Embracing a BYOD strategy is usually a good thing for your users and your company, but it also creates some concerns about the devices and applications that are being used to access corporate data.
To demonstrate the type of issues that arise I’ve connected an iPad to a user’s Exchange Online mailbox by setting up an account using the native email app on iOS. The user is able to make an ActiveSync connection to their mailbox, download email messages, and save any attachments to his personal Dropbox account that is also set up on the device.

Dropbox itself is not necessarily a problem. The concern for the organization is that users will save corporate data to untrusted or insecure external services that are owned by the individual user. There’s multiple strategies that can be implemented to mitigate this risk, one of which is Intune conditional access policies in combination with Intune mobile application management (MAM) policies.
To begin, lets set up conditional access in Intune for Exchange Online and SharePoint Online. In the Azure portal navigate to Intune mobile application management, and then go to the two conditional access settings. For each of Exchange Online and SharePoint Online, configure the Allowed apps to “Allow apps that support Intune app policies.”
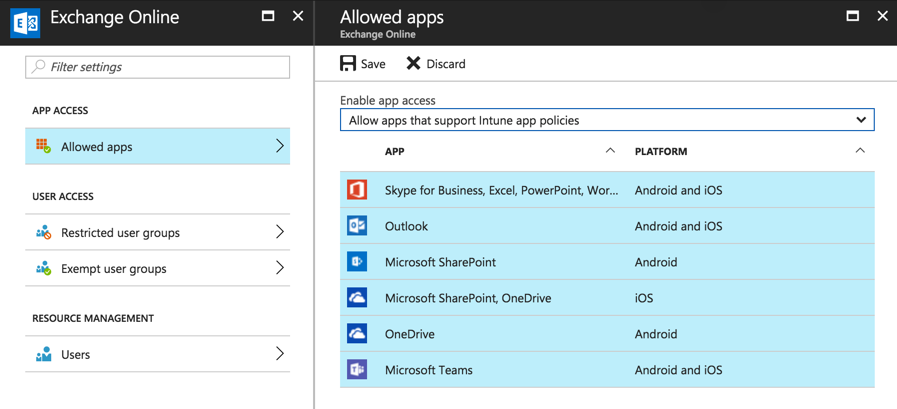
After saving the change, go to Restricted user groups and add the groups that contain the users you want the conditional access policies to apply to. For this example I’m using the same Azure AD group that is used to assign the EMS licenses to users, rather than create a separate group. For your own deployment you might choose to target MAM conditional access policies at a separate group that represents approved BYOD users.
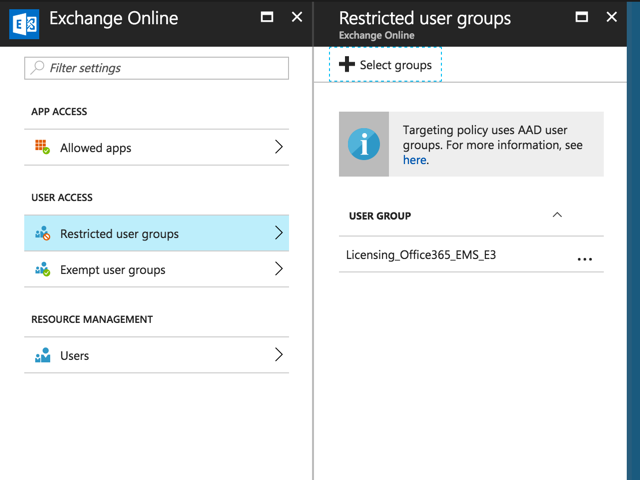
Make sure you repeat the same steps for SharePoint Online.
After creating the conditional access policies it will take a short time before they take effect for users. When the policies take effect the users who are targeted by the policies will no longer be able to connect to Exchange Online and SharePoint Online with apps that don’t support Intune policies. That will prevent the native mail app on iOS or Android from connecting, as well as a wide range of third party mail apps. An email notification is sent to the user to let them know that they need to use Outlook. This email notification will appear on the mobile device, but no other new emails will arrive on the device.
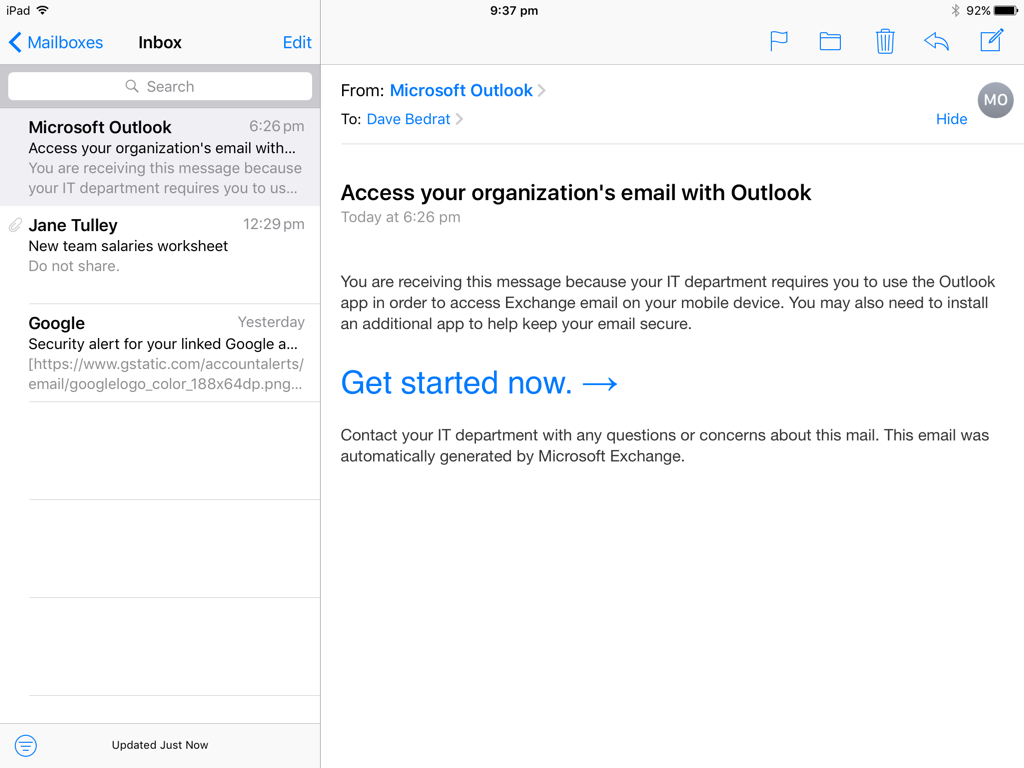
The user in this example will need to install the Outlook app for iOS. They’ll also need to install the Microsoft Authenticator app to act as an authentication broker for the managed Outlook app (Android devices need the Company Portal app instead). However, the user does not need to enrol their device in Intune, which is ideal for employee owned devices (BYOD).
When I was working through this demonstration I ran into what seems to be a bug with Outlook for iOS at the moment. When the user sets up Outlook to connect to the Exchange Online mailbox, they are prompted to authenticate via the Microsoft Authenticator app.
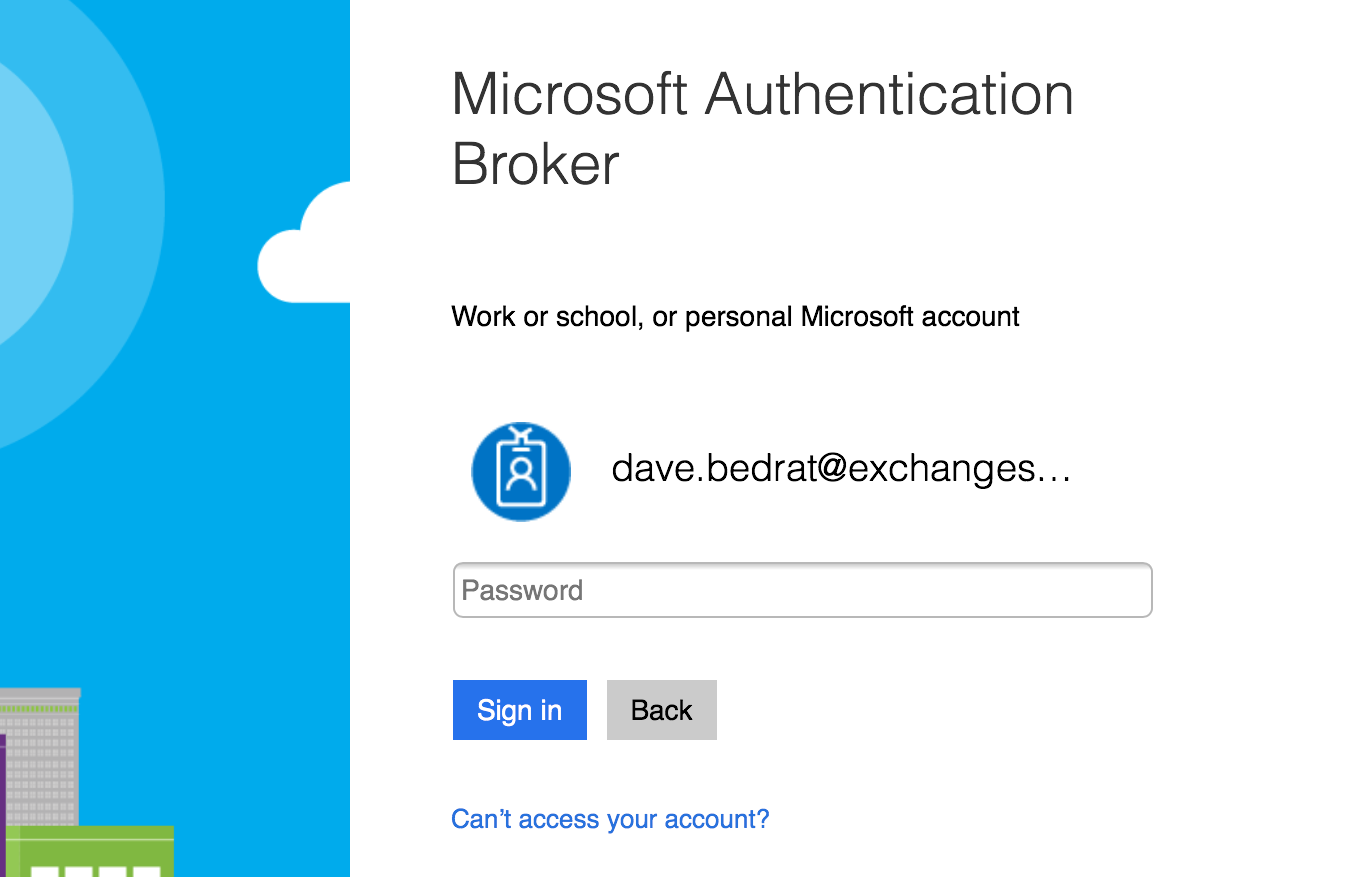
This is the normal process, but right now instead of a successful authentication the Outlook app returns an “Oops, something went wrong” message.
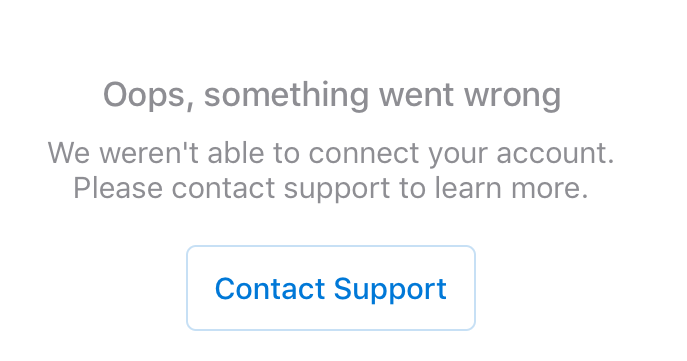
When I repeat the login process with another app on the device, the Microsoft Teams app, the authentication process takes me to the correct step to register the device. Registering a device for MAM conditional access is not the same as full enrolment in Intune, but is required for the MAM policies to be able to be enforced.
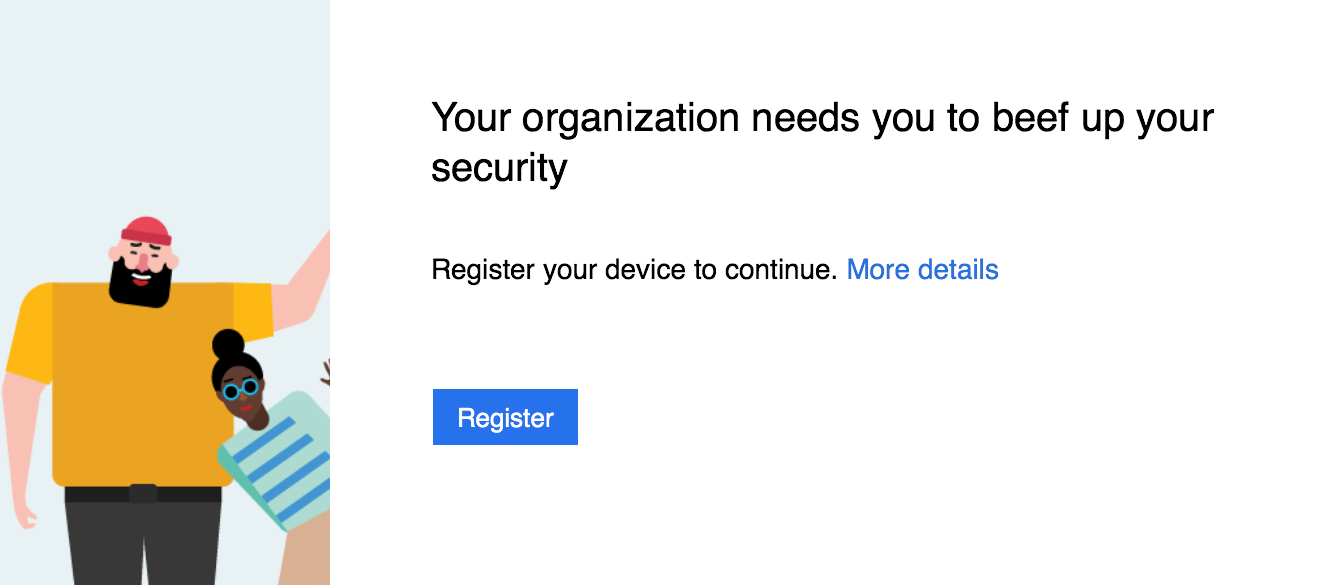
Registration takes just a few seconds, after which the user can access Exchange Online and SharePoint Online with managed apps (e.g. Outlook starts working after the device is registered successfully via Teams).
At this stage we’ve solved part of the original problem. Users are prevented from accessing Exchange Online or SharePoint Online using unmanaged apps such as the native mail app on iOS, and instead are required to use managed apps like Outlook, OneDrive, Teams and so on. However, the user can still access Dropbox from within the Outlook app.
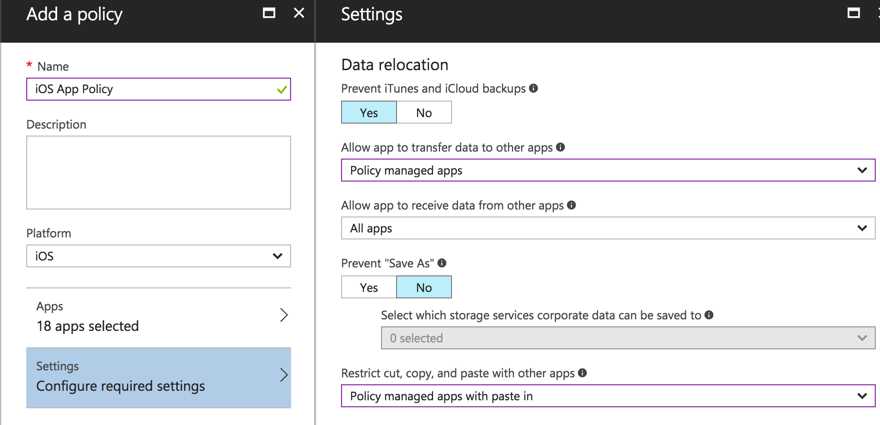
The solution to that problem is to configure an App policy in Intune App Protection. App policies are quite comprehensive and flexible. Among other things, you can use an app policy to restrict the transfer of data in or out of policy managed apps, including copy and paste of data. For this example I’ve configured:
- Policy managed apps to transfer data only to other policy managed apps. So the user can transfer data from Outlook to OneDrive or Excel, but not Outlook to Dropbox.
- Policy managed apps can receive data from all apps. So the user can copy data from Dropbox to Outlook if they need to.
- Cut, copy and paste can only be performed between policy managed apps, or from other apps to policy managed apps. But the user will not be able to copy and paste from a policy managed app like Outlook to an unmanaged app like Dropbox or Safari.
- For good measure I have also required a PIN for access to the policy managed apps. The user has not enrolled the device in Intune for MDM, so a device-level PIN isn’t enforced. The app policy will enforce the PIN at the app level instead.
After creating the policy we then need to go into the policy settings and configure an assignment to target the policy to a security group. Again I am using the same security group that is used to assign my Intune licenses.
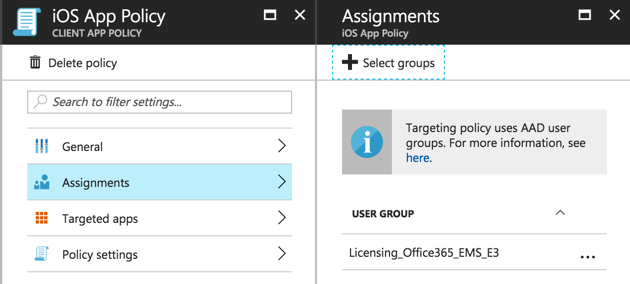
The policy assignment doesn’t take effect until the device or application checks in. You can see the status of the app policy for a user in the App protection user report that is available in the Intune App Protection area of the Azure portal. In the example below, the user’s Word app has picked up the app policy, but the other apps haven’t yet applied it.

Word will now enforce the configured policy by preventing the user from saving corporate data to unmanaged apps. For example, a Word document opened from OneDrive for Business can’t be saved to Dropbox.
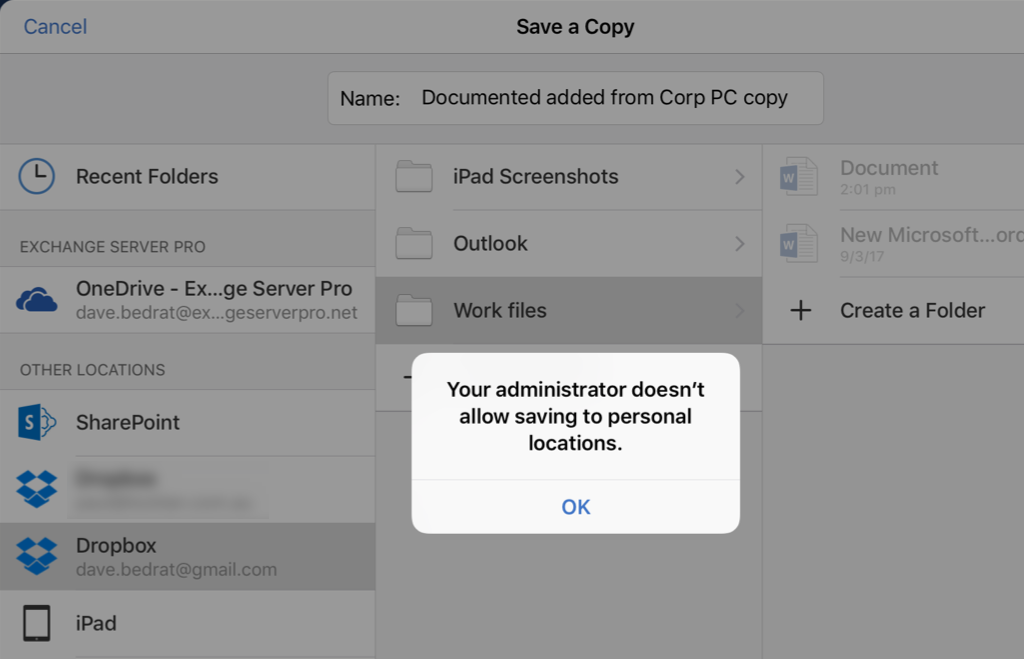
As you can see it is possible to use Intune mobile application management to prevent corporate data from leaking when it is accessed by users on personal devices. These features do require an Intune license for the user, but do not require the user to enrol their personal device for full MDM, which is often more appealing to them as they don’t need to allow total control over the device by corporate IT.



Pingback: Use Azure AD Conditional Access to Enforce MFA on Unmanaged Devices
Intune company portal is not working if I block browser based access. ? How to resolve this issue ?
When you get the “Oops Something Went Wrong” message, what did you do to fix the issue? I have a conditional access policy, preventing users from using a native client, and users sporadically get this message. If you have any information, I would greatly appreciate it.
Did you get anywhere with this? We are attempting to set this up for a BYOD trial and are receiving the exact same message. We are only allowing Outlook access for BYOD so have no other apps to connect to the Microsoft Authenticator app.
Any help would be much appreciated.
Great post. If a device is already enrolled with a 3rd party MDM, I believe that you cannot fully enroll the same device to Intune. But can you still ‘register’ the device to Intune still to use the MAM conditional access features?
Yes, you can still use MAM policies if you are using a third party MDM.
I have a question that maybe you can answer. We have a LOB that we updated and wrapped as of August. During this time we did only had the Online Exchange Conditional Access policy enabled to users can get their email using the native mail app of the mobile device.
Recently the LOB can not be accessed giving the following Alert:
“The application requires you to be enrolled with Microsoft Intune, but your account has not been setup. Contact your IT Department for help.”
I know for a fact that each person, including myself, has an Intune License as well as an account. Do you think this may be related to a conditional access issue or more on the Azure Account Issue or possibly a combo of both.
I have been scratching my head on this for sometime as the other apps work except for this LOB one.
Any sight at this point would be helpful.
Thanks
Hi Paul, me again. I was so confused by your post. I am still unsure. You used the line: “To begin, lets set up conditional access in Intune for Exchange Online and SharePoint Online.”
I could only see Conditional Access in Intune where I could set cloud apps and a number of conditions, I assumed the portal had been updated since your post. So I created 2 policies – and EAS CA policy and Exchange online desktop apps and browsers CA policy.
Today however, I found “Intune App Protection” in the portal which looks more like the screenshot you posted where I can configure Exchange and SharePoint conditional access – where I can set “Allow apps that support Intune app policies.”
Now what is the difference?
Also, to add to my confusion, I have legacy Silverlight portal Intune policies which are read only and can’t be deleted.
I appreciate your opinion and thoughts in this regard.
Thanks
Intune App Protection = Intune MAM policies, yes. The UI has changed a little since my post.
For the classic portal policies, this is what you need to know:
https://cloudblogs.microsoft.com/enterprisemobility/2017/10/23/this-one-is-important-time-to-migrate-your-v1-0-conditional-access-policies-to-v2-0/
Hi Paul, great article thanks.
I have a requirement from a client to be able to manage the native iOS mail client.
Is this only possible if the device is enrolled? Does enrolled management only give you the ability to provision an email profile and not protect the app data like a MAM policy? My understanding is that the iOS mail client is not an Intune compatible app and can’t be introduced to Intune via the SDK either. Do you have any insight or comment in this regard?
Intune has a device configuration policy type of “Email” for iOS that lets you deploy a managed email profile for the native mail app. I haven’t checked it recently but I believe that will work. There’s also a compliance policy that will block a manually created mail profile so that they must use the Intune managed one for corporate mail.
Thanks, but all of those require the device to be enrolled via the Company Portal and therefore the entire device is “managed” and corporate wipe or device wipe can be issued, but for those folks that don’t want their BYODs to be enrolled, but still use the native app, the company want to manage that app like they can the Outlook for iOS app through a MAM app protection policy. Is this possible?
No. The company can’t manage the email profile on an unmanaged device. Without enrolment/management they can only enforce some controls on Intune MAM-capable apps.
Pingback: Microsoft To-Do Reaches General Availability
Thanks great post.
One thing that keeps coming up with almost every company I go to is the use by the same user of both personal BYOD devices and Corporate CYOD devices.
The byod device only needs to register and nor enroll
the CYOD device needs to enroll
This scenario does not seem possible yet most companie I go to the user has 3-4 devices at least.
If I understand your question correctly, what I think you need to look at is the corporate device identifiers options in Intune:
https://docs.microsoft.com/en-us/intune/corporate-identifiers-add
Then the enrolment restrictions options:
https://docs.microsoft.com/en-us/intune/enrollment-restrictions-set
The corporate identifiers help to place byod devices into a separate group. The problem is, app protection policies only seem to work when I assign them to a user group. It didn’t enforce the policy when I assigned a device group.
Yes, that sounds right for the policy assignments. I believe I saw the same when testing myself.
Pingback: Is Outlook for iOS and Android a Free App?
Hi Paul,
Another great article.
I’m fairly new to Intune but ive put a couple of policies in place for BYOD (MAM policies) and COPE (MAM/MDM policies).
I cant seem to find a way of stopping a BYOD user from just using their native safari browser to login to 365 and copy/paste data between that and personal apps as well as downloading attachments etc.
How have you addressed this issue in the past?
Hi Ian,
There is a new feature in Preview right now for SharePoint called App Enforced Restrictions that will block some of the behavior you’re talking about, at least for SharePoint currently.
You can create a conditional access policy for SharePoint Online in Azure AD that only applies to iOS and Android, and only web browsers. Target it at any users/groups you want it to apply to. Within that conditional access policy you then go to the Sessions section and check the box to enable app enforced restrictions.
Once that’s done, go to your SharePoint admin portal and click the Device Access option in the bottom left. Check the box in the middle of the screen to enabled limited SharePoint access, and then choose if documents unsupported by Office Online are allowed to be downloaded, or just blocked from access via mobile browsers. Click OK to save the settings.
Now, users who are accessing SharePoint via a browser on a mobile device will be in a “limited” mode where they can’t download, print, or sync files. They can still view and edit files in Office Online. They will see a warning about this in a yellow notification bar across the top of the screen.
Since this feature is in preview, it will only show up in your SharePoint admin console if you have “First Release for Everyone” set for your O365 Organization. You can check this by going to the O365 Admin Center – Settings – Organization Profile and looking at “Release preferences”. Also, I believe you need to turn on Preview Features in SharePoint, which is in the SharePoint admin portal under Settings – Preview Features.
My understanding is that Microsoft will be rolling out these app based restrictions to all of the O365 products, but they are starting with SharePoint first.
That won’t stop them from copying/pasting data out of documents into non-managed apps, but it would stop them from downloading files to non-managed locations. To stop the copy/paste behavior, you could create a more restrictive conditional access policy that is based on iOS and Android, again target it at web browsers only, and then choose Block Access under the Grant section of Access Controls. That should keep them from accessing SharePoint online, Exchange Online, or any other cloud app you add to the conditional access policy, and force them to use the managed app.
I hope that helps!
Hi Paul,
When I go to Azure Portal ->Intune->Conditional access, I am getting
We’re not quite ready for you.. We’re updating accounts to be able to take advantage of the public preview as fast as possible over the coming weeks.
Is it a general issue?
Thank you.
It means your Intune tenant is not ready for the new portal yet. The migrations were supposed by be completed several weeks ago, unless the tenant has a blocking issue.
Review this article and if you need more help contact Microsoft/Intune support.
https://blogs.technet.microsoft.com/configmgrdogs/2017/05/18/intune-on-azure-migration-blocker-guidance/
Hi Paul
Can you please let me know if it is possible to configure Mobile Device Management Service for O365 from PowerShell? From configuration, I mean enabling MDM, changing device related settings, etc.
Thanks