Understanding Security Challenges in AD Migrations
During the TEC 2022 event in Atlanta, GA I had the pleasure of attending a very instructional session conducted by Bryan Patton (CISSP) and Joe Sharmer (Systems Architect) called “Secure that Active Directory (AD) Migration.”
Joe and Bryan did an outstanding job at identifying two of the key challenges facing today’s Active Directory administrators during consolidation and divestiture projects.
- With the proliferation of hybrid Active Directory in Enterprise environments, AD migration projects have become much more complex to discover, plan and execute, meaning that IT needs to adjust strategy, choose new tools and methods, and adjust expectations for stakeholders.
- According to Trend Micro’s “Attacks from All Angles: 2021 Midyear Security Roundup” report, the banking industry reported a 1,318% year-on-year increase in ransomware attacks in the first half of 2021. AD security is critical when planning an AD consolidation or divestiture project. You don’t want your migration project to open new opportunities for attackers to exploit.
According to the experts, an M&A project is the perfect opportunity to improve an organization’s security posture by carefully reviewing and planning for each area the migration touches, such as Groups, GPOs, Accounts, and Applications. Making the right decisions before a migration starts means that the target organization will be even more secure after the migration finishes.
Takeaway Lessons
Bryan and Joe listed direct actions to take to both secure and simplify an AD consolidation or divestment project. I attempted to capture their list of best practices below:
- Don’t accept the risks of the legacy AD migration methods – Old habits are hard to break but you must evolve your migration practice to meet the challenges of the hybrid AD world.
- Avoid or limit the transfer of GPOs – Don’t assume what works in your current environment fits the target environment. Security vulnerabilities are easily introduced and exploited if policies are blindly transferred between environments.
- Avoid synchronizing passwords – Don’t open another possible entry point by bringing over hashes to avoid a simple password reset for the new accounts.
- SID History isn’t a requirement! – Remember, without SID History, the worst case is that the end-user must re-authenticate. This is a small pain to ensure that the organization is not open to possible vulnerabilities.
- Don’t migrate existing SID History – Legacy SID History should have already been cleaned up after the last migration, but if it hasn’t, then don’t transfer potential security gaps an attacker can exploit.
- Always monitor accounts using SID History – Track the accounts where you decided to transfer the last SID to ensure that no malicious behavior attacks these accounts. Each organization will have a different set of criteria to identify these accounts such as by OU, group membership, or manually through a know list. However, one possible method is to build a list using PowerShell:
Get-aduser -filter * -properties sidhistory | Where sidhistory
This will first return all users with the sidhistory property, if it exists.
Microsoft Platform Migration Planning and Consolidation
Simplify migration planning, overcome migration challenges, and finish projects faster while minimizing the costs, risks and disruptions to users.
- Always clean up SID History when the migration is complete – If you decide to migrate the last SID to the target object, remember it is a temporary solution that will not always be required, so set up a project milestone or checkpoint to plug that hole when the time comes. When you reach this milestone, you may remove the existing SID History using PowerShell. Click here for more details from Microsoft on, “How To Remove SID History With PowerShell”.
- Avoid or limit synchronizing security and distribution groups – Groups are used to authorize access. Instead of just moving a group, you may consider understanding what that group is being used for and if the current membership of that group aligns with those members that should have access to that resource. Blindly moving all groups can open an attack path as those groups may be nested in other groups that may be authorizing their members to access sensitive data and perform sensitive tasks. For more guidance around nested groups, be sure to read Using Group Nesting Strategy – AD Best Practices for Group Strategy.
- Trusts are not required for migrations – Some contemporary third-party migration tools provide options where trusts are no longer required for many aspects of the AD migration process, such as directory object synchronization utilizing SaaS-based directory synchronization technologies for disparate AD environments, or transferring SID History between AD Forests. New and temporary trusts can add attack paths for bad actors to exploit. Keep them to a minimum during migrations to avoid further exposure.
- Greenfield does not equal EASY! – Just because the new house is empty doesn’t mean you should bring over all your old stuff! Evaluate what worked in the old environment to help guide what should be included when planning the new environment’s structures and processes, while avoiding the inheritance of existing security gaps.
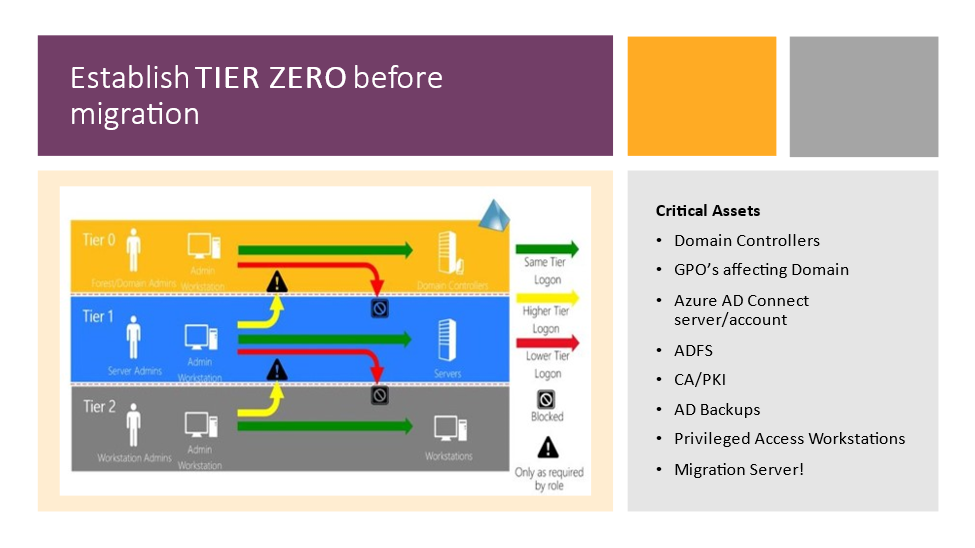
- Establish a TIER 0 group of critical assets before a migration – Create an Active Directory (AD) tier model to create security boundaries to sbit.ly/3K8zeSYhield your most critical assets before, during, and after the migration events (Figure 1). If you want to deep dive further into this subject, register for the webcast “Practical approach to secure critical assets in Active Directory and Azure” conducted by Bryan Patton and Jonas Knudsen, of SpecterOps.
- Map the relationships of your critical assets – Map every attack path using every possible misconfiguration and every relationship. Once you identify and close these choke points, you begin to eliminate the risk of downstream attack paths. There are several third-party vendors that provide solutions for Active Directory Attack Path Management that visualize, prioritize, and quantify attack path choke points.
- Update KRBTGT account password before a migration – To prevent golden ticket attacks before, during, and after migration events, it is important to regularly update your KRBTGT account password. For additional insights into this topic, check out this article from Bryan about “What is KRBTGT and why should you change the password?”.
- Refresh password policies before a migration – Similar to GPOs, password policies should be reviewed before implementing any new or updated standards in the new environment. Depending on the new environment, “passwordless” might be the best standard to adopt.
Protect Active Directory!
Active Directory is a major focus for ransomware attackers, and I believe Bryan’s and Joe’s message is spot on! As practitioners, we need to make security planning core for all M&A projects, especially those involving Active Directory.
And I will leave you with this, as Bryan said during the session, “If you aren’t changing your behavior before doing a migration, you shouldn’t expect to be more secure after the migration.”
See you at Virtual TEC 2022, December 6-7, and GO ENABLE MFA!!
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.




https://theexpertsconference.cventevents.com/event/b90218f8-46cd-4b3f-b98d-39dac24c1a06/websitePage:8c699f24-f1dc-4f41-942c-4ed5a001cb5e?refid=p365
How can I attend this session as I can’t find any registration link in this article.
The Real Person!
Author Tony Redmond acts as a real person and passed all tests against spambots. Anti-Spam by CleanTalk.
The article is a report about what happened at a TEC session, not an invitation to attend a session.