Mobile Threat Defense Blocks Threats to Apps
There have been many cases of scams, phishing, and malicious apps around the world lately. The use of fake apps or malicious apps has led to people and companies losing large amounts of money like those mentioned here. Increased awareness of the need to enhance mobile endpoint security to prevent issues mentioned earlier from happening, especially in the context of Bring Your Own Device (BYOD) deployments where both corporate and personal data are vulnerable. Many solutions are available and Microsoft’s offering is Defender for Endpoint. In this article, we focus on the Defender for Endpoint functionality and features related to mobile devices, specifically for BYOD scenarios. Defender for Endpoint works on Windows, macOS, and Linux endpoints.
BYOD – Mobile Application Management
BYOD deployments allow users to connect their own mobile devices to the corporate environment. Employees purchase and own devices, not companies. BYOD can lead to problems when administrators attempt to “enhance security” on devices, like preventing screenshots at the device level, blocking iCloud backups, etc. Thinking that the company has full control over devices can make employees feel uncomfortable when they access personal data. I have witnessed some very unfortunate events that resulted from administrators’ mistakes. This is due to the fact that MDM management software often has full control over the devices. Examples of such events include wiping the entire device (including the photo albums) of a VIP user because an administrator submitted a request for the wrong user.
There should be some way to control or prevent accidents like this, but accidents do happen… Whenever such a problem occurs, it reduces people’s confidence in the solution. Eventually, users might ask for company-provided devices to avoid losing their personal data. Giving devices to users is likely to cost more than a BYOD deployment.
Instead of enforcing policies at the device level, Microsoft Intune enables administrators to enforce policies and restrictions at the application level. Limiting policies to applications reduces the potential impact of accidents since only the target applications are affected. Refer to this article about configuring Intune MAM to protect mobile apps.
Defender for Endpoint and Intune MAM
There is a drawback to application-based management, which is the leakage of information to other parts of the devices. For example, Intune MAM (implemented using an application protection policy) can detect if the device is jailbroken or rooted but cannot detect if malicious apps are present on devices. When the information security team knows this limitation, they will simply say we need to control all devices.
Luckily, Microsoft enhanced the application protection policy a while back to include a launch condition called Mobile Threat Level (referred to as Risk Signal in some Microsoft documentation). This condition triggers the preferred mobile defense app to check and report if the device is “clean.” If a mobile device app is not installed, it prompts you to install one. Microsoft Defender for Endpoint is one of the applications supported by this check of course. Other vendors are supported, but this article focuses on configuring Intune MAM to use Defender for Endpoint as a Mobile Threat Level check provider.
How does the check work? In short, when MAM’s enabled app is open, it checks if the application, registered as a mobile defense provider (i.e., your mobile security platform of choice), gives a green signal. The green signal means the device is safe and the MAM-enabled app can continue to open and allow users access to corporate data. If the signal is not returned or present, MAM can reject corporate data access or even wipe out corporate data.
An ideal situation is where a policy requires a device to be clean before the user can open or set up any MAM-enabled app. This is another way of saying that clients must have mobile security apps installed to perform regular and real-time checks against threats. This is an effective yet simple way to enhance the device’s security level. It can be presented as an “employee benefit” to protect employee-owned devices from scams or malicious apps. We kill two birds with one stone here.
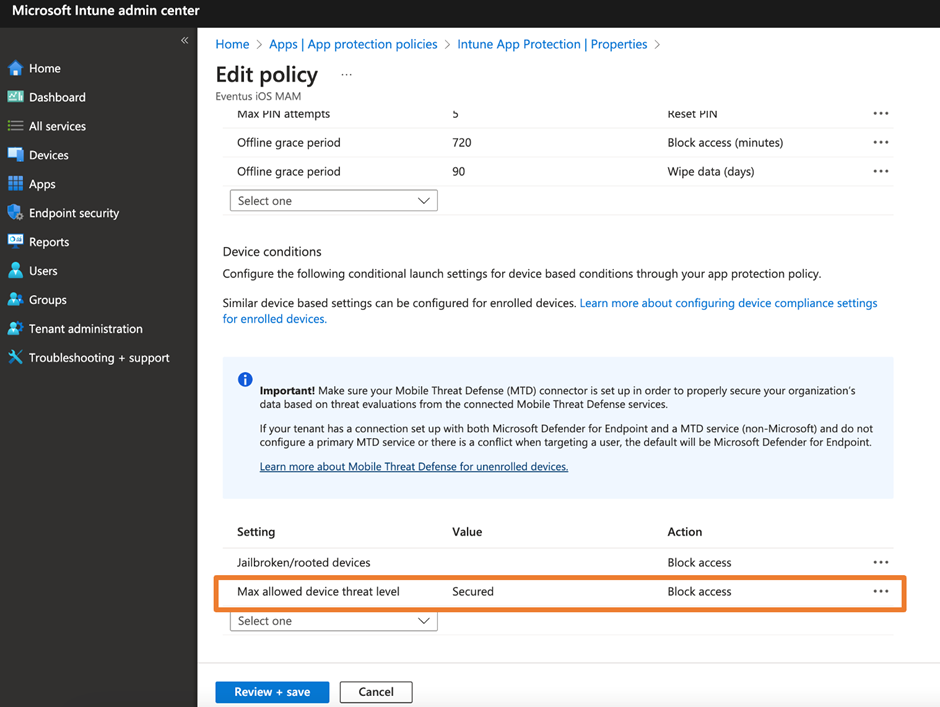
It’s simple to accomplish the goal. Simply enable the device condition as shown in Figure 1 and the rest will be taken care of. Once the policy is deployed to endpoints, they are prompted to install Defender for Endpoint and sign-in with their Microsoft 365 account to enable the feature. People using this feature require a Defender for Endpoint P1 or P2 license or Microsoft 365 Business Premium license. This also includes the Defender for Endpoint Business license. The Microsoft documentation defines the policy levels you can configure. Whenever possible, I choose Secured, but pay attention to what we will discuss next about customizing Defender for Endpoint mobile apps.
Customizing the Defender for Endpoint App
Microsoft updated the Defender for Endpoint app with the ability to configure and customize its behavior. This provides us with a way to enable or disable certain features as shown in Figure 2. Note that if you are deploying Defender for Endpoint in an MDM solution, the configurations will be different from those explained here. You can refer to this Microsoft article for devices and how to set them up.
One of the settings I always update when deploying Defender for Endpoint for MAM is to disable web protection. This uses VPN-based detection. Even though it makes the solution less secure, it creates a bigger issue because many users will complain about a reduction in battery life. This is because VPN-based web protection creates a VPN tunnel on the device itself and forces all traffic to route via that VPN tunnel to allow Defender for Endpoint to check traffic to detect potential malicious activities. The use of VPN tunneling in mobile OS consumes a lot of power and creates a noticeable reduction in battery life.
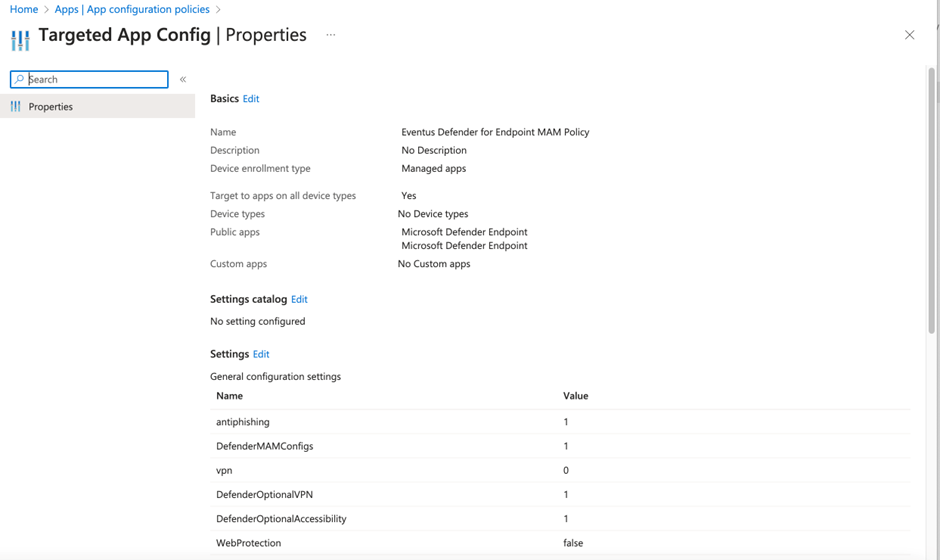
Microsoft has updated Defender for Endpoint for Android to allow administrators to skip VPN permission when installing the app. As long as VPN permission is not given by users or disabled by administrators, Defender for Endpoint will monitor other apps’ traffic or web requests for scams or phishing using Accessibility functions instead of VPN. This improves the battery situation a lot. At the time of writing, iOS still uses the VPN-based approach and hence we often have to disable the feature. Figure 2 illustrates the usual configurations I deploy. Table 1 lists the meanings of the configuration settings are listed.
| Configuration Key | Description |
| DefenderMAMConfigs | Set to 1 enables the mobile app to read the configuration from the MAM configuration policy |
| antiphishing | For Android only. Set to 1 enables web protection check |
| vpn | For Android only. Set to 1 enables the app to optionally request VPN permission needed to support VPN-based web protection. Meaning the app will continue to function if permission is not granted. |
| DefenderOptionalVPN | For Android only. Set to 1 enables the app to optionally request VPN permission needed to support VPN based web protection. Meaning the app will continue to function if permission is not granted. |
| DefenderOptionalAccessibility | For Android only. Set to 1 enables the app to optionally request accessibility permissions needed to support accessibility-based web protection. Meaning the app will continue to function if permission is not granted. |
| WebProtection | For iOS only. Set to false disables the web protection check |
You can reference here for Android and here for iOS configuration keys. Also, note that the configuration keys are case-sensitive. The app configuration policy illustrated in Figure 2 is configured as one policy for both iOS and Android apps. You don’t need to do that, but I was lazy and mixed both platforms to reduce the number of policies.
User Communication is Key
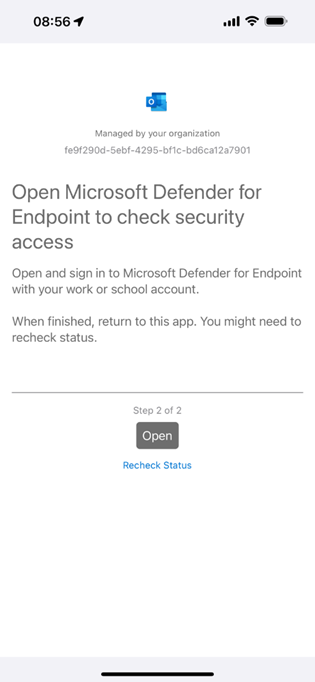
Remember to communicate with your users before enabling app launch conditions as this deployment is not without issues. I often experience (as a user and in client support) that the check cannot completed at the device level meaning that Defender for Endpoint does not give the green light to proceed, similar to Figure 3.
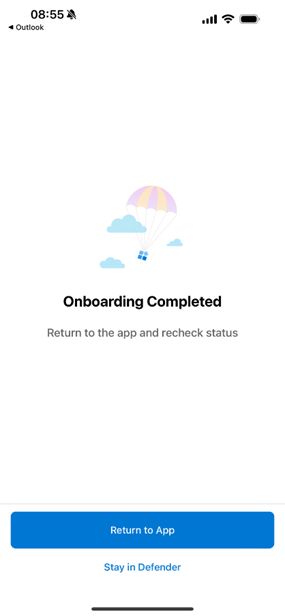
But when we open the Defender for Endpoint app, it shows that everything is fine (Figure 4). No matter how many times you press the Return to App button, it won’t pass the check. Often this can be resolved by killing the app you need to use (such as Outlook) and then relaunching it. One reason why this happens is when Microsoft updates apps using a different version of an SDK. This can cause a mismatch when apps like Outlook and Defender for Endpoint try to communicate. The issue can be resolved by updating apps to the latest version, which is always a best practice in any case.
Mobile Threat Level is Recommended if You Are Already Licensed
If you already deployed Intune MAM, I would say deploying Mobile Threat Check is a must-do item. This is given the fact that many of the security risks around corporate data, or even users, originate from devices. If your license already includes Defender for Endpoint, I encourage you to explore Mobile Threat Check and enable it to enhance security. If not, you consider purchasing Defender for Endpoint P1 (P2 is even better) as a standalone license to enable additional protection.




