Take the Advice
The world is full of advice, much of which is given to us ostensibly for our own good. A lot of this advice is predicated on the idea that humans will make rational choices, but it turns out that, here, in reality, people don’t often behave as perfectly rational actors. For example, some of us are still running unsupported versions of SharePoint or Exchange on-premises, despite many warnings to the contrary. One way to ensure that people don’t ignore well-meaning advice is to enforce that advice. This doesn’t always work, but it tends to work better when the advice-giver has stronger enforcement powers. You can see this principle in action with two recent changes Microsoft has made to multi-factor authentication in Microsoft 365.
Number matching
Back in September 2022, Microsoft’s Alex Weinert shared an innocent-sounding statistic. According to Microsoft’s data, about 1% of users will approve a simple MFA request on the first try, even when they didn’t expect it. For brevity, we’ll refer to these as “bad” approvals (maybe a better name would be “false positives” or something): the user’s approving an MFA prompt for an authentication request they may not have made.
That doesn’t sound too bad until you do a little math—if you have 300 users, and each one is getting one MFA request per day, that’s 3 “bad” MFA responses per day. More likely, your users are getting multiple MFA requests per day, meaning the odds go up. Since even a single bad approval can allow an attacker into your network, a 1% rate starts to sound pretty scary. Microsoft has been preparing countermeasures to reduce this statistic for a while; in November 2021, they announced two new features: number matching and authentication context. Number matching requires the user to read a two-digit code from the on-screen Microsoft 365 authentication prompt and enter it in the Authenticator app, while authentication context shows the user additional information about the authentication request, including a geolocation based on the requestor’s IP address and information about the requesting application.
Microsoft started enforcing the use of number matching on May 8, which means you may have noticed an uptick in helpdesk activity as users ask, “Hey, what’s this new thing” or “Why can’t I approve authentication prompts on my Apple Watch anymore?” While this is a welcome security improvement, it definitely falls into the enforced-good-advice category, and I suspect that the May 8th enablement caught more than a few tenant admins by surprise.
System-preferred MFA
But guess what? Microsoft’s about to do the same thing again. This time, they’re going to “encourage users to authenticate with the strongest method available to them,” but in a slightly more friendly way than the number-matching enforcement. The change, in this case, is that Microsoft 365 will start suggesting the strongest authentication method available when the user sees an MFA prompt. This changes the existing behavior, which is to let the user choose their own default in a way that should help reduce the use of less-secure authentication methods such as SMS. The feature first appeared in April 2023, but it wasn’t enabled. Now that it is enabled, here’s how it will work.
In the Entra Azure AD portal, if you go to the Security > Authentication methods > Settings blade, you’ll see a screen that looks like the one below in figure 1. The State field shows you how (or if) Microsoft will apply this policy:
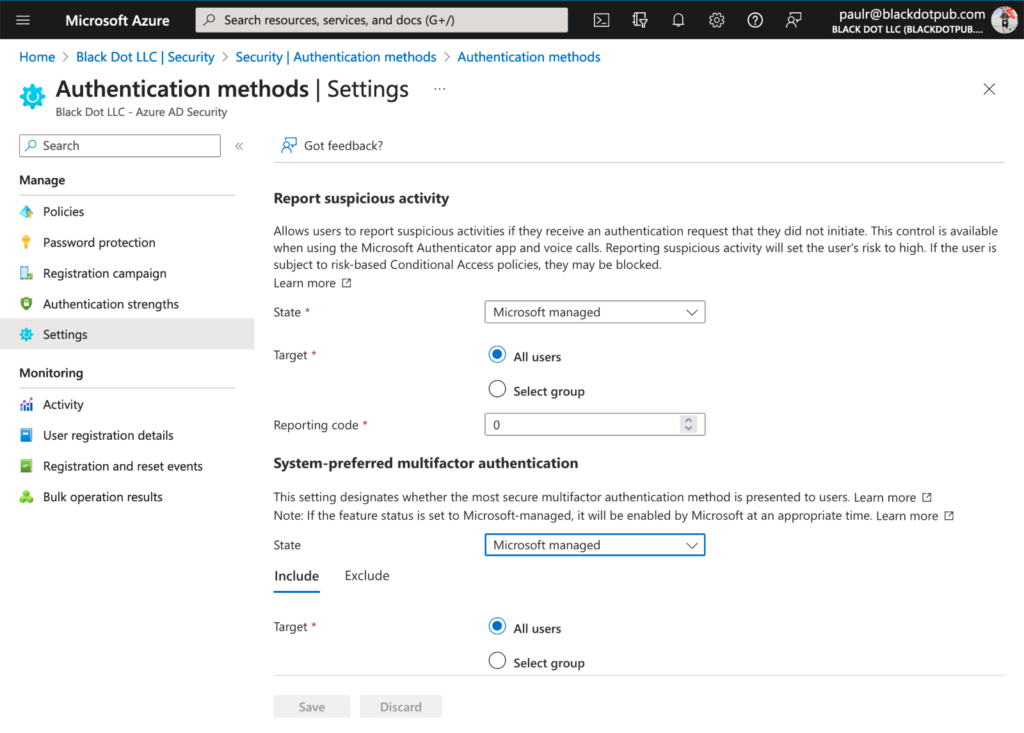
- At first, all tenants are set to “Microsoft managed (disabled).” This just means that the code that handles this setting is available to your tenant, but nothing changes.
- Over time, on a schedule Microsoft hasn’t publicly discussed, tenant settings will flip to “Microsoft managed,” as in the screenshot above (figure 1). When the state is “Microsoft managed,” Microsoft will turn on system-preferred MFA whenever they want to, but you can still disable it.
- You can set the state to “Enabled” to immediately start using this mode at any time.
- For now, you can set the state to “Disabled” to force this feature off.
At some point, Microsoft will remove the ability for individual tenant admins to set the state to “Enabled” or “Disabled.” At that point, we’ll all be “Microsoft managed” even if the UI controls are no longer present.
Ben Franklin and multi-factor authentication
I love Ben Franklin, and I think his Autobiography is worth reading to get an idea of just what a remarkable person he was. One of my favorite Franklin quotes is simple: “Hear Reason, or she’ll make you feel her.” You can either hear reason and get on board with deploying and supporting MFA for your users, or Microsoft is going to do it for you, and you may not like the rules they enforce. At the end of the day, though, broader adoption of MFA is good for Microsoft as a service provider, so don’t expect them to let up or delay on this front.



