Sensitivity Labels Might be the Best Way to Block Access to Documents for Terminated Employees
In a simpler world, we worried about the prospect of terminated employees removing information from companies in PST files generated by Outlook. PST files arrived with Outlook in 1997 as a solution for the limited mailbox storage available in Exchange Server at the time. Most users had 50 MB mailbox quotas. Even with the smaller average size of messages and lower message volumes, it was easy to fill a quota, which meant that you needed to free mailbox space to continue receiving new emails.
The PST, or personal store table, allowed users to move messages from their online mailbox to local storage. Since then, people have used PSTs in many different ways from mailbox migrations to mailbox exports (something still supported today by Purview content searches). Useful as they could be, the insecurity and fragility of PSTs were their downsides, an aspect exposed all too often when attackers compromised servers and recovered PSTs full of sensitive information (like the 179 PSTs stolen in the great Sony heist of 2014).
Time moved on. Mailbox quotas expanded dramatically and migrations moved online. Outlook still supports PSTs and some companies still seek to convince users of the wisdom of using PSTs for mail storage. And people do use PSTs to store email and attachments – and take that information with them when they switch employers. A registry setting is available to block Outlook from creating new PSTs or adding new items to PSTs. It’s a good control to implement. No Microsoft 365 enterprise user needs to create and store email in PSTs and any deviation from policy should require an excellent justification.
A More Complicated World
But stopping people from walking away with Microsoft 365 data is a more complicated challenge than the relative simplicity of dealing with PSTs in Exchange. Consider these factors:
- More data is stored online. Microsoft facilitates personal storage with large mailbox quotas, and “unlimited” storage for OneDrive for Business.
- More data types are involved (Teams, Planner, Viva Engage, Exchange email, SharePoint documents, and so on).
- More devices are in active use. Since the Covid pandemic, more people have been working from home and possibly using unmanaged devices.
- Better synchronization capabilities in both Outlook and the OneDrive sync client.
It’s also the case that corporate information can find its way into OneDrive consumers. For instance, if someone uses Visual Studio Code to synchronize code from a GitHub repository, it can end up in a folder under their Documents folder. If OneDrive consumer synchronizes Windows known folders, it processes the copy of the GitHub cope too.
When a user leaves an organization, it’s easy to remove access to their account and mailbox. It’s much harder to be sure that the ex-employee hasn’t retained copies of sensitive documents synchronized locally from:
- Their OneDrive for Business account.
- SharePoint Online sites they have access to through explicit membership or a Microsoft 365 group (Teams).
The question is what steps can organizations take to minimize the potential of data loss to ex-employees?
Microsoft’s advice on dealing with the data of ex-employees covers aspects like wiping mobile devices and granting access to the OneDrive for Business account to another user. Both are good steps, and the account deletion process used by the Microsoft 365 admin center includes the option to grant access to another user.
OneDrive Group Policies
OneDrive for Business supports a comprehensive set of group policies. The policies include options such as blocking:
- Synchronization of Known Windows folders.
- Synchronization of Files from other tenants.
- Running OneDrive consumer.
- Upload of specific file types.
All are useful in their own context, but none help with ex-employees. One setting that might is DehydrateSyncedTeamSites, which converts files synchronized from SharePoint Online to online-only files. In other words, only pointers exist on the local PC and if the user wishes to access the content, they use the pointer to open the online file. If the user can’t sign in because an administrator has blocked their account, they won’t be able to open the online file.
Use the Block Download Policy
Another approach is to use the SharePoint Online block download policy to protect sites that hold confidential information. Administrators can assign the policy to sites with PowerShell (soon they’ll be able to assign a sensitivity label containing the block policy to sites). When a site comes under the control of the block download policy, users can’t download files (even to print them). The only access is through a browser-based app, like Office Online, unless the user is on a policy exclusion list.
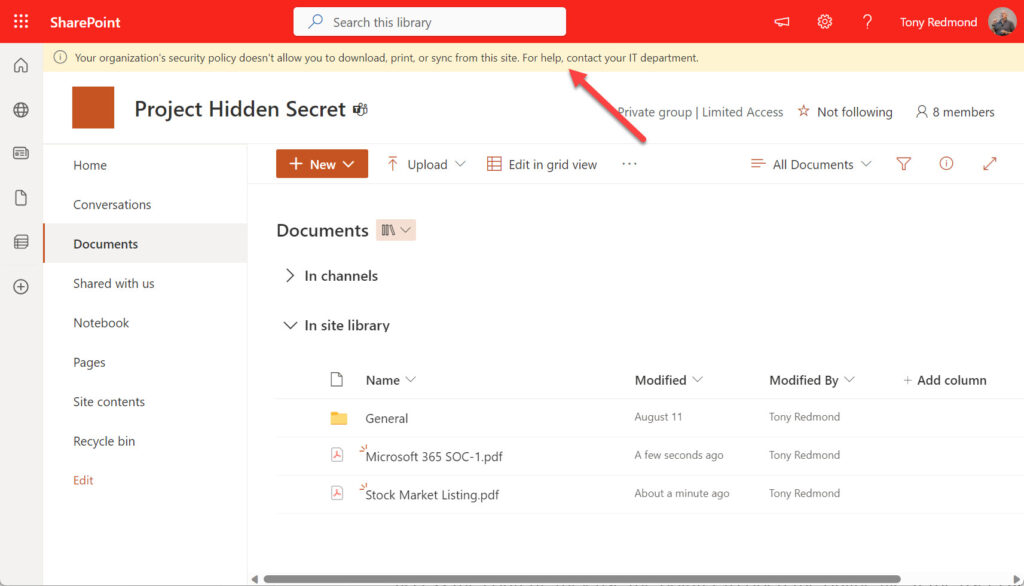
The downside of using the block download policy is that every user who accesses a site protected by the policy requires the Microsoft Syntex – SharePoint Advanced Management license ($3/user/month). In the overall scheme of things, $3/user/month isn’t a lot to protect sensitive information, but it could rise to a substantial amount if the block gets applied liberally to hundreds of sites.
Use Sensitivity Labels
The basic principle behind rights management is that a user must prove their identity to secure the rights to interact with content. When a user attempts to open a document protected by a sensitivity label, they must authenticate by signing into Entra ID. If they can’t authenticate, they can’t access the content.
Sensitivity labels “travel” with their documents. If an ex-employee synchronizes a bunch of protected documents before they leave the organization, they cannot open those documents after the organization blocks their account. The exception is where the rights assigned by labels to documents include permissions granted to “any authenticated users” or users belonging to other specified domains. If the ex-employee can authenticate with Entra ID in another tenant or uses a Microsoft Services account, they can open documents using the “any authenticated users” permission, or if the tenant is listed in the permissions, they can use that right. It’s unlikely that highly sensitive documents will have labels with such wide permissions as this removes some of the benefits of protection.
Sensitivity labels are a good way to protect confidential information from unauthorized access to Office documents and PDFs. Unless you use the File Explorer extension to assign sensitivity labels to other file types, they won’t be protected. Currently, the File Explorer extension is part of the Unified Labeling client (due for retirement on 11 April 2024). The client requires an Azure Information Protection license. Microsoft says that they will make the File Explorer extension available separately following the retirement of the unified labeling client.
No Silver Bullet
There’s no single off-the-shelf answer to how to prevent ex-employees from accessing local copies of confidential documents after they leave. OneDrive for Business makes it easy for users to synchronize documents from their own account and every SharePoint Online site they have access to. Without much effort, someone can download gigabytes of documents without much effort (if they do this in the days before they leave, it might trigger a Purview alert). Compared to PSTs, which only Outlook for Windows clients can open, downloaded copies of Office documents and PDFs are more accessible.
Overall, sensitivity labels are the best way to stop ex-employees from accessing local copies of confidential documents. The necessary technology is part of the Office 365 E3 and above SKUs. The caveat is that before deploying sensitivity labels, make sure that you understand how sensitivity labels work, the supported applications, and how to manage sensitivity labels. Microsoft has done a lot to make sensitivity labels work well across Microsoft 365, but the practical, day-to-day administration of protection still requires effort and expertise to stop OneDrive for Business from becoming the same kind of weakness that PSTs once were.
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.





Thanks, Tony! Previously I liked the idea to use Conditional Access with Windows Information Protection. It’s sad, that MS decided to discontinue WIP and there are no alternative as far as I know…
Great article and timely for Copilot pre-adoption readiness around data governance.
Thanks for the overview, Tony.
As someone new to this field and rolling out sensitivity labels for the first time it’s good to see that it’s a potential solution for this problem.
Another helpfull article, just great.