Modern Authentication for Pure Exchange On-Premises Organizations Running Exchange 2019 and Exchange 2016
In December 2017, Microsoft announced Hybrid Modern Authentication for Exchange On-Premises, a method to allow Exchange Servers to accept OAuth tokens issued by Azure AD to authenticate user connections. It was the first step to move Exchange Server away from basic authentication and leveraged the hybrid connection between Exchange Server and Azure AD (how hybrid MFA works for Exchange). However, as the name implies, the solution only works for hybrid organizations.
Five and a half years later, and fresh from the long-running but successful project to eradicate basic authentication from Exchange Online, Microsoft is turning its attention to bringing modern authentication to non-hybrid (or “pure”) Exchange Server organizations. This functionality is available in Exchange 2019 CU13, aka the 2023 H1 cumulative update for Exchange 2019, released on May 3, 2023.
Many have criticized Microsoft for not moving to enable modern authentication for on-premises servers sooner. Although it’s fair to ask why Microsoft did not put the necessary wheels into motion before now, it’s probably because of the declining size of the non-hybrid Exchange installed base. Many organizations have Exchange Server, but most run in hybrid mode and can take advantage of hybrid modern authentication (HMA). In fact, Microsoft is careful to point out that because HMA uses Azure AD, it is a better solution than the ADFS mechanism that they’re making available to non-hybrid Exchange Server organizations.
Modern authentication is available to organizations with Exchange 2019 and Exchange 2016 servers but doesn’t work when Exchange 2013 servers are present. The logic for Microsoft’s stance is simple: Organizations must install updates to enable modern authentication. Exchange 2013 exited support on 11 April 2023. Microsoft doesn’t create new functionality for software once it passes its end-of-support date. The same applies to earlier versions.
Making Modern Authentication Work for Exchange Server
The new solution has several prerequisites for different components:
- Updates to Exchange Server. You’ll need to deploy Exchange 2019 CU13 on all client access (aka front end) servers. Exchange 2016 does not support modern authentication. The proxied connection from the Exchange 2019 client access server uses Kerberos.
- An update for the schema of the Exchange Server organization (run /PrepareAD). The upgrade adds new parameters for the authentication policy cmdlets (see below) used to control which mailboxes use modern authentication.
- ADFS 2019 performs token issuing and authentication for Exchange Server on-premises accounts (by comparison, Azure AD fulfills this role for cloud accounts). The ADFS server requires suitable certificates to secure traffic between clients and servers and must be configured to support modern authentication.
- Only the latest subscription version of the Outlook for Windows client (version 16327.20200 or later) supports modern authentication with Exchange Server. Clients need software updates to allow them to fetch tokens from ADFS rather than Azure AD. Microsoft says that they will make the necessary update for volume-licensed versions of Outlook by the end of June 2023. Updates for Outlook for Mac, the Outlook mobile apps, and other clients “will be added later.” (Be sure to check that any Outlook add-ins you use can handle modern authentication).
- The PC must run Windows 11 with the 22H2 update and the KB5023706 security update. In addition, some registry changes are needed on client workstations.
- The organization must deploy suitable authentication policies to define the set of users allowed to use modern authentication (see below).
For more information, read Microsoft’s documentation.
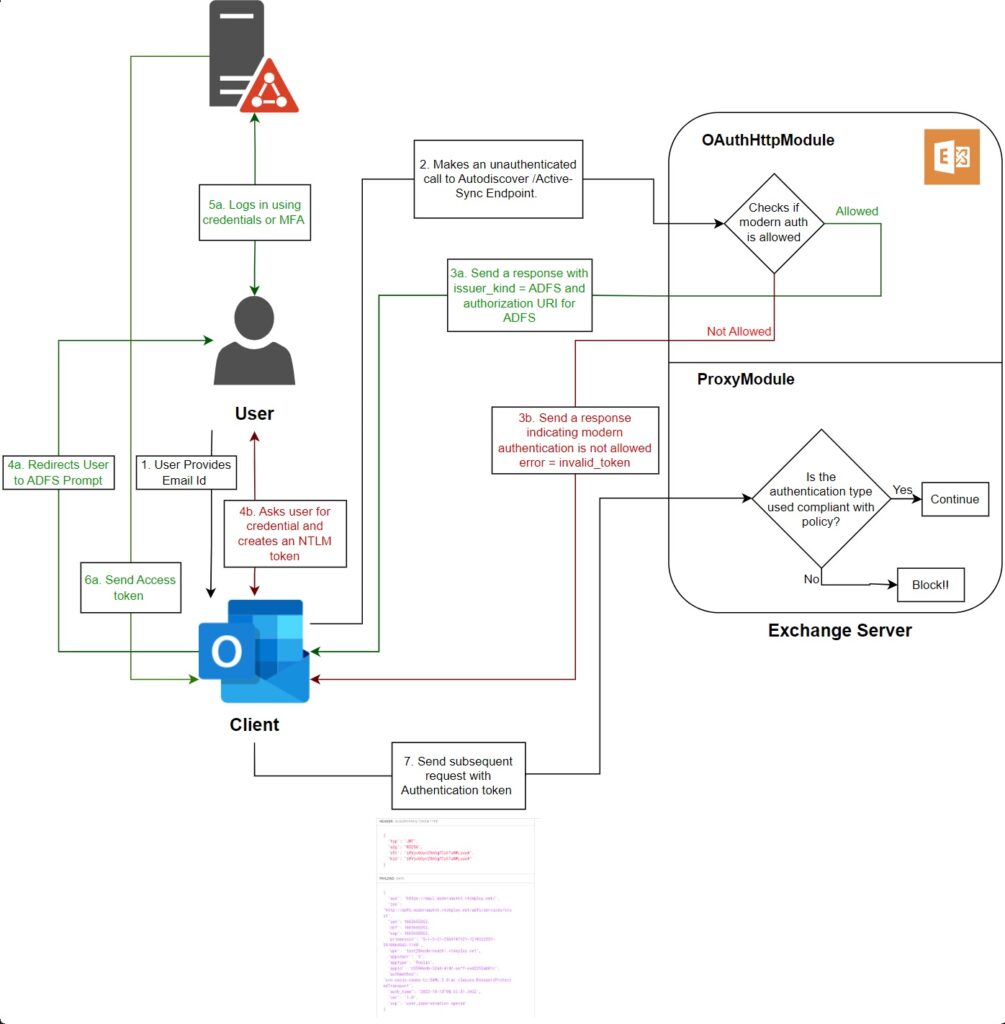
The authentication flow (Figure 1) is as follows:
- The user starts Outlook and enters their email address.
- Outlook uses Autodiscover to check if the server supports modern authentication. If yes, Exchange responds with the URI to allow Outlook to contact ADFS.
- Outlook interacts with ADFS to sign in with the user credentials (including MFA if required).
- ADFS generates an access token.
- Outlook uses the access token to connect to Exchange Server.
- Exchange checks if the authentication policy assigned to the user permits modern authentication. If yes, Outlook opens their mailbox.
Policies to Block and Allow Modern Authentication
Exchange Server uses authentication policies to determine which user accounts can use modern authentication. The installation of Exchange 2019 CU13 updates any pre-existing authentication policies to block modern authentication for all accounts. This is a deliberate step to make sure that everything works as before. New policy parameters are available to control modern authentication for each connection protocol available to clients (like POP3, IMAP4, ActiveSync, Exchange Web Services, and so on).
Authentication policies are managed with PowerShell. To create a new authentication policy to block modern authentication for all protocols, run the New-AuthenticationPolicy cmdlet and specify the block parameter for each protocol:
New-AuthenticationPolicy -Name "Complete Modern Authentication Block" -BlockModernAuthWebServices -BlockModernAuthActiveSync -BlockModernAuthAutodiscover -BlockModernAuthImap -BlockModernAuthMapi -BlockModernAuthOfflineAddressBook -BlockModernAuthPop -BlockModernAuthRpc
To make the new authentication policy the default for the organization, use the Set-OrganizationConfig cmdlet to update the organization configuration with the name of the policy:
Set-OrganizationConfig -DefaultAuthenticationPolicy " Complete Modern Authentication Block"
After configuring ADFS to issue tokens and are ready for users to test the new functionality, you can create or amend a policy to allow modern authentication and assign it to user accounts that satisfy the prerequisites. For instance, this policy blocks modern authentication for IMAP4, POP3, ActiveSync, and RPC while allowing modern authentication for the other protocols:
New-AuthenticationPolicy -Name "Allow Modern Authentication Outlook” -BlockModernAuthActiveSync -BlockModernAuthImap -BlockModernAuthPop -BlockModernAuthRpc
You can then assign the new authentication policy to the user’s account with the Set-User cmdlet:
Set-User -Identity Jane.Doe -AuthenticationPolicy "Allow Modern Authentication Outlook”
If you enable modern authentication for an account and the user then attempts to use an unsupported client, it’s likely that the client will be unable to authenticate and connect to Exchange Server because it won’t include the code to detect a failure with modern authentication leading to a fallback to basic authentication.
In the future, Microsoft could make modern authentication the default and begin the process of removing basic authentication from on-premises servers, just like what happened for Exchange Online. Reaching this stage requires updates for many different clients, so it won’t happen overnight.
No Silver Bullet
Any change that improves security is welcome. Eliminating basic authentication is helpful, but it’s not a silver bullet that will improve the overall security stance for Exchange on-premises servers. Instead, it’s a good update that rewards those who run the latest version of Exchange Server in pure on-premises organizations.
The organizations I worry about are those running old, unpatched, and vulnerable servers. The advent of modern authentication for Exchange Server will do nothing for these organizations. Perhaps the soon-to-be-implemented plan to block inbound mail traffic from obsolete Exchange servers will deliver the necessary push to do better.
The Microsoft 365 Kill Chain and Attack Path Management
An effective cybersecurity strategy requires a clear and comprehensive understanding of how attacks unfold. Read this whitepaper to get the expert insight you need to defend your organization!




They changed their article. The volume license version of Outlook 2021 now says unsupported. Classic Microsoft.
That’s the nature of software development now… Constant change.
Thanks Tony for this article. I support many companies with email support. All these companies [note ALL not some] have a Hybrid model and use the full Office365 Outlook version installed on Windows 10 and 11 machines. So getting all this going is not in the hands of only the Exchange serve admin it seems, but several IT teams would be involved here. A pity that MS made modern auth on-prem so complex.
What happens with OWA and EWS, can you integrate Modern Authentication?
As the article says, the only client supported by modern authentication is Outlook for Windows. Microsoft is working to support other clients using the method described here. Their announcement also says that OWA supports “claims-based authentication with ADFS, which is a form of modern authentication.”
Würden die Produkte etwas beheben und nicht immer leiden verursachen dann wurde man alles recht schnell patschen.
Jedesmal die Bange frage läuft noch alles und kann jeder noch einsteigen!
The need for windows 11 and a subscription version of office does not align with organizations running on prem exchange.
Historically, Exchange Server on-premises customers have not been terrific at upgrading servers or clients. If Microsoft said that they would provide a patch for (say) Outlook 2016, would customers upgrade? By using the subscription version, the patch is in the mainline builds and customers who use the subscription model will get it automatically. But the subscription version of Outlook is only the first client. Microsoft has already committed to delivering an update for the LTSC version and other platforms (Mac, mobile). As to Windows 11, I guess they want to move people to the latest desktop OS. I think they should have supported Windows 10 too, but I don’t get to vote.