It’s Time to Review Security Baselines
It’s been 18 months since I wrote about Deploying Microsoft Intune Security Baselines. In that article, I reviewed three Intune security baselines:
- Microsoft Security Baselines
- NCSC Baselines for Intune
- CIS Baselines for Intune
At the time, I concluded that Microsoft’s built-in Intune Security Baselines and NCSC Baselines are secure and easy to implement. However, the CIS Baselines are harder to implement as administrators must implement settings individually following detailed instructions published in the CIS Baselines.
Since then, the rapid growth of Artificial Intelligence (AI), particularly Copilot for Microsoft, has made CXO level more anxious about data protection and how data is secured within their Microsoft 365 environment. Having spoken to over 30 organizations in the past six months about Copilot, I have seen a significant amount of worry about the damage that a bad actor is able to carry out at a greater pace than before. Statistics from the Early Adopters Programme show that 75% of users thought it made it easier to find whatever they needed in their files. Previously bad actors from a phishing attack could take weeks or even months within an environment to collect data before a leak, this could now take days or possibly hours with the capabilities to search more intelligently across data within the Microsoft 365 tenant.
This has seen organizations analyze their security posture and ensure their environment is secure in case of an attack. In this article, I am providing my updated thoughts on the three security baselines described in my previous article including some tools to help secure Microsoft 365 tenants.
CIS Benchmarks
I am very impressed with the CIS Guidelines for Windows 11 and 10. The community that maintains the CIS guidelines has published multiple versions to keep up to date with Windows feature updates. In November 2023, they released Versions 2.0.0 for both operating systems. CIS has security baselines for other operating systems supported by Intune such as macOS, iOS, and Android, all updated by the CIS community of experts.
CIS also provides benchmarks for Microsoft 365 tenants, covering all the main areas including Entra ID, Microsoft Defender XDR, Microsoft Teams, Exchange Online, SharePoint Online, and OneDrive for Business. These benchmarks are thorough and provide industry-leading guidance for security across Microsoft 365.
To access the CIS baselines, you must join CIS Workbench. This takes you to a portal with all the benchmarks at your fingertips. After joining CIS Workbench, you can download any of the benchmarks.
Two options exist to implement the CIS baselines:
- The Free Option – This is creating a Configuration Profile in Intune and implementing each recommendation manually. Each benchmark is extensive with the CIS Benchmark for Windows 11 coming in at 1294 pages long. Therefore manual implementation could be a lengthy process.
- The Premium Option – CIS has made implementation easier for members of their SecureSuite, memberships cost range from $980 to $4,000. Access to SecureSuite gives members access to Build Kits that can be easily implemented and the CIS-CAT Pro tool which will scan your system.
In conclusion, CIS Benchmarks are incredibly strong, and, in my opinion, enterprise organizations should look to invest in SecureSuite to keep on top of security within Intune and Microsoft 365. Although the cost of SecureSuite may seem high, the following benefits should be noted when weighing up the ROI:
Reduced Configuration Time: By using Build Kits, organizations can significantly cut down on the time IT staff spend on manual configuration.
Enhanced Compliance: The CIS-CAT Pro tool automates compliance checks, making it easier to adhere to regulatory standards such as Cyber Essentials Plus.
Proactive Security Posture: Automated tools in SecureSuite allow for proactive security measures, reducing the likelihood of successful cyberattacks.
Breach Avoidance: The cost of a security breach can be substantial, not only in terms of monetary loss but also in reputational damage.
NCSC & Intune Baselines
I am quite disappointed with both NCSC & Intune baselines as no updates have taken place since my last article. NCSC has not updated their repository for Intune for over two years, and Microsoft’s security baselines haven’t been updated since November 2021.
Microsoft plans to revamp the security baselines for Intune in early 2024, but what this will look like, I am unsure.
Cybersecurity and Infrastructure Security Agency
Since March 2023, I have worked closely with CISA (Cybersecurity and Infrastructure Security Agency)’s Microsoft 365 Baselines, which covers the same areas as CIS for Microsoft 365 – Entra ID, Microsoft Defender XDR, Exchange Online, Microsoft Teams, SharePoint, and OneDrive for Business. Unfortunately, there is no guidance for Windows 10 or 11, but what I love about the CISA baselines is that they are updated and CISA provides a free reporting tool called ScubaGear which can generate a report on a Microsoft 365 tenant, including identifying gaps that might exist in the environment.
Within an hour of setup time, organizations can get a complete report of the Microsoft 365 tenant (Figure 1):
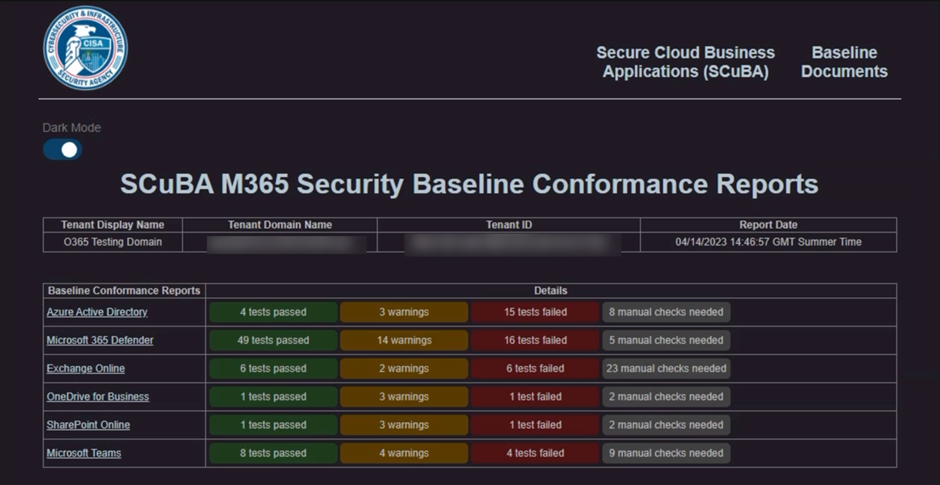
The report gives a breakdown of each area in a Red/Amber/Green/Grey format which is broken down into 3 categories:
- Shall – This is a security setting that must be implemented, if not it will Fail and in turn, a red mark will appear on the report.
- Should – This is a security setting that is recommended but not mandatory, if it is not implemented, it will result in a warning and a yellow mark on the report.
- N/A – This is a security setting that may need to be done manually by checking the Details in the report and cross-referenced with the baselines here.
For reference, a Microsoft Defender report looks like the following (figure 2):
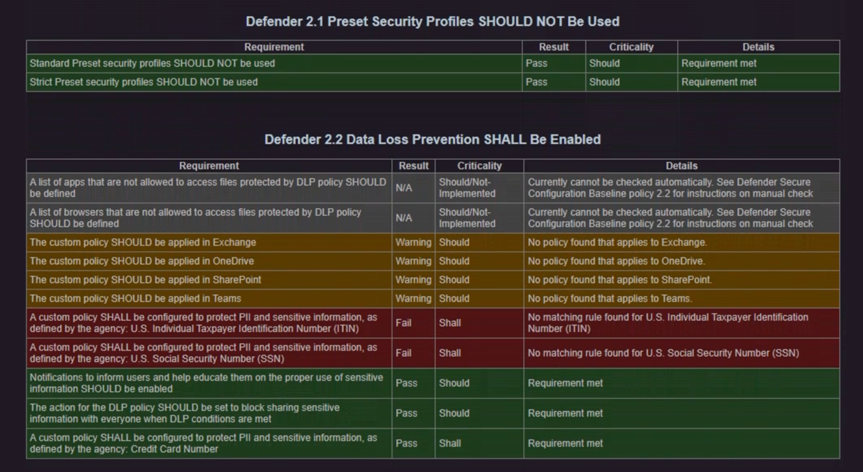
Although CISA generates a fantastic report, there is no automated way to import the Microsoft 365 baselines via PowerShell scripts. Instead, CISA provides a step-by-step guide on how to implement each setting in the baseline. Although this is a manual task, it is not as complicated as the CIS guidelines, as there is a lot of guidance on how to implement it.
Open Intune Baseline
Community tools are a great resource. James Robinson maintains a GitHub repository called the Open Intune Baseline. James has taken the following baselines into account and amalgamated them into one Intune baseline:
- NCSC Device Security Guidance
- CIS Windows Benchmarks
- ACSC Essential Eight
- Intune Security Baselines for Windows, Edge & Defender for Endpoint
- Microsoft Best Practice
James exported the settings into JSONs (available in the repository) which can easily be imported into Intune by using Mikael Karlsson’s IntuneManagement tool.
In my opinion, the OpenIntuneBaseline offers a perfect blend of security settings across the Intune stack. The guidance has been created for Entra ID Joined (Azure AD Joined) devices and not Hybrid Entra ID Joined devices, which alligns with Microsoft’s best practices.
Comparison
Table 1 compares the Microsoft 365 and Intune Security Baselines:
| Baseline Name | Covers M365 | Covers Intune | Security Rating | Ease of implementation |
| CIS | Yes | Yes | 10/10 | 3/10 (Manual Implementation) 9/10 (SecureSuite Member) |
| Microsoft Intune Security Baselines | No | Yes | 6/10 | 10/10 |
| NCSC | Yes | Yes | 6/10 | 9/10 |
| CISA | Yes | No | 10/10 | 6/10 |
| OpenIntuneBaseline | No | Yes | 10/10 | 9/10 |
I gave 10/10s Security Ratings for CIS, CISA, and the OpenIntuneBaseline because they include the best security configuration and are consistently updated. NCSC and Microsoft’s score have not updated the baselines with new versions of Windows. I therefore give a score of 6/10
I give 9/10s for OpenIntuneBaseline/NCSC because of the need to know a little bit of PowerShell to implement with Microsoft’s Intune Baseline 10/10 for the ease of implementation via the Intune Management Console.
The CISA guidelines come in at a 6/10 because of the manual implementation process. This could be time-consuming but the documentation is a lot easier to follow than CIS’ PDF. CIS is split into two 3/10 for manual implementation and 9/10 for the tools available to SecureSuite members. These baselines and tools need good Intune skills to implement.
What Should Your Organization Use?
My conclusion is to avoid NCSC and Microsoft’s Intune Baselines until they have been updated. My recommendation for security baselines depends on your circumstances. If I were a CTO of an organization, I would sign the organization up to join CIS SecureSuite and implement their baselines, because they are secure, updated regularly, and are known globally as the go-to for cybersecurity frameworks.
However, not everybody can access or afford SecureSuite. In these circumstances, a combination of CISA’s baselines and OpenIntuneBaseline is the right way to secure your organization’s environment.





Where do i put the Security baseline for Microsoft Entra hybrid joined ?
We’re in the position of migrating to Windows 11 and I’d like to get off on a good foot. I like the relative simplicity of the NSCS baselines but I don’t think I have time to wait for their update. Does anyone know how straight forward it would be to update the baseline as and when they do release new recommendations?
Thanks for the write up, important topic
Great article. Do you have a view on which benchmark from cis to apply where the windows device is hybrid entra joined and enrolled into intune. Preference is to configure settings with intune. There is variation between the intune benchmarks and the benchmark for dom joined devices. The intune kit is aimed towards entra joined. Considering whether the policies that aren’t maped in the intune build kit should be created manually.
This person is implementing both the Intune and AD GPO benchmarks in a hybrid scenario. Anyone have any thoughts or pros/cons in doing this: https://www.reddit.com/r/Intune/comments/1ce1dt0/best_method_to_harden_win10_gpos_for_cis_l1_for/