Different Recommendations to Choose From
One of the most important requirements for organizations that wish to use Microsoft Intune is the security baseline of the device. In the UK, the National Cyber Security Centre (NCSC), is a government entity that provides recommendations to help companies gain status such as the Cyber Essentials Plus certification.
However, I was tasked recently by a client with ensuring Windows desktops are secured using benchmarks provided by the Center for Internet Security (CIS) – an independent, non-profit organization based in the United States.
Many customers ask about the differences between the guidance provided by NCSC, CIS, and Microsoft’s pre-configured security baselines for Intune. In this article, I explain the guidance from each organization, while providing a gap analysis between the baselines.
Read more from Randy Franklin Smith: Windows Laptops, Remote Work and Today’s Threat Landscape
CIS Benchmark
To begin with, the CIS Microsoft Intune for Windows 10 Release 2004 Benchmark was released on May 18, 2021. The first thought many will have, is that this latest CIS benchmark is for an OS that is now out of support as of December 14, 2021. Although many aspects of this benchmark are still relevant to later versions of Windows 10 (it was last updated in May of 2021), there have been no updates to reflect versions past 2004 or Windows 11.
It should be noted that the benchmark is a little difficult to access. The first step is to fill out a form, and after a couple of hours (in my case) you will receive an email with a list of different CIS Benchmarks. The benchmarks themselves come in PDF format, and the document for Windows 10 and Intune is over one thousand pages. Within the document there are Policy Definitions that provide IT admins options for configuring Intune to various levels of security. The options are:
- Level 1 (L1) – Corporate/Enterprise Environment (general use)
- Level 1 (L1) + BitLocker (BL)
- Level 1 (L1) + Next Generation Windows Security (NG)
- Level 1 (L1) + BitLocker (BL) + Next Generation Windows Security (NG)
- Level 2 (L2) – High Security/Sensitive Data Environment (limited functionality)
- Level 2 (L2) + BitLocker (BL)
- Level 2 (L2) + Next Generation Windows Security (NG)
- Level 2 (L2) + BitLocker (BL) + Next Generation Windows Security (NG)
- BitLocker (BL) – optional add-on for when BitLocker is deployed
- Next Generation Windows Security (NG) – optional add-on for use in the newest hardware and configuration environments
In terms of the recommendations, the benchmark is highly informative. Each recommendation typically contains the following information:
- Name
- Profile Applicability
- Description
- Rationale
- Impact
- Audit
- Remediation
- References
- CIS Controls
However, the implementation of the CIS benchmark is painful. Very painful. For the purposes of this article, I created three Microsoft 365 tenants with Office 365 E5 licenses and configured a benchmark on each tenant. Completing just Level 1 with BitLocker of the CIS benchmark took a couple of evenings to finish, so my opinion could be clouded by the fact that working with these recommendations requires a substantial time commitment.
Read more: Taking Control of Your Unmanaged PCs with Intune
CIS Policy Highlights and Lowlights
The positives of implementing the CIS Microsoft Intune for Windows 10 benchmarks:
- Extremely thorough investigation with details, providing admins with the exact reasons why to apply each listed setting.
- The Level 2 + BitLocker + Next Generation Windows Security, specifically, is a very thorough baseline. It’s intended for highly secure locations such as government facilities, or for extremely sensitive/secret departments.
The negatives of implementing the CIS Microsoft Intune for Windows 10 benchmarks are:
- It takes an exceptionally long time to implement the baseline with no importable JSON or PowerShell scripts to ease the implementation.
- You potentially run into the instance of laptops being “overprotected,” which could influence user productivity if Level 2 protection is enabled.
- By CIS’ own admission, Level 2 protection “may negatively inhibit the utility or performance of the technology and limit the ability of remote management/access.”
- The latest guidance is for Windows 10 2004, which is now out of support.
- If there are any future changes (minor or major) to the CIS benchmark, it could possibly make things more difficult to update, especially if you need to scan another 1000-page document.
NCSC Guidance
The National Cyber Security Centre supports UK organizations by being a single point of contact for security issues that affect SMEs, large organizations, and government agencies. Like the Center for Internet Security (CIS), they provide guidance for configuring Windows 10 for Intune and their Intune guide is available online.
Unlike the CIS benchmarks, you can download JSON files to import into Intune from the NCSC’s GitHub repository with import instructions found here.
The guidance on GitHub suggests that the NCSC’s guidance may be better suited to government or medium/large organizations, but I would suggest that even small businesses consider implementing these policies.
Following the same process for the CIS benchmark policies, I created another demo tenant, applied the NCSC policies, and found that the task of implementing the policies was a painless exercise. In the past, I have found that the NCSC policies caused many conflicts with other policies which resulted in failures, but this time, all the policies succeeded without the need to update anything. Figure 1 shows a summary of the NCSC policies assigned to a Windows 10 device:
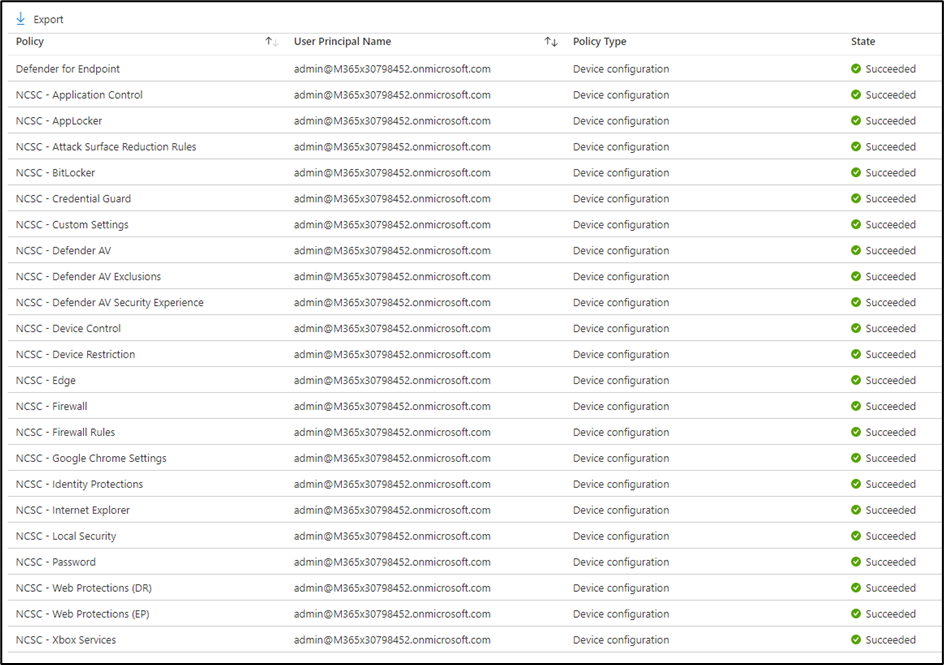
As with the CIS benchmark part of this article, the Microsoft Secure Score for Device on this tenant is a lofty 82.04%, which I think is a great score. Microsoft recommends only twenty-two additional improvement actions which would take the score to 100%, as shown in Figure 2:
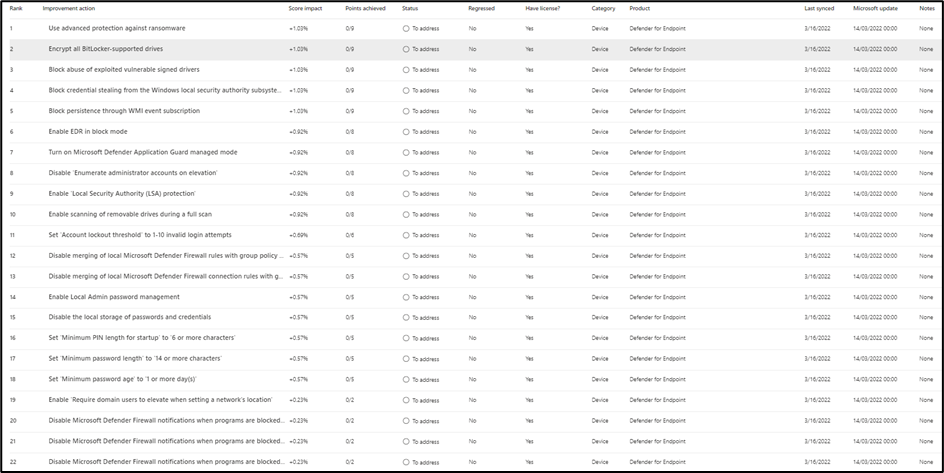
Therefore, if you are looking for a secure baseline with optimal ease of us – the NCSC policies are near to perfect. More importantly, for organizations where it’s essential to get to a near 100% Secure Score rating, the NCSC policies are a great starting point.
NCSC Policy Highlights and Lowlights
The positives of implementing the NCSC’s guidance for Windows 10:
- Relatively simple to implement; it took around 15-20 minutes to import each baseline then assign a group for distribution.
- Companies who abide by this guidance could achieve the Cyber Essentials Plus certification.
- Obtaining a high Secure Score rating for Devices
The negatives of implementing the NCSC’s guidance for Windows 10:
- As with the CIS benchmarks, the NCSC guidance was last tested on Windows 10 2004 – again, an out of support Operating System.
- The BitLocker encryption policy is 128-bit, and not 256-bit.
Microsoft Intune Security Baselines
Microsoft provides the following Security Baselines ‘out of the box‘:
- Security Baseline for Windows 10 and later.
- Microsoft Defender for Endpoint Baseline.
- Microsoft Edge Baseline.
- Windows 365 Baseline.
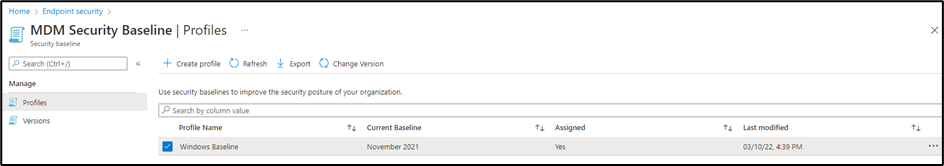
These policies are easily applied to devices by going to the Security Baselines section in Endpoint Manager (Figure 3). The best aspect of Microsoft baselines is that Microsoft regularly updates them, and those updates are easily applied to user devices. When an update is available, it’s as simple as clicking on the profile name then Change Version (Figure 3):
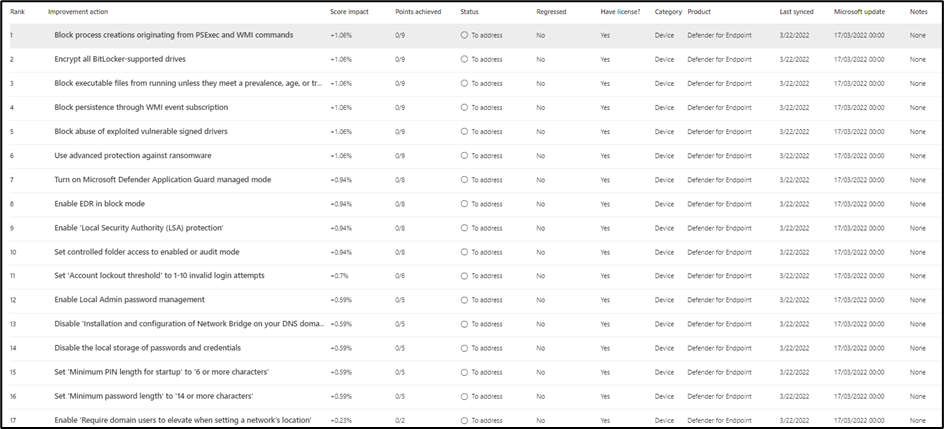
The Microsoft security baselines are also very secure with a Secure Score rating of 83.65%, with only seventeen improvement areas to address manually (Figure 4):
Microsoft Intune Security Baseline Policy Highlights and Lowlights
The positives of implementing the Microsoft Security Baseline’s guidance for Windows 10:
- Amazingly simple to implement across all devices in an organization.
- An easy update function which enables comparison of new and old baselines to give IT administrators the ability to see what will change before updating the baselines.
- A high Secure Score rating for Devices.
The negatives of implementing the Microsoft Security Baseline’s guidance:
- The BitLocker encryption policy is 128-bit and not 256-bit.
128-Bit vs 256-Bit Disk Encryption
While looking through all the baselines, it is apparent that baselines recommend 128-bit disk encryption over 256-bit encryption which has me a little surprised. In conversation with NCSC’s research team in April 2021, NCSC said that 128-bit was the recommendation based on “public and internal research.”
However, the team also said that it isn’t an issue to change to 256-bit encryption if that need exists. Personally, I prefer that any organization that I work with uses 256-bit encryption as default; but in my opinion, although 128-bit is “secure enough,” using 256-bit ensures that any future requirements with encryption are satisfied without any need for migration.
Conclusion
Implementing CIS benchmarks can be a cumbersome, time-consuming experience working with Intune. With no JSONs available to import into Intune as there are for the NCSC policies, I cannot stress how much of a difficult and laborious a task it is to implement even just level 1 of these policies. Is the CIS benchmark secure? Yes, but I highly recommend that small or medium-sized businesses without a large infosec team should look at the other two alternatives.
Both the Microsoft Security Baselines and NCSC guidelines are almost equally secure and enable device protection for users to be able to do their day-to-day jobs without an overly locked-down experience. I have had organizations that have been penetration tested using both baselines and passed. But as alluded to earlier, I recommend Microsoft Security Baselines for organizations as they have an easy upgrade path for future versions of Windows.





Being an InfoSec individual and working in IT for many years I respectfully disagree with your assessment on the CIS benchmarks. Is being ‘over protected’ a problem if your systems operational as expected? While IT is usually overwhelmed, too many times we look for the ‘easy button’ to push which just make things secure. There is something to be had digging in trying to understand each of the CIS recommendations. The one size fits all does not work with security and will usually leave an organization vulnerable. The CIS does a great job at trying to give administrators what to do, how to do and why you’re doing it explanation. Use the different approach and document what you don’t apply vs. what you applied. This put both the administrator and the organization is a much better position. The administrator knows and documents exactly why they can’t implement a security recommendation, which is then used by the organization to determine the risk to the organization. It’s not what I know what scares me it’s what I don’t know. Yes the CIS takes time and effort, you can pay for the easy button, but I always recommend that my clients take the harder path as it usually pays dividends in the end. My two cents.
Hi Michael,
Please see my updated article, https://practical365.com/revised-security-baselines-for-microsoft-365-and-intune/
At the time of writing this article the CIS guidelines were out of date and the others provided better protection- not anymore 🙂
Useful and timely article – CIS really don’t make it easy to adopt their guidelines.. we’re running the built in baselines however CIS still kicked out approx 78 fails.. now pushing to find out what the score was as I’m hoping its enough to mark as compliant and move on..
I really dont want to have to manually build out CIS policies!
Very useful article thank you. Do you know whether the new Cyber Essentials BYOD requirements can be implemented on persona devices using Endpoint Manager?
Very useful article thank you. Do you know whether the new Cyber Essentials BYOD requirements can be implemented on persona devices using Endpoint Manager?
You can now Import your GPO’s into the Intune GPO Analyser, and then Migrate them to Intune Configuration Profiles. Easy
Great article. I don’t suppose you have the exported JSON files (CIS + NCSC) once you did implement them in Intune?
Hi David, thank you! I tried and failed with the export of CIS baselines.
When they are exported, most of the values turn into “******”, which would mean going through the JSON and manually updating nearly every single line manually. I don’t think it is worth it when the Microsoft Security Baselines offer more comprehensive protection.
Thanks