I recently met with Tony Redmond and Malte Schoch for a TEC talk to discuss Microsoft’s announcement that Exchange Online will start blocking messages from older, unsupported Exchange servers. Tony had previously shared some early analysis on this topic here on Practical 365.
This TEC talk provided a forum where participants could learn more about the upcoming changes and get answers to some of their specific concerns since Exchange environments can be quite complex and have unique configurations.
We were grateful to also have Scott Schnoll from Microsoft join us in the chat to help address many of the questions that we received throughout the session. Below are some highlights of the topics discussed.
What Exactly will Microsoft be Blocking?
Microsoft is implementing new security measures for messages sent from your on-premises Exchange servers to Exchange Online. The updated protection will require you to keep your Exchange servers updated and patched to ensure that messages can flow to Exchange Online through your inbound connector.
Since the change is specific to the traffic that passes through the inbound connector, the new requirements only apply to the Exchange servers passing that traffic, and you can operate with a mix of old and new versions in your environment:
- This change only applies to the Exchange servers that host on-premises connectors to Exchange Online
- Other Exchange Servers in a hybrid organization are unaffected (for now)
TEC Talk: What to Do About Exchange On-Premises After Microsoft Starts to Block Messages
Hear what Tony Redmond has to say about what might happen if your org is using older on-premises Exchange servers.
How will Enforcement Occur?
Microsoft is using a staged rollout to provide time for Exchange administrators to review and update their servers.
Enforcement begins with a 30-day reporting phase to identify any non-compliant servers sending messages over the inbound connector. After 30 days, message flow over the connector will become increasingly throttled and messages will start being blocked. If you do not update the server hosting the connector within 90 days of the initial report, all message flow will be blocked over that connector. Figure 1 shows a chart the Microsoft tech community created to show the different stages from initial Detection to 100% blocking.
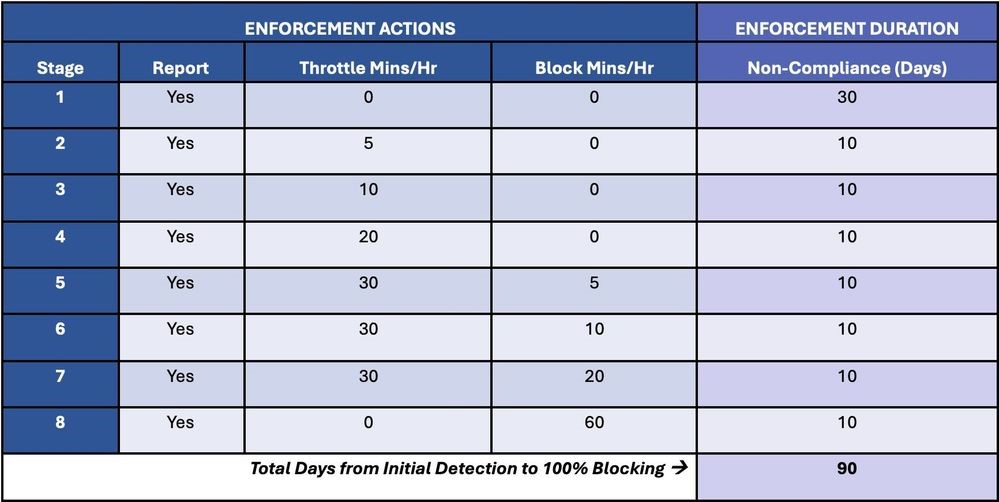
When Will Enforcement Begin? What if I Need More Time?
Initial enforcement started in June 2023 for Exchange 2007 and Microsoft will follow up with enforcement for Exchange 2010 and Exchange 2013 over the next few months. During this time, all Exchange servers that host on-premises connectors to Exchange Online should be updated to a supported version of Exchange 2016 or Exchange 2019. Figure 2 below shows a timeline for Exchange enforcement over the next 10 months.
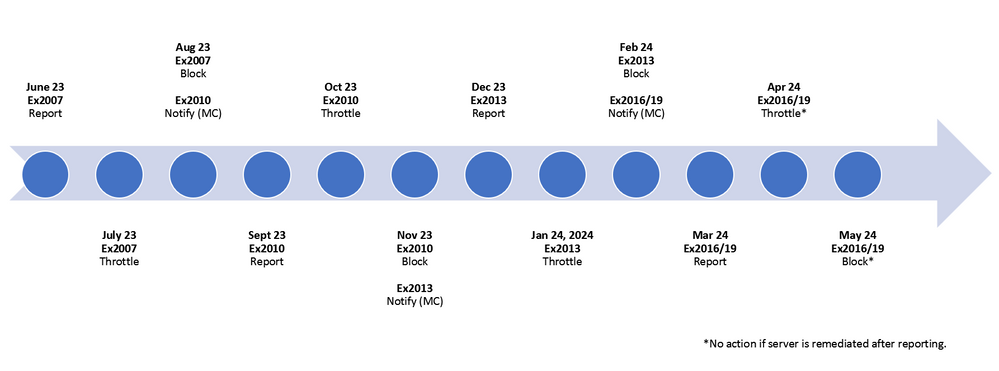
Once your servers are updated to a supported version, you will also need to keep them patched in a timely manner moving forward. Reports will continue to be available in the Exchange Admin Center to help identify whether you have old or unpatched Exchange servers sending messages through an inbound connector to Exchange Online.
Microsoft will allow you to request an extension if you need more time to test updates before deploying them to your production servers. You have an annual pool of 90 days for your tenant that you can use to pause message throttling and blocking.
Is Microsoft Planning to Stop Supporting Exchange On-premises?
No, Microsoft will continue to fully support both Exchange on-premises and Exchange Online. They understand that many companies still require Exchange hybrid configurations and this change will help reduce risk in those environments moving forward. Following are just a few examples that participants mentioned in the TEC talk for why they are keeping Exchange servers:
- Some prefer the mass mailing features from Exchange on-premises
- Some applications such as multi-function devices, websites, and reporting tools need to maintain their on-premises configuration
- Some administrators want better options for migrating resources to Exchange Online
The next version of Exchange Server is scheduled for release in H2 of 2025 according to the Exchange Roadmap. Scott from Microsoft mentioned that they will be very transparent about minimum compliant builds and will publish full details before they do anything about removing support for Exchange 2016 and 2019.
What Steps Should You Take Next?
Review your hybrid Exchange configuration and identify whether you will be impacted by this change. If you have older Exchange servers, decide whether to keep Exchange on-premises or whether you want to move to Exchange Online.
If you decide to update your Exchange servers:
- Identify the servers that host connections to Exchange Online
- Update these servers to Exchange 2016 or Exchange 2019
- Continue to monitor mail flow reports and keep servers patched
If you decide to move to Exchange Online:
- Understand that you can remove your Exchange servers while still keeping AD on-premises
- Migrate remaining mailboxes and public folders to Exchange Online
- Remove your final Exchange server from your hybrid environment, but do not uninstall
- Use PowerShell to manage Exchange recipients with the Exchange Management Tools
- Remember that you can migrate resources back to on-premises if you identify an operational impact that warrants a rollback process
Regardless of the path you choose, keep a close eye on the Exchange Team Blog & Practical 365 for the latest updates about this feature and other changes that impact Exchange.





We are running Exchange 2016 Build 15.01.2507.039 (ie CU23) in hybrid mode but the EAC Online reports that our Exchange server is running 15.1.2507.6 so has started throttling. We have paused the throttling but time is running out as you can only do this for 90 days. Does anyone have any idea how to get Exchange Online to report the correct version?
Thanks
This is where you absolutely need to report the problem to Microsoft support. If you don’t, then engineering will never hear about the issue.
Hi Callum, this change will not affect customers sending directly to recipients hosted by M365, since those messages do not enter M365 via the On-Premises Inbound Connector. Instead, those messages are routed to EXO via normal mail flow based on MX records and can be scanned by the recipient’s standard mail protection methods.
Microsoft is adding this change for Hybrid environments because messages routed from on-prem to EXO in a Hybrid configuration pass directly through the Inbound Connector and skip all the normal hygiene processes, so they are at greater risk when coming from unsecured systems.
Is this only affecting Hybrid configurations or are customers without any sort of hybrid setup that are sending directly to recipients hosted by M365 also affected.