An Ongoing Battle to Improve Tenant Security
If there’s one topic all administrators can agree on, it’s that security is something every organization should work to improve in 2022. However, when it comes to tightening security for a tenant, some administrators incorrectly believe they need Azure AD Premium or Enterprise Mobility and Security to do so. While most of Microsoft’s marketing does tend to favor the more expensive SKUs, achieving the ‘minimum’ required security configuration is possible without spending extra money.
In this two-part article series, I’ll explain ten different ways to improve tenant security that every administrator should consider. In the first part, I’ll review five ways to harden your tenant without the need for extra licenses using controls that every organization can implement. In the second part, I’ll cover five ways that do require additional licenses, such as Azure AD Premium.
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.
One: Choose Least Privileged Admin Roles
Currently, Azure AD supports eighty-one different administrator roles. Most day-to-day administrator tasks can be delegated to a specific, granular administrator role to avoid using over-privileged accounts. The most common role amongst organizations is the ‘Global Administrator’ which exists in every tenant. A user with this role has permissions to update every setting in the tenant.
While holding the global administrator role ensures that an admin can execute their tasks, assigning a global administrator to more than a limited set of accounts is extremely dangerous. An administrator with these permissions can remove every user account; read, and update every mailbox item in the tenant; and prevent users from logging in. If compromised, an account with the global administrator role has so many permissions that an attacker can implement any number of backdoors, which most organizations can’t spot.
Luckily, almost every task executed by a global administrator can be delegated to a less privileged role. A great example is Domain Name Administrator. Before this role existed, only a global administrator could add a domain to the tenant, but now you can delegate this task to the domain name administrator role.
With so many roles available, it can be tricky to determine which one is the least privileged for a task. Microsoft publishes a list of every role with their detailed permissions, in addition to a list of actions and the least privileged role to execute that action. Unfortunately, this list only covers Azure Active Directory and not Microsoft 365 in general.
If you can’t immediately find the information you need, locating the least privileged role sometimes requires a bit of trial and error. In that instance you would assign the role, assess if the admin can execute the necessary tasks, and if needed assign another (more privileged) role.
Aside from the Azure AD roles, most products have their own set of granular roles, and a perfect example is Intune. There’s only one role, ‘Intune Administrator’ in Azure AD, but an administrator can create granular roles within the Intune portal itself.
Two: Enable MFA and Blocking Legacy Authentication Through Security Defaults
Multifactor (MFA) authentication is a basic control every organization should enable, and a hot topic in many security-related conversations these days. According to recent numbers published by Microsoft, only 22% of Azure Active Directory tenants have a strong authentication setup through either Azure AD and/or third-party Identity Providers.
Currently, there are two ways you can enable multifactor authentication – by Office 365 ‘per-user’ MFA, or through Security Defaults.
Office 365 ‘per-user’ MFA has existed for a long time, and it allows you to manage MFA on a per-user basis (which also happens to be its biggest downside.) When a new employee joins the organization, MFA for their account must be manually enabled.
Additionally, the MFA configuration portal is extremely old (Figure 1), lacks recent updates and desperately needs a makeover:
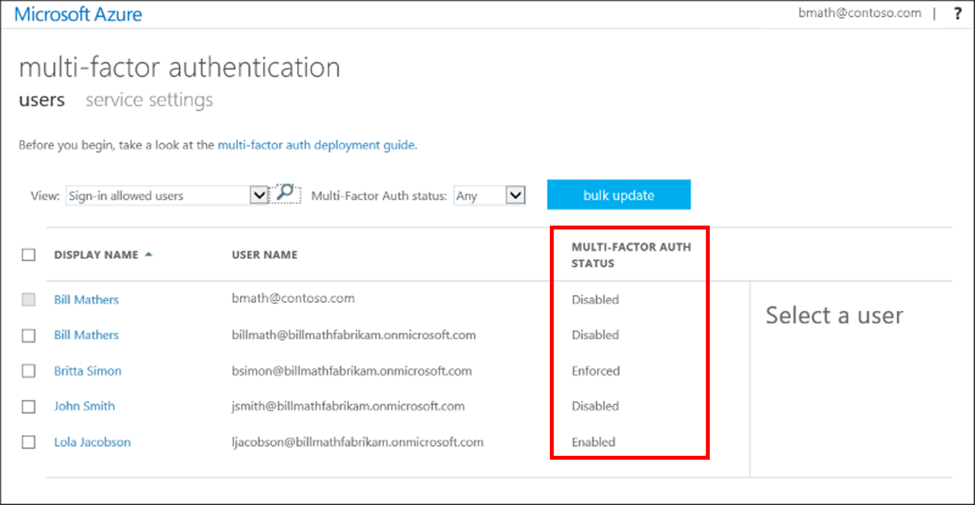
Security Defaults is a relatively new feature that Microsoft enables for every newly created tenant. With a single setting you can activate the following controls:
- Require multifactor authentication for certain high-privileged administrator roles.
- Require multifactor authentication for users when Azure AD deems the sign-in risky.
- Block legacy authentication.
- Require multifactor authentication when users access Azure resources (through the portal or API).
Security Defaults doesn’t require extra licenses and any tenant can enable it, making it an extremely valuable feature in the battle to secure tenants. To check if Security Defaults is enabled, open the Azure AD admin center, select Properties and choose Manage Security defaults as shown in Figure 2. On the next screen, you’ll choose to enable or disable Security Defaults.
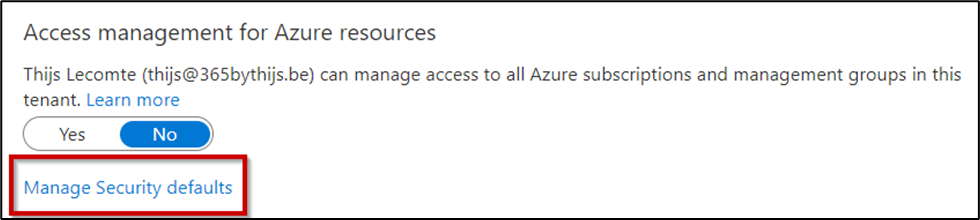
The main downside to using Security Defaults is the fact that they don’t support any exclusions. If you have accounts or business applications that don’t support these rules, you can work around the controls or disable security defaults entirely. You can work around most of the Security Defaults controls by using app registrations and the Graph API. If you do not have Azure AD Premium licenses, this is the best way to increase your identity security.
Read more: What are Azure AD Security Defaults, and should you use them?
Three: Avoid Enterprise Applications Phishing Attacks
Enterprise Applications integrate first or third-party applications into Microsoft 365, and with them you can enable a third-party application to access data in Microsoft 365 (including Single Sign-On data, files and emails). While it’s nice to be able to integrate applications with Microsoft 365, attackers are using Enterprise Applications to compromise tenants.
By tricking a user into adding a new Enterprise Application into a tenant, that application will receive permissions within the tenant, bypassing MFA and password changes. Enterprise Applications can also be a vector for a ransomware attack on Exchange Online.
To disable the ability for users to grant consent for Enterprise Applications, open the Azure AD admin center, navigate to Enterprise Applications > Consent and Permissions (Figure 3) and choose either Do not allow user consent, or Allow user consent for apps from verified publishers, for selected permissions. I recommend the first option as this gives you total control of Enterprise Applications within your organization.
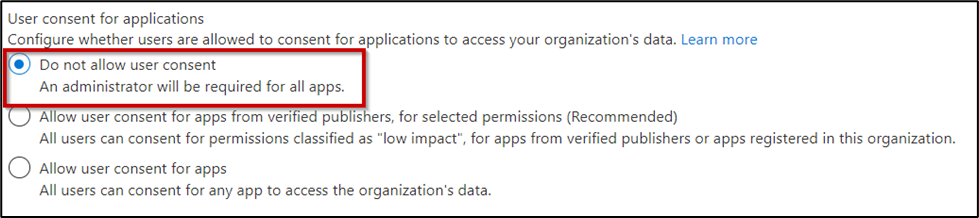
When disabling Enterprise Application consent, I’d advise that you enable Admin Consent Workflow as this allows end-users to request the addition of certain Enterprise Applications.
Four: Keep an Eye on Audit Logs
Audit logs detail what is happening in an environment, including both user and administrator activities. The Microsoft 365 platform contains a plethora of logs, capturing events from activity in Teams to user mailboxes to administrator changes, such as updates to security policies in Azure AD.
You should regularly review these three logs:
- Azure AD Audit Logs
- Unified Audit Logs
- Combines events generated by multiple Microsoft 365 workloads into a single log; a complete list of sources can be found in the Microsoft docs.
- Exchange mailbox logs
When combing through the logs you might find use cases where you’ll want to generate alerts when certain activity happens, and this is where Microsoft Sentinel comes in. Microsoft’s cloud SIEM & SOAR product built on Azure, Sentinel allows you to set up certain detection rules and configure automatic remediation actions.
The Microsoft 365 Kill Chain and Attack Path Management
An effective cybersecurity strategy requires a clear and comprehensive understanding of how attacks unfold. Read this whitepaper to get the expert insight you need to defend your organization!
Five: Avoid Data Exfiltration with Power Automate Data Loss Prevention
My last tip is centered around the dangers of Power Automate and suppressing the possibility for data exfiltration. Power Automate is an amazing platform that allows end users to create automations through a no-code solution, but it also contains many ‘connectors’ that enable easy integration with other cloud platforms, including both Microsoft and third-party products.
Google Drive connector is a good example – this connector allows users to create a Power Automate Flow to upload documents to Google’s cloud platform. This can be an extremely dangerous thing, as someone could create a flow to upload every email or document they receive in their mailbox to Google Drive.
However, Power Automate supports Data Loss Prevention (DLP) so you can tag connectors as business or non-business or even block certain connectors entirely. A flow cannot mix business or non-business connectors, and this ensures no data exfiltration to non-authorized applications can happen. Power Automate DLP is configured through the Power Platform administrator portal.
**If you wish to audit which connectors are currently in use before blocking them, you can use this script to create such a report.
Five More Ways in Part Two
While there’s no guarantee that these suggested approaches will make your tenant 100% secure, they do provide additional layers of protection. Although I’ve only suggested five ways here to boost security, there are many steps you can take to improve further.
Like just about every aspect of technology, security techniques are constantly improving and it’s important to keep an open mind and have a willingness to learn new methods. In part two, I’ll review five more ways to secure your tenant using options that are available with additional security licenses.





Incorrect, per-user MFA in Microsoft Entra is completely free. Conditional Access MFA requires P1.
I think per user mfa requires azure ad p1 license.
Only free option for mfa is azure ad security defaults.
how can i get money please send me
Thijs,
This is a great article. This is exactly what I am looking for.
Thanks,
Dan Vespa