Three licenses are available for Microsoft Defender for Business: Defender for Endpoint Plan 1, Defender for Endpoint Plan 2, and Defender for Business. A Plan 1 license is limited and contains only Antivirus capabilities. Defender for Endpoint Plan 2 is the oldest and default plan, and it covers features such as Antivirus, Endpoint Detection & Response (EDR), Attack Surface Reduction, Advanced Hunting, and Automated Investigation and Response. Defender for Business is a license tailored to small and medium-sized businesses whose feature set sits between Plan 1 and Plan 2. In this article, I discuss the capabilities of Defender for Business.
Comparing Features
A complete comparison between the different license plans is available on Microsoft Learn. Here, I compare Defender for Endpoint Plan 2 against Defender for Business. I ignore Plan 1 because it is a basic plan that misses critical features such as Endpoint Detection & Response. Organizations looking for an Endpoint Protection system should select one with EDR capabilities. EDR provides more in-depth monitoring capabilities compared to a traditional antivirus, as it is not based on signatures but will scan all activity in a cloud database, providing more in-depth detections.
A couple of significant differences exist between Defender for Endpoint Plan 2 and Defender for Business. The two most important ones are listed below, which are covered in depth later in the article.
- Configuration of the Endpoint agent on workstations is simplified in Defender for Business.
- The Business license includes no threat-hunting capabilities.
Besides these differences, a couple of minor differences from Defender for Business that are good to know include:
- The lack of device groups.
- No way to see the currently logged-on user of a device.
- Lack of custom detection rules
The Microsoft 365 Kill Chain and Attack Path Management
An effective cybersecurity strategy requires a clear and comprehensive understanding of how attacks unfold. Read this whitepaper to get the expert insight you need to defend your organization!
Threat Hunting
Threat hunting is the most crucial feature not covered by the Business license. But what exactly does this mean, and is the lack of threat hunting a dealbreaker?
When Microsoft states that Defender for Business has no threat hunting capabilities, they mean that there is no way to get a hold of the raw data which Defender for Endpoint collects. The raw data consists of the device timeline, a visual representation of all events collected on an endpoint, and advanced hunting, which allows you to retrieve this data through KQL.
The main reason why people use Microsoft Defender is for incident investigation. If there is an incident, you investigate it thoroughly and check if there are any follow-up actions to take:
- Should I reset the user’s password?
- Do I need to reinstall the device?
- Is there any user education required to avoid such an incident in the future?
Defender for Business is limited to the information Microsoft provides. Each incident has an alert story describing the actions Defender identifies as suspicious, as shown in Figure 1.
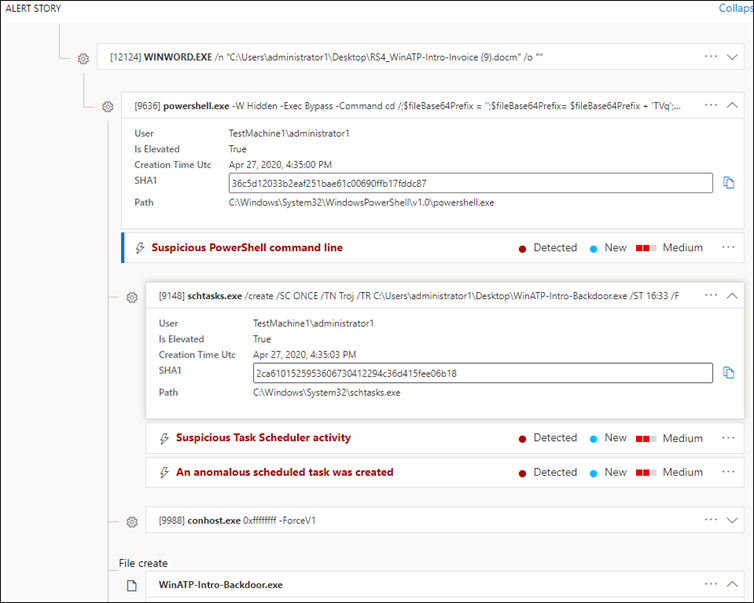
While information retrieved from the alert story might be adequate for some investigations, in my experience, the information presented by Defender for Business often lacks details. Sometimes, you need to know which URL the user visited before the attack was launched or which files were modified by a specific process. I typically get this information from the device timeline, but this is unavailable when using Defender for Business.
This is not a disaster, but it means you cannot double-check any incident Microsoft creates. You must trust Microsoft’s detection mechanisms.
The same goes for the lack of advanced hunting. Advanced hunting allows you to create KQL queries to generate an incident if a query has a result. Because advanced hunting is unavailable, you lack the ability to create incidents based on conditions or logic.
As Defender for Business is geared toward small and medium-sized businesses, the above might not be a dealbreaker for organizations without a dedicated security or IT engineer. Diving into logs to get more information is not something every IT engineer will do because they lack the knowledge or time for such investigations.
Client Configuration
Defender for Business simplifies the deployment and configuration of your endpoints. In comparison, a typical Defender for Endpoint onboarding is done through the Microsoft Intune portal by deploying the necessary onboarding and configuration policies. Defender for Business supports the onboarding of Intune-enrolled Windows devices through the setup wizard. This means there is no additional configuration using the Intune portal, as Microsoft sets everything in the background. Besides onboarding, Defender for Business also deploys a Microsoft-recommended configuration of the antivirus (including scan configuration) and the endpoint firewall. This is great for small IT teams without in-depth knowledge of the Microsoft security stack.
Minor Differences
Not all license differences are covered on Microsoft’s website, meaning it’s unclear what features you miss. I have run into some features that aren’t in Defender for Business that are useful.:
- Most logged in user
- If you navigate to a device’s page, Defender for Endpoint displays a ‘Last Logged-On User’ property showing which user most commonly logs into the device. This is a handy way to identify which end-user is using a device. This type of information is not available for Defender for Business tenants.
- Device Groups
- Device Groups are used to create a logical grouping of different sets of computers. Some examples are servers vs. endpoints, mobile vs. desktop, or active vs. inactive devices.
A Strong Core Set of Features
While there are quite a few differences between Enterprise and Business licenses, the core features remain the same. With a Defender for Business license, we get the following:
- A fully-fledged, modern Antivirus system configured according to Microsoft best practices.
- An EDR system using behavior monitoring scans your endpoints and blocks threats if required.
- Insights into vulnerabilities using the built-in Vulnerability Management license.
Your organization’s appetite for security
Microsoft Defender for Business is a great way for small businesses to use enterprise-grade protection and detection without needing an IT engineer with a good knowledge of endpoint security. It simplifies incident investigation and device onboarding by abstracting more complex workflows from the organization. This makes Defender for Business an excellent fit for small organizations, as it is easy to deploy and maintain.
Nevertheless, Defender for Business is not great for medium-sized organizations that need an in-depth, advanced security solution. Some organizations are below 200 employees and thus eligible for Business licenses but need a higher level of sophistication in their security solution. This type of organization might look for an outsourced SOC or a dedicated security engineer who needs tools such as advanced hunting and the device timeline. For those types of organizations, I recommend a Defender for Endpoint Plan 2 d.
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.





Amazing article, thank you SO much.
Hi Thijs
Great article, thank you. Not being able to identify users is a problem with Defender for Business. Ate yiu aware of any method of pulling device owners besides manual tagging?
Hi Michael
I haven’t and I fear there is none. With MDFB, you don’t have access to the same raw data. You can use the primary user in Intune, but that’s static unfortunately.