Don’t Assign Privileged Roles without Oversight
Privileged Identity Management (PIM) is a component of Microsoft Entra ID that allows organizations to exert granular control and monitoring for highly privileged user accounts. PIM enables roles to leverage Just-in-Time (JIT) privileges for access to Azure and Microsoft Entra resources. Although PIM has been around for several years, many environments still fail to leverage its true benefits.
In another article, Mike Parker covers how PIM controls the activation of eligible assignments. Here, I cover how PIM uses a powerful role setting to require approval prior to account activation. Implementing this control creates a workflow that could stop attackers in their tracks even after they’ve succeeded in compromising administrative credentials.
Implementation
When viewing membership from both the user and role perspective, assignments are split into three tabs, Eligible, Active, and Expired. To take advantage of the JIT features of PIM, members added to roles must use the eligible assignment type. When a user has an eligible assignment for a role, they must activate the role before permissions are applied to the session…
After a role utilizes eligible membership, an administrator must modify the role settings to require approval to activate, as seen in Figure 1. The administrator then selects approvers unless the default approvers (Privileged Role Administrators and Global Administrators) are acceptable. The list of approvers supports the use of both Users and Groups of all types. This includes guest accounts and security and Microsoft 365 groups.
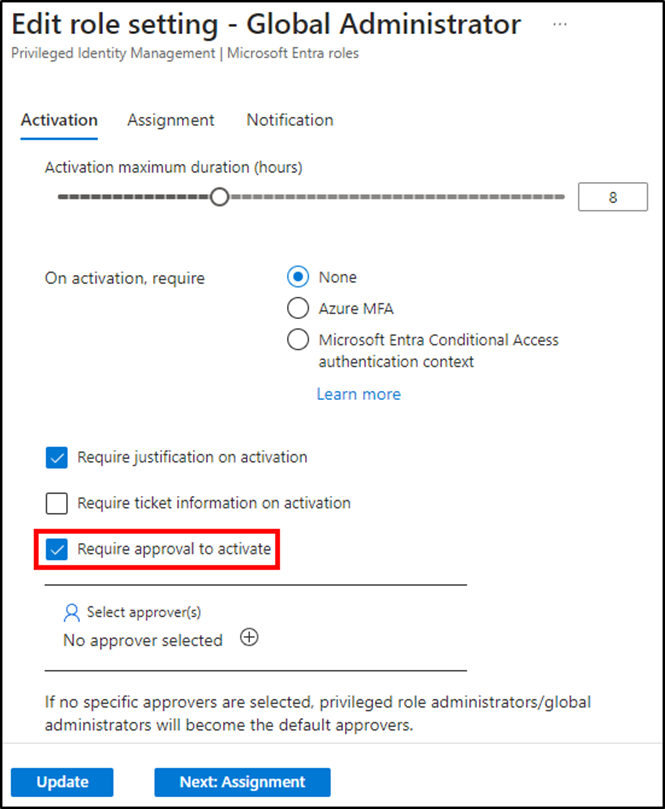
Notifications should utilize default recipients for Admin, Requestor, and Approver to “Send notifications when eligible members activate this role”. These settings ensure that:
- Approvers receive notifications for activation requests.
- Admins receive notifications that the activation request was approved.
- Requestors receive notifications that the activation request was approved.
Additional recipients can also be used instead of, or in addition to, the default recipients. Figure 2 shows the available notification options.
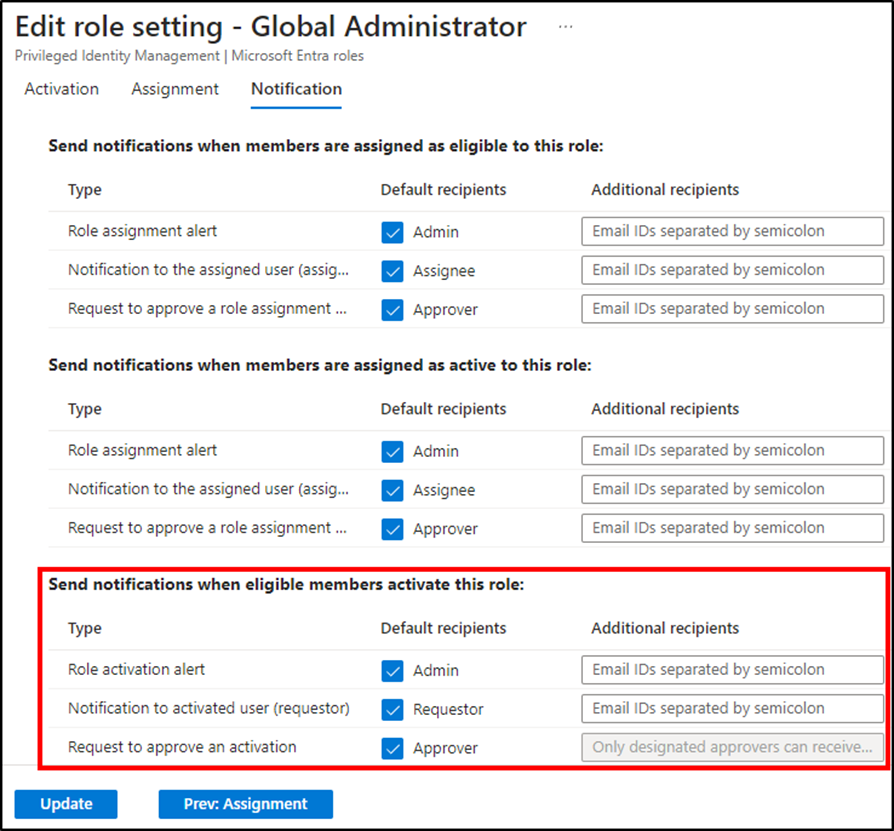
These are the only required steps to configure a role to require approval. The workflow from the requestor and approver perspective is equally as simple.
Workflow
Once a user is granted an eligible assignment for a role, they can “Activate” the assignment. In doing so, they initiate the activation workflow. The requestor must adhere to any additional activation requirements configured in the role setting. Figure 1 displays other activation settings such as requiring justification or Azure MFA. From there, the activation request sends a notification to the mailbox of all configured approvers. At this point, the activation is in a pending state.
Any of the approvers can Approve or Deny the request in the Entra admin center Approve requests blade. Approving or Denying requests requires the approver to provide a justification for their decision. Upon approval, all approvers receive another email identifying who reviewed the request. Finally, the requestor is notified of the approval.
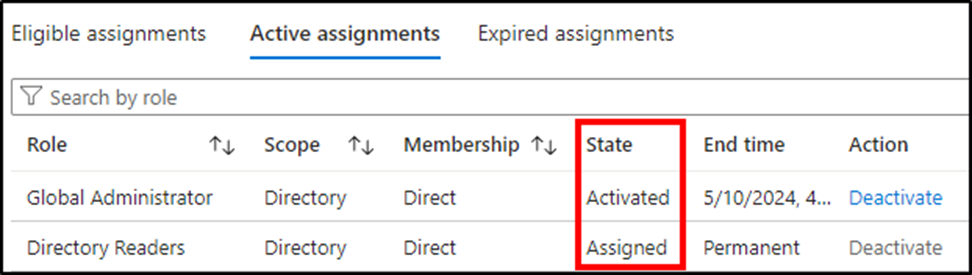
Once all stages of the workflow are complete, access is granted to the requestor. The activated assignment appears under the requestor’s Active assignments tab with a state of “Activated”. Figure 3 shows the difference between a role that has been elevated and one always assigned to be in the active state.
If permissions associated with the newly activated role are not immediately applied, the Troubleshooting Recently Activated Permissions in Privileged Identity Management article may be helpful.
Auditing
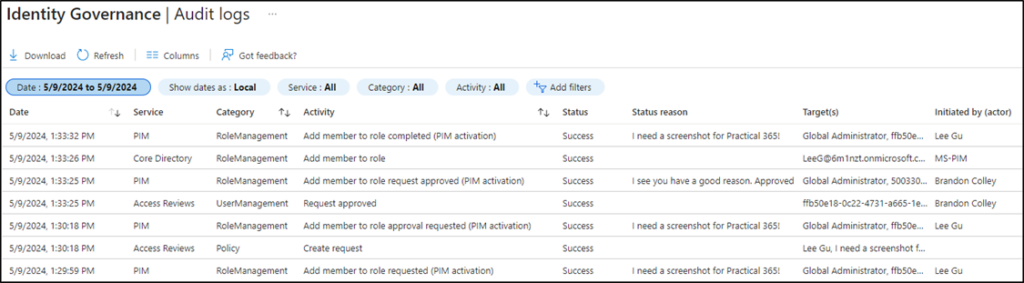
The approval process lifecycle provides monitoring opportunities in addition to the added layer of security. Identity Governance audit logs capture details for the addition of new members to roles, modification of role settings, and activating an eligible assignment. They also log the full approval lifecycle including the reason for an activation request and the justification provided by the approver. Figure 4 shows this workflow. Starting at the bottom, Lee requests PIM activation, Brandon approves the request, and the MS-PIM actor adds Lee to the role.
The PIM resource audit logs hold similar details and include a “My audit” option that provides details related only to the logged-in user. Additional audit information is available using the access reviews feature but this solution requires an ID Governance license.
Leveling Up
The setting to require approval from a manager or colleague arguably adds the highest level of security surrounding account activation. Requiring approval utilizes a sort of rocket launch double-check as it requires a second account (or human) to grant permissions. Most other PIM settings do very little to provide additional security when attempting to determine the difference between an account owner and an adversary elevating an account’s permissions.
Implementation of an approval workflow for the highest privileged roles encourages administrators to use roles appropriate to the task. There is very little reason for members of Global Administrators to regularly log into admin center. Assigning multiple roles to administrative personnel, utilizing varying levels of account protections, is one method to achieve the least privilege.
Finally, it is important to note that the use of PIM does not replace the need for other security measures. Utilizing dedicated administrative accounts and workstations helps to provide segmentation and protects against phishing attacks. Implementing conditional access policies are imperative to increase overall security posture by requiring MFA, enforcing trusted locations/devices, and limiting actions when risk conditions are present. Continuing to add layers of security to Entra accounts and applications is truly how to level up.




