Safe Teams External Access Means Limiting Communications to Known Domains
In September 2022, a security researcher demonstrated how an external participant in a Teams chat could send a modified GIF containing malware that infected the recipient’s PC. By default, Teams allows users to chat with anyone from any other Microsoft 365 tenant. The solution to something like the GIFShell exploit is to restrict Teams external access to an allow list (whitelist) of known tenants.
The problem then becomes how to populate the allow list. At the time, I suggested that organizations could make a start by building a list of the domains that guest accounts came from. It isn’t difficult to use PowerShell to find all guest accounts, extract their domains, and use that information to build a allow list, which is large enough to accommodate approximately 4,000 domains.
Job done, or so I thought. However, others believe that using guest domains as the basis for an allow list isn’t good enough. There’s no guarantee that the set of domains derived from guest accounts will cover every possible domain that an external chat participant might come from. Some arrangement is therefore necessary to allow people to request the addition of a domain to the allow list. This reduces the spontaneous nature of chat-based collaboration across organizations, but it might be the price necessary for secure communications.
Then someone decided that it might be possible to examine all external chats in an organization to discover the set of domains that external chat participants belong to. Sounds good, but how can you find and process the information from user chats? That’s what I explain in this article.
Accessing Chat Participants is the Key for Teams External Access
In another article, I explain the basics of using the Microsoft Graph PowerShell SDK to find and process Teams chat and chat messages. The PowerShell script dissected in that article allows administrators to remove messages from group chats that might be objectionable or contain sensitive information. The script needed here has to find chats too, but one-to-one chats rather than group chats. After finding a list of user accounts with the Get-MgUser cmdlet, we can use a different filter with the Get-MgBetaUserChat cmdlet to find the one-to-one chats for each user.
Each chat has a list of participants that can be fetched using the Get-MgChatMember cmdlet. One of the participants is a tenant account, the other might be an external participant. To build a list of external domains, the script needs to examine the participants for each chat and find those involving external participants. With that data, the script can build a domain list. At least, that’s the theory.
Defining the Solution
The outline of the solution is clear. However, detail makes the difference and there are some important details to consider here.
First, the script must use application permissions to access user chats. This wasn’t a problem for the previous script because I used an Azure Automation runbook with a managed identity for authentication. The necessary Graph permissions are assigned to the Azure Automation account.
In this scenario, I want to use the Get-CsTenantFederationConfiguration cmdlet from the Microsoft Teams module to fetch details about the tenant’s external access configuration. The policy management cmdlets that Teams inherited from Skype for Business Online do not support managed identities (the other Teams cmdlets do because they are Graph-based). I could get around the problem and still use Azure Automation by leveraging Azure Key Vault to store account credentials and using those credentials to connect to Teams. In the end, I decided to go with a different approach and use certificate-based authentication because all cmdlets support this approach.
Because the script uses certificate-based authentication, it needs a registered Entra ID app to store the certificate and hold the Graph permissions necessary to access the data needed by the script:
- CrossTenantInformation.ReadBasic.All: Read tenant identifier and return tenant display name.
- User.Read.All: Read user account information.
- Chat.Read.All: Read user chats.
- Directory.Read.All: Read home tenant information from the directory.
- Mail.Send: Send an email with the results.
In addition, because the script runs a Teams policy management cmdlet, the app must hold the Teams administrator role. This isn’t difficult because the role assignment is easily done using the Entra ID admin center, but it is an example of the kind of detail required to make everything work.
The steps outlined in this article describe how to create a self-signed certificate (enough for testing) and upload it to a registered app (Figure 1).
The article also describes how to use PowerShell to assign an Entra ID administrative role to an app using code like this:
$TeamsAppSp = (Get-MgServicePrincipal -Filter "DisplayName eq ‘PowerShellGraph'").Id
$TeamsRoleId = (Get-MgDirectoryRole | Where-Object {$_.DisplayName -eq "Teams Administrator"}).Id
$NewAssignee = @{
"@odata.id" = ("https://graph.microsoft.com/v1.0/directoryObjects/{0}" -f $TeamsAppSp)
}
New-MgDirectoryRoleMemberByRef -DirectoryRoleId $TeamsRoleId -BodyParameter $NewAssignee
With the app assigned the necessary permissions and role and a certificate in place, we can write some code.
Scripting the Solution
The steps in the script are:
- Connect to the Microsoft Graph endpoint using certificate-based authentication. You need the client identifier for the registered app, the tenant identifier, and the certificate thumbprint to connect.
- Connect to the Teams endpoint using certificate-based authentication. Get-CsTenantFederationConfiguration is the only cmdlet used from the Teams module. All other cmdlets come from the Microsoft Graph PowerShell SDK.
- Find the set of registered domains for the tenant. This information is used to figure out if a one-to-one chat is with someone from inside or outside the tenant.
- Fetch the set of licensed user accounts in the tenant. This can include shared mailboxes with licenses, but it’s the easiest and quickest way to find the set of accounts that use Teams.
- For each user, find the set of their one-to-one chats. A small delay is imposed between each user to avoid Microsoft 365 throttling.
- For each chat, retrieve the participant list and remove the user being processed from the list. Because these are one-to-one chats, only one other participant should remain.
- Find the domain name for the other participant to figure out if the chat is internal or external.
- If external, resolve the tenant domain by using the tenant identifier.
- If the chat is hosted by the home tenant, retrieve the number of messages in the chat. You can’t retrieve this information for chats hosted by external tenants.
- Record what’s been found and go back to process the next chat.
- After processing chats for all users, check the Teams external access configuration and compare the domains in its allow list against the domains used for external chats. Report any domains used for external chats that are not in the allow list.
- Email the results to a predetermined recipient. The results are details of external chats and the information about external domains.
- Declare success.
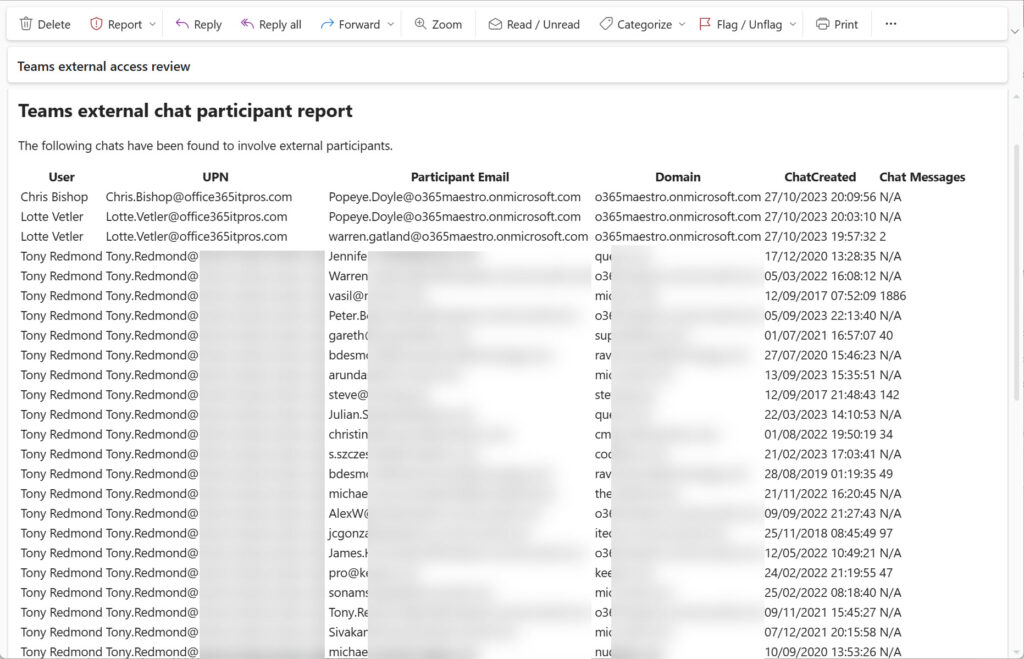
Figure 2 shows an example of the email sent by the script. The set of properties for each record is defined in the script and doesn’t include all those captured in the report. No filtering of the data is done. For example, you might decide to concentrate on chats with external participants initiated in the last two years and ignore earlier chats.
Running the Script
You can download the script from GitHub. Remember, this script works but it is only intended to demonstrate the principles of using the Graph SDK to fetch and process information about Teams chats and their participants. It is not designed to be an off-the-shelf solution and I have not run it at true scale. Given the need to fetch all one-to-one chats for each user processed, the script is not lightning-fast. You might want to run it for a limited set of users first. If so, apply a filter to the set of users fetched from Entra ID. For instance, to limit the set to users from a specific department, you could modify the Get-MgUser call to something like this:
[array]$Users = Get-MgUser -Filter "assignedLicenses/`$count ne 0 and userType eq 'Member' and department eq 'IT'" -ConsistencyLevel eventual -CountVariable Records -All | Sort-Object displayName
Before attempting to run the script, make sure that all the prerequisites are satisfied and that you use a registered app assigned the necessary Teams administrator role and Graph permissions.
Make Decisions Based on Data
This exercise is a good example of how useful the Microsoft Graph PowerShell SDK is when the need arises to extract information from Microsoft 365. Without access to user chats, it’s impossible to know who outside the tenant people are conversing with. The Graph SDK exposes their secrets and helps administrators make better decisions based on data rather than intuition, and that’s always a good thing.
Microsoft Platform Migration Planning and Consolidation
Simplify migration planning, overcome migration challenges, and finish projects faster while minimizing the costs, risks and disruptions to users.





@ Tony
How can I include Teams meeting with external user in this report?
BR
You’d have to read the meeting information from user mailboxes, find meetings with external users, and create a list of domains. It’s not Teams data – instead, you’re looking at calendar events, so you’d use code similar to that discussed in https://practical365.com/calendar-events-graph-api/
Thank you.
BTW, is it possible to send https://admin.teams.microsoft.com/analytics/reports (External domain activity) to a user automatically? If not is there any Graph API I can use to build the same.
Domain Name Users in your org TimePeriod
office365support.com 1 7d
The report is essentially the same data as the data created by this script. The Teams admin center doesn’t have a way to circulate the report automatically, but you could do it with PowerShell.
ok. if I create a teams meeting link and send to a user and user joins the meeting where those information are stored? how can I extract them?
BR
Hello Tony,
I have come up with this but it does not pick all records. I want to get exactly the same result with additional fields. Any suggestion will be much appreciated.
# Connect to Exchange Online (run this before script or uncomment)
# Connect-ExchangeOnline
# Configuration
$StartDate = (Get-Date).AddDays(-7)
$EndDate = Get-Date
$ChunkHours = 24 # Smaller chunks for PowerShell 7 efficiency
$MaxResults = 5000
$BatchSize = 200 # Larger batches for PS7
$MaxConcurrentJobs = 3 # Parallel processing
Write-Host “Fetching tenant accepted domains…”
$tenantDomains = Get-AcceptedDomain | Select-Object -ExpandProperty DomainName
if (-not $tenantDomains) {
Write-Warning “No accepted domains found. Exiting.”
return
}
# Convert to hashtable for O(1) lookups
$tenantDomainsHash = @{}
$tenantDomains.ForEach{ $tenantDomainsHash[$_.ToLower()] = $true }
Write-Host “Tenant domains: $($tenantDomains -join ‘, ‘)”
# Pre-compile regex for better performance
$emailRegex = [regex]::new(‘@’, [System.Text.RegularExpressions.RegexOptions]::Compiled)
# Use concurrent collection for thread safety
$results = [System.Collections.Concurrent.ConcurrentBag[PSCustomObject]]::new()
function Invoke-SearchUnifiedAuditLogOptimized {
param (
[datetime]$Start,
[datetime]$End,
[int]$MaxResults = 5000
)
$maxRetries = 3
$retryCount = 0
do {
try {
Write-Host “Searching logs from $Start to $End…”
$logs = Search-UnifiedAuditLog -StartDate $Start -EndDate $End -ResultSize $MaxResults -ErrorAction Stop
return $logs
}
catch {
$backoffSeconds = [Math]::Pow(2, $retryCount) + (Get-Random -Maximum 1000) / 1000
Write-Warning “Search-UnifiedAuditLog failed: $_. Retrying in $([Math]::Round($backoffSeconds, 2)) seconds…”
Start-Sleep -Seconds $backoffSeconds
$retryCount++
}
} while ($retryCount -lt $maxRetries)
throw “Search-UnifiedAuditLog failed after $maxRetries retries.”
}
# Optimized participant extraction using PowerShell 7 features
function Get-ParticipantsFromData {
param($log, $data)
$participants = [System.Collections.Generic.List[PSCustomObject]]::new()
# Use PowerShell 7’s improved null handling and performance
$possibleFields = @(
$log.UserId,
$data.UserId,
$data.Participants,
$data.Users,
$data.Attendees,
$data.UserIds
).Where{ $null -ne $_ }
foreach ($field in $possibleFields) {
if ($field -is [System.Collections.IEnumerable] -and $field -isnot [string]) {
$field.ForEach{
$participant = Get-ParticipantFromItem $_
if ($participant) { $participants.Add($participant) }
}
}
else {
$participant = Get-ParticipantFromItem $field
if ($participant) { $participants.Add($participant) }
}
}
return $participants
}
function Get-ParticipantFromItem {
param($item)
switch ($item) {
{ $_ -is [string] -and $emailRegex.IsMatch($_) } {
return [PSCustomObject]@{
DisplayName = $null
UPN = $_
Domain = ($_ -split ‘@’)[-1].ToLower()
}
}
{ $_ -is [pscustomobject] -and $_.UPN -and $emailRegex.IsMatch($_.UPN) } {
return [PSCustomObject]@{
DisplayName = $_.DisplayName
UPN = $_.UPN
Domain = ($_.UPN -split ‘@’)[-1].ToLower()
}
}
default { return $null }
}
}
# Process chunk function for potential parallel execution
function Process-AuditChunk {
param($chunk, $chunkNumber, $totalChunks)
Write-Host “[$chunkNumber/$totalChunks] Processing chunk: $($chunk.Start) to $($chunk.End)”
$chunkResults = [System.Collections.Generic.List[PSCustomObject]]::new()
try {
$logs = Invoke-SearchUnifiedAuditLogOptimized -Start $chunk.Start -End $chunk.End -MaxResults $MaxResults
if (-not $logs -or $logs.Count -eq 0) {
Write-Host “[$chunkNumber/$totalChunks] No logs found”
return $chunkResults
}
# Apply filtering with PowerShell 7’s improved Where-Object
$filteredLogs = $logs.Where{
$_.RecordType -like ‘*Teams*’ -or
$_.Operation -match ‘MeetingCreated|MeetingParticipantAdded|MeetingParticipantJoined’
}
Write-Host “[$chunkNumber/$totalChunks] Found $($filteredLogs.Count) matching logs”
if (-not $filteredLogs -or $filteredLogs.Count -eq 0) {
return $chunkResults
}
# Process in batches with PowerShell 7’s improved performance
for ($i = 0; $i -lt $filteredLogs.Count; $i += $BatchSize) {
$batch = $filteredLogs[$i..([Math]::Min($i + $BatchSize – 1, $filteredLogs.Count – 1))]
$batch.ForEach{
$log = $_
try {
$data = $log.AuditData | ConvertFrom-Json -ErrorAction Stop
}
catch {
Write-Warning “Failed to parse JSON for log at $($log.CreationDate)”
return # Continue to next item in ForEach
}
$participants = Get-ParticipantsFromData -log $log -data $data
if ($participants.Count -eq 0) { return }
# Use PowerShell 7’s improved Where-Object performance
$external = $participants.Where{ -not $tenantDomainsHash.ContainsKey($_.Domain) }
$internal = $participants.Where{ $tenantDomainsHash.ContainsKey($_.Domain) }
if ($external.Count -eq 0) { return }
# Use null coalescing operators (PowerShell 7 feature)
$operation = $log.Operation ?? $data.Operation ?? ‘Unknown’
$meetingId = $data.MeetingId ?? $data.MeetingDetails?.MeetingId ?? ‘N/A’
# Pre-calculate internal users string
$internalUsersString = ($internal.UPN | Sort-Object -Unique) -join ‘; ‘
$external.ForEach{
$ext = $_
$chunkResults.Add([PSCustomObject]@{
Date = $log.CreationDate
Operation = $operation
MeetingID = $meetingId
ExternalName = $ext.DisplayName
ExternalUPN = $ext.UPN
ExternalDomain = $ext.Domain
InternalUsers = $internalUsersString
})
}
}
}
}
catch {
Write-Error “[$chunkNumber/$totalChunks] Failed to process chunk: $_”
}
return $chunkResults
}
# Calculate chunked date ranges
$chunks = for ($dt = $StartDate; $dt -lt $EndDate; $dt = $dt.AddHours($ChunkHours)) {
$chunkEnd = if ($dt.AddHours($ChunkHours) -gt $EndDate) { $EndDate } else { $dt.AddHours($ChunkHours) }
[PSCustomObject]@{ Start = $dt; End = $chunkEnd }
}
Write-Host “Processing $($chunks.Count) chunks with $ChunkHours hour intervals…”
# Sequential processing with progress (you can enable parallel processing if needed)
$allResults = [System.Collections.Generic.List[PSCustomObject]]::new()
$chunkCounter = 0
foreach ($chunk in $chunks) {
$chunkCounter++
Write-Progress -Activity “Processing audit logs” -Status “Chunk $chunkCounter of $($chunks.Count)” -PercentComplete (($chunkCounter / $chunks.Count) * 100)
$chunkResults = Process-AuditChunk -chunk $chunk -chunkNumber $chunkCounter -totalChunks $chunks.Count
$chunkResults.ForEach{ $allResults.Add($_) }
}
Write-Progress -Activity “Processing audit logs” -Completed
if ($allResults.Count -gt 0) {
Write-Host “Exporting $($allResults.Count) records to CSV…”
$allResults | Export-Csv .\ExternalMeetingActivity.csv -NoTypeInformation -Encoding utf8
Write-Host “Report exported: ExternalMeetingActivity.csv ($($allResults.Count) records)”
} else {
Write-Warning “No external meeting activity found in the queried period.”
}
# Memory cleanup
$allResults.Clear()
$allResults = $null
$results = $null
Thank you
This code seems like you’re calling the Search-UnifiedAuditLog cmdlet to fetch all audit events for a period and then selecting those for Teams meetings to parse the participants. I wonder why you’re not calling Search-UnifiedAuditLog with the Operations parameter to only fetch events of the required type, and why you don’t remove the duplicates that often come back by sorting on the unique identity… And the code won’t find meetings organized with Outlook…
Also, will the operations you’re looking for find participant detail? https://learn.microsoft.com/en-us/purview/audit-log-activities#microsoft-teams-activities
We are trying to identify all external users or domains that our organization’s users have communicated with using Microsoft Teams (chat, meetings, or calls). Is there a way to extract or generate a report showing these external interactionsusing PowerShell?
Ideally, we’d like to see:
The external domain or email
The internal user(s) who interacted with them
The type of communication (chat, call, meeting)
Date/time of interaction (if available)
The article covers how to extract the information for chats. I haven’t tried finding that kind of data for calls. For meetings, youd’d use the Events API to find meetings in user calendars and extract the participant information from those events. I already pointed you to an article about how to use the events API. All can be done with PowerShell.
Thank you again. Your script works well but it checks every user chat history for unlimited time and for a large tenant it is very time consuming. I wanted to get for 7 or 30 days period. Also your other article again great script and article. I could be wrong – it does not give me if I create a meeting link and send to an external user that does not store in Calendar.
In Short I like to get any kind of teams interactions for all users EXCEPT accepted domains with my tenant
Thank you
BTW, How can I run your script for 7, 30, 60 days? Can you please let me know?
Thank you
I imagine you’d add some code to state the period the script should cover… and add a parameter to allow the user to choose.
The data you want to extract is available – calendar events have a property to show if they are an online event that can be used to find Teams meetings. You’ll need to check the participants of these events to find external users.
These scripts are not written to be production code. Instead, they are intended to demonstrate principles that readers can exploit to build whatever code is needed. I don’t have the time or the energy to solve every problem a reader has when building their own version of scripts. That’s where you come in…
I wrote some code based on the room mailbox reporting script to find online meetings in user calendars, extract the attendees from the meetings, and determine the set of external domains found for meeting attendees:
Unique domains found bibblenet.com; bluewin.ch; cmportalsolutions.com; eightwone.com; gmail.com; itechcs.onmicrosoft.com; keepit.com; michev.info; microsoft.com; o365maestro.onmicrosoft.com; ravenswoodtechnology.com; mykit.com
Is this what you want to do?
Hi Tony
That will definitely help.
Thank you again for all your afford.
try https://github.com/12Knocksinna/Office365itpros/blob/master/Analyze-ExternalCalendarMeetings.PS1
I plan to write about this, but you can test the code…
Has anyone encountered this error?
Can’t fetch participant information for chat 19:323dc082-0c43-434a-a27a-4d23d8262cc2_c3f29ef2-863c-4799-b778-b447d2513e10@unq.gbl.spaces
I get this on every chat and no results.
Are you running the script with the right permissions? If you run the code interactively, the script can use delegated permissions to fetch your chats but it cannot access chats in other accounts. In the article, I say:
First, the script must use application permissions to access user chats. This wasn’t a problem for the previous script because I used an Azure Automation runbook with a managed identity for authentication. The necessary Graph permissions are assigned to the Azure Automation account.
If you want to run the job interactively, create a registered Entra ID app, assign it application permissions, create a certificate and upload it to the app, and then run Connect-MgGraph with the certificate thumbprint, app id, and tenant id.
@Tony: Spelling mistake in Line 65: Lookimng for chats for user 😊
Thanks for this amazing script!
Aha. A bug I can fix! 😉
Thanks for sharing the script Tony. I had the same idea a couple of months ago but never found the time to get into developing it, so this is much appreciated!
Great walkthrough of a clever use of the available information.
One non-technical note though: replace whitelist with allowlist.
Well, the whitelist term is used for external access but I won’t fall out with you and have changed the term in the article.