Constant and Evolving Change to Improve Sensitivity Label Functionality
Microsoft released sensitivity labels for Office 365 in September 2018 to replace Azure Information Protection (AIP) labels. At the time, sensitivity labels offered limited functionality and required users to install a separate client before they could apply labels to Office documents. Since then, Microsoft has steadily pushed out new features and capabilities. Perhaps 2023 will be the year when your organization deploys sensitivity labels to protect and classify information stored in Exchange Online and SharePoint Online.
Licensing Sensitivity Labels
Sensitivity labels are part of the Microsoft Purview Information Protection product. Anyone with an Office 365 license can read documents or emails protected by labels. Users require Office 365 E3 or above to apply a label manually, while automatic policy-driven application of labels requires Office 365 E5, Microsoft 365 E5, or Microsoft 365 E5 compliance licenses. Automatic is a broad term and includes assigning a default sensitivity label for a SharePoint document library (the same requirement exists to apply a default retention label for a document library).
Users who don’t belong to a Microsoft 365 tenant can still receive and access protected content. In these scenarios, attempts to access the content will redirect to the Office 365 Message Encryption (OME) portal. Once authenticated, the user can read the content.
Managing Sensitivity Labels
Sensitivity label management is through the Information Protection section of the Microsoft Purview Compliance portal (Figure 1). Note that each label has a priority number from 0 (zero – the lowest priority). SharePoint Online uses the priority order to decide if users store confidential information on sites intended for more general access (a label mismatch).
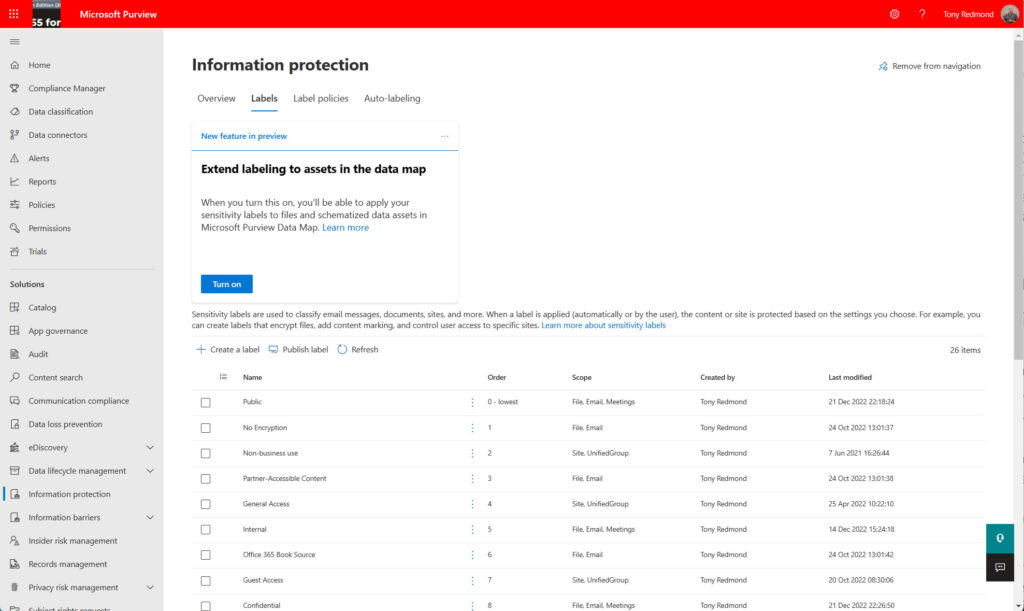
The tasks involved in managing sensitivity labels are:
- Defining the usage of the labels.
- Defining settings for individual labels.
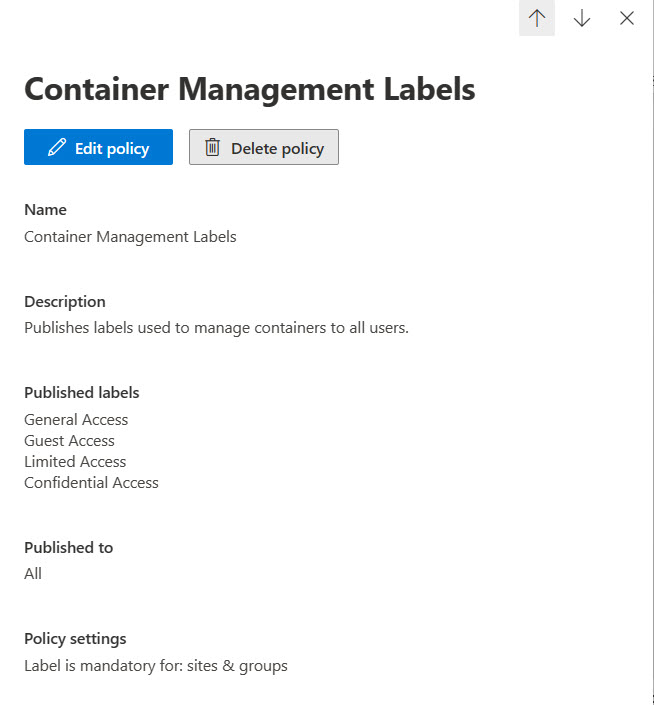
- Publishing labels through label policies to target audiences (user accounts). A label policy (Figure 2) consists of one or more specified labels and a target audience (user accounts). Publication must make labels available to users before they can apply the labels to documents and emails.
Two Broad Categories of Functionality
Sensitivity label functionality divides into two broad categories.
Protection: This was the original focus for sensitivity labels, where protection came from Azure Information Protection rights management. Essentially, users can only access protected content if the creator grants them the right to do so. The rights granted define the actions a user can take. For instance, they might be able to read a document but not print it. To help users understand that they’re dealing with confidential information, sensitivity labels can apply visual markers to documents and messages. For example, a label might insert text like “Confidential – Do Not Release Outside the Company” in a footer in Office documents.
Sensitivity labels also support the use of color as a visual indicator for the relative importance of labeled content. Labels applied to the most confidential material might be red, while those applied to less sensitive information might be yellow, green, or whatever other color hex code you think appropriate.
Either Microsoft (the default) or the tenant (BYOK or bring your own key) manages the encryption keys used for protection. Double-key encryption (DKE) is also available where both Microsoft and the tenant have separate keys, both of which must be available before a user can access the content. Finally, Outlook supports sensitivity labels that use S/MIME to encrypt and apply digital signatures to email. BYOK, DKE, and S/MIME show how Microsoft has expanded sensitivity labels to accommodate different forms of protection used by customers. However, the most common form of protection continues to be where Microsoft manages the encryption keys in its Rights Management service.
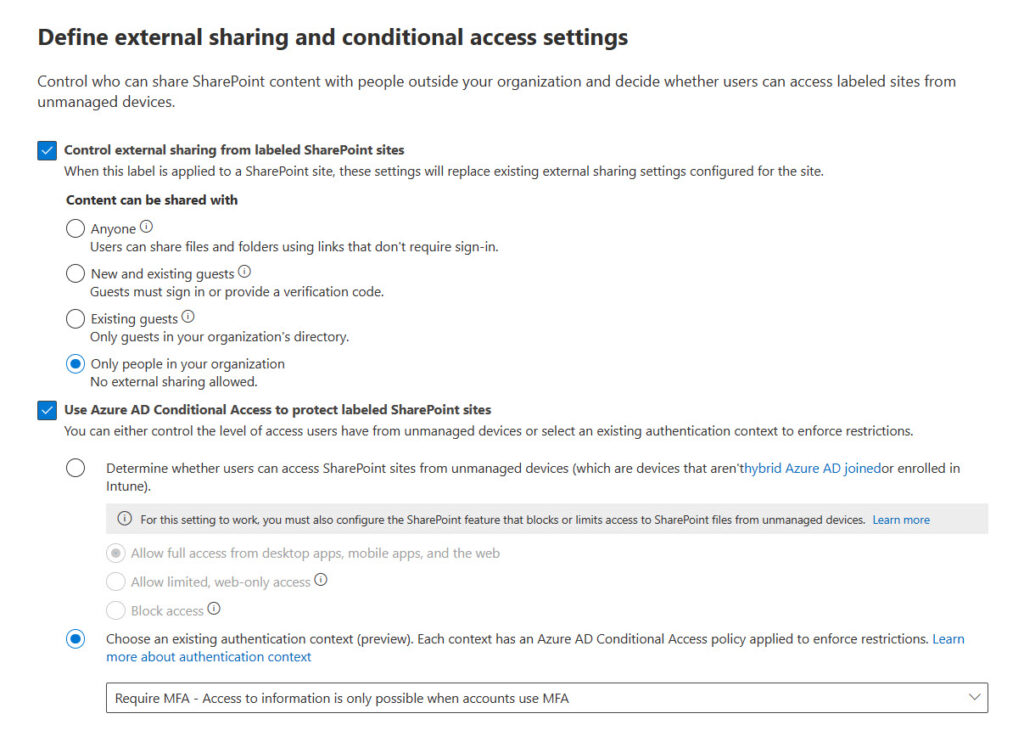
Container Management: Originally, a container is a team, group, or site. Recently, Microsoft has added OWA meetings and Teams meetings to the set (the latter requires Teams Premium licenses). Container management is a way for an organization to apply policy through labels. For instance, an organization probably doesn’t want guest users to be members of teams where people review highly sensitive information. By applying a label to the team that has the Guest Access setting disabled, no one except an administrator can add an external user to the team’s membership. Another example is the setting to control the sharing capability for a SharePoint site. In our example, it’s unlikely that the organization wants people to share documents from the site owned by the team with external users. The same sensitivity label that stops guest user access can also limit the external sharing capability for the site to be “Only people in your organization” (Figure 3).
Cybersecurity Risk Management for Active Directory
Discover how to prevent and recover from AD attacks through these Cybersecurity Risk Management Solutions.
Separate Sets of Sensitivity Labels
It’s possible to use sensitivity labels for both protection and container management. However, I prefer to create separate sets of labels to handle the two functions. I think this approach makes label management easier to understand. The scope of the labels shown in Figure 1 tells you the use of each label. “Site, UnifiedGroup” means that a label is for container management, while “File, Email” means that the label is for protection. “Meetings” is the latest scope used to protect meetings.
It’s important to emphasize that any implementation of sensitivity labels involves a considerable effort to plan and deploy labels. Even items that appear simple, like label naming, require care. Users will do the right thing to protect sensitive information if they are guided by good names, descriptions, and limited choices. By that, I mean that it’s hard for users to decide between three or four labels that might be very similar. A label naming scheme that is clear, precise, and easy to follow is always better than giving too many choices. Take the example shown in Figure 4. Eighteen labels is too many, and the names of some do not clearly indicate the intended usage.
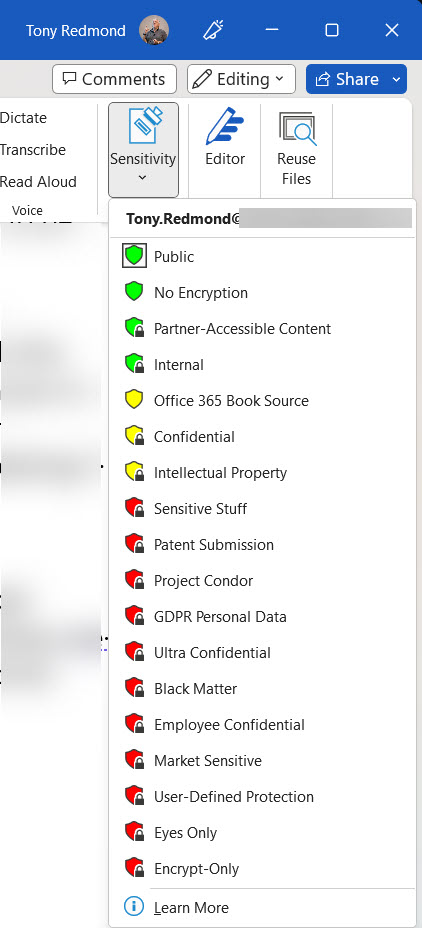
The screenshot comes from my tenant, and I know the reason why so many labels are present. But think of the average user who’s asked to choose from the array of available labels and then reflect on how many errors might happen.
Sensitivity Label Clients
The biggest change for sensitivity labels over the past few years is native mode support for labels within applications. Native mode means that an application includes code built using the Microsoft Information Protection SDK to apply, read, and respect sensitivity labels. As noted above, originally, labeling depended on a separate client (the AIP client and later the unified labeling client). Now, the Microsoft 365 enterprise desktop apps (Word, Excel, and PowerPoint), their online equivalents, and the paid-for version of Adobe Acrobat can interact with sensitivity labels directly. Support extends to protecting PDFs generated by Office applications.
The unified labeling client is now in maintenance mode. However, it’s still needed to apply sensitivity labels to files stored outside Microsoft 365 or files belonging to applications that don’t support information protection. This article discusses how to use the client to apply sensitivity labels to the MP4 files generated for Teams meeting recordings.
SharePoint Online and Sensitivity Labels
Another area of major improvement over the last few years has been the support of sensitivity labels within SharePoint Online. Initially, although it was possible to store protected content in a document library, SharePoint Online couldn’t do anything with the encrypted file. SharePoint Online stores item metadata separately to the blobs used to hold documents in Azure SQL, so the metadata (like document names and authors) was always available. However, services like Microsoft Search couldn’t index the encrypted content, which meant that other Microsoft 365 services like Data Loss Prevention (DLP) policies couldn’t work.
The solution is for SharePoint Online to decrypt content before storing files and to encrypt files when users access the content. This makes it possible for other services to access and use protected content stored in both SharePoint Online and OneDrive for Business. The mechanism sounds simple, but a lot of engineering effort happened to make it possible.
Before an organization can use sensitivity labels with SharePoint Online in an integrated manner, it must opt-in to support sensitivity labels. This simple step tells SharePoint Online that it should decrypt protected content before storage.
Sensitivity Label Challenges
Microsoft has made great progress to improve and refine how sensitivity labels work across Microsoft 365. Some challenges still exist, including the lack of APIs to allow organizations to apply sensitivity labels to content (this is coming), but overall, the picture is very positive.
That is until you venture outside the boundaries of day-to-day work with Office/PDF files. Management of protected files can be difficult, especially for third-party applications. Take backup products for example. They request data from SharePoint and download protected files, which the backup product then copies to its repository. But recovery and access to the backup files by end users is less certain. Conceptually, the challenge is easier for the forthcoming Microsoft Syntex backup service because all data remains within Microsoft, but it’s still something to test.
The same question of how to deal with protected content exists for tenant-to-tenant migrations when millions of emails and documents might move from one tenant to another. User accounts created in the target tenant can open unprotected files, but it’s likely that rights assigned to protected files won’t include their email address and block access. Removing encryption from documents before the transfer can be done (the same process is used to recover protected documents left behind by ex-employees), but it’s painful and slow.
No doubt improvements will happen in these areas in the future. I can’t say when, so my anticipation is more in hope than with certitude.





Tony,
Can you confirm or deny the following:
“Sensitivity Auto-labeling for files at rest in SharePoint Online and OneDrive does not require the files to be new or modified. Existing files can be automatically labeled based on the conditions specified in the Sensitivity auto-labeling policies.”
If true, what triggers Purview to evaluate the policies on the files in the scope of the auto-labeling policies?
Hi Tony, excellent article.
I have a question: we recently implemented sensitivity labels with sublabels. We published only the sublabels for a pilot group, while another group was assigned only the top-level label (without sublabels). However, users in this second group cannot see the main label in their labeling options.
Is this the expected behavior, or is there something else we need to configure?
I’d expect users to be only able to see labels published to their location, so not seeing the main label because it’s not published to a user seems correct.
Thx for the reply! Maybe I didn’t explain it right, but in my lab tests, when I create a tag with subtags and only publish the main tag (without the subtags) to the end user, the user can’t see the tag at all.
Right. It’s because the sub-tags need an anchor. You must publisb both the tags and the sub tags so that clients can display the tags like Anchor/Sub-tag
Thanks for the clarification! I understand your point, but there’s something that still feels off. Here’s the scenario: I have a label with sublabels, and I publish only the main label (without the sublabels) to a user. In Office applications like Word or PowerPoint, the user can see and apply the label without any issues. However, when the same user tries to use the label in the new Outlook or Outlook on the web, the label doesn’t appear at all.
This doesn’t make much sense to me because the label works perfectly in Office apps but is completely unavailable in email. Shouldn’t the behavior be consistent across all applications? Is there something specific about Outlook that prevents the label from being displayed, even though it’s published correctly?
I just tested this scenario. Outlook classic displays both root and sub-labels properly. The new Outlook and OWA do not. You should report the issue to Microsoft, who will probably tell you that the new Outlook is a work in progress and not complete in some areas of functionality.
Hello Tony, great content from you. Still on the migration from tenant-to-tenant for sensitivity labels with encryption settings. Do you have like a guide on how to achieve this seamlessly without loosing access to files on the new tenant? Thanks
I don’t. I have never attempted to write it up.
Hi, I wonder where are the encryption keys stored when encrypting documents? And is anyone able to access the keys (tenant level admins, someone from Microsoft)? Any ideas? Thanks
Encryption is normally done by what’s called Microsoft managed keys controlled by key management devices in Microsoft datacenters. This is the easiest way to protect documents. Customers have the option to use double key encryption (DKE) https://learn.microsoft.com/en-us/purview/double-key-encryption where they control one of two keys that must be available for decryption/encryption.
I have an E5 license, I am showing a full list of Microsoft’s pretrained Classifiers in the Trainable Classifiers view, but when i attempt to create a Auto-Labeling policy based on a Trainable Classifier, the option for utilizing a Trainable Classifier doesn’t appear for me. Any idea what might be going on?
No idea. I did a quick check and see trainable classifiers when I follow the guidance in https://learn.microsoft.com/en-us/purview/apply-sensitivity-label-automatically and create a Content Contains rule and add a type to look for.
Within the Content Contains rule, is there any way to do a text match on the actual document contents? I see that there is a way to match on the document name, but I don’t see a way to specify a condition such as: Content LIKE “*Employee Termination*”
I haven’t tried this kind of match. Have you tested it?
That’s the problem. I don’t see anywhere that I can even specify a condition for a content text match. It seems like it should be a supported capability. ChatGPT and CoPilot both say I can do it, but the interface doesn’t seem to support it, and I can’t find anything in MS Learn documentation for it either.
So it sounds like it isn’t a thing.
Have you tried creating a custom classifier to match the text in the documents that you’re interested in? That’s one way to do it…
In the “Convert your label settings into an auto-labeling policy” (https://learn.microsoft.com/en-us/purview/apply-sensitivity-label-automatically#convert-your-label-settings-into-an-auto-labeling-policy) section of the article that Tony shared, it states that if the label contains trainable classifiers as a label condition, you won’t see the option to automatically create an auto-labeling policy. It does not state why.
Hi Tony, what is the best practice to manage digitally signed documents (e.g. Adobe Sign, Docusign, …) with encrypted sensitivity labels? I would like to be able to label those as well but it’s impossible, which make sense because the encryption would modify the document integrity. But we have many contracts etc which we would like to classify as “Employees Only”. Is the solution to store / send those files within an “encrypted envelop” (e.g. an email with encrypted label with the digitally signed doc as attachment)? Or else? Thanks!
That’s really a question to direct to Adobe because I have no idea if they are discussing this issue with Microsoft. The two companies have a close working relationship for sensitivity labels and might be able to help. Even if nothing solid is available today, raising the issue with Adobe will put it on their to do list.
I am in the testing phase to apply sensitivity labels at the company where I work. But I have faced a series of compatibility issues when opening files protected by labels that apply encryption and that were created before the labels were deployed to users, especially when users try to open these documents in Office Web (F3 Licenses, E1). For example, if I create a new word document (from scratch) and apply a confidential label that applies encryption and send it to a colleague who only has Office Web, he can open the document correctly. But if I take an old document, created last month (before the labels were deployed), for example, and apply this same confidentiality label. When I share it with my colleagues who use Office Web, they are unable to open the document and are presented with the message: “Sorry, this document is protected by Information Rights Management (IRM) and contains special properties that Word does not support in a browser. …..”
And that’s weird, because it’s the exact same label. However, one is applied to a file created after the deployment of the confidentiality labels and the other is applied to a file that already existed before this deployment.
I tried to replicate this by taking some old documents about Exchange 2013 (from 2012-13) and applying a sensitivity label that I updated yesterday to them. All worked as expected and I was able to open the protected documents with Edge. Obviously, I have no access to your tenant, so I think you should report the issue to Microsoft and ask them to check out tenants, labels, policies, access rights, etc. to make sure that everything is configured as it should be.
Tony– I’ve used sensitivity labels for about 7 years to protect access with an expiration date. In August, I began having problems that some users who were authorized were denied access. We tried an alternate email address for access, which worked half the time and then stopped working. Microsoft had us rebuild the registry for Office file/credentials. That worked for some for a few weeks. Last week Microsoft had us run a command in Powershell to fix the problem and now I can’t access the labels: I get ‘not able to find IRM template’ error message. Our problem is creating huge problems by users not having access to documents.
Did this change to Purview cause this? Do you know a fix (Microsoft doesn’t)?
Many thanks!
I don’t have a magic bullet for you to fire. This sounds like something you need to escalate within the Microsoft suppprt organization. You’re paying for support, so they should deliver it. Not being able to find the IRM template is serious because it could mean that the database where the templates are kept is inaccessible. Can you edit labels through the Purview compliance center? Either way, I think I’d be making a big noise with Microsoft Support and asking for escalation for assistance from engineering…
Thank you. I have been working with Microsoft support for months without resolution. I appreciate you taking time to read and learn that this is tough nut.
A most helpful article, thanks for pulling that together.
I work in a highly regulated finance firm and we want to encrypt highly sensitive SharePoint docs (inc PDF) from Teams/SharePoint admins (i.e. me!) from accessing those docs once labels are applied.
The content is unstructured and virtually impossible to create rules for, so container protection I guess is the way to go.
I’m thinking of creating a parent label called Restricted, with a bunch of sub-labels for each of the types of data being protected, then controlling access to those sublabels through Entra M365 Groups (not the Teams Groups), so only our security team can effectively manage label access. Is this the way to go? Or am I barking up the wrong tree! :o)
Cheers, Ellya
SharePoint Dude
First, by container protection, do you mean setting a default sensitivity label for document libraries? That will certainly work to assign a label to all new documents created in the library, providing users have Office 365 E5 (or equivalent) licenses.
Second, why would you have sub-labels for each type of data being protected? The usage rights assigned in labels apply to users and groups, not file types. Do you mean that you will have different labels for different groups within the company?
Hi Tony,
Thanks for this article and all the materials here! Great stuff!
I have a question for you about using sensitivity labels to limit users from creating public SPO groups/sites.
I’ve created 2 labels and published them via a single label policy, however I haven’t figured out how to prevent users from using one of the labels (for public sites), while the other (default, for private sites) would be the only one they could use.
The goal is to make the users have to ask for admin approval to create public sites (which should be as few as possible).
I tried to do it in Entra ID conditional access policies + groups, but they don’t seem to be the right tool to me…is MS Defeder -> Policies (which I’ve only started exploring) the right answer?
Any advice would be highly appreciated 🙂
Many thanks!
Mike
If you want that kind of control over public groups, I would only publish container management labels that allow users to create private groups/sites/team and implement a process to allow them request that a group/site/team be changed to public through application of a label that is only published to administrators.
Thanks Tony, that makes sense!
Can you today not just read but also classify a .pdf without having to buy an Adobe Professional / Enteprise license? It seems it was possible before with the client. (https://techcommunity.microsoft.com/t5/security-compliance-and-identity/using-azure-information-protection-to-protect-pdf-s-and-adobe/ba-p/282010)
The unified labeling client can classify PDFs (I believe). However, it’s due for retirement in April 2024 https://learn.microsoft.com/en-us/azure/information-protection/rms-client/aip-clientv2
Do you have a recommended best practices for testing labels, label policies, and DLP policies?
Get a free development tenant.
Set it up as closely as possible to the environment of the production tenant.
Test policies thoroughly in the development tenant before bringing them to production.
Hello good afternoon.
Excellent article, very useful for today..
We are experiencing the same scenario described in the paragraph:
“The same issue of how to handle protected content exists for tenant-to-tenant migrations when millions of emails and documents can move from one tenant to another. User accounts created in the destination tenant can open unprotected files, but it is likely that rights assigned to protected files do not include your email address and block access. Remove encryption from documents before the transfer can be made (the same process is used to recover protected documents left behind by former employees), but it is painful is slow.”
Do you have any strategy recommendations for “reclassifying” protected files en masse?
We thought about MCAS, but it seems that it has limitations for changing encrypted files through governance actions.
I do have ideas, but I suggest that you engage the help of someone experienced who has been through a T2T migration involving encrypted content. There is no substitute for experience.
Hi Tony –
Great info, thanks. Question: I have an auto-labeling policy applying a label to all files in a teams site. If I change the label in the auto-labeling policy, will it override and change the label that was previously applied by the policy? Do you know if the auto-labeling policy will apply to files in private channels created later too? I can’t find anything definitive about this.
With auto-labeling policies, if you change the label, it will be reapplied to items within scope of the policy if the priority of the new label is higher than that of the previously applied label. See https://learn.microsoft.com/purview/apply-sensitivity-label-automatically?WT.mc_id=M365-MVP-9501#will-an-existing-label-be-overridden
Thanks. And so far in my testing, an auto-label policy will not place labels on files in a private channel unless you add the private channel SharePoint site to the scope of the policy.
Yes, that’s right. The site belonging to a private channel is a separate site and therefore needs to be specified in the scope for an auto-label policy.
Hello, I need to disable external access to the some of my sharepoint sites connected to the same hub site called “Finance”. Based on the hub site, I need to restrict external user access to all these sites . So can you guide me to apply sensitivity label for this scenario ? Thanks!
What kind of sites are you using? Team sites are the only type that support sensitivity labels.
Hello Tony, Thanks for the response. We are using Team sites connected with M365 groups. I could see that we can use ‘External sharing and conditional access’ but how can set the adoptive scope as all my team sites connected to the Hub Site ? I could see only the Users and Groups only option under Information Protection –> Label Policy . Thanks for the help.
To use an adaptive scope with sites, you set a property on each site: https://practical365.com/using-adaptive-scopes-retention-policies-sharepoint-online/. However, adaptive scopes don’t currently support label application to sites.
The solution is therefore to go ahead and apply the appropriate sensitivity label to each of the team sites. This can be scripted using PowerShell.
Thanks . You put me in the correct direction . Your response really helpful for me. I do have one more requirement. I have other batch of sites with same List (Category), as a common list for every site. I need to apply sensitivity label and restrict external access for these sites. Do you think , here also I should go with PowerShell Script to apply label for each site ? Please confirm
I really can’t say because I don’t know the full circumstances of your environment. The decision about how to apply a sensitivity label (manually or via PowerShell) is one that you’ll have to make.
Hi Tony, this is very useful information, thank you.
I do have a question, I’m hoping you can help me with. If the company shareholders all have E5 licensing and apply a confidential label to a folder (in SharePoint or Teams) so that only the shareholders can view documents within that folder, what happens if a staff member with an E3 license tries to access that folder?
You apply sensitivity labels to documents, not folders (you can apply a retention label to folders). If the label settings do not permit users to access content, they won’t be able to open the files.
Great article! Thanks
I’m still a bit confused by the split between E3 and E5 capabilities. I’m hoping you can help me out.
If I only have E3 licences and apply a sensitivity label to a SharePoint site will all the documents in that site inherit that sensitivity label?
If you apply a default sensitivity label to a SharePoint document library, all new documents (but not existing document) will inherit the label. This is deemed to be an automatic function and therefore requires E5.
Hi there, solid info.
One quick question though
One of my customers is running with Business Premium License + Information Protection & Governance E5 license.
When deploying a sensitive label linked with an Azure AD authentication context it returns a client error: “Protection Level” not supported because the tenant is not E5 or the flight is off”
I thought we had the necessary licenses for this already, assume this means we need another license ?
Thansk
Authentication context needs Syntex advanced management licenses. See https://learn.microsoft.com/en-us/sharepoint/authentication-context-example
I am in the same situation as Alex. However I am not so sure about the Syntex advanced management license requirement. The section https://learn.microsoft.com/en-us/sharepoint/authentication-context-example#set-a-sensitivity-label-to-apply-the-authentication-context-to-labeled-sites you referred to, mentions “Sensitivity labels require Microsoft 365 E5 or Microsoft 365 E3 plus the Advanced Compliance license.” Especially Advanced Compliance license seems odd as this seems to be a discontinued SKU.
Syntex advanced management license is mentioned in the section before “Apply the authentication context directly to a site”. However this also works with Business Premium and Information Protection & Governance E5.
Support is still struggling with this. I am already at my third ticket for this with an additional GitHub issue for the docs clarification. Also because https://learn.microsoft.com/en-us/office365/servicedescriptions/microsoft-365-service-descriptions/microsoft-365-tenantlevel-services-licensing-guidance/microsoft-365-security-compliance-licensing-guidance#microsoft-purview-information-protection-sensitivity-labeling seems to mention other license prerequisites.
One of the Microsoft program managers working on SharePoint Online support for sensitivity labels is here at the TEC 2023 conference in Atlanta so I asked him. The response is that authentication context requires EITHER an E5 (Office 365/Microsoft 365) license OR the Syntex-SharePoint advanced management license. He suggested that if Microsoft support has an issue, they can ask about the topic in the https://www.yammer.com/askipteam#/home Viva Engage community.
Thank you for your feedback. Support hasn’t come back to me yet, sort of playing ball with the case between the M365 support team and Azure AD support, which is quite frustrating.
I already went the road with Syntex-SharePoint advanced management license, at least I guess this is behind “SharePoint advanced management plan 1” which I am on a trial right now. However this didn’t change anything with respect to the error message even after some days of having the trial active in my tenant.
Ask the Microsoft support team to speak to Sanjoyan Mustafi. He’s the PM for the feature.
Microsoft support guy just came back to me with the information that this only works with full E5. No E3 + some E5 add-on (like E5 Compliance). Just full-blown E5.
Well that’s a bummer. It quite takes away some of the advantage of having a separate Syntex-SharePoint advanced management license. Who said that Microsoft licensing is easy…
Very useful read, thank you for that.
My question is how are users supposed to deal with a document that carries a sensitivity label of another tenant and they are forced to apply a label from their own tenant when editing it.
As per my tests the existence of the sensitivity label from another tenant does not stop the user’s home tenant from forcing him to apply another sensitivity label.
Am I missing something or is there any way how to solve this?
Thank you!
A document can only have one sensitivity label with encryption (it can have multiple labels that don’t encrypt content). Users won’t be able to remove and replace a label on a document they receive unless they have the right to do so (Co-Owner). In your tests, did the label on the inbound attachment encrypt the content or is it just a visual marker?
Tony, all documentation that I can find indicates that a document can NOT have multiple labels applied simultaneously. Can you clarify?
A file can be assigned one sensitivity label with encryption at a time. If the labels don’t enforce encryption, several can be present on a file concurrently.
That was a great read! Although I have a question, if you may;
I’ve managed to create labels and a policy to apply them, and they work like a charm on the office online apps,
but they don’t show up at all on the desktop version. This may be silly, but I can’t quite figure this one out.
Do you use a perpetual version of Office or the Microsoft 365 apps for enterprise? You need the click to run version: https://learn.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-versions?view=o365-worldwide#sensitivity-label-capabilities-in-word-excel-and-powerpoint
Is it now possible to force external users to use true MFA when using Sensitivty labels on an email? When i’ve been experimenting with this before i could not find a scenario where i could encrypt/label an email to force the user to authenticate with true MFA (Authenticator, SMS etc) before opening the email. Only email OTP was possible, and that was only when the external user was using something other than Microsoft, for example gmail.
It’s sad that you cannot apply labels to one note content. Makes me wonder how much development is left for this app. You can apply flip but not sensitivity or one note and I haven’t found a third party app yet either.
It’s certainly curious that Microsoft has not yet plunged into labeling OneNote files, but the structure of a OneNote file might mitigate against the kind of protection they have. I don’t know. This is just idle speculation.
Great information, as always from you @tony 🙂