Handling inactive devices is a tougher challenge than you might expect. As I previously explained, there is no public method to remove devices from Microsoft Defender for Endpoint (MDE). This can cause several issues:
- Secure score results seem incorrect.
- The number of devices isn’t correct.
- Inventory is cluttered with old devices.
Over the last year, Microsoft released several features to make the management of inactive devices easier. I recommend reading my original article on this topic before continuing here, as it covers some important aspects that this article builds upon.
In summary, these are the main topics to remember:
- Each device has a state (active vs inactive). A device becomes inactive after 7 days of inactivity (meaning the device isn’t connected to Defender).
- Offboarding a device doesn’t remove it from the inventory immediately, it just stops new data from coming into Defender XDR. Defender only removes a device after the configured retention period has run out. More details on retention periods can be found in the previous article.
- My tip for handling inactive devices is to tag a device as ‘Offboarded’ (either manually or automatically) and use device groups to filter them from the inventory and dashboards.
Transient Devices
Defender’s device discovery feature automatically looks for non-onboarded devices on a corporate network and adds them to the device inventory.
Microsoft released the transient devices feature in May 2024. This is an automated process to tag devices that have not appeared on the network for a long time, meaning there was not enough time to do an adequate scan. The intention is to avoid inventory clutter if a device hasn’t been seen long enough to execute an adequate discovery that would gather all required details of a device.
The transient devices feature is enabled by default and there is no way to turn it off. If you visit the device inventory page in the Microsoft Defender XDR portal, you will see that a filter is enabled automatically to filter out transient devices (Figure 1).
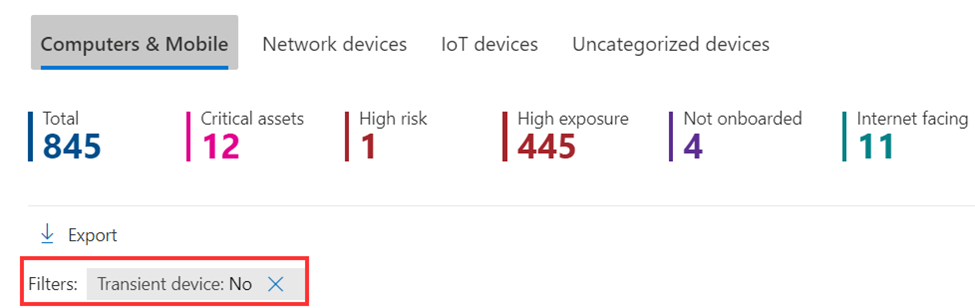
It is important to note that the transient devices feature doesn’t take any action on servers. I have seen cases where Defender tags a device as transient when it was a corporate asset.
The transient device feature helps administrators maintain a cleaner device overview by removing some clutter. However, I advise you to tread carefully and validate all transient devices to ensure you don’t filter out any useful devices. This can be done by checking all transient devices and verifying that there are no company assets included.
Excluding Devices
In April 2024, Microsoft released the ability to exclude devices. To exclude a device, navigate to a device page (security.microsoft.com > devices > select a device), click the ellipsis menu on the top right, and choose ‘Exclude’ (Figure 2).
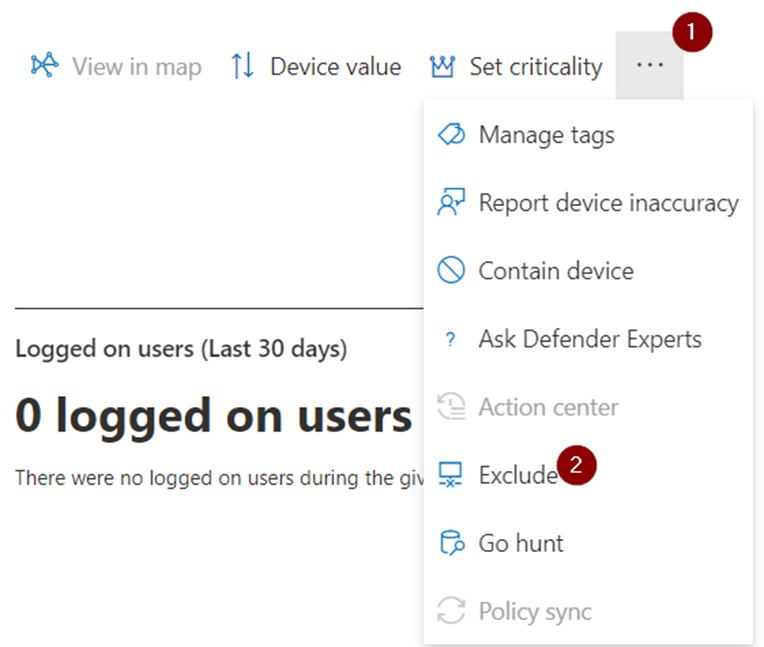
Excluded devices are removed from vulnerability management, meaning that you won’t see any of the installed software and affecting vulnerabilities in the overview, nor will it count towards your exposure score.
You can exclude both active and inactive devices. If you try to exclude an active device, Defender displays a pop-up warning that this is unsupported.
It’s easy to create a view of excluded devices by applying a filter to the device inventory. By default, the filter ‘not excluded’ is enabled (figure 3).
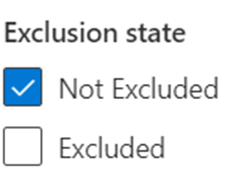
I see some organizations using this feature to ‘hide’ their legacy environment and artificially increase their exposure score. These organizations are lying to themselves. Just because a major vulnerability is excluded doesn’t mean it doesn’t exist. An attacker will always try to find the weakest link and it is important to identify any weak links.
I typically don’t recommend excluding a device that is active because the vulnerabilities on it are still accurate. Of course, scenarios exist where it is impossible to update a certain machine due to organizational restrictions. In that case, I recommend that you create an exception for a specific recommendation. Adding an exception means the recommendation is removed from the list; it enables you to focus on what is important. The main added value is that an exception can be scoped to a specific piece of software or vulnerability and doesn’t exclude the entire device.
The only time to exclude a device is if you remove a device from your network and want to immediately remove all associated software and vulnerabilities, instead of waiting for the device to become inactive.
Your Process to Handle Inactive Devices
The two new features help organizations to build a process to handle inactive devices. They add more context and provide additional functionality, but they don’t solve the issue of handling inactive devices. Handling inactive devices is still a time-intensive problem and there is no solution that works for everyone.
Many companies don’t bother with building out such processes. As I mentioned in the original article, a device is automatically hidden from Defender Vulnerability Management after 30 days.
If you like to keep a clean inventory, I recommend trying to use a combination of tags and device groups to filter out old devices. Every organization has a device offboarding procedure. Usually, this includes actions such as: wiping the device, disabling it in Active Directory or Entra ID, and updating the status in asset management. A fourth step would be to add a device tag called ‘Offboarded.’ Afterward, you can create a device group based on that tag and easily filter out all offboarded devices.
You can also automate this task and add the tag using PowerShell or other scripting languages like Python. To do so, you need to use the machine API within Microsoft Defender for Endpoint. For a full example of using the MDE API using Powershell, there is a great learn article available.
Keeping Track of Health Issues
As I mentioned in my earlier article, a big difference exists between a device that is offboarded and a device that has connectivity issues. The first scenario doesn’t have any impact, while the latter can mean an attacker has been able to sever the connection between the machine and Defender. It is important to keep track of the health state and identify any potential issues. A possible solution could be to run a script to verify if a device is inactive in Defender while it is active in the asset management tooling or to create an alert if a new device becomes inactive.
Keeping track of endpoints is difficult as you are not always sure if the user is working or might be on holiday. That is why I typically limit this process to servers.
Finding What Works for You
There is no ‘ideal’ way to handle inactive devices within Microsoft Defender for Endpoint. While I wish Microsoft would deliver better granularity for handling inactive devices, I understand their reluctance because every capability can be abused by an attacker. It is important to identify a method that works for you. It could be that you do not need to manage a clean-up process and are fine with keeping the overview as is, or you could try a manual or automated process as discussed here.





Completely useless functionality. I’ve lost Server 2019 servers that I turn on once a month to perform maintenance like change our Citrix master image for example. Regardless of the transient device filter setting, these servers will not show up anywhere anymore.
Some nice practical advice in this article, thanks very much.