Understand PIM to Maximize Its Productivity
Privileged Identity Management (PIM) may be available in your tenant, but is PIM configured to maximize productivity, and are administrators using it efficiently? PIM includes several subtleties that must be modified out of the box to truly leverage the benefit of PIM. Even then, it’s possible the just-in-time benefits are being bypassed. This article outlines how to get started with PIM, how to audit its use, and what workarounds could be circumventing your security controls.
Getting Started with PIM
To use PIM, a tenant requires Microsoft Entra ID P2 or Microsoft Entra ID Governance licenses. A license is required for each user that utilizes any PIM feature. This can mean a few different things. Microsoft explains PIM licensing here.
After the first PIM license is activated, PIM features become available and all existing members of administrative roles are automatically converted to PIM as “active” memberships. Active membership was previously referred to as “permanent,” which now holds a completely different meaning in PIM. Instead of walking through that confusion, we focus here on what has always been called an “eligible” assignment.
Eligible PIM Assignment
Eligible assignment is what enables the power of PIM. Eligible assignments to highly privileged roles must first be utilized, and role settings need to be customized. Most of PIM’s benefits surround the role settings associated with the “activation” of an assignment. When a member of an Entra role is “eligible,” that user must perform an extra step to activate the privileges associated with that role.
Role settings define what this step looks like and can be configured to require justification, a ticket/case number, or manager approval prior to activation. A growing number of opportunities are unlocked once eligible assignments are in place. So, how does an administrator or auditor know if eligible assignments are in use?
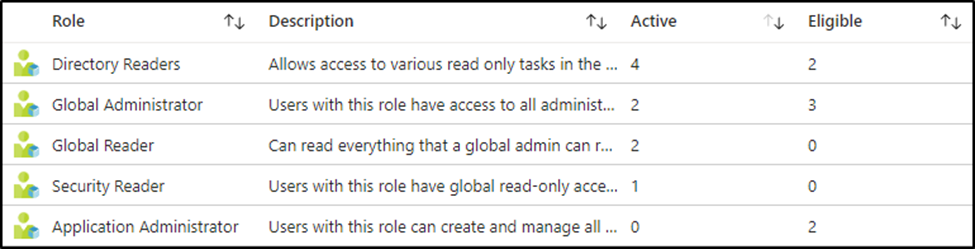
Probably the simplest method is shown in Figure 1. The PIM GUI displays the number of active and eligible members for each role. These columns are sortable for a quick glance and can be exported to csv for a more detailed review. Figure 2 shows the output of the exported file containing assignment state, name, role, and several other columns. This information can also be reported on using this PowerShell script.
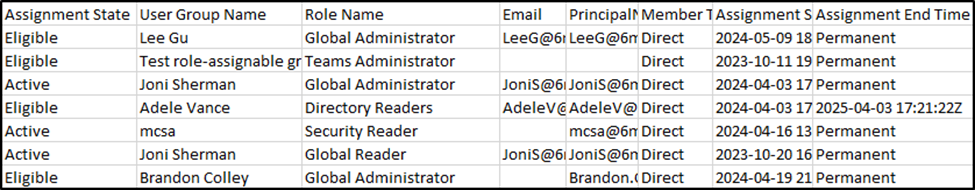
Accounts configured with active assignment possess the permissions of their roles as soon as authentication is successful whereas eligible members must adhere to the activation rules defined earlier. A benefit of this extra activation step, even at its weakest, is the ability to audit individuals and roles.
Logging
Entra stores logs in multiple locations. Sign-in logs provide a detailed account of authentication attempts and can be filtered on multiple attributes such as user or application, but they won’t tell the full story of PIM activation. Audit logs provide a more comprehensive view of the workflow but tend to be quite noisy. Filtering by Target and specifying a role or user can identify actions of a specific account, or details associated with a specific role. The PIM menu also offers a Resource audit that lists all membership changes for roles. It’s searchable but the filtering options are highly limited. Finally, access reviews are a more advanced option for reviewing logs and creating an approval workflow. This option requires a Microsoft Entra ID Governance license.
Evaluation of these logs may uncover possibly dangerous patterns of administrative behavior. Much like water, human tendency is to follow the path of least resistance so it’s not uncommon to identify patterns of administrators continuing to elevate a role with the highest privileges available even to perform mundane tasks. It may also become evident that users are making it part of their daily routine to activate privileges every morning. While these routines may not be ideal, more dangerous methods exist to work around eligible assignments.
Modifying Role Membership
Permissions are plentiful in Entra ID. There are over 100 roles, each with a different set of permissions. Some of these roles can directly modify PIM role assignments. Of course, Global Administrators have these rights, but the Privileged Role Administrator and Partner Tier 2 Support roles also possess these rights. The use of role-assignable groups adds another layer of complexity when identifying who might be able to manipulate role membership.
Role-assignable groups can be granted membership to Entra roles in the same way that users are directly added. Members of these groups then inherit the role permissions through group assignment. Modification of members of these roles is reserved only for the Global Administrator and Privileged Role Administrator roles. However, groups also have owners that can modify group membership. Figure 3 shows an example of a role-assignable group with an owner. This owner can update the list of members, which indirectly adds members to any Entra role of which the group is a member.
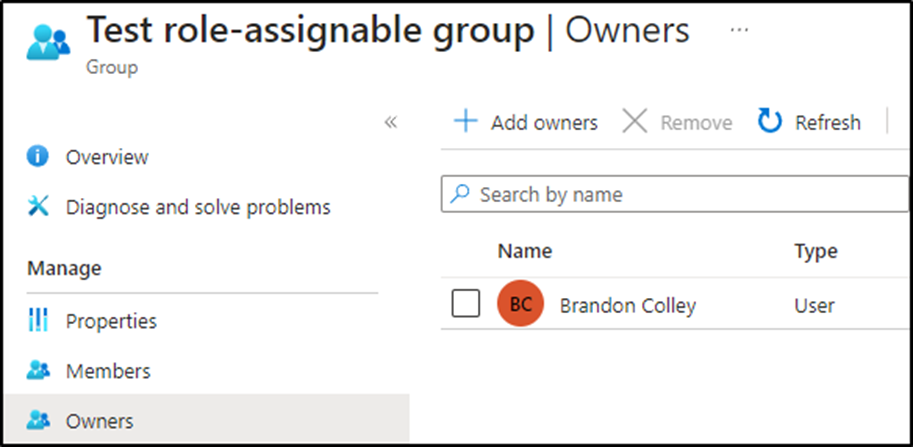
Membership changes that occur via group changes do not appear in the PIM resource audit menu. Log entries can be found in the audit log but there is no indication that the modification resulted in role membership. In fact, it may easily blend in with changes to standard groups.
Exploring PIM’s Full Potential
These methods of role exploitation continue to increase the attack surface, but the primary goal remains the same. Utilizing eligible assignments for all privileged roles creates an additional barrier for both adversaries and administrators looking for a shortcut to administration.
Performing continued audits of role members and groups ensures administration is being performed as intended. Analyzing the sign-in and audit logs helps detect risky behavior. Being proactive and intentional with administration will ensure PIM is used to its full potential.





Want to automate your PIM configuration and assignment? Or get a visual report for PIM activities? My EasyPIM module can help you, please check https://github.com/kayasax/EasyPIM
This is a nice one. Will definitely test it.