Serialization Payload Signing Contributes to Server Security
The January 2023 Security Update for Exchange contains a new feature called ‘certificate-based signing of PowerShell serialization payloads’ (1). Signing of serialization payloads in PowerShell is an important security feature, but most Exchange admins don’t know what PowerShell serialization is, let alone what signing of a serialization payload is. In this article, I discuss PowerShell serialization, what PowerShell serialization payload signing is, why this is important, and how to manage it.
PowerShell Serialization
PowerShell is an object-oriented scripting language. This means that PowerShell uses objects to transfer data and that these objects have attributes and methods. For example, a mailbox has attributes like DisplayName, PrimarySmtpAddress, ShowInAddressBook, etc. When PowerShell retrieves details for a mailbox from an Exchange server, the output is treated as an object. Sometimes these objects need to be exchanged. For instance, between PowerShell sessions or from a PowerShell session to a database or file using the Export-CliXML or ConvertTo-JSON commands.
The best-known way to transfer objects in PowerShell is through pipelines via the pipe operator “|”. An example of using a pipeline is a command like:
Get-Mailbox -Identity D.Jones | Set-Mailbox -DisplayName "Don Jones II"
The mailbox object is transferred from the Get-Mailbox cmdlet to the Set-Mailbox cmdlet.
To transfer objects, PowerShell uses a process called serialization. Serialization converts the state of an object into a stream of bytes. This stream of bytes can be transferred to memory, a database, or a file. PowerShell uses serialization to pass objects between sessions. To reconstruct this stream of bytes back to an object, a process called deserialization is used.
A visible example of serialization is when exporting an object to a disk as an XML file. When exporting a mailbox to an XML file, PowerShell serializes the properties of the mailbox object and writes the serialization data into the XML file. Here’s an example of exporting a mailbox to an XML file:
Get-Mailbox -Identity D.Jones | Export-CliXML -Path C:\Scripts\MBX-DonJones.xml
If you open the XML file, you see details of the mailbox properties. If you zoom in, you see more information and several XML nodes ‘SerializationData’. This is the converted data from the mailbox object shown in Figure 1.
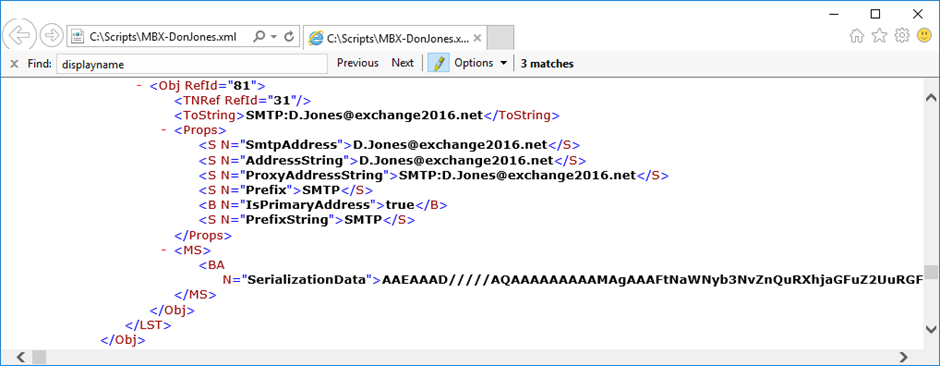
Please note that in the entire file, there are multiple sections containing serialization data.
When importing the XML file, the properties are read and the serialization data is used to recreate the complete object, the mailbox in this example. Be aware, it’s only the object and its properties, not the mailbox contents.
Serialization also occurs when requesting an object from the server. A client with a remote PowerShell session (which can be on the Exchange server itself) requests the deserialization of an object. The server requests what object needs to be deserialized and the client answers with the object type, followed by the server returning the requested information. This is shown in Figure 2.
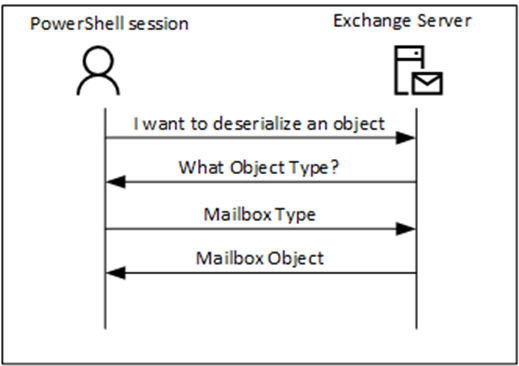
In a regular PowerShell session, this mechanism works fine, but instead of a regular admin or process, a malicious user can also try to retrieve information. In Figure 2, when a malicious user returns some random information after the server requests the object type it is unknown what happens. This is what hackers do by returning some random information and seeing if they can get into an elevation of privileges or remote code execution on the server side. In late 2022, there was a vulnerability in the Exchange Server that led to Remote Code Execution after a malicious user responded to a request with a payload designed to allow them to access the server. Microsoft fixed this security vulnerability (CVE-2022-41082) in the September 2022 Security Updates for Exchange server and followed up with a further fix for the root cause in the January 2023 Security Updates for Exchange server. This is what ‘serialization payload signing’ does.
Serialization Payload Signing
When serialization payload signing is implemented, the serialization string is signed with the private key of a certificate on the Exchange server (see below). The client can use the public key of the server’s certificate to validate the signature of the serialization string.
This is how it works:
- The server serializes the data for exchange or export.
- The server creates a cryptographic hash of the data. Common hash functions in PowerShell are SHA-256 or SHA-512. The output of the hash is a fixed-size string.
- The hash generated in step 2 is signed with the private key of the certificate on the Exchange server.
- The signature generated in step 3 is attached to the serialization string and the data is exchanged.
- When the data is received, the steps are performed in reverse order.
- The serialization string is used to recreate the object, and the signature is verified using the public key of the server’s certificate. When successful, the client has verified that the data that was exchanged was not tampered with.
The certificate that is used by the Exchange server is the Exchange organization’s authentication certificate. This is a self-signed certificate created during the installation of the first Exchange server. It is stored in Active Directory and has a lifetime of five years. Since it is stored in Active Directory, all Exchange servers in the organization have the same authentication certificate.
Serialization payload signing is enabled by default when the November 2023 Security Update for Exchange server is installed on a per-server basis. It is also installed by the January 2023 Security Update but disabled by default. Unless you are running Exchange 2019 CU14 with the November 2023 Security Update you must manually enable serialization payload signing.
The first step is to check the Exchange authentication certificate on the Exchange servers. Microsoft has created the MonitorExchangeAuthCertificate.ps1 script to do this, and this script can be downloaded from the Microsoft Github. A successful run of the script is shown in Figure 3.
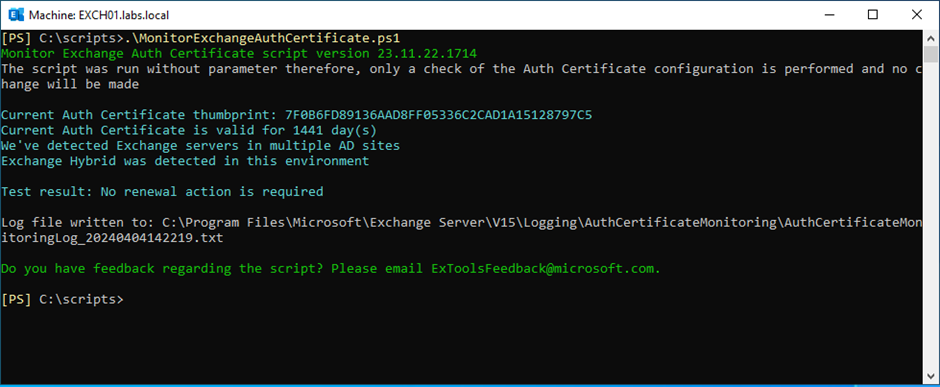
When running Exchange 2019 or Exchange 2016, serialization payload signing can be enabled centrally by creating a new setting override. Use the following command in Exchange Management Shell to create a new setting:
New-SettingOverride -Name "EnableSerializationSigning" -Component Data -Section EnableSerializationDataSigning -Parameters @("Enabled=true") -Reason "Enabling Signing Verification"
This command needs to be run on only one Exchange server. Afterward, Active Directory stores the setting override and shares it with all Exchange servers in the organization.
The next step is to refresh the Exchange server VariantConfiguration component by running the following command:
Get-ExchangeDiagnosticInfo -Process Microsoft.Exchange.Directory.TopologyService -Component VariantConfiguration -Argument Refresh
The last step is to restart the WordWideWeb publishing service and the Windows process activation service on the Exchange server where the setting override was created. Use the following command to do this:
Restart-Service -Name W3SVC, WAS -Force
Because serialization enablement for Exchange 2013 is controlled through a system registry key, enabling serialization for Exchange 2013 is a manual process. To create the registry key, run the following command on every Exchange 2013 server:
New-ItemProperty -Path HKLM:\SOFTWARE\Microsoft\ExchangeServer\v15\Diagnostics -Name "EnableSerializationDataSigning" -Value 1 -Type String
Make sure the implementation is consistent across all Exchange servers in the organization. Failure to do so can lead to a PowerShell error message like:
Deserialization fails due to one SerializationException: System.Runtime.Serialization.SerializationException: The input stream is not a valid binary format.
If you run an older Security Update on your Exchange server, enabling the serialization payload signing feature can lead to some known issues, like the Get-ExchangeCertificate command not returning certificate details, or the Queue viewer not working correctly. More information can be found in this Microsoft article. But instead of trying to work around these issues, of course, it is a better solution to bring your Exchange environment up-to-date with the latest security updates.
Summary
Certificate signing of PowerShell serialization payload in Exchange Server is a security feature introduced in the January 2023 Security Update and enabled by default in the November 2023 Security Update. Enabling this feature prevents tampering with data exchanged in PowerShell sessions, a security breach that was disclosed in September 2022 that could result in a Remote Code Execution.
If you are not running the November 2023 or later Security Update, make sure that you enable this feature manually on all Exchange servers in your organization.



