Extend Copilot Studio Agents with the Model Context Protocol the Right Way
Securing any form of AI integration is crucial before you can deploy and use AI in your organization. It’s important to understand how to use, manage, and control new AI technologies as they become available.
A relatively new standard, Model Context Protocol (MCP) arrived as a preview in Microsoft Copilot Studio a little over a month ago and became Generally Available at Build 2025. It has potential to be used in a wide variety of agent use-cases as it enables connections to external apps, AI models and diverse data sources. However, the flexibility of MCP to allow the AI model to discover and decide how to use MCP, presents a real risk in both vendor/community integrations and the possibilities unlocked with in-house integrations developers can build.
In this article, we consider how to architect secure MCP server deployments. To understand the importance of securing MCP deployments, we explore a practical example: Practical 365 IT Solutions, a managed service provider, wants to use Copilot Studio with MCP connectors to reduce the time it takes to resolve service desk tickets and improve the customer experience.
Our Example Organization: Practical 365 IT Solutions
Practical 365 IT Solutions is a Managed Services Provider based in the USA. They use Copilot Studio to automate tasks and use several different solutions to manage ongoing work.
Practical 365 IT Solutions is exploring the use of MCP to enhance its Copilot Studio integrations to improve their customer support experience. The idea is to enable service desk teams to use MCP-powered agents to find answers to client support tickets more quickly, using information from their Atlassian-based systems, their HubSpot CRM and their bespoke internal MariaDB-based service desk ticket system.
Understanding MCP
MCP is a standardized protocol that Copilot Studio agents can use to connect to external applications platforms and data sources. Think of MCP as a universal translator, enabling secure communication between Copilot Studio and diverse systems.
MCP creates a middleware-style layer designed to allow an LLM (Large Language Model) to understand how to communicate with different services, and to then perform actions against an app or data source. MCP’s protocol makes it easy to interact with different systems. Finally, the built-in authentication and authorization for sensitive data access in MCP ensures secure connections.
Typically, an MCP integration is deployed as an MCP server, which acts as the middleware, presenting an API interface that the MCP client ( Copilot Studio) connects to.
Each MCP server is defined as a specific Power Platform connector, which allows Copilot Studio to create secure ‘actions’ calling external services and APIs for tasks from data retrieval, information processing to external workflow triggering.
Planning a Secure MCP Architecture: A Fortress Mentality
For Practical 365 IT Solutions, securing MCP deployments means protecting client data and trust. They adopt a ‘fortress mentality,’ building layered defenses against threats.
Their approach starts with assessing security needs:
- What data will MCP integrations access?
- Which systems are involved?
- What are the compliance requirements?
- What are potential attack vectors?
Based on this assessment, they design a appropriate architecture aligned with Azure best practices for Copilot Studio integration. This architecture incorporates several key components to ensure a robust security posture (figure 1):
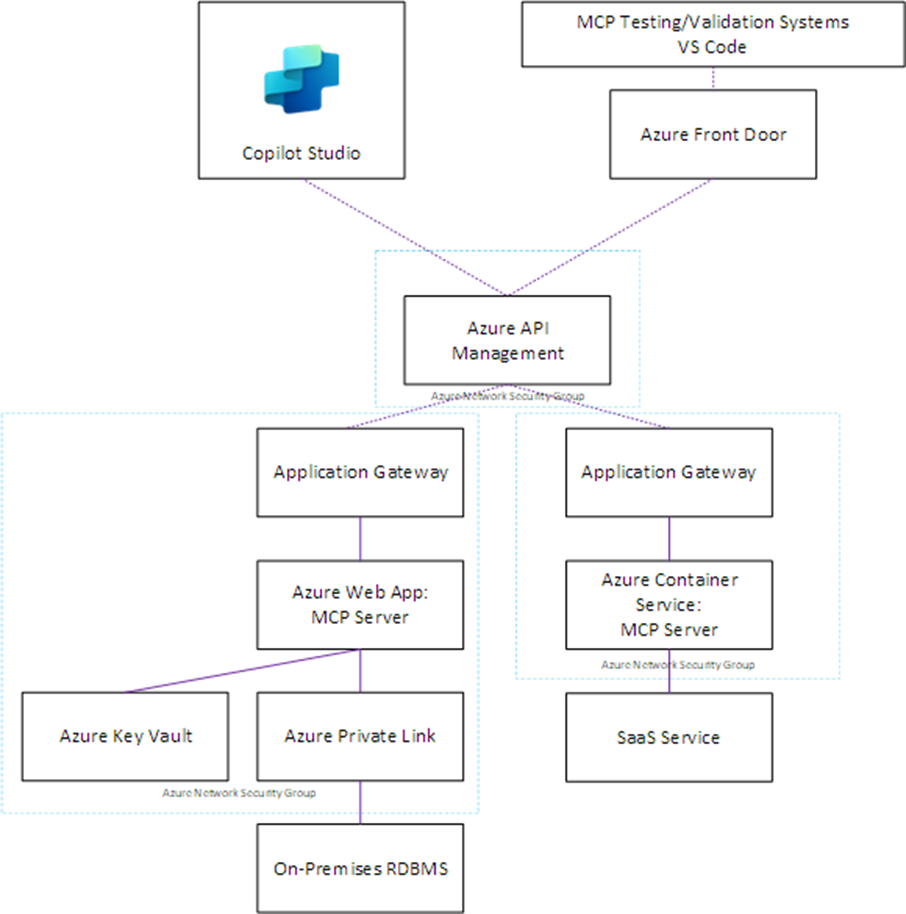
The architecture utilizes critical Azure components:
- Azure API Management: Serves as the primary entry point for Copilot Studio requests, providing IP filtering to allow only Copilot Studio networks, with additional capabilities for authorization and access controls and potential rate limiting.
- Application Gateway: Provides Layer 7 load balancing, SSL/TLS termination, and Web Application Firewall (WAF) capabilities to protect against web exploits.
- Hosting for the MCP Server: Hosted as an Azure Web App, or potentially a suitable technology such as Azure Container Services for ease of deployment.
- Azure Private Link: If the MCP server connects to an on-premises system, such as databases and production line systems, this link ensures network isolation and security.
- Azure Key Vault: Securely stores API keys, certificates, and database credentials. Requires support from the MCP server to utilize this technology, but crucial to avoid insecure techniques such as use of .env files to store credentials.
- Azure Monitor: Provides comprehensive monitoring and alerting through Application Insights and Log Analytics.
This layered approach ensures network security through:
- Network Isolation: Virtual Network integration, Network Security Groups (NSGs), and Private Endpoints.
- Access Control: Azure AD integration, Role-Based Access Control (RBAC), and Managed Identities.
- Data Protection: TLS 1.2+ enforcement and data encryption at rest and in transit.
As security is an ongoing process, these measures are a starting point, and our example organization will evolve these measures based on the types of integrations they deploy over time and the type of data and apps they intend to integrate.
Hardening the Perimeter
Securing MCP server deployment is essential to protect against threats. For our example organization, the initial architecture allows multiple MCP servers to be hosted, using a hub-and-spoke model with network-level security, WAF, and centralized API management, allowing us to utilize Application Gateway, and API Management.
As an accelerator for MCP server deployment, we can also consider Microsoft’s AI-Gateway, a comprehensive pattern for deployment of services in this way.
In our deployment, a crucial measure is to restrict MCP server access based on IP address, allowing only the IP address ranges of the Power Platform (inclusive of the connectors used in Copilot Studio), configured within Azure Firewall or Application Gateway. Its important to note that these ranges allow all Power Platform environments, regardless of tenant/organizations, so although this restricts where connections are allowed, the deployment should still be treated as if it were publicly accessible.
Data Loss Prevention (DLP): Protecting Sensitive Information
DLP protects client information like financial records, medical data, and intellectual property. Whilst the organization plans to use Copilot Studio’s MCP capabilities to enhance integration between existing systems they own, they still wish to ensure that sensitive data, such as financial data, is not transferred.
For example, if an MCP integration tries to access credit card numbers, the DLP policies (configured in the Power Platform admin center) would detect, block, and log the incident, preventing unauthorized exposure, potentially blocking requests, redacting responses, or encrypting/masking server responses. Likewise, if a user attempts to provide a Copilot Studio agent with sensitive data, for example, via a prompt, and the MCP server is, for example, being used to search the internet for results, this could present a data loss.
In our example organization though, some types of data are acceptable – for example, PII is stored by the service desk system and asking questions that make use of service desk ticket numbers, usernames and other identifiable information is crucial to the agent being able to provide useful results. Data such as financial information is not – therefore basic DLP rules that protect against this should be put in place.
Potential for MCP – Integrations for our Example Organization
By using MCP servers, Practical 365 IT Solutions enables Copilot Studio to perform actions that go above and beyond well-defined integrations from their vendors, potentially combining information from multiple systems – such as information from Microsoft 365 via Copilot Studio’s built-in capabilities – with information from multiple systems the MCP connectors provide access to.
Data enhancement gives better answers to queries, such as service desk tickets. MCP allows an agent to go further though – such as performing actions, such as updating service desk tickets with answers. The caveat of course is that it will be advisable (and most likely essential) to ensure that actions that make changes include a human in the loop, to approve, alter or deny the change.
A comprehensive list of MCP servers is maintained by the Model Context Protocol project owners (Anthropic) and allows community contributions from anyone.
As a starting place for understanding the integrations we can consider, we’ll look at several solutions listed that integrate with Practical 365 IT Solutions’ service desk team’s systems today:
- Atlassian (Confluence and Jira) to provide AI-Driven Project Background: The MCP powered Copilot Studio agent can use the MCP server to allow the service desk to quickly understand and ask questions about ongoing projects they are providing support for, based on documentation and project tasks. Using this MCP integration, they could also find the most relevant team member from the customer’s project team to help solve the issue.
- HubSpot CRM to provide deeper customer information and context: The organization uses HubSpot as its CRM, and benefits from the integration to provide deeper context and information about customers, such as upcoming potential projects and engagements and wider background information.
- MySQL/MariaDB information from their bespoke system: By choosing one of many MCP servers listed designed for MariaDB interaction and selecting one that meets requirements for use with Copilot Studio, the organization can extract additional context from their internal bespoke ticketing system based on a back-end MariaDB database. As this integration has the potential to operate over a more complex set of data, their in-house developer will need to implement the MCP server integration and assist with the configuration of the Copilot Studio agent.
Conclusion
Preparation for the use of MCP with Copilot Studio is essential and adds complexity, but by adopting a common architecture pattern the MCP servers are easier to secure and maintain.
Part of the preparation should include understanding the potential integrations that the business is likely to request, beginning with core business systems outside Microsoft 365. Assess security requirements for access to those systems both through API access and by user access – Copilot Studio is in effect both.
If you plan to use off-the-shelf MCP servers – particularly open-source community-built offerings, then consider the deployment risks of doing so and mitigate against the potential for an MCP server being susceptible to a supply-chain attack.
Plan a secure architecture based on principles that incorporating segmentation, Web Application Firewalls, API Management, and encryption, integrating security from the start. Consider Microsoft’s AI-Gateway as a starting point and reference pattern, and layer this with the DLP controls available in the Power Platform to restrict sensitive data leaving the environment.
By following guidance and typical best practices for securing API endpoints, implementing an architecture designed to secure the MCP deployment enables you to use Copilot Studio with the preview MCP integration while protecting data.




