A few weeks ago, after my podcast with Brian Reid about Exchange Online Protection, I finally got around to signing up my Office 365 tenant for Advanced Threat Protection.
If you’re new to EOP and ATP, I recommend having a listen to the podcast to learn more. But in brief, ATP delivers a series of enhanced email security features for Exchange Online Protection to prevent malicious attachments and links from causing customers to be infected with malware.
The three main capabilities of Advanced Threat Protection are:
- Safe Links – URLs in email messages are rewritten so that users are redirected through a Microsoft service that checks the link for malicious content when the user clicks it.
- Safe Attachments – email attachments are tested in a sandbox environment to detect malicious behaviour and attempt to block zero day attacks.
- Anti-Impersonation (anti-phishing) – detects phishing attacks that use lookalike domains and email addresses.
In this article I’ll share my experience with those features so far.
Enabling Advanced Threat Protection
Enabling ATP was simple enough, as I’m already an Office 365 customer. I purchased the additional ATP license and assigned it to my user account.
As a single-user tenant I wasn’t quite sure how many licenses I would need. I do have a handful of shared mailboxes that I use for various purposes, so I asked Microsoft whether I needed to license each of those as well. The answer I received was to license anyone who would normally utilize an Office 365 license. Since shared mailboxes do not consume a license, I don’t need to buy them ATP licenses. However, don’t take licensing advice from me. Ask your licensing provider who you need to license for ATP in your tenant.
After activating the license a new Advanced Threats option appeared in my Exchange admin center after a few minutes.
Safe Attachments
The first feature I looked at was Safe Attachments. There were no default policies created in ATP for my tenant. I am told that sometime in the past default policies were created, and maybe that will change again in the future. If you don’t see any default policies in your tenant, just go ahead and create one or more to suit your needs.
Safe Attachments policies can be targeted at specific recipients, domains, or group members. I chose to apply one policy to all of my domains.
A Safe Attachment policy can be set to Off (not sure why you would do that), Monitor, Block, Replace, or Dynamic Delivery. At first I used Block. But there were a few false positives early on, so I changed it to Dynamic Delivery, which will deliver the message without the attachment, and then a few minutes later when the attachment analysis is complete, the delivered email is updated with the attachment. In my experience so far no spammy emails with stripped attachments have made it to my inbox. I guess if the email itself is spam, one of the other filters in EOP will block it.
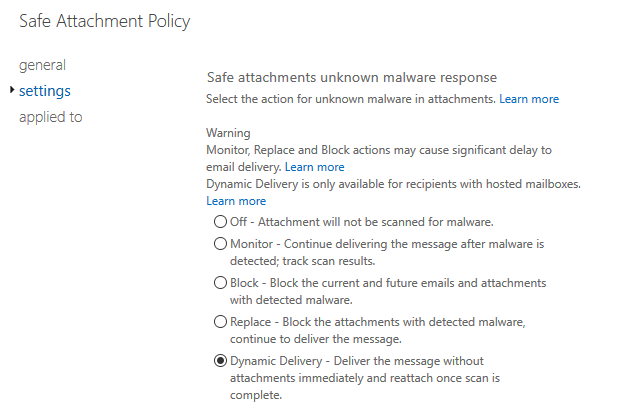
I also elected to redirect blocked messages to a quarantine mailbox. Mostly I was curious to see what it blocked. I’ve been happy to see ATP block multiple ransomware emails over the last several weeks. Also, I decided to enforce the Replace action if ATP malware scanning ever fails or times out. So far it seems to have had no trouble.
Speaking of timing out, if you’re wondering whether the testing of email attachments in a sandbox environment slows down email, the answer is yes.
![]()
Emails with attachments see a delay of several minutes. I don’t notice this, because I’m rarely expecting a specific email attachment to arrive. Things just appear when they appear, and everything is fine.
The only “problem” I’ve had with ATP was an obvious false negative that occurred within the first week or so. A fake FedEx email arrived in my inbox. The attachment was a 0KB Word document. My desktop AV didn’t consider it malware at first (a few days later it did), but I wasn’t willing to try and open it to see for myself. I logged a support case with Microsoft, and after a few weeks of investigation (yes, weeks, I needed to run multiple message traces, and there was the usual delays you get when you’re involved in a support case across multiple time zones) Microsoft determined that the reason was that the 0KB attachment was not seen by ATP as something it should scan. I haven’t seen a repeat of this type of email though, so my guess is Microsoft has successfully closed that gap.
All in all, Safe Attachments is working fine for me and I’ve had no more issues of false positives/negatives since the first week or so.
Safe Links
Safe Links replaces URLs in email messages with URLs that redirect the user through a Microsoft service that checks the URL for malicious behaviour or content at the time the person clicks on it. The user’s browsing traffic isn’t proxied through the Microsoft server, it’s just a security check and then the user is sent to the real URL.
Safe Links policies can be set to Off (again, why? I guess so you can temporarily turn it off?), or On. There’s some tracking of user clicks (this is available in the URL trace tool under mail flow in the Exchange admin center), and an option for whether to allow users to click through a blocked URL (in effect, they would be overriding the block if Microsoft had detected a malicious URL).
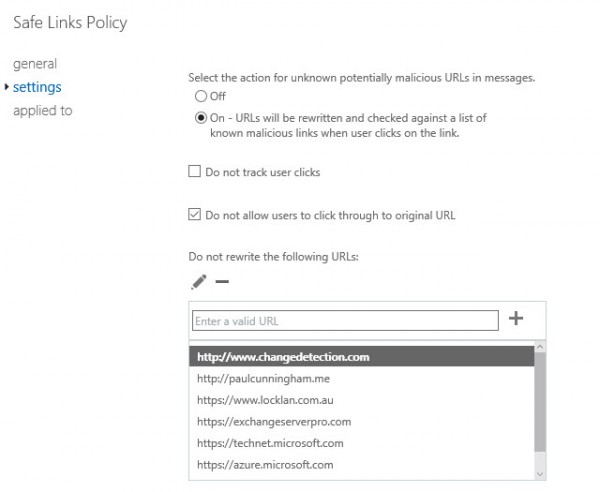
I added some URLs that should never be rewritten by Safe Links. These are URLs that I get in emails at lot (such as for blog comments) and the long Safe Links were quite messy and confusing to look at sometimes, so I started adding exceptions. As it turns out, there’s a cap length of the property that stores the exceptions. I got to about 10 entries before I hit that cap.
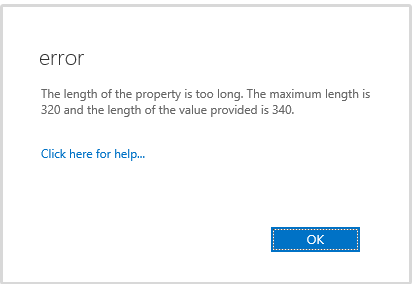
I thought that perhaps adding multiple Safe Links policies would be a way around this cap. For example, could you have one general policy applied to the entire domain, and then separate individual policies for exceptions that specific people need. Unfortunately, chaining multiple policies like that doesn’t seem to work. Instead, the highest priority rule matching the recipient is applied.
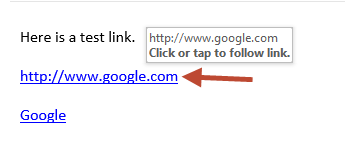
I also found that it is not necessary to set exclusions for some domains. Microsoft seems to have a list of trusted domains that Safe Links does not rewrite the URLs for. For example, a Google URL is not rewritten as you can see here. Similar behaviour occurs for many Microsoft domains as well.
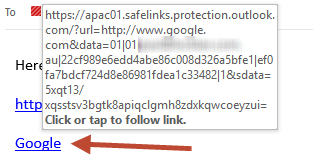
However, if the URL is hidden behind some anchor text, it still gets rewritten.
Safe Links has been working fine for me. There’s the briefest of delays after clicking a link while I wait for Microsoft to redirect me to the real URL. I have occasionally sent someone a Safe Link instead of the real URL, but since the links still work fine for anyone who clicks on them (they’re not restricted to just your users) that is more of a cosmetic issue than a functional issue.
Anti-Impersonation
The anti-impersonation features of Office 365 ATP are a recent addition to the service to help prevent phishing, spear-phishing and whaling attacks. Using anti-phishing policies in ATP you can protect your users from receiving phishing emails that attempt to impersonate legitimate senders by using lookalike domain names and email addresses.
I’ve written a detailed look at Office 365 ATP anti-phishing here.
Summary
My experience so far with Exchange Online Protection and Advanced Threat Protection has been good. Granted, I am a very small customer. But I do support other customers of varying sizes that also rely on EOP and ATP for email protection, and it works well for those companies as well. As far as Advanced Threat Protection goes, I think it is worth the additional investment to add it to your Office 365 tenant and get some more powerful protection from malware, phishing, and other attacks.





Hello Paul,
i am sharing here my issue, talking about ATP, in extended message trace, due to a message placed in spam, i am trying to get info about an agent, if it is, stamped as TACT=1|DI=SX|TACTCAT=SPM, after that my scl, it is rised to 5.
The message is empty except for an applied signature. My researches didn’t give me any clue.
I will appreciate any hint more than the guessed.
Good one you all.
Mcafee is the best secuirty for online protection. http://www.mcafeecustomerservice.co.uk/
Hi Paul
could u pls tell how did you measure the delivery time ? im referring to this https://www.practical365.com/wp-content/uploads/2016/04/safe-attachment-01-600×47.png
good post . pretty informative! thanks for the efforts
The Real Person!
The Real Person!
You can copy/paste the headers into a header analyzer.
https://www.practical365.com/exchange-server/how-to-read-email-message-headers/
Or use the Message Header Analyzer add-in for Outlook.
Advanced threat protection FAQ
https://technet.microsoft.com/en-us/library/mt789012(v=exchg.150).aspx
Do I need to assign licenses and configure policies in order for Advanced Threat Protection to work?
Advanced Threat Protection doesn’t require that licenses be assigned. However, enabling Advanced Threat Protection does require the configuration of policies in order to activate and target specific users, groups, or domains to be protected by the service. You can configure separate policies for Advanced Threat Protection to check links, attachments, or both. Safe links and Safe attachments policies can each be applied to specific sets of users. Learn how to do this at Set up a safe attachments policy in ATP and Set up a safe links policy in ATP. You can also create individualized policies within the Safe links and Safe attachments settings so that subgroups of users can have custom protection settings.
What are the license requirements for shared mailboxes?
Shared mailboxes need to be licensed for Advanced Threat Protection. See the following example:
A company has five users in Office 365. Each user has a mailbox, and there is one shared mailbox. This company will need a license for:
6 seats of Exchange Online Protection (5 users + 1 shared mailbox)
6 seats of Advanced Threat Protection (5 users + 1 shared mailbox)
Hello, Safe Links for internal emails seems the policy does not apply. If sending an email to internal colleague with URL link this not being scanned. I have the policy settings applied to the domain.
The Real Person!
The Real Person!
Yes, that is the expected behavior. Safe Links policies apply to email sent by external senders, not internal senders.
We are currently using ATP in our environment. We are replacing malicious attachments, but still sending the email through. When the attachment is replaced, it leaves a default O365 text file attachment. Is there a way we can modify the text of that file to represent our standard verbiage.
The Real Person!
The Real Person!
None that I’m aware of. You can raise a support ticket to find out for sure, or a uservoice (https://office365.uservoice.com/) about it and if enough people want it they might consider adding it.
Paul
Any idea when ATP Dynamic Delivery general release date?
We are having some issues with Dynamic Delivery (Public Preview) not redelivering clean attachment once released, approx 1 in100 email.
Regards
Matthew
The Real Person!
The Real Person!
Dynamic Delivery is GA right now, according to the road map. If you’re having technical issues then you should raise a support request so that it gets looked at. No point staying silent on the issue.
Does it known from witch partners are the anti-malware engines used by EOP? Or at least how many engines do they use?
Thank you.
The Real Person!
The Real Person!
I can’t provide licensing advice. You should ask your license distributor.
@Paul, you would set the service up to redirect threat catches to another mailbox. You would manually release from there is it was a false positive.
Brian
Hi Paul,
I have a question if you can help.
How can i release an email from ATP lock-down in a false positive scenario?
Regards,
My question for you is, How did you handle communication with the End User when you turned on Safe Links and Safe Attachments? We are about to enable for our Enterprise environment and are struggling to find end user friendly training or knowledge white pages to explain how the changes could impact them.
The Real Person!
The Real Person!
No secret sauce. You can turn it on for yourself first, see what is different, work out what you need to educate your users on, turn it on for a pilot group, get feedback, iterate, etc…
Hi Paul,
Big fan of your blog. I will like to know how this solution can be integrating with exchange 2013 and other third party messaging solution.
Thanks
The Real Person!
The Real Person!
You can use Exchange Online Protection and ASP with on-premises Exchange, although some functionality won’t be there. It’s something we discussed in this podcast episode:
https://www.practical365.com/podcast-episode-13/
Hello!
Does ATP scan internal emails (between 2 mailboxes on the same domain and server)?
Thanks!
apparently it doesn’t scan between mailboxes because we have seen exploits come into non ATP protected users and then successfully forwarded to ATP protected users. This was a while ago so this may have changed.
Thank you for the article Paul. My organization is a user of ATP and heavily focused on security. One of the directions we provide to our end users is to hover over a link received via email and confirm the links match to prevent phishing. With the cryptic (to the average user) rewrite of the URL, I’m finding it difficult to educate the end users on how to detect a phishing attempt. It seems unreasonable to expect the average non-technical user to visually decipher the link to determine its legitimacy before clicking. I’m interested in your comments and experience in this area.
Thanks,
Tom
The Real Person!
The Real Person!
I see your point. If the URL is one of the key things they’re looking for, then ATP Safe Links is going to get in the way of that.
Perhaps Safety Tips will help you with that, when it’s rolled out.
Theoretically, Safe Links should be protecting users from those phish attempts.
Hi Paul,
I’m fan of your site! – just enough explanations, screen shots and pertinent info to Keep an Exchange Pro informed and moving forward.
That said, our MS Exchange environment uses Mimecast for SMTP security gateway services such as TTP and Safe Attachments (perhaps the Marketing term differ).
Mimecast touts a partnership with Microsoft in the SMTP security space.
In your honest opinion, MVP status aside, what’s the real deal? Why would they partner?
MM
The Real Person!
The Real Person!
Vendors partner with other vendors all the time, for all kinds of reasons. Just because they might compete in one particular space, doesn’t mean they don’t also have complimentary products or services elsewhere.
@Seth, remember that you cannot avoid EOP for an Office 365 mailbox. So if you use Proofpoint (or any other cloud filtering vendor) then you will also be using EOP. You then loose some of the functionality of EOP such as:
* All inbound email comes from your other vendor and not the actual source address – so IP based filtering is pointless (and remember EOP is part of Office 365 which is part of Microsoft who also filter Outlook.com, and are the biggest cloud filtering company in the world, so have a lot of good info on bad IP’s to filter against.
* User driven safe lists in Outlook are not processed by the other vendor
* EOP quarantine if you want it is pointless, as the other vendor should get rid of the spam first.
That said, ATP is still a great addition – catch zero day stuff missed by the other vendor, though in this case Proofpoint have a similar option.
Brian Reid
Exchange MVP
We are a McAfee SaaS customer, but they are getting out of the email filtering business so we will be switching soon. We’re considering several options, EOP+ATP being one of them. There’s no doubt that Microsoft is upping their game with email gateway security through ATP, etc. However, I had an interesting conversation with ProofPoint this week who said that they on-board a large amount of customers who are using Office 365 who move to ProofPoint because they aren’t satisfied with EOP. Some of these are very large companies. EOP comes with the Office 365 license, but ATP does not. Is it worth the extra money, or could it be better spent? I’m curious if anyone else has any input on this topic or who uses ProofPoint and Office 365/Exchange on-prem. Obviously, with the number of threats hitting organizations each day through email, it’s a huge issue for most. My company has about 7,000 mailboxes. This year has been on of the worst for zero-day and I expect it to get worse. Anyone else in my shoes? Your input is welcome.
Seth,
O365 E4, some E5 licensed, customer with 6K+ mailboxes.
Before ATP – Microsoft EOP was HORRIBLE at filtering spam, spoofing, malware, etc. We probably had several dozen cases open with Microsoft last year alone where messages that were VERY obviously malicious were making it through their filters. That said, EOP in and of itself has come a LONG way with improved efficacy in the last 12 months or so, and continues to improve.
Proofpoint has long been courting us and wanting to do a POC to prove just how much more effective they are than Microsoft. We’ll sure, they’re a company that focuses solely on email security – I’d would expect they would be better. But they come at a fairly hefty cost.
Introduce ATP and you get much of the same highly touted “differentiator” type features that Proofpoint pushes at a much more reasonable price point. Couple ATP with your SPF, DMARC, and DKIM protections and you have solid layers of email defense.
If you don’t follow Microsoft’s own Terry Zink (https://blogs.msdn.microsoft.com/tzink/) you’re doing yourself a disservice when it comes to O365 mail security.
This is perhaps one of the most idiotic responses I have ever heard. So you saying EOP/ATP is “good enough” even though Proofpoint focuses on email security. This is exactly why the campaigns just keep on coming out because people rely on “good enough” products because they are cheap.
If you don’t want to be a news headline, I suggest you look at a company like Proofpoint because Microsoft isn’t “good enough”
Ask yourself this, why don’t you use Windows Defender or Security Essentials to protect your environment from virus and malware? Thought so……..because Microsoft isn’t that good at security.
As of December 2017, I still do not think ATP is a good value. Its better than nothing. But for our company, the cost per month per mailbox would buy a much better service with additional capabilities. The internet keeps getting more dangerous. EOP is not much better that 1990’s whitelisting/blacklisting. Unfortunately its difficult to convince the right people that EOP and ATP are simply in adequate.
Hi Paul, I am in the same boat as you (single user type tenant setup) and I have mine implemented in very much a similar way. I have many customers who balk at EOP and think its not a good threat protection service being offered for Exchange Online, they do come round most of the time once they see what it can do and how if setup correctly does provide a good layer.
Great article as always.