Next Step in the Fight Against Basic Authentication
Flush with the success of stopping millions of tenants from using basic authentication for email connectivity, Microsoft announced that Autodiscover is the next target in the process of removing basic authentication from Exchange Online. The November 16 announcement and November 17 message center notification (MC467901) both contain a simple message: using basic authentication for Autodiscover is unnecessary after email clients move to modern authentication, so Microsoft will disable basic authentication for the Autodiscover protocol.
Microsoft introduced Autodiscover in Exchange 2007 to help Outlook clients configure user profiles automatically by “discovering” the services Exchange offered to clients. The services include public folders, alternative (shared) mailboxes, the offline address book (OAB), and calendar free/busy (availability).
Today, the range of clients that support Autodiscover includes the Outlook family, mobile email apps using Exchange ActiveSync (EAS), and apps using Exchange Web Services (EWS). Other Microsoft 365 services (like Teams) also consume Autodiscover, and it’s important to configure the service correctly to make sure that clients can find published services efficiently.
With the deprecation of basic authentication for protocols like EAS and EWS, it doesn’t make sense to allow clients to continue sending username and password credentials to Autodiscover. Microsoft is now removing that ability. Autodiscover will continue to function perfectly well, but only with connections that use modern authentication.
Closing Off Potential Vulnerabilities
Closing off basic authentication for Autodiscover will eliminate another potential vulnerability for attackers to exploit. In September 2021, security company Guardicore reported that they had been able to gather the credentials of 96,671 unique Windows domain credentials by exploiting an Autodiscover flaw.
As I said at the time, I wasn’t too worried about the situation, and subsequently, the researcher involved in the disclosure admitted that it was a client-side issue. However, these issues underline the point that any transmission of username and password credentials can be potentially intercepted. Removing that possibility makes a heap of sense, especially after basic authentication is no longer possible for email connection protocols.
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.
Ready, Steady, Bang for Autodiscover Basic Authentication
Microsoft says that they are “starting right away” to remove basic authentication in tenants that have not used basic authentication “at all” in 2022. In early 2023, as the process to permanently remove basic authentication for email connectivity protocols reaches its conclusion, they’ll update Autodiscover in the remaining tenants. No tenant gets to vote, and Microsoft will exclude no customer from the basic authentication depreciation process. Even if you want to continue with potentially vulnerable connections, Microsoft won’t let you. It’s not exactly a libertarian approach, but it’s for the good of the overall service.
DIY Deprecation for Autodiscover Basic Authentication
If you want to get ahead of the curve, you can do so by deploying an Exchange authentication policy to block basic authentication for Autodiscover. The default authentication policy used by a tenant can be managed using the Microsoft 365 admin center (Figure 1) or PowerShell. I’ve used a policy to block basic authentication for years without any problems.
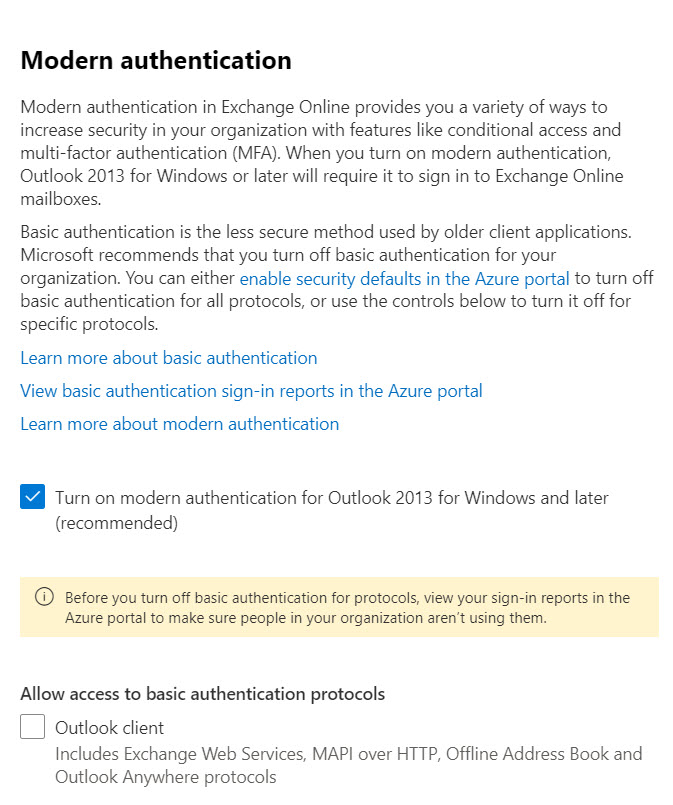
To check whether a tenant has an authentication policy in place that blocks basic authentication for Autodiscover, run:
Get-AuthenticationPolicy | Format-Table Name, AllowBasicAuthAutodiscover Name AllowBasicAuthAutodiscover ---- -------------------------- No Basic Auth False PowerShell Basic Auth False
To check the default authentication policy Exchange Online applies to accounts, run:
Get-OrganizationConfig | Select DefaultAuthenticationPolicy DefaultAuthenticationPolicy --------------------------- No Basic Auth
In this case, the “No Basic Auth” policy blocks basic authentication for Autodiscover for all accounts (unless an account is assigned a different authentication policy that permits basic authentication).
No Change for Exchange Server
Although Microsoft is eradicating basic authentication for Exchange Online, there’s no progress in making the same kind of change for on-premises Exchange organizations. Basic authentication remains all that’s available for clients to connect to Exchange Server. An arguable case exists that Microsoft had to remove basic authentication for its cloud service because the service depends on internet connections. The same isn’t true for on-premises Exchange where many connections originate from within a corporate firewall. However, on-premises Exchange supports external connectivity for mobile clients and OWA, and many of the recent exploits against Exchange Server have exploited the connectivity used for remote clients.
On-premises customers might ask why Microsoft hasn’t taken the work done to protect Exchange Online and transferred it to Exchange Server. It’s a reasonable question, and I think the answer lies in a simple response: “what configuration of Exchange Server should be protected?”
On-premises deployments are notoriously slow in deploying new software. Microsoft is only able to protect Exchange Online by constantly refreshing the 300K mailbox servers that run the service. If Microsoft came out tomorrow and said that it was possible to enable modern authentication in a future cumulative update Exchange Server 2019, how quickly would customers deploy that update? Given that many still run Exchange 2013 and 2016, I suspect that the answer would be “a long time.”
Turning off Basic Authentication Has an Effect
According to sources in Microsoft, they still see attackers attempting to exploit basic authentication for email connection protocols like POP3 and IMAP4. Turning off basic authentication for these protocols repels attempted password spray and other attacks and makes Exchange Online a safer environment with less likelihood of penetration of user accounts through techniques like business email compromise. Turning off basic authentication for Autodiscover is one step along the way. Enabling multi-factor for all Azure AD accounts is another.
SMTP AUTH is likely to be Microsoft’s next target, which is why tenants should upgrade PowerShell scripts to use Graph-based methods to send email. Admittedly, eradicating SMTP AUTH from Exchange Online will be harder, if only because of the many devices that send email, but it will happen. Someday.
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.




