Four-Year Campaign to Eradicate Basic Authentication
From mid-2019 to July 2023, Microsoft ran a campaign to retire basic authentication for seven email protocols. Greg Taylor, who directed the four-year long effort, came to The Experts Conference (TEC) in Atlanta to share information about the tactics used and learnings from the campaign that reduced daily count for basic authentication connections for email protocols from some 70 million to close to zero. Greg’s chart showing the drop-off in basic authentication connections illustrates the effectiveness of the project after Microsoft started to disable the protocols for all tenants in late 2022 (Figure 1).
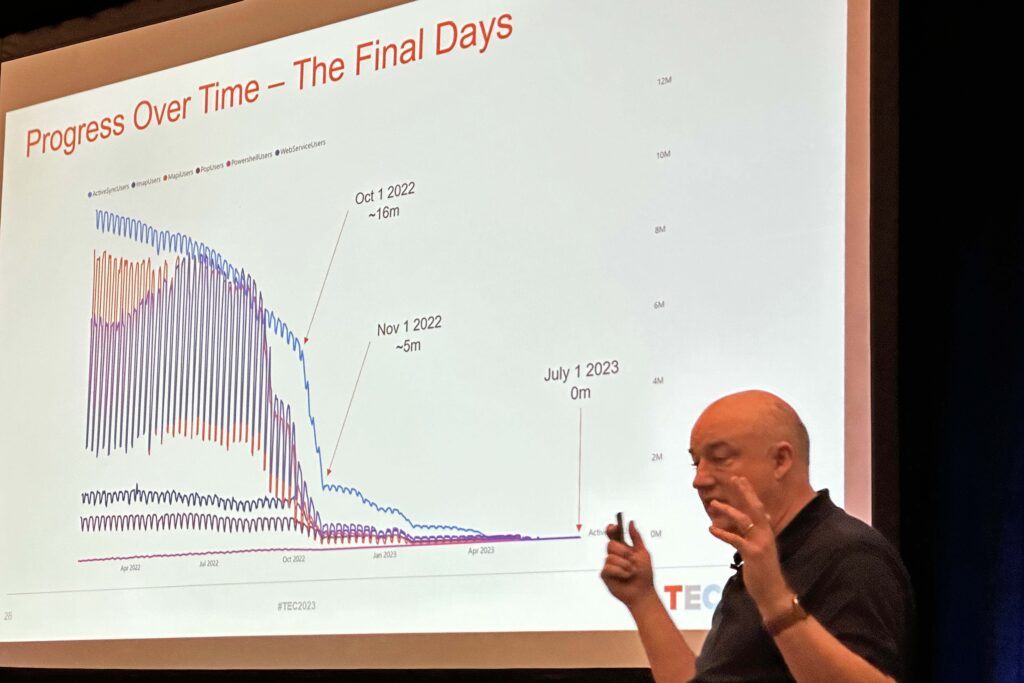
The reasons why Exchange Online needed to eliminate basic authentication are well known, Basic authentication is the chosen route for attackers seeking to compromise user accounts. Greg said that 99% of password spray attacks against Microsoft 365 use basic authentication and that more than 1,000 such attacks occur every second. Attackers still try to connect to Entra ID accounts using protocols like IMAP4 and POP3. The block on basic authentication cause these attempts to fail immediately, but they keep on coming.
Microsoft’s Tactics
The tactics used by Microsoft to nudge tenants to move from basic authentication included:
- Disabling basic authentication for email protocols in tenants that use Entra ID Secure Defaults.
- Disabling unused protocols automatically to reduce the potential for compromise. For instance, if Microsoft telemetry showed that a tenant didn’t use Exchange Web Services (EWS), the project team submitted a job to disable EWS without tenant intervention.
- Turning off protocols for 48 hours (for small tenants) to see what happened. If problems occurred (like an app using IMAP to poll a mailbox no longer worked), the administrator could switch the protocol back on.
- Forcing Outlook (desktop) clients to switch from basic to modern authentication by updating tenant configurations when telemetry showed that the Outlook clients used in the tenant supported modern authentication. All tenants created since August 2017 enforced modern authentication beforehand, so this step was only needed for older tenants. Again, the configuration update happened without local administrator intervention.
- Working with partners like Apple and Google to make sure that their email clients switched away from basic authentication. Apple changed their operating systems to force mail clients to upgrade their configurations. Google added a button to the Gmail client to allow users to upgrade the client when they weren’t able to connect after their tenant blocked basic authentication. Both are great examples of major vendors working together to serve common customers.
These steps delivered gradual reductions in the amount of connections using basic authentication. Eventually, the time comes for a complete closedown, a process that started in October 2022. Tenants were able to request an extension for protocols support, and Greg noted that just 0.05% of tenants made a request through the diagnostics feature in the Microsoft 365 admin center. Extensions allowed time to upgrade apps and user clients based on newer authentication methods for client protocols.
Greg acknowledged that some customers were disrupted during the transition and related a story about an ambulance service that transmitted instructions to pick up patients via email. When Microsoft disabled the IMAP4 protocol, the ambulances failed to receive any email until the administrators worked out what was happening and restored the protocol.
Communications via Message Center and Service Health Dashboard
Communications was a critical part of the project with Microsoft posting messages to the Microsoft 365 Message Center and Service Health Dashboard (SHD) to inform tenants when changes occurred. Greg noted that only 50% of large tenants read message center posts with that percentage declining significantly as tenants get smaller. This might be because important messages are hidden in a flood of other updates, but it does point to an issue that tenants should address. Much valuable information is shared in message center posts, and it’s a real pity when a tenant is surprised by a change Microsoft told them about two weeks before an event happens.
Interestingly, information posted to the SHD is 800% more likely to be read by a tenant administrator. This might be because administrators check the SHD more regularly to see if any known problems exist with Microsoft 365 services. The takeaway is that Microsoft needs to do better at communicating about change to its customers but also that tenants need to consume the information provided to them.
More Change Coming
The campaign to remove basic authentication took a long time but ultimately delivered success. Exchange Online is now better at resisting attacks, at least over obsolete connection protocols, and that’s a good thing. Next up, Microsoft plans to decommission the Outlook V2.0 REST API on March 31, 2024, with Exchange Web Services (EWS) due for removal on October 1, 2026. The Microsoft Graph APIs replace both and Microsoft has work to do to close some acknowledged gaps beforehand. No doubt the experience gained when removing basic authentication will make these projects easier for all concerned. At least, that’s the plan.




I ran it right up until the last day microsoft would let us! CCUM 10.something integration had no valid upgrade path to deliver voicemail 😁