How Web Sign-in Helps Achieve Passwordless Authentication
It’s been four years since Microsoft launched security key (FIDO2) sign-in to Windows 10. Since then, there have been no new sign-in options for Windows. This is changing with Windows 11 with the introduction of a new form of sign-in called ‘Web sign-in’ which uses an embedded browser to allow the user to authenticate just as they do using a web portal. A web sign-in requires an internet connection and is only available on Windows 11 and Microsoft Entra joined devices (previously Azure AD joined).
Enabling Web Sign-in
Web sign-in isn’t available by default and needs to be turned on explicitly. The easiest way to do this is by using a Settings Catalog policy in Microsoft Intune. If you do not use Microsoft Intune, you can configure the following OMA-URI (./Vendor/MSFT/Policy/Config/Authentication/EnableWebSignIn) with another MDM tool such as ManageEngine.
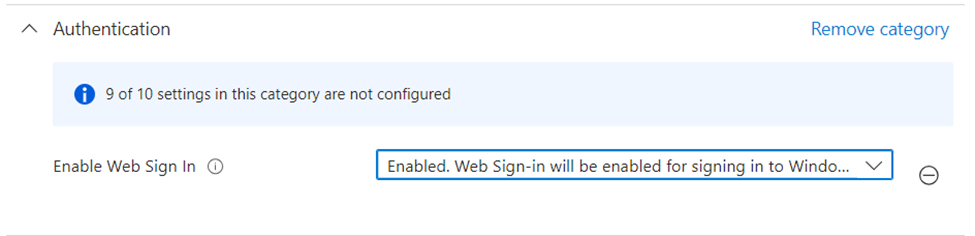
To create a policy in Intune, go to the Intune Admin portal (https://intune.microsoft.com) and go to Devices > Windows > Configuration Policies. Within the settings catalog, you must enable the setting ‘Enable Web sign-in’ from the ‘Authentication’ category, as seen in Figure 1.
How Does Web Sign-In Work?
After enabling the setting, a new icon (![]() ) appears on the lock screen. If you click the icon, an embedded web browser appears. This experience is the same as if you sign into Microsoft 365. After filling in your username, you are prompted to enter your password or to execute a passwordless sign-in using a FIDO2 key or the Microsoft Authenticator app.
) appears on the lock screen. If you click the icon, an embedded web browser appears. This experience is the same as if you sign into Microsoft 365. After filling in your username, you are prompted to enter your password or to execute a passwordless sign-in using a FIDO2 key or the Microsoft Authenticator app.
If we review the documentation for the specific setting, there is a clear warning:
The Web sign-in feature is intended for recovery purposes in the event a password isn’t available as an authentication method. Web sign-in only supports temporary access pass as an authentication method for Microsoft Entra ID, unless it’s used in a limited federated scope.
This is important information as it is clear Microsoft does not envision you to use the browser as your primary method for signing into a Windows 11 computer. While Microsoft does not say why, I have identified a number of disadvantages of using Web sign-in.
- A computer needs an internet connection before you can sign in. If somebody visits a new place, most people tend to sign into the laptop first and only connect to the Wi-Fi later.
- The web sign-in method is a bit tedious and time-consuming. Using other methods (such as password or PIN), you can log into your device in seconds. When using web sign-in, it takes a while for the embedded browser to open and complete the process.
However, there are two valid use cases for web sign-in:
- 100% passwordless authentication while using a Windows device.
- Allowing IT support engineers to set up an end-user’s computer without needing to know their password.
Using Web Sign-in for Passwordless Authentication
One of the main reasons to use web sign-in is to create a 100% passwordless experience. When someone receives a new computer, Windows Hello for Business is not configured and thus the user must fill in their username and password on the Windows login screen after OOBE (Out-Of-Box Experience). After the initial sign-in, they can configure Windows Hello for Business, essentially enabling the user to execute passwordless sign-in in the subsequent scenarios.
By enabling web sign-in, a user can authenticate with the Microsoft Authenticator app before configuring Windows Hello for Business.
You might think that this scenario is also covered by FIDO2, but this is only partially true. If you configure multiple accounts from the same tenant on a key, you cannot choose which account to use when signing in. That is why FIDO2 sign-in doesn’t cover all scenarios that allow for a 100% passwordless experience.
After configuring the device, you can choose to enable the Windows passwordless experience. This will remove password sign-in during login. If the user forgets their Windows Hello PIN code, they can use the web sign-in to execute a password reset.
Passwordless Computer Configuration
When I was a support engineer, I would log new computers with the owner’s account when setting up their device. In an ideal world, this should not be necessary as this is what Windows Autopilot Pre-Provisioning is for. Pre-provisioning ensures all user-bound configurations happen before the user first logs in.
However, in reality, support engineers still log in to ensure that the Outlook profile exists, preferences are correct, and that data is migrated from old devices. In order to sign-in to a user’s account, that person’s password is required. Most of the time, the end-user provides the password. In some cases, they might reset it temporarily, so the engineer does not know their actual password. While this is better than sharing the actual password, the user experience is still not great as executing password changes messes up things such as email synchronization on a mobile phone. In any case, asking the end-user for their password is a bad practice and teaches them that sharing their password is okay, which should never be the case.
The solution is to use a Temporary Access Pass (TAP) in combination with Web sign-in. Temporary Access Pass is a limited lifetime credential that serves as a multifactor-capable method. The maximum lifetime of a TAP is 8 hours, and you can configure it to be used once or multiple times. In our scenario, a support engineer can create a multi-use TAP that is valid for 4 hours. By using web sign-in, this TAP can be used to ensure the engineer can log into the device, reboot it multiple times to install updates, and deliver it to the end-user. When the user receives their device, they can log in and configure Windows Hello for Business.
This is the approach that I use to set up new devices for customers. It removes the dependency to ask for the password and allows for a seamless handover to the user.
Use Web Sign-in When Necessary
Web sign-in is a new feature specific to Windows 11 and covers a specific use case, aimed at passwordless authentication. It’s great if you are working on your own passwordless journey, but it’s not a feature that is useful for every organization.




