Defender for Cloud Apps — It’s More Than Just Another Security Tool.
Microsoft Defender for Cloud Apps (a.k.a. Microsoft Cloud Apps Security) is a very powerful tool. However, many administrators think it’s just yet another “Microsoft Security” product. After using Defender for Cloud Apps in a project with Microsoft 365 E5 licenses, I realized it’s a handy and powerful tool at a reasonable price even if purchased as a standalone product. Defender for Cloud Apps provides the ability to monitor and enforce restrictions on major Microsoft 365 apps (e.g. Exchange Online, SharePoint Online, OneDrive, Teams) as well as some third-party apps to allow browser access to the apps with some restrictions in place to prevent potential information leakage.
Key Functions of Defender for Cloud Apps
Defender for Cloud Apps includes three key functions:
- Discovery – analyze network access logs captured from different sources and generate reports about the usage of cloud applications.
- Monitoring – collect audit/activity logs via connectors and provide insight on who, when, and what happens in supported cloud apps. This capability requires a connector to connect logs to Defender for Cloud Apps.
- Enforcement –block or apply restrictions based on policies defined to prevent unauthorized access to corporate data. This feature requires session monitoring to be enabled and using Defender for Cloud Apps as a CASB (cloud access security broker) for the designated cloud apps.
Defender for Cloud Apps works well with Microsoft 365 products. Although some complications exist when using Defender for Cloud Apps with third-party apps. I’ll explain what I mean, especially for the Monitoring and Enforcement function.
Support for Third-Party SaaS Apps
To enable Defender for Cloud Apps to monitor SaaS apps, you need a connector. Microsoft has a wide array of available connectors. To start, select the app you want to use and provide the necessary credentials to connect to the app. In this article, I use Salesforce as an example (Figure 1).
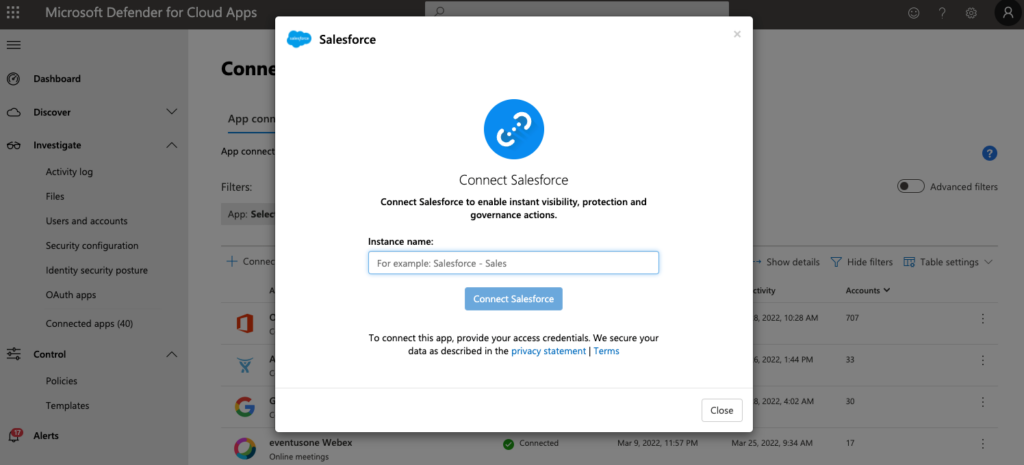
Each app has its own requirements. For Salesforce, you must:
- Specify the display name of the Salesforce instance to monitor with Defender for Cloud Apps. This will redirect you to a setup screen.
- Configure Salesforce including making sure you have the needed licenses. Instructions about what you need to do to connect Salesforce are available online.
After connecting to an app, Defender for Cloud Apps automatically collects some information, including:
- Users
- Groups
- Files
- Activities/Audit Log
Some apps, like Salesforce and Slack, have specific license requirements because the Connector requires access to some features that are only available in a specific pricing plan.
Once you’ve configured the app, Defender for Cloud Apps automatically begins gathering user activity information and you will see activities in the activity log. At this point, you can set policies to detect potential security risks, like a disgruntled employee trying to delete all your company data or an outside agent trying to steal your company files. The alert will allow you to act quickly to defend against such an attack.
Figure 2 shows a security policy to detect users who download over 50 unique files within a minute (this is based on a template provided by Microsoft). When Defender detects a violation, Azure AD forces the user to sign in again and Defender generates an alert to allow administrators to determine if any follow-up action is necessary.
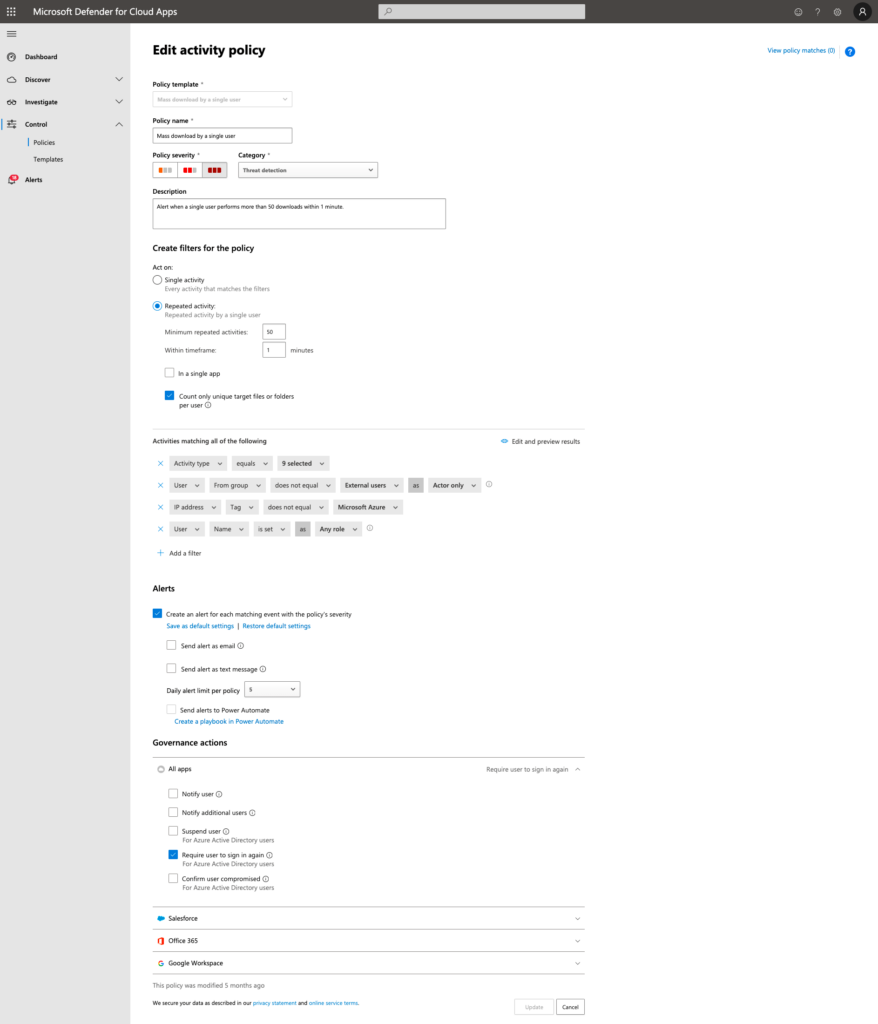
When Defender detects and flags activity as risky, several remediation steps are available. In the example above, the user must sign in again if the policy detects that they are downloading too many files. If the offense is serious enough or you think it’s necessary for any reason, you can configure the policy to suspend the user permanently.
Check out the Top 10 Security Events to Monitor in Azure Active Directory and Office 365 in this eBook.
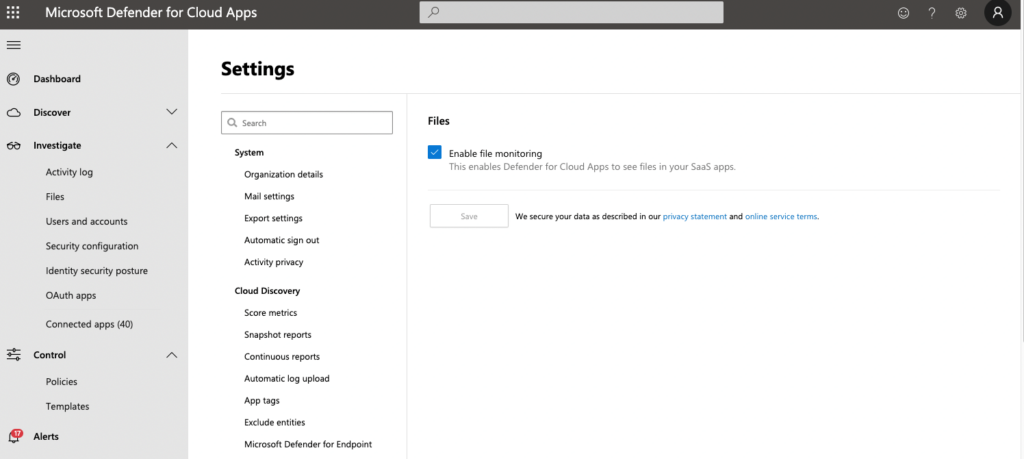
Enable File Monitoring
File Monitoring is not a default setting. I recommend enabling File Monitoring in Defender for Cloud Apps (Figure 3) because the data insight it provides is invaluable and it is included in the license cost.
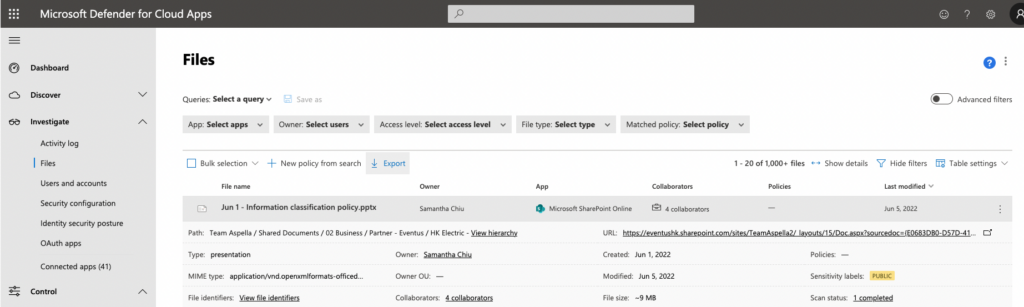
After File Monitoring is enabled, you can find a file, see who accessed it and when each user accessed it. This makes it easier for administrators to investigate and monitor SaaS apps. Figure 4 shows examples of data collected from Microsoft 365 and Salesforce after enabling File Monitoring. You can see the information gathered such as collaborators, owners, and sensitivity labels.
Session Monitoring and Enforcement
Another key aspect of Defender for Cloud Apps is the cloud app security browser (CASB). Technically, a CASB works with any SaaS app and does not require you to configure any connectors before you can use it. Essentially, a CASB is a big reverse proxy server sitting in front of your SaaS apps. It helps control and monitor all incoming and outgoing traffic between users and SaaS apps.
To enable CASB in SaaS apps you must configure single sign-on (SSO) of the SaaS app with Defender for Cloud Apps or Azure AD. I recommend you use Azure AD because it is easier as many of you might use Azure AD for SSO already. To set up SSO with Azure AD, you must configure a conditional access policy to trigger session monitoring. Azure AD then passes the session to Defender for Cloud Apps instead of the SaaS app after authenticating the user. Using conditional access requires Azure AD Premium P1. However, if you do not have that license and only purchase the MCAS license, you can choose to enable the session monitoring with MCAS.
When configuring the conditional access policy, it’s better to select Custom Policy (Figure 5) so that you don’t have to choose what to monitor here and allow Defender for Cloud Apps to manage when to monitor access. Instead of using Custom, you can use a predefined policy like Block Download or Monitor Only, but you will lose the ability to prevent some apps from using the CASB feature if you run into issues later. For example, the CASB feature breaks part of the SaaS apps for mobile users. Given this bug, you want to stop the CASB feature from applying to mobile devices for specific conditions until Microsoft comes back with a fix. This can only be done using the session policy in Defender for Cloud Apps but not in the conditional access policy.
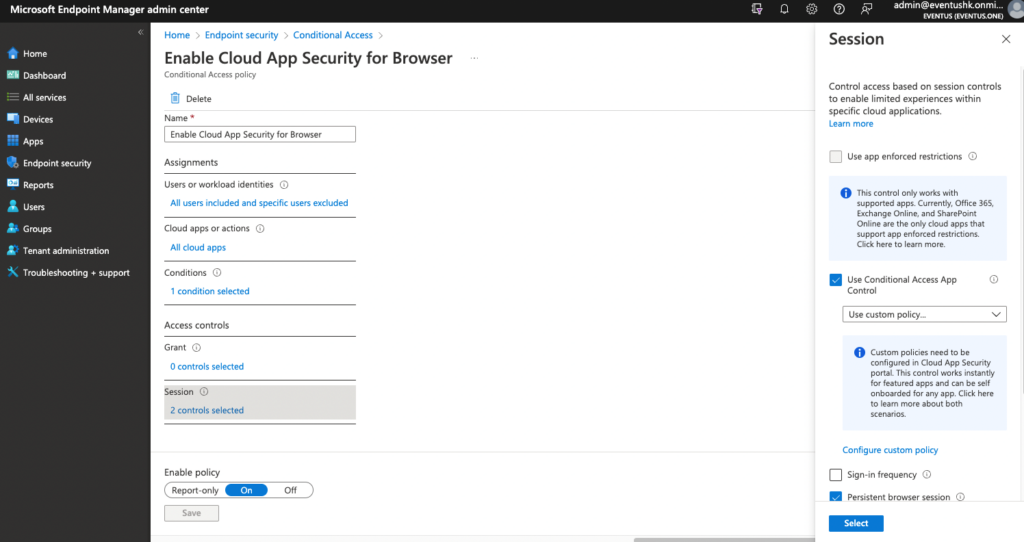
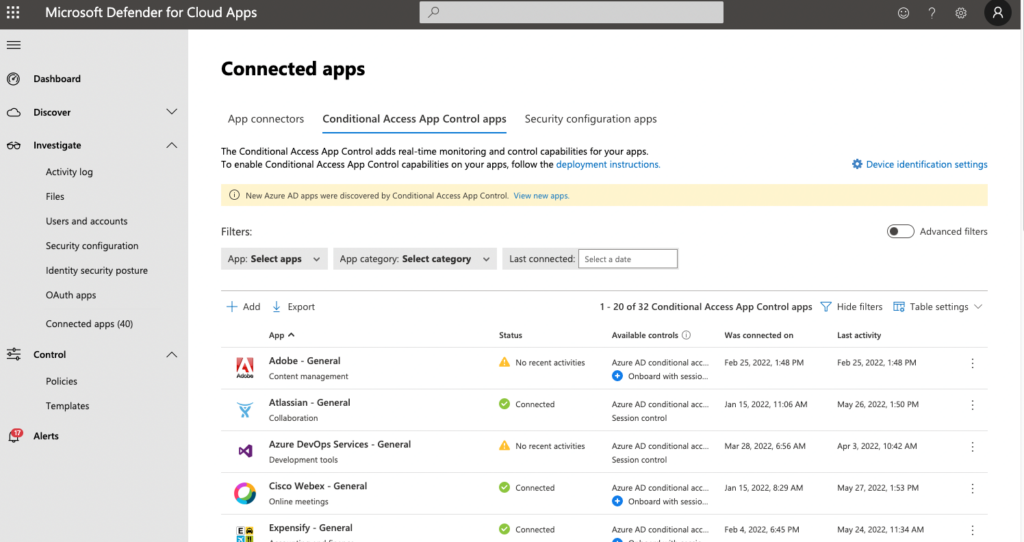
After enabling the conditional access policy, SaaS apps appear in Defender for Cloud Apps (Figure 6). Use the Available Controls column to control if you want to enable session control on per-app basis. If you do not use conditional access, you must add the app manually and configure SSO with Defender for Cloud Apps. This can be complicated, which is why I recommend you implement a conditional access policy.
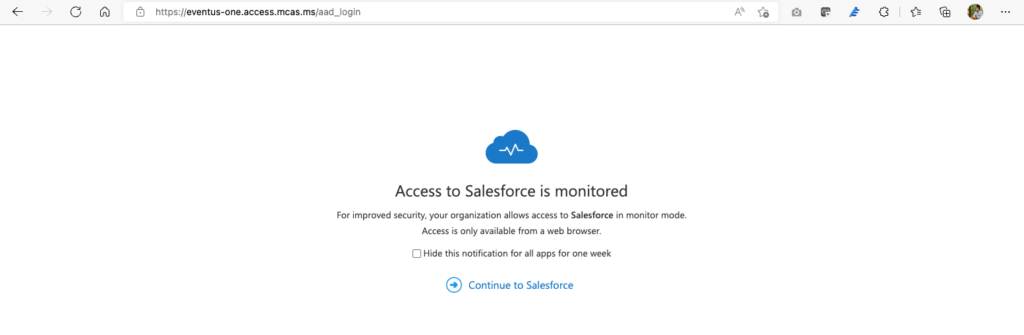
After you enable SSO at the SaaS app level and configured session control in Defender for Cloud Apps, users will start to see a modified connect screen when they sign in to SaaS apps (Figure 7). In this case, all client browser traffic for Salesforce is being monitored by Defender for Cloud Apps. How do you know that monitoring works? Easy! All the URLs change to *.mcas.ms because the traffic passes through Defender.
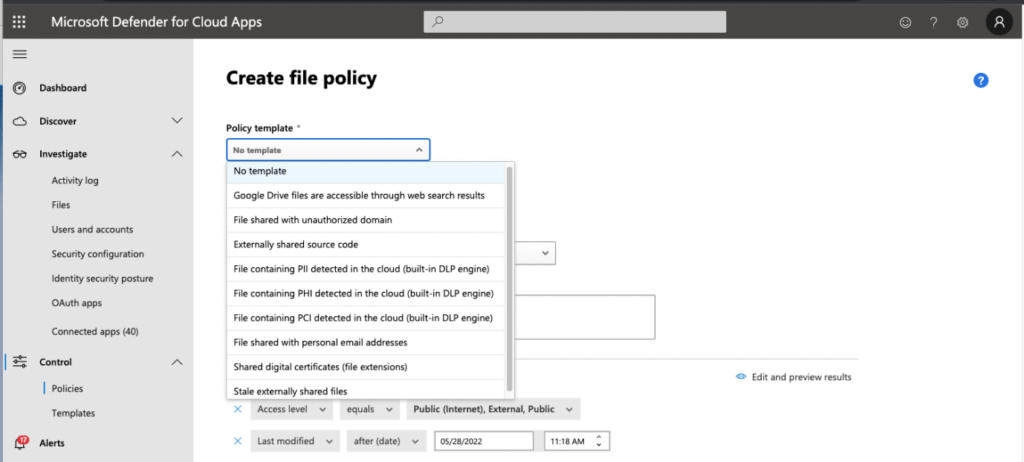
After confirming that Defender is monitoring the app, you can enable policies to monitor and enforce access controls. Defender for Cloud Apps includes several templates to help organizations to create policies. A good place to start is with threat and malware protections or information leakage. Figure 8 shows how to create a file policy to monitor file access conditions.
Issues
Everything seems so perfect and simple, right? Unfortunately, that’s not the case. If you just set up the Connector-based monitoring feature, you’re likely to have almost no issues because Microsoft tests all the connectors. However, I still come across some minor issues when trying to set up connectors. Often the issues are related to licensing of SaaS app —I cannot set up Slack because my workspace doesn’t have audit API; or connection —My Salesforce connector cannot gather some specific data via API calls).
The most challenging feature setup is session monitoring (i.e. CASB). Since it will monitor and write URLs and modify the HTML returned to users, I have come across situations where monitoring breaks. These include:
- Functions in salesforce web app
- Not able to sign in mobile app
These are just a few of the issues encountered when setting up Defender for Cloud Apps. The key point here is that you must do some thorough testing if you want to use session policy to enforce restrictions as it may not always work especially with third-party apps. Sometimes, you may need to open support cases with Microsoft to have them check and change some “backend settings” to fix problems.
Having said that, Defender for Cloud Apps is a powerful tool that helps you monitor and enforce security policies across the most popular SaaS apps at a very affordable cost.




is it possible to apply policy for Teams app for the external device ?