But You Need to Act Now
The difficulties of bringing a large community through a fundamental technical transformation are vividly illustrated by the many steps in Microsoft’s campaign to eradicate basic authentication from Exchange Online. This project affects how the largest Microsoft 365 workload operates across millions of tenants and hundreds of millions of individual users. It’s a great example of why herding cats is so difficult.
Microsoft has been trying to remove support for basic authentication for seven email connection protocols (MAPI, RPC, Offline Address Book (OAB), Exchange Web Services (EWS), POP, IMAP, Exchange ActiveSync (EAS), and Remote PowerShell) for the last three years. They’ve already disabled basic authentication for millions of tenants and the pace has quickened considerably over the last few months. Exchange Online is a much safer place today because a much higher percentage of user accounts are immune from password spray and business email compromise (BEC) attacks, but there’s still lots of work to do.
Compromises and Initiatives to Push the Project Along
In a drive to get to a point where they could finally flip the switch, Microsoft granted an exemption for SMTP AUTH to allow customers to continue using multi-function devices, programs, and scripts that use Exchange Online to send emails (switching to use Graph APIs is not difficult, but it takes time to find, upgrade, and test code). Microsoft also co-operated with Apple to make sure that iOS and iPadOS users could continue to connect to Exchange Online with the native mail app.
And now, a month away from the October 1 deadline, Microsoft announced that they are giving customers one last chance to request a three-month extension to continue using basic authentication before the guillotine finally descends. Microsoft isn’t saying why they’re giving customers a little extra time, but it’s a reasonable guess that they’ve heard from some organizations that they just won’t be able to meet the October 1 deadline. Stopping users from connecting to their mailboxes has a big effect on company operations, hence the desire for “just a little extra time.”
If you’re in the position where you need extra time to upgrade POP3 and IMAP4 clients and apps, make sure that ActiveSync clients running on multiple mobile devices continue to work, and validate that PowerShell code will continue to work, then you must apply for the three-month extension. Pushing off deprecation day to January 1, 2023, won’t happen automatically.
Seeking an Extension
Microsoft is leveraging the self-service support capability built into the Microsoft 365 admin center to allow customers to seek a one-time extension for basic authentication in a tenant. During September, customers can opt out of basic authentication disablement. This means that Microsoft will not include the tenant in the list that they’ll use to start disabling basic authentication beginning on October 1. However, the clock runs out on January 1, 2023, and Microsoft will then disable basic authentication permanently with no possibility for tenants to use basic authentication for Exchange Online connections thereafter.
To request an extension, use this link to open the Microsoft 365 admin center with a pre-populated support request.
After October 1, Microsoft will start to disable basic authentication. If you discover that disabling basic authentication causes problems for your tenant, you can use the same process to request Microsoft to re-enable one or more of the affected protocols. Microsoft says that it should take about an hour for basic authentication to begin working again for the requested protocols. Once again, after January 1, 2023, all bets are off, and you’d better be prepared to function exclusively with modern authentication for email connectivity.
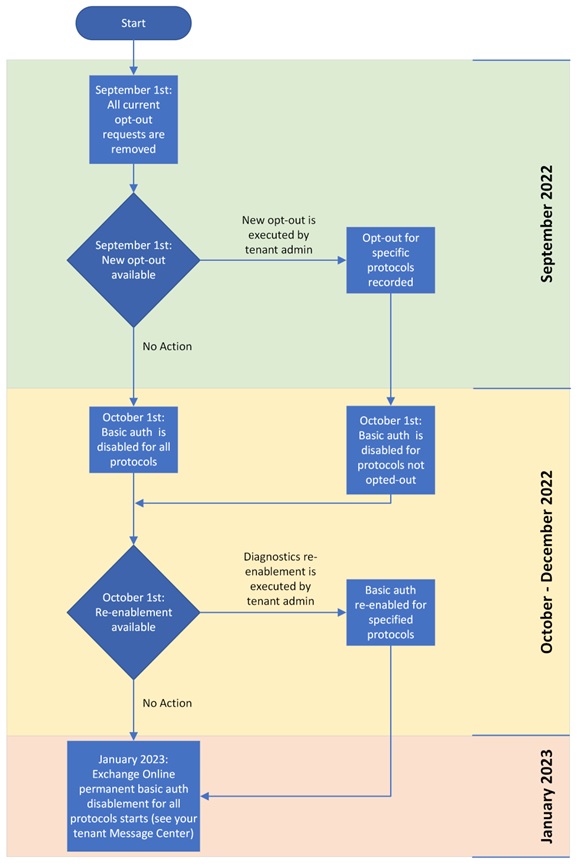
Figure 2 is Microsoft’s timeline for the remaining stages of the project to deprecate basic authentication for the seven connectivity protocols in Exchange Online.
No Basic Authentication for Microsoft 365 Apps for Enterprise
In an associated development, Microsoft plans to upgrade the Microsoft 365 apps for enterprise (Office subscription apps) with a new feature to block access to documents using basic authentication. This feature is currently in private preview. Basically, if you try to open a file stored in a location using basic authentication, apps like Word and Excel will block access instead of being willing to open the file. This won’t affect the opening of Office documents stored in SharePoint Online or OneDrive for Business as these services use modern authentication. It should help to block access to files used by attackers to inflect accounts with malware.
Long Road with End at Hand
The project to remove basic authentication from Exchange Online has traveled a long road. With a last push, we should get there on January 2023. If you’re not prepared now, it’s time for a renewed effort to ensure that clients, apps, and users are ready to drop the insecure and inadequate protection afforded by basic authentication. Time’s running out (and this time, Microsoft is serious), and given the progress to date, I think that January 2023 deadline will hold.
PS. If you want to get the inside track about the great Exchange Online basic authentication depreciation project, listen in to Greg Taylor’s session at TEC 2022. The word is that Greg has some great stories to tell about his interactions with customers and partners as he laid out the logic and logistics behind removing basic authentication.
Microsoft Platform Migration Planning and Consolidation
Simplify migration planning, overcome migration challenges, and finish projects faster while minimizing the costs, risks and disruptions to users.





This is a nightmare – I have 7 or 8 aliases within Gmail that have been working perfectly for almost 10 years. All of my client email comes into one webmail account and I can colour code according to client. Do I now have to check 7 separate mailboxes 3 times a day? Can you recomment an alternative to Gmail if Gmail can’t find a solution to this? Surely two enormous tech giants can work something out between them… ?
I’m not sure what the question has to do with Exchange Online and the removal of basic authentication?
If you strougle with Exchange Web Services and Basic authentication deprecation – I’ve created workaround: A service that proxy requests with oauth2 tokens. So this allows change authentication without touching the app code 😉 https://github.com/mmalcek/basicToOauth