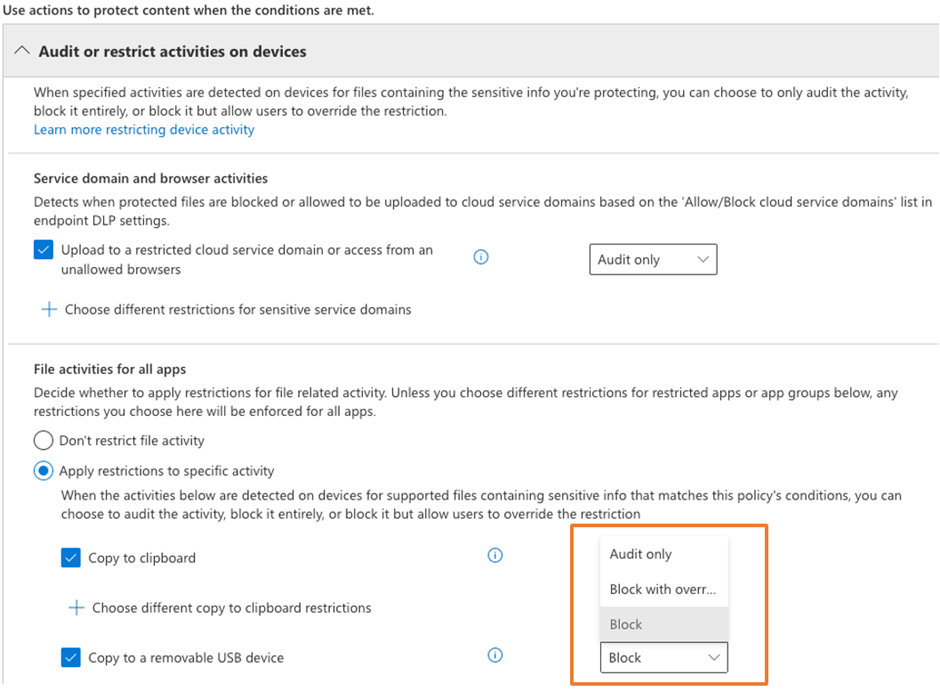
You might think that the policy is all set at this point. Well, that’s not always the case. In a recent project, my team had the same thought, but the reality was different. They configured the policy and waited for a few hours to ensure that Purview replicated the changes to all Microsoft 365 services and backend servers… but no alerts appeared. Usually, I go back to the basics: is the device onboarded to Defender for Endpoint, and is Endpoint DLP enabled? During client enrollment to Defender for Endpoint, it’s possible to miss out on some configuration steps that must be in place to enable Endpoint DLP (for example, the macOS configuration profile disables Endpoint DLP).
Advanced Detections
If you work with Microsoft DLP, you probably know some advanced detection capabilities in Microsoft 365 DLP — for example, Exact Data Match (EDM) or Named Entities. In particular, EDM is gaining traction with my clients as they seek detection that extends beyond patterns. For example, say your company’s account number is an 8-digit string; the pattern-based matching of the SIT will match all 8 digits in the content, which will result in many false positives. The EDM is able to narrow down to a specific 8-digit string since we need to provide a list of 8-digit strings to Microsoft 365. We do not need to worry if an 8-digit string will match content like 20230501, which usually means 01 May 2023. We do not intend to walk through the details about EDM here, but you can find out more about it by visiting this page.
However, there is one thing you need to remember if you plan to use EDM or Named Entities as part of your Endpoint DLP policies. Support for using EDM or Named Entities requires you to turn on Advanced Detection capabilities support for Endpoint DLP, which means that clients upload files to the Microsoft Cloud for analysis. If the client has no internet access and you limit the bandwidth use per endpoint, all detection occurs locally, and only basic SIT detections (e.g., credit card number detection) can occur.
User and Admin Awareness
I’m a huge fan of making sure users know what’s going on instead of blocking the actions users are doing without telling them why. There was a time when security teams liked to keep users in the dark and keep them wondering why they couldn’t do certain things. In some ways, I agree, but for things like DLP, I prefer to inform users. Therefore, I always enable User notifications for DLP rules (not just endpoint DLP). Different policy tips are supported on each platform (see Microsoft documentation).
The best place to view all DLP-generated alerts is the Microsoft 365 Compliance Portal. You can view audit records logging what happened and why the file triggered a DLP policy, no matter what location they are in (endpoint, SharePoint, OneDrive, etc.). This comes in handy as we no longer need to search in multiple places to find information.
A Few Points to be Aware of
When using Microsoft 365 Endpoint DLP, you must pay attention to these things:
- A change to a DLP policy may take up to an hour to update all Microsoft 365 services. So, configuring the policy may not take effect immediately.
- Endpoint DLP uses the MIME type to monitor key file types (Word, Excel, PowerPoint, and PDF), so even if a file extension changes, policies still work.
- Endpoint DLP requires Microsoft 365 E5 license or E5 Information Protection and Governance license.
Should you enable Endpoint DLP?
If you have no other solutions deployed, and you only need basic detection and restrictions and have the necessary licenses, you can leverage Endpoint DLP. Otherwise, it may be worth waiting for Microsoft to release more mature functionality. Compared to other Endpoint DLP solutions on the market, especially the most popular ones (like Symantec DLP). Microsoft Endpoint DLP is behind in terms of functionality and detection capabilities. Here are a few examples of where DLP Lacks:
- Document fingerprinting support.
- Ability to support other document types, like AutoCAD drawings.
- Ability to use advanced features, like EDM matching, for endpoint DLP without internet access.
If Microsoft is able to address all of these, they will be able to gain much better traction with customers in the endpoint DLP space.



