In my Office 365 security course at Pluralsight I’ve included a module on Windows Defender Advanced Threat Protection. Windows Defender ATP is built in to Windows 10 build 1607 and later. Right now it’s in the Professional, Enterprise, and Education SKUs, but to use it you need specific licensing (see this page for current information).
There is also support for Windows Server and down-level versions of Windows, and support for non-Windows devices. Those are in various stages of “preview” and “coming soon”, so for the sake of this article I’m only going to use Windows 10 in my demonstrations.
The Role of Windows Defender ATP
Windows Defender ATP is not an antivirus product. Malware prevention is not the role of Windows Defender ATP. That role is fulfilled by Windows Defender or a third party anti-malware product.
Windows Defender ATP is a post-breach investigation tool. Windows Defender ATP performs behavioural analysis of code or programs that run on a machine to look for suspicious behavior. What we’re assuming here is that a breach can and will occur, which is the correct position to take. No security solution is perfect, and if a threat has made it past other lines of defence, you need something that can alert you to the breach so that you can begin to investigate.
So Windows Defender ATP is there to tell you that a breach has occurred, then provide you with the information you need to work out
- how the threat got in
- what the threat is, based on behavioral analysis and other signals
- where the threat is going, on the machine or further into your network
Windows Defender ATP Architecture
One of the advantages of Windows Defender ATP is that you do not need to deploy any on-premises infrastructure. Windows Defender ATP is a cloud hosted solution, even though you are using it for your on-premises endpoints.
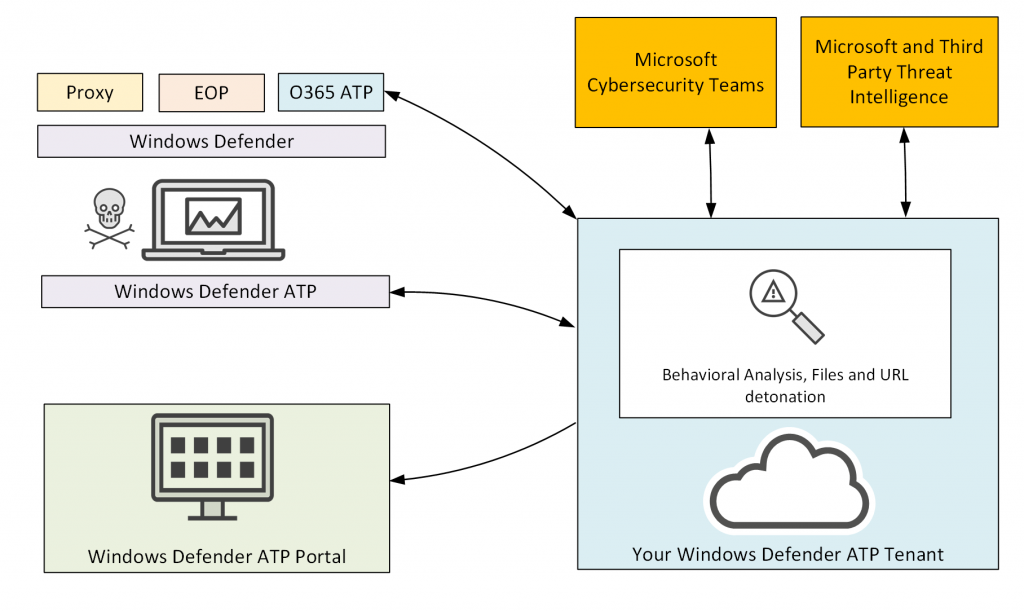
When you sign up for Windows Defender ATP a new ATP tenant is created for you to store your organization’s data separately to any other Windows Defender ATP customer, and this is associated with your existing Office 365 tenant as well.
Your endpoints are protected by your normal preventative measures. You might have a secure web proxy for internet browsing traffic, as well as Exchange Online Protection and Office 365 Advanced Threat Protection working to prevent threats from reaching your endpoints. Windows Defender or a third party anti-malware product would also be running on the endpoints to provide that traditional signature-based antivirus protection.
If malware or an attacker makes it past those defensive measures and onto the machine, Windows Defender ATP is there to analyze the behaviour of any code that the malware or attacker runs. That analysis is integrated with the cloud, and includes the ability to upload suspicious files for analysis in a sandbox. All that cloud-hosted analysis is constantly updating with learnings from the Office 365 ATP service itself, as well as input and research from Microsoft’s cybersecurity teams and third party threat intelligence services. You as the customer get access to a nice Windows Defender ATP portal for managing your endpoints, dealing with alerts, and so on.
Onboarding endpoints is as simple as running an activation script that registers the machines with your Windows Defender ATP tenant. For Windows 10, the ATP bits are already present, so there’s no MSI or Setup package to deploy. The onboarding script can be run manually, via GPO-assigned scheduled task, or by a tool like SCCM or Intune.
Windows Defender ATP in Action
If you don’t have the eligible licenses for Windows Defender ATP you can still sign up for a 90 day trial. I’ve been running Windows Defender ATP in three tenants for the last few months. Fortunately, there have been no malware outbreaks or advanced persistent threats (APTs) in any of them during that time. Unfortunately, that makes for a fairly dull demonstration of Windows Defender ATP.
To make the most of the trial period, Microsoft provides a series of simulated attack scenarios that you can run. One of the simulations is a macro-enabled Word document that downloads an harmless executable to the machine in the same way that a malicious macro might plant an attack tool or remote access trojan on a victim’s computer.
After running two out of the three simulations, I had generated a nice amount of alert traffic in my Windows Defender Security Center. The alerts appear quickly, within a few seconds in some cases. With email or other notifications configured, you would almost immediately be aware of any alert condition on a machine that is being monitored by Windows Defender ATP.
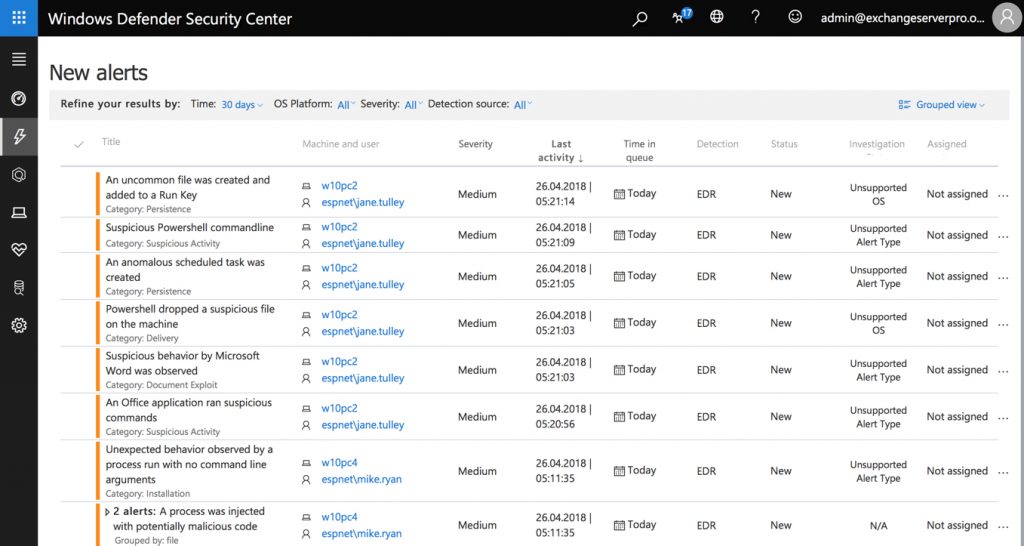
Investigating Alerts
Drilling down into one of the alerts, things start to get more interesting. Some details about what has happened are provided, as well as guidance as to what actions are recommended to begin investigating the alert.
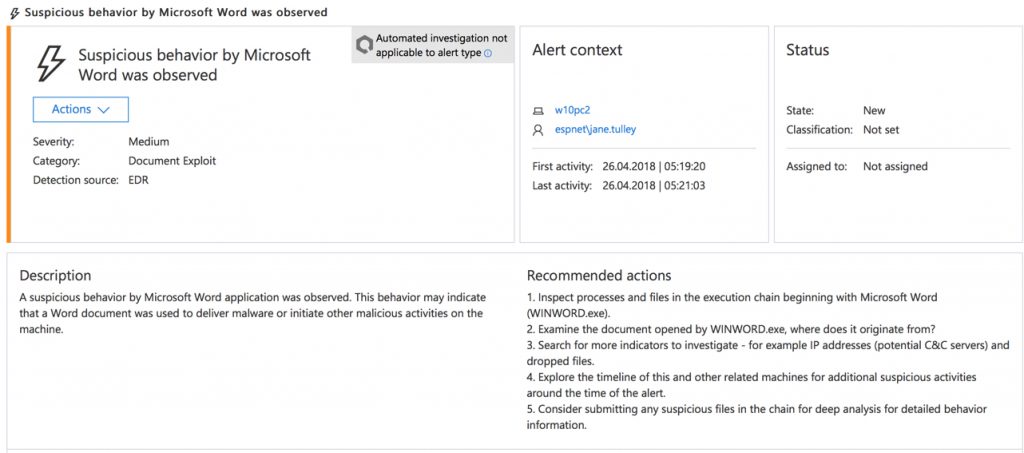
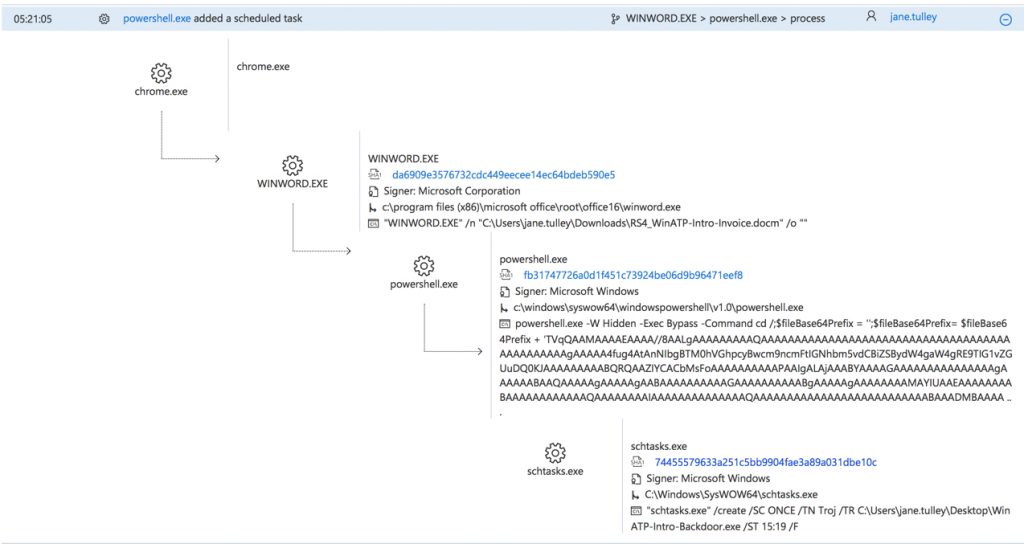
The alert process tree reveals a timeline of events on the computer. In this example we can see that Chrome was used to download a macro-enabled Word document. Microsoft Word (WINWORD.EXE) was used to open the document, which spawned a PowerShell.exe process that created an executable file named WinATP-Intro-Backdoor.exe. These events are highlighted as suspicious in the timeline.
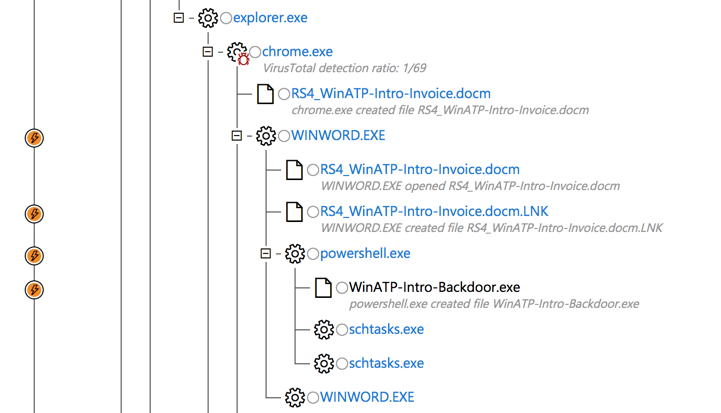
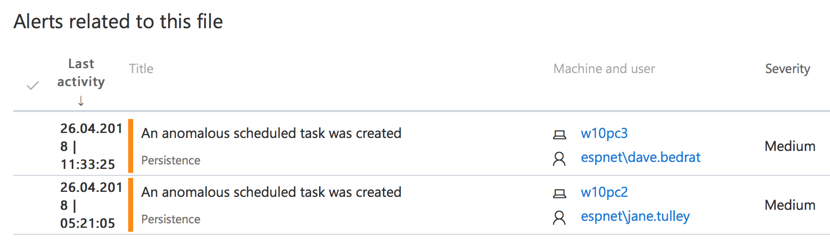
There are also two instances of schtasks.exe spawned from the PowerShell.exe process. Clicking on one of those takes us to a related alert for an “anomalous scheduled task” being created. Note that in this screenshot two different computers have this alert. I’ll come back to this point in a moment.
Obviously there’s something bad going on here, so it’s time to start an investigation into one of the machines.
Responding to Breaches
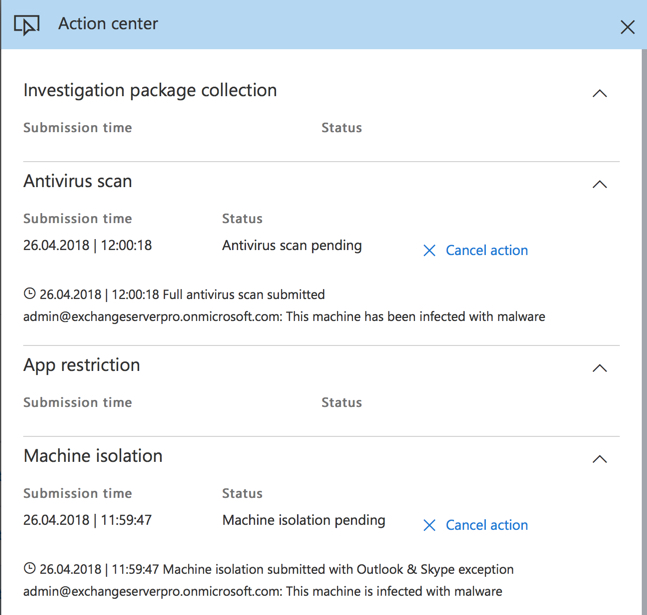
From here there’s actions we can take that include running a virus scan, restricting app execution (only Microsoft signed apps will run), or isolate the machine entirely from the network (except for Windows Defender ATP connections). As a side note, there is an alert count from Azure ATP as well. I happen to have this Windows Defender ATP instance integrated to an Azure ATP instance for the same organization. Azure ATP monitors for suspicious behavior in domain controller traffic. If this same machine was showing Azure ATP alerts that indicated an attacker had control of the machine, then that would be information that helps us decide how to respond to this incident.
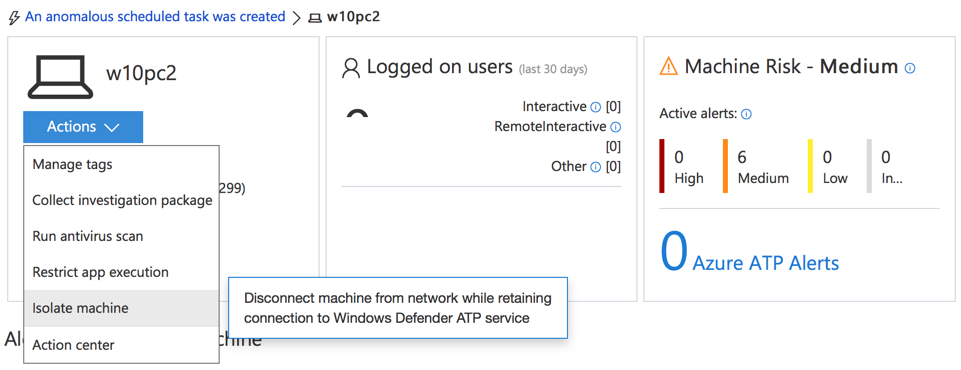
We also get to see more details of the scheduled task that was created by the malware. The scheduled task will run the backdoor executable that was dropped on the machine by the macro-enabled Word document, so that an attacker has access to the machine even after it has been rebooted.
So clearly there’s a security breach here. Remember, Windows Defender ATP is post-breach monitoring, alerting and analysis. Without Windows Defender ATP I’d have no idea that this machine was infected with this malware, because the antivirus software on the machine has not blocked it. To get to this stage, the malware had to make it past Exchange Online Protection, Office 365 ATP, Windows Defender, and the Office macro security settings on the machine. In the real world you should expect some zero day threats to make it this far, hence the need for a post-breach tool like Windows Defender ATP.
Anyway, I’ve isolated the machine and kicked off an antivirus scan for now. In all honesty I would just re-image this machine anyway. Once it has been compromised, it can’t be trusted. But you can at least scan for other infections while you wait to get hands-on with the machine.
Tracking the Spread of Infection
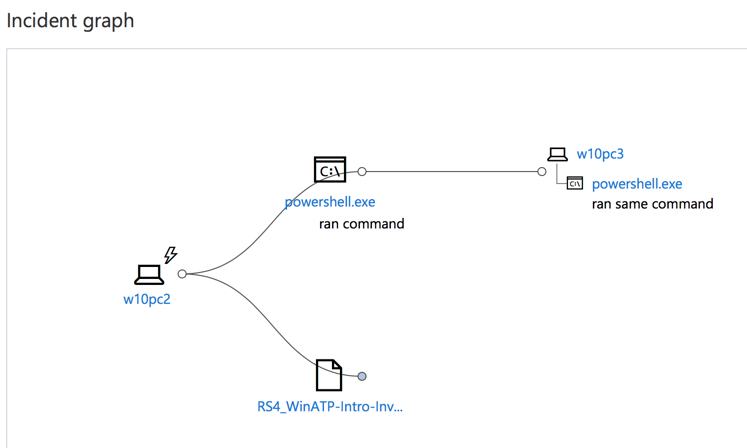
If you recall earlier we looked at a pair of alerts for anomalous scheduled task creation on two separate machines. This brings us to the question of where else has this infection spread within the network. The incident graph for an alert provides us with the answer. The initial machine, W10PC2, has potentially passed the infection along to W10PC3 which ran the same command a short time later.
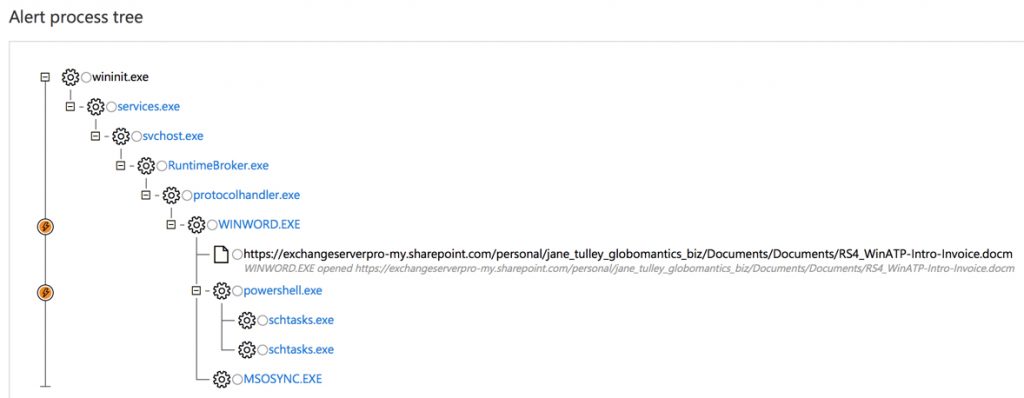
In the good old days, an investigation of this type would probably not even get this far. We’d have no idea where else an infection may have spread. Even if we ask the owner of the first infected machine, they probably won’t remember (or won’t admit to) sending a suspicious file to someone else. Fortunately, Windows Defender ATP provides those answers for us. For one thing, the alert process tree on the second computer tells us that the owner (Dave Bedrat) accessed the file from the first user’s (Jane Tulley) OneDrive. So we can reasonably conclude from this that Jane shared the file with Dave via a OneDrive sharing link.
A quick visit to the threat management explorer in the Security & Compliance Center confirms that Jane did in fact share the file with Dave via email (twice, but the first attempt was blocked due to the macro-enabled Word attachment). A message trace in Exchange Online would tell you a similar story.
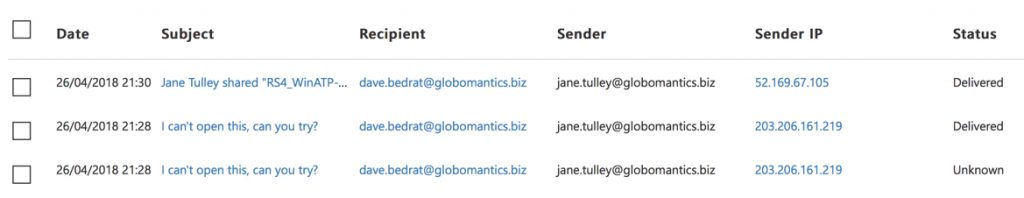
Any actions being taken on Jane’s machine (isolated, scan, re-image) should therefore also be taken on Dave’s machine as well. And further investigation can be performed to determine whether Dave sent the file to anyone else.
What’s interesting to me about this whole scenario is the visibility into the endpoints that Windows Defender ATP has provided. Being able to look at process histories, with suspicious activities already flagged and brought to your attention, is powerful stuff. Evidence of what has already happened on a machine is otherwise quite difficult to come by. If you’ve ever worked for a manager or customer who assumes you can just “look at the logs” to piece together a detailed history of a machine’s activities, then you know what I mean.
What Else Can Windows Defender ATP Do for Us?
What I’ve already demonstrated here is the core capabilities of Windows Defender ATP for detecting, investigating, and responding to suspicious activity on your endpoints. As part of your investigation, you can collect a package of files from the suspect machine and upload it to Microsoft for analysis (similar to Office 365 ATP sandbox analysis of files by Safe Attachments).
Naturally, as a cloud service Windows Defender ATP integrate with several other Microsoft services.
- Office 365 ATP – details of new zero day threats detected by either O365 ATP or Windows Defender ATP are shared between the services. For example, a threat identified by Windows Defender ATP will be blocked next time it passes through Office 365 ATP for the same customer or for other customers.
- Azure ATP – for correlation between suspicious application activity and suspicious user activity. Imagine an attacker using the backdoor that was dropped on the machine in this demo to further probe your network and attempt to gain elevated privileges. Azure ATP will alert you to that type of activity.
- Office 365 Threat Intelligence – for enabling investigations to extend into Office 365 mailboxes. In the case above, Windows Defender ATP can report that the suspicious file exists in any user mailboxes where it has been received.
- Microsoft Intune – Windows Defender ATP machine alert status can be taken into account for determining device compliance, which allows it to be a factor in conditional access rules as well.
You can also integrate Windows Defender ATP with a SIEM tool, if you’re already running one, and third party threat intel services.
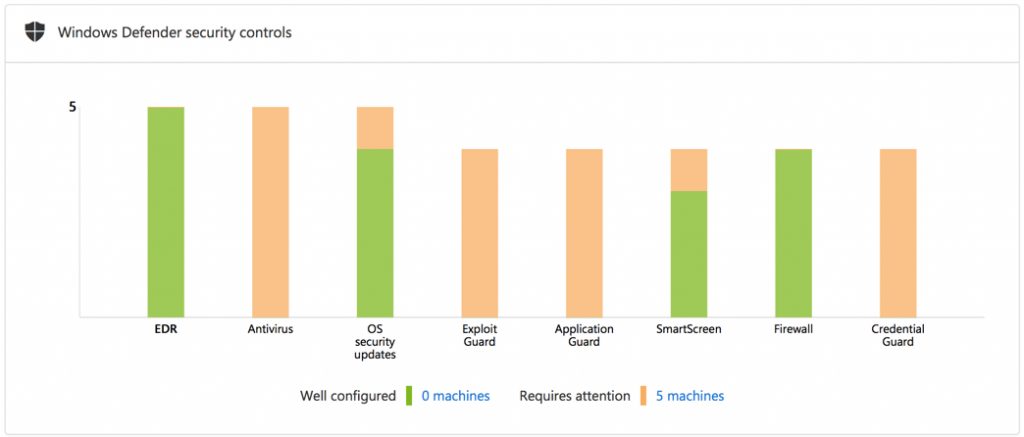
Windows Defender ATP also provides its own “secure score” rating that grades your compliance with recommendations for configuration of Windows Defender features such as Exploit Guard. Microsoft’s documentation is available to let you know exactly how to implement those recommendations.
Summary
Windows Defender ATP provides excellent visibility into the applications and code that are running on your user’s machines. There’s a lot of development still happening with Windows Defender ATP as well. New features are appearing rapidly, and the product just gets better each month.
Although the enterprise licensing might make it difficult for some customers to acquire Windows Defender ATP, it is fairly simple to sign up for a 90 day trial to at least look at how well it performs in your environment. Given there is no requirement to deploy servers, only to onboard endpoints with a simple script, the roll out of Windows Defender ATP is quite simple to achieve.
Photo by Olloweb Solutions on Unsplash
[adrotate banner=”50″]





Pingback: Windowsdefenderatp比較 - Compare · microsoft/WindowsDefenderATP-Hunting-Queries · GitHub
Does your course align to the MS-500 exam requirements? I’d like to become certified – it gets me motivated – but I would like to enroll for an online course that can provide me with a great foundation for taking on the exam.
Hi Paul
I want to start my career in window defender ATP. Please consult me from where I can start and from where I can get detail information about WD ATP.
Thanks and Regards
Gaurav
Thanks for the info Paul. Great article.
I have enrolled some Windows 7 machines into ATP, but I cannot run the toolsets thats available for Windows 10? Is my configuration incorrect?
regards
Hi Paul,
If our organinsation is running on Windows 10 Pro, Can we onboard those devices to Windows Defender ATP?
Thanks for you time.
Thanks for the quick reply, will be on the lookout.
Hey Paul, great article! When is your Office 365 Security coruse going to be available on Pluralsight?
It’s on final production stage now. So could be any day now.
Thanks, Paul. Does it work for older Windows clients (e.g. 7, 8)?
Yes, that is the “down-level” support I mentioned in the post. It’s been announced, due for availability sometime this year.