My team has recently worked on some projects featuring multi-tenant and multi-Exchange environments. A common requirement for all projects is the ability to share free/busy information across all environments. In this article, I will dive into using free/busy sharing with Exchange/Microsoft 365 in the worldwide cloud.
Sharing Free/Busy Information
Let’s start with the obvious issues: how to conduct authentications between tenants and know where to query for free/busy information. Microsoft introduced a hosted service called Microsoft Federation Gateway (MFG) with Exchange 2010 to simplify the process for exchanging authentication tokens between different Exchange organizations, and essentially acted as a broker for Exchange Server to support free/busy sharing. It’s a free service and it is still used in the latest version of Exchange and Exchange Online.
In nutshell, MFG forms a trust called Federation Trust between Exchange Server/Exchange Online with MFG and stores the free/busy endpoint URL information. During the initial setup, we used PowerShell to query the MFG for the free/busy endpoint information and store that information in Active Directory or Azure AD. MFG helps with authentication by issuing a certificate during setup that it then uses for system-to-system level authentication. This mechanism allows different Exchange systems (Online and Server) to communicate with each other without the need to create service accounts.
Let’s get into the configuration. For each system, you need to do the following:
- Create Federation Trust with Exchange Server/Exchange Online
- Validate ownership of a domain via a DNS TXT record.
- Add an organization relationship policy.
All Microsoft 365 tenants are preconfigured with a MFG connection, so there is no need to add any additional settings (i.e. items 1 and 2 above). In addition, if you run the Hybrid Wizard for your Exchange environment, the setup is likely done as MFG is how hybrid Exchange shares free busy information between Exchange and Exchange Online.
Microsoft Platform Migration Planning and Consolidation
Simplify migration planning, overcome migration challenges, and finish projects faster while minimizing the costs, risks and disruptions to users.
Creating a Federation Trust Between Exchange Server and Microsoft Federation Gateway
You must create a federation trust to publish information to MFG and generate the required certificates. You can create the Federation Trust using:
- The Exchange Control Panel (ECP) for Exchange Server (Organization > Sharing > Federation Trust)
- The Exchange admin center for Exchange Online (Organization > Sharing).
- PowerShell.
You need to select a primary domain to be used by the federation trust. This domain is used by other admins to locate your federation configurations in MFG. You can use any domain from your accepted domain list. I recommend selecting the best-known domain (the one used by most users) because administrators often use someone’s email domain to look up MFG. In case the organization uses multiple domains for user email addresses, you can add additional domains to the organization trust to support look up of the federation information from MFG.
As part of the federation trust setup process, MFG generates a challenge (a text string) for you to put in the public DNS as a TXT record. Being able to create the TXT record for the domain proves your ownership of the domain (Figure 1).
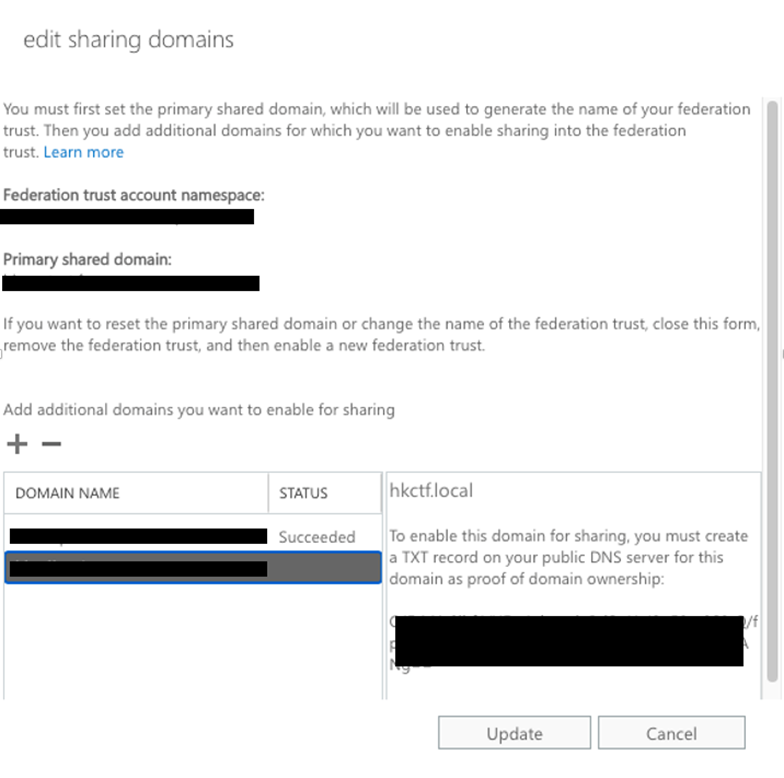
The purpose of adding all your email domains to the federation trust is to allow other administrators to locate your Exchange and the corresponding settings via MFG when they set up free/busy sharing within your Exchange environment.
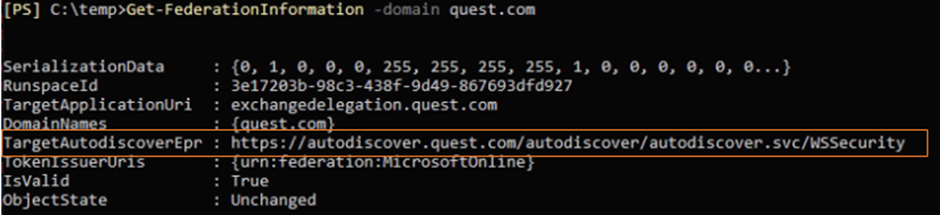
You can use this PowerShell command to query MFG to verify if the published information is correct:
Get-FederationInformation -DomainName <email namespace>
I recommend that you run Get-FederationInformation after configuring the Federation Trust to confirm the setting, as shown in Figure 2. Make sure the URL listed in the TargetAutodiscoverEpr property contains a URI that is internet accessible. If not, change the URL configuration of your Exchange organization and recreate the Federation Trust to store the correct information in MFG.
Configuring Free Busy Sharing between Exchange/Microsoft 365 and Exchange/Microsoft 365
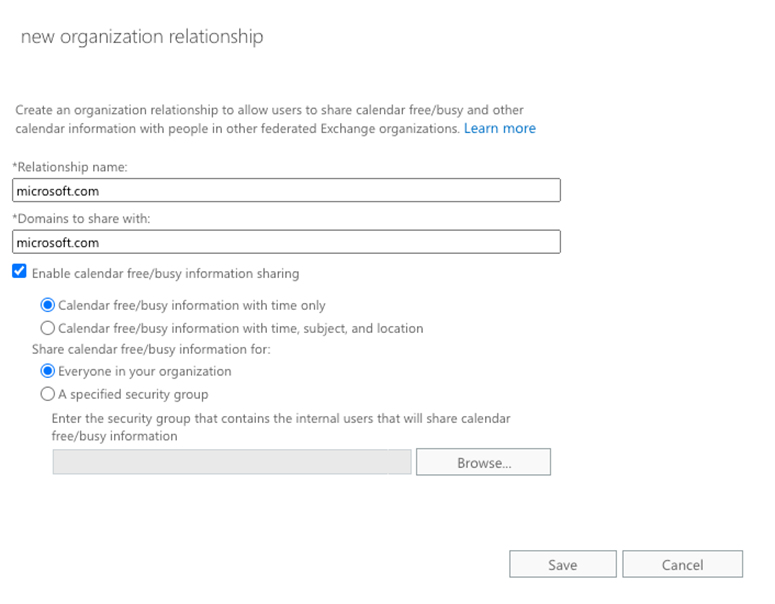
Let’s switch to the other side of the configuration: to allow users in your Exchange/Microsoft 365 organization to access free/busy information in external organizations. To do that, you need to add an organization-sharing entry in ECP or EAC. Specify the domain of the target domain and select the option to enable free/busy sharing (Figure 3). Exchange Server and Exchange Online will automatically handle the complexity of exchanging certificates and creating the necessary records in AD/Azure AD to support cross-organization free busy lookup. You can also control the options to allow restricted free/busy access for users from external organizations or to restrict specific group members from being able to see free/busy information within the target domain.
In the previous section, I mentioned the importance of publishing the correct Exchange Server URL to MFG. In case the URI is incorrect, you can override it at the organization relationship level. After creating the Organization Trust, you can select it in EAC to edit the properties. Then you will be presented with a field which is the Autodiscover endpoint obtained from MFG (i.e. the value I asked you all to check earlier), as shown in Figure 4. If needed, you can modify it to override the value to use another Autodiscover endpoint.
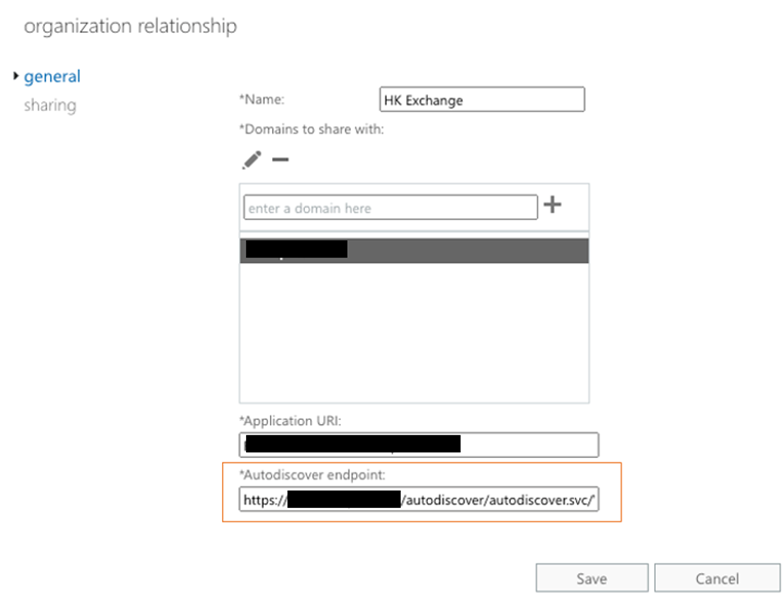
You can add as many organizations as you need. Each organization relationship has their specific domains associated, which is used by Exchange Server/Exchange Online to determine which organization relationship to use.
Shared Domain Between Environment
In terms of domains, there are instances when the same email domain is used in more than one environment. The hybrid exchange setup is an excellent example since they will be sharing the same domain. In the case of domains that are found in the home Exchange Server/Exchange Online environment, Exchange will not reach out to the other environment by querying the configurations specified in organization relationships.
By leveraging the targetAddress attribute, free/busy lookup can work across two environments that share the same email domain. If targetAddress exists on an object, the free/busy lookup will use targetAddress instead of the mail attribute during the lookup process. We will create a user or contact object, and we will add the targetAddress for routing purposes. This can redirect Exchange Server/Exchange Online to use another email address for free/busy lookup, as well as email routing. I usually set up a subdomain like hk.<email domain> or us.<email domain> for this purpose. The domain can be anything, but it must be unique across environments.
Use OWA to Test Free/Busy Sharing
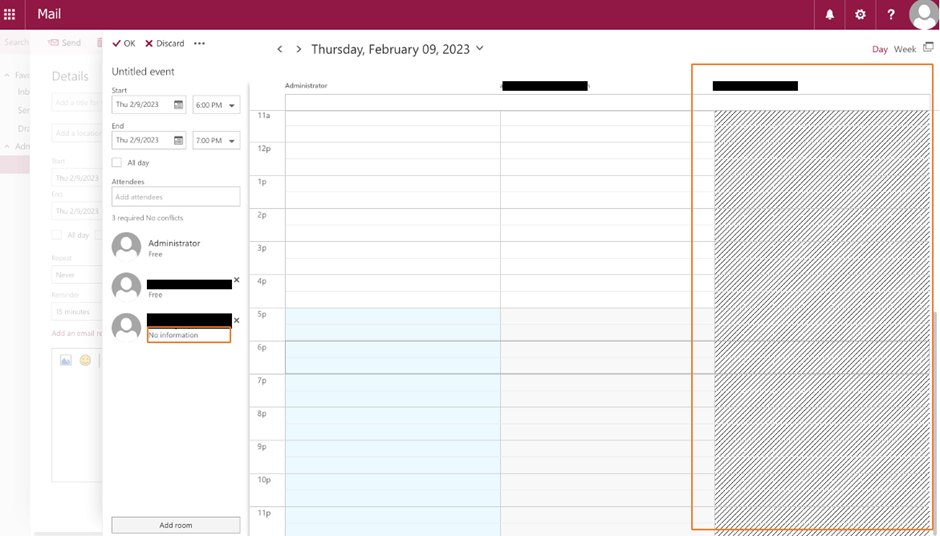
The easiest way to verify if sharing is configured correctly is to use OWA to create a new meeting and add people from the target organization. You can validate if the Scheduling Assistant can display free/busy information for those people. In Figure 5, you can see that free/busy information appears for the middle user. However, free/busy information isn’t available for the last user.
If there is an issue, you can use these troubleshooting tips:
- Test-FederationTrust -UserIdentity <OnPremisesMailbox> -verbose
Run this Exchange Server-only PowerShell cmdlet to verify if trust and connectivity between MFG and Exchange are in good shape. Adding a UserIdentity switch to test a specific mailbox ensures the token is able to query free/busy information for this specific mailbox. - https://testconnectivity.microsoft.com
This is a set of tools hosted by Microsoft. If there’s an issue with free/busy sharing with on-prem Exchange or Exchange Online, go here and perform an Outlook Connectivity Test to ensure Microsoft’s server is able to connect, as sometimes the network or firewall may be blocking the traffic. The tool also will help verify things like Autodiscover is set properly. Unless Autodiscover works, you won’t be able to connect and find free/busy data. The Test Connectivity Tool also includes a tool to query free/busy, which you can use to verify access to free/busy information on both Exchange Server or Exchange Online - Make sure the organization relationship is configured properly and that the correct domain name is specified.
Now Get (Free/) Busy!
At this point, your Exchange Server and Exchange Online can share free/busy information with each other, and you know how to troubleshoot issues. You can also start working with partners or customers to enable this to allow for better collaboration between your users and external parties.
The Experts Conference 2023 European Roadshow
Join us April 17-21, 2023, for practical security insights into hybrid AD and Microsoft 365.





Thanks for sharing the article. we have followed the steps and configured federation trust. our on-premises users can view our Office 365 users’ calendar free/busy information without any issues. However, our Office 365 users cannot see the free/busy information for on-premises users. It’s not an hybrid environment. Could you please help us to fix this issue.
Hey James…quick question.
In the Configuring Free Busy Sharing between Exchange/Microsoft 365 and Exchange/Microsoft 365, there is the option to share calendar free/busy information with a specified security group. Currently, we are syncing an on-prem mail-enabled security group with 100’s of users to our cloud tenant. That group is used as the group for free/busy sharing. Now, the company wants to share the free/busy data for 3 conference rooms that are Azure Teams-enabled rooms.
I can’t add the Azure conference rooms to the on-premise group, because they aren’t synced with our on-prem environment. The Org Sharing also only lets you define one group to use for the sharing. If I create a new Azure mail-enabled security group and add the 3 conference rooms to it, will the free/busy sharing support nesting the on-premise group inside the Azure group?
Thanks!